Best Noname Security Alternartives and Competitors
Discover the top 10 Noname Security alternatives and competitors in 2025 for better API protection.

Kruti
Jan 16, 2025
API security is important for every type of organizations that rely on APIs. They have to protect sensitive data, avoid breaches and ensure compliance. Noname security is an API security platform that helps in real-time threat detection, gives advanced behavioral analysis, and provides comprehensive protection features.
This blog will explore the top 10 alternatives of Noname security by giving an overview of their key features, strengths and weaknesses. It will allow organizations to choose the best tool for them according to their preferences.
Top 10 Noname Security Alternatives
API security is important to protect private data, prevent security breaches, and maintain compliance. Noname security is a leading platform that can meet organizations’ preferences and budgets. Here are the top ten alternatives of Noname Security.
1. Akto
Akto is an all-in-one API security platform. It allows teams to easily incorporate security into their development process, increasing productivity and decreasing vulnerabilities. Akto supports quick setup with an easy user interface, making it simple for small teams who value efficiency and secure development processes.
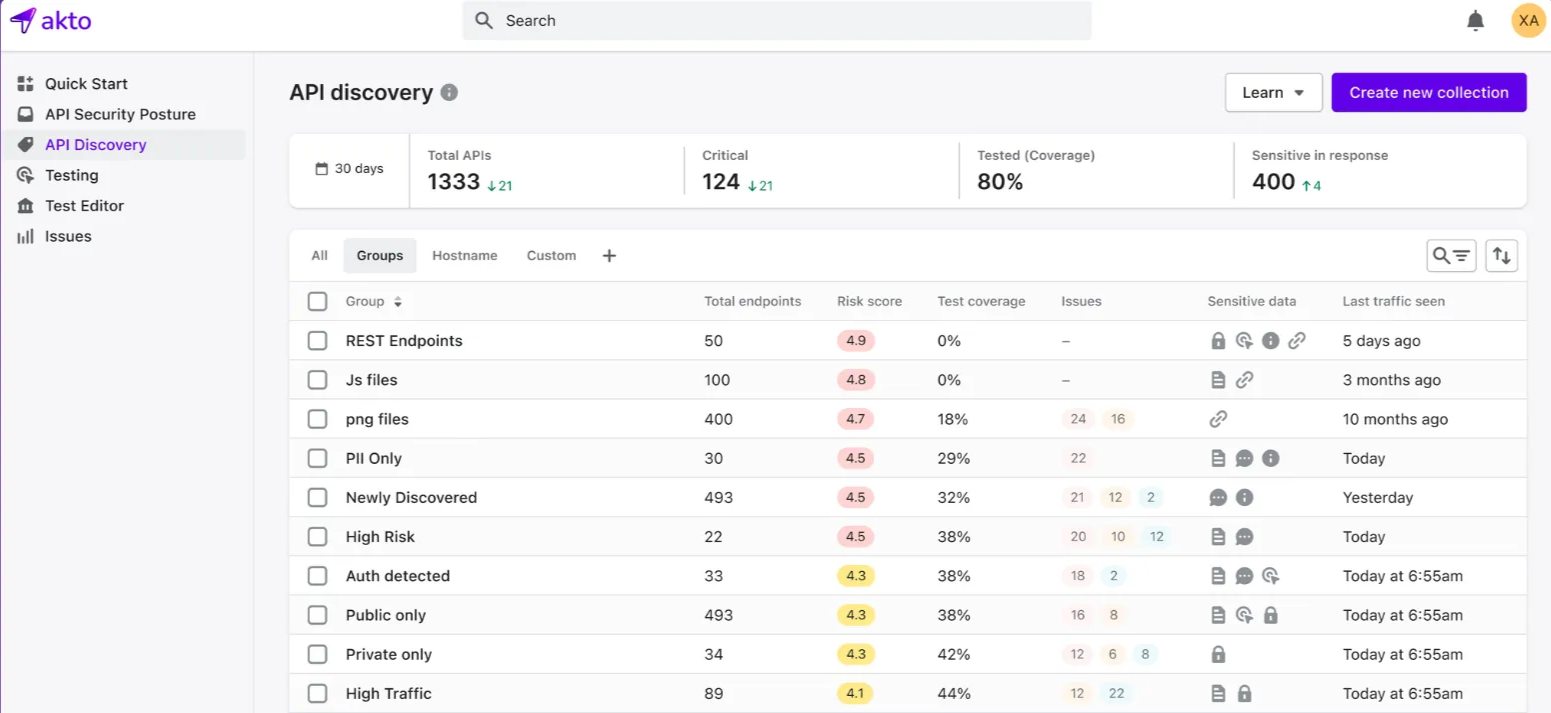
Source: Akto.io
Features of Akto API
Automated Vulnerability Scans: It scans APIs automatically to check the common security problems and save time and resources.
CI/CD Pipeline Integration: It easily integrates with common CI/CD solutions to make security testing part of the development process.
Comprehensive API Inventory: Provides a clear and structured list of all APIs for easier management.
Security Checks Before Deployment: It runs security checks before deployment to detect vulnerabilities early in the lifecycle.
Real-Time Notifications: It sends information about possible threats to security teams directly and allows them to take action before it grows.
Advantages of Akto API
Ease of Use: Small teams and startups can quickly embrace this solution.
Low Pricing: They provide low pricing which is perfect for small businesses.
Scalable Architecture: It has a scalable architecture that expands as the API ecosystem grows.
Simple for Installation: Security teams can easily install it without requiring training.
Best For: Akto is meant for startups and larger business setups looking for less expensive, developer-friendly API security options that are well integrated into the workflow.
2. Pynt
Pynt is an automated API security tool that security engineers use to perform tests in a fast-paced DevOps environment. This simple method allows security engineers to detect and manage issues quickly without affecting existing workflows. It uses CI/CD integration and quick deployment.
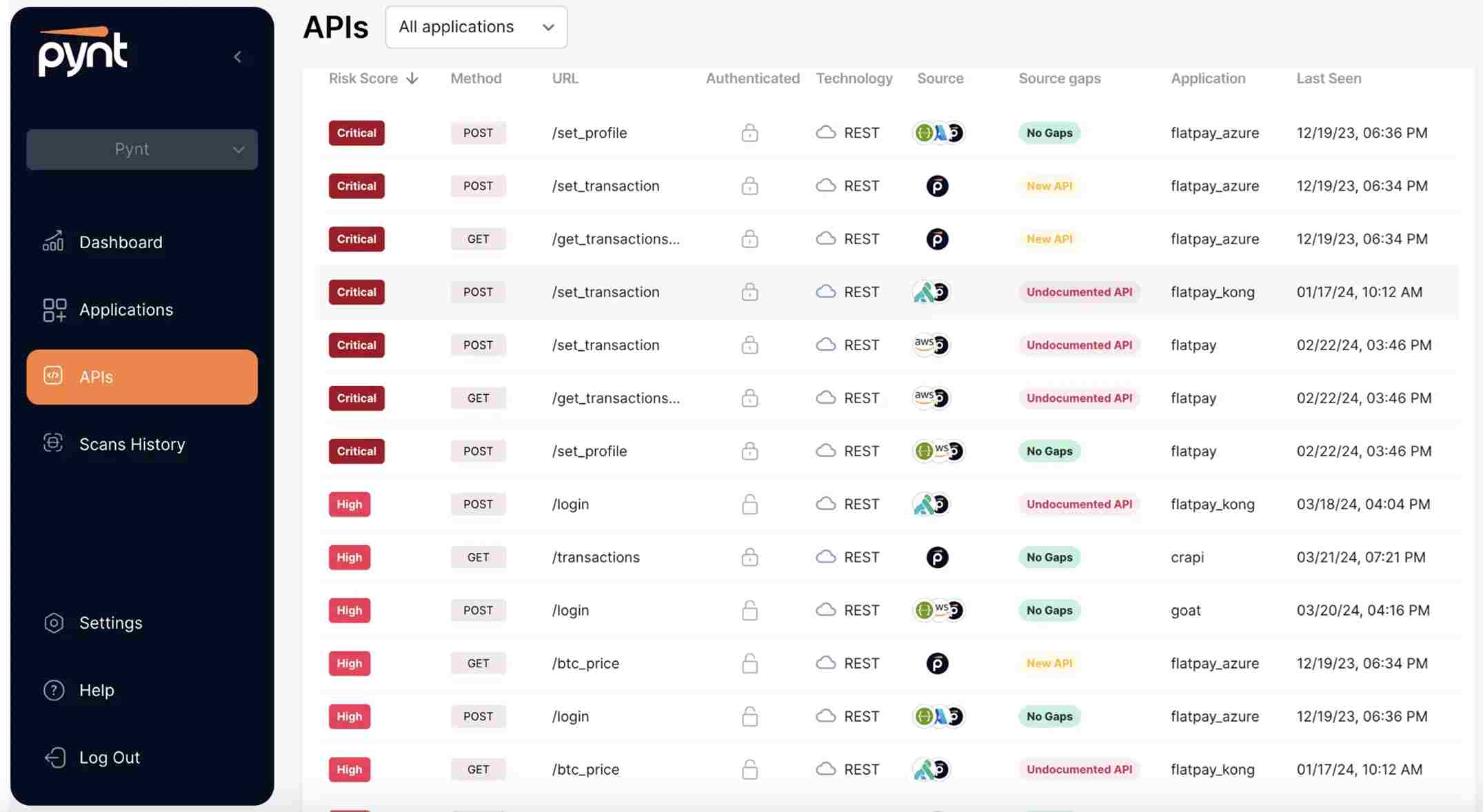
Source: Pynt.io
Features of Pynt
API Fuzz Testing: It performs fuzz testing to find hidden vulnerabilities.
Easy CI/CD Integration: It is easy to set up into DevOps pipelines, where security teams continuously perform security checks.
Detailed Reports: It provides comprehensive reports after every test.
Real-time Scanning: It scans APIs in real-time to find possible threats.
Advantages of Pynt
Automation-Driven: It automates tasks and reduces manual effort.
Strong Compatibility: It works with the latest development frameworks and tools such as selenium, RestAssured, Pytest and Jest.
Developer-Centric: Developers created it to provide every detail they need for their requirements and procedures.
Affordable Pricing: Smaller teams and entrepreneurs can access affordable pricing.
Disadvantages of Pynt
Complex Setup and Usage: Pynt’s set up and usage process requires specialized knowledge in cybersecurity, which may become a challenge for security teams.
False Positives: Pynt can confuse security teams with unnecessary alerts by generating false positives.
Best For: Pynt is ideal for DevOps teams seeking a lightweight, user-friendly API security tool for CI/CD.
3. APIsec
APIsec is an API security solution that provides penetration testing and AI-driven research. It offers powerful tools to detect vulnerabilities and reduce risks in complex API ecosystems. The platform gives organizations with strict security requirements.
Source: APIsec.ai
Features of APIsec
AI-Powered Threat Detection: It mainly uses AI to identify vulnerabilities and potential threats in the APIs.
Penetration Testing: It uses real-world attacks on the API and performs pen testing.
Automatic Compliance Checks: Performs automated API checks and follows compliance rules, such as GDPR or HIPAA.
Detailed Reporting: It provides detailed security reports with relevant data.
Scalable Security Solutions: It provides scalable security solutions to large organizations that have complex infrastructures.
Advantages of APIsec
High Scalability: Effectively secures large and complicated API systems.
Advanced Analytics: Offers detailed insights into API vulnerabilities and attack surfaces.
Proactive Security: Detects and handles threats before deployment.
Easy To Blend: Easily combines with enterprise security and IT systems.
Follow Compliance Rules: It follows all regulatory rules for easily installing APIs.
Disadvantages of APIsec
Hard to Learn: Security teams require training to achieve the best performance.
High Pricing: It is for large organizations with larger budgets.
Best For: APIsec is for organizations that need strong security and compliance features for protection, such as banking, healthcare, and e-commerce.
4. Imvision
Imvision provides API security solutions with detailed analytics for detecting vulnerabilities. It provides a detailed view of API behavior and allows organizations to check, understand, and secure their API ecosystems. Imvision's technologies help with complicated security and compliance requirements.
Source: Imvision
Features of Imvision
Validates API Schema: Automatically checks that APIs meet all the security standards.
Detects Fraud: Detects vulnerabilities in API usage patterns.
Compliance Analytics: Provides analysis according to compliance rules such as PCI DSS.
Visualization Dashboards: Provides simple dashboards for tracking API activity.
Scans Sensitive Data: It scans and protects sensitive data used for APIs.
Advantages of Imvision
Detailed Reports: It provides detailed data and reports about API traffic.
Compliance Features: It provides regulatory compliance features in every industry.
Scalable for Big Organizations: It manages large-scale API networks effectively.
Sends Alerts: It enables easy and quick monitoring and sends alerts for threat detection.
Data Security: It protects the important data of customers and organizations.
Disadvantages of Imvision
High Costs: It is perfect for big organizations, and may not be the one for smaller businesses.
Hard to Setup: It needs expertise for implementation.
Targeted Audience: It is for specifically targeted organizations with high-risk industries.
Best For: Imvision is for organizations that want to prioritize compliance and data protection, in industries such as finance and healthcare.
5. Data Theorem
Data Theorem offers a security solution for APIs, mobile applications, and cloud infrastructure. The company has a proactive threat detection and compliance solution, making it adaptable to all those organizations seeking comprehensive, all-in-one security capabilities.
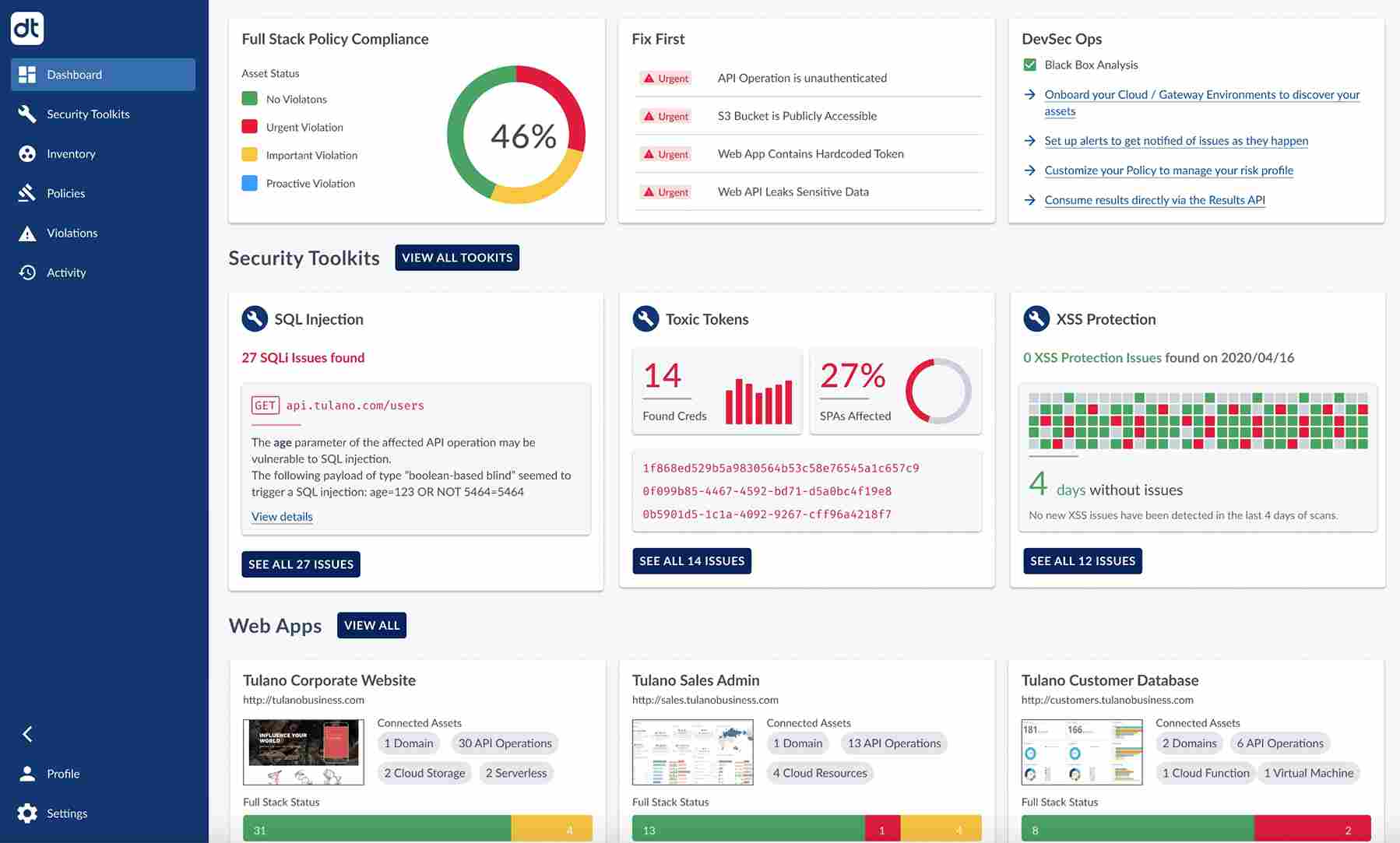
Source: datatheorem
Features of Data Theorem
Vulnerability Detection: Detects weaknesses in APIs and apps before their exploitation.
Combined with Cloud Security: It merges APIs easily in cloud settings such as AWS and Azure.
Mobile Application Security: Provides API security for mobile app backends.
Follow Compliance Rules: Ensures that APIs meet compliance criteria such as SOC 2 and GDPR.
Advantages of Data Theorem
Large Coverage: It protects APIs, mobile apps, and cloud environments.
Automation Tools: It provides automated tools to assist in vulnerability detection.
Detailed Insights: It provides detailed information regarding security threats.
Real-time Protection: It provides real-time protection, responding to threats as they arise.
Disadvantages of Data Theorem
Costly: It may be costly for small businesses that require complete features.
Basic API Tools: It provides basic API security tools with limited customization options.
Requires Expert Knowledge The platform requires competent IT teams to use it.
Best For: Data Theorem provides detailed security solutions for APIs, mobile apps, and cloud services.
6. Traceable AI
Traceable is a powerful API security solution that protects APIs in real-time using artificial intelligence and machine learning. It provides detailed insights on API traffic and behavioral analysis, with essential security measures, making it appropriate for big organizations with complicated requirements.
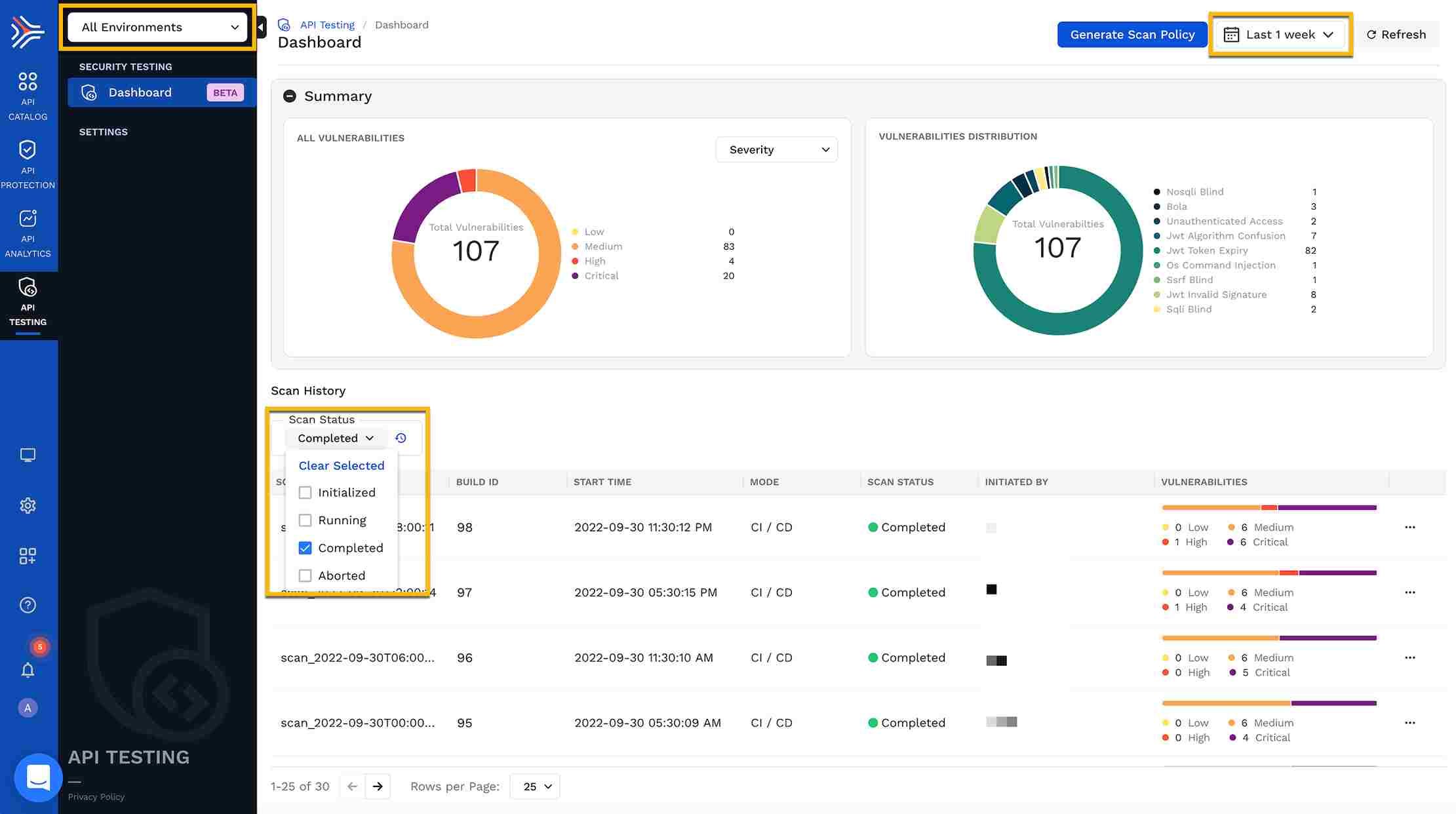
Source: Traceable AI
Features of Traceable AI
AI-Powered Threat Detection: It uses artificial intelligence and machine learning to identify advanced threats in real-time.
Behavioral Analytics: Tracks API traffic to identify unusual behavior patterns that could signal a security issue.
Real-Time Threat Blocking: It actively blocks possible threats when they are formed, thus decreasing the chances of breaches.
Comprehensive API Visibility: This provides visibility throughout the entire API usage and security.
Advantages of Traceable AI
Comprehensive Security: Defense against internal and external attacks on APIs and the infrastructure surrounding them.
Simple to Combine: With a proper setup, Traceable AI incorporates efficiently with complicated and current API infrastructures.
Complete Reporting: Provides thorough data and suggestions to improve security.
Disadvantages of Traceable AI
Costly: Traceable AI targets larger organizations, making it expensive for startups
Hard to Setup: Traceable AI setup needs proficiency and advanced configuration that will be difficult for the teams who are new to API security tools.
Fine-tuning: AI/ML models take time to optimize for new contexts.
Best For: Traceable AI is perfect for large organizations that want to perform real-time threat detection and complex security features in industries like banking, technology, and e-commerce.
7. 42Crunch
42Crunch is an API security platform, especially for development and production. It helps in API design, vulnerability scanning, and risk management. The platform is for organizations who want security throughout the API development process.
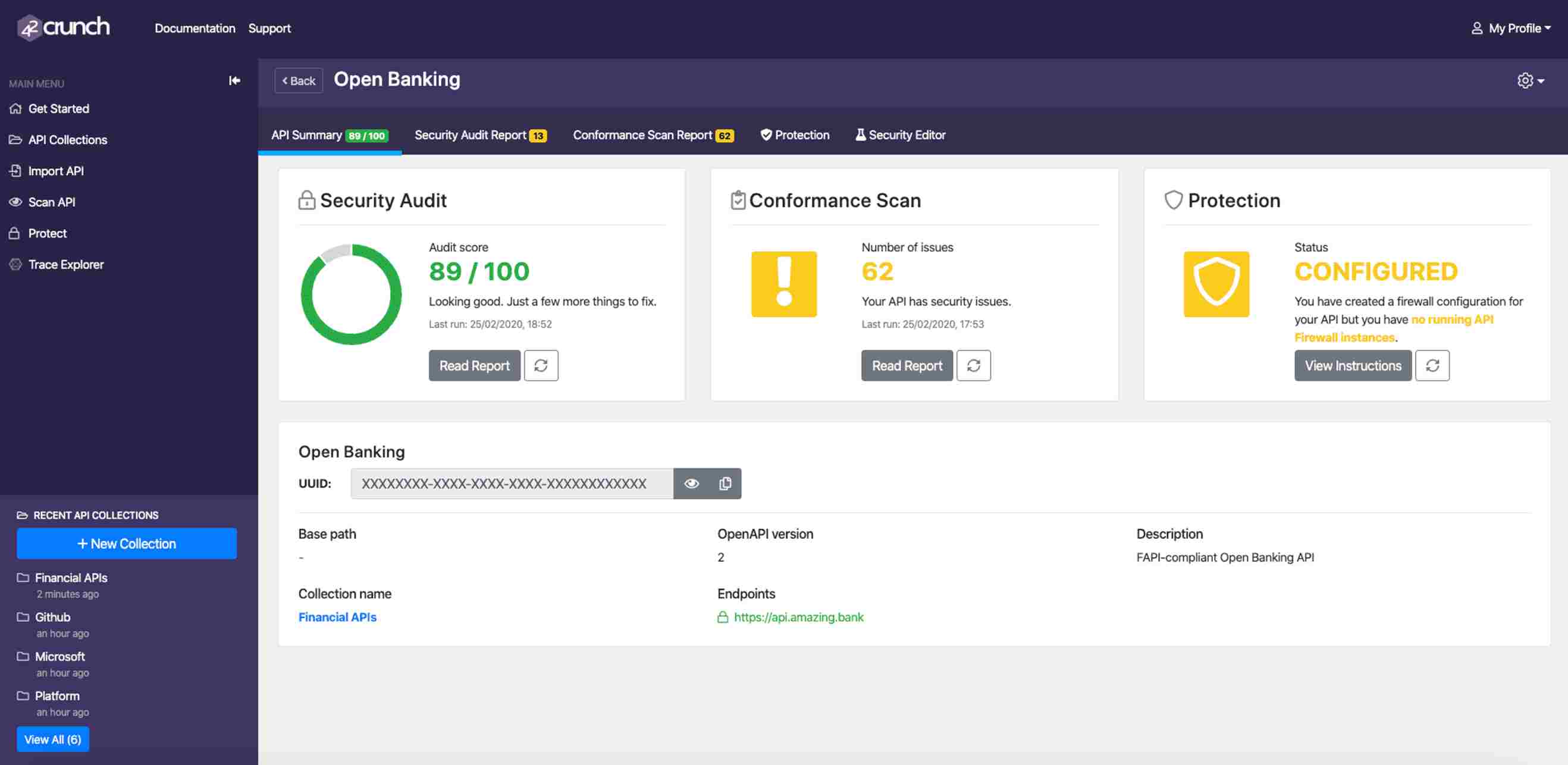
Source: 42Crunch
Features of 42Crunch
API Security Testing: The platform designs APIs and performs security and vulnerability detection at the time of design.
Risk Scoring: This gives a thorough risk assessment for APIs and allows to prioritize vulnerabilities based on their risk and potential impact.
Automated API Scanning: Automatically scans APIs for misconfigurations and security vulnerabilities when developers make updates.
Integrated Developer Tools: Offers plugins for IDEs (e.g., VS Code), SDKs, and CI/CD integration to support seamless security testing during development.
Advantages of 42Crunch
Developer-Friendly: Designed to work seamlessly with developers' workflows.
Early Risk Detection: Detects security risks during the design process, prior to implementation.
Regular Scanning: Scan APIs on a regular basis whenever they change.
Risk Prioritization: Identifies risks depending on their complexity.
Disadvantages of 42Crunch
Cost: The subscription plans of 42Crunch can be expensive for smaller teams with limited API security requirements. ****
Limited API Support: This platform mainly provide support for REST APIs, that may become a drawback for diverse API infrastructures
Enterprise-Level Pricing: This may be expensive for small and medium-sized enterprises without greater security expenditures.
Best For: 42Crunch is ideal for organizations looking to integrate security into API design and deployment processes, particularly in regulated areas like healthcare or finance.
8. Wallarm
Wallarm provides API security solutions for cloud-based environments and protects organizations from bot attacks, DDoS threats, and new vulnerabilities while regularly monitoring APIs. Wallarm is for organizations who want to transfer to existing cloud infrastructures.
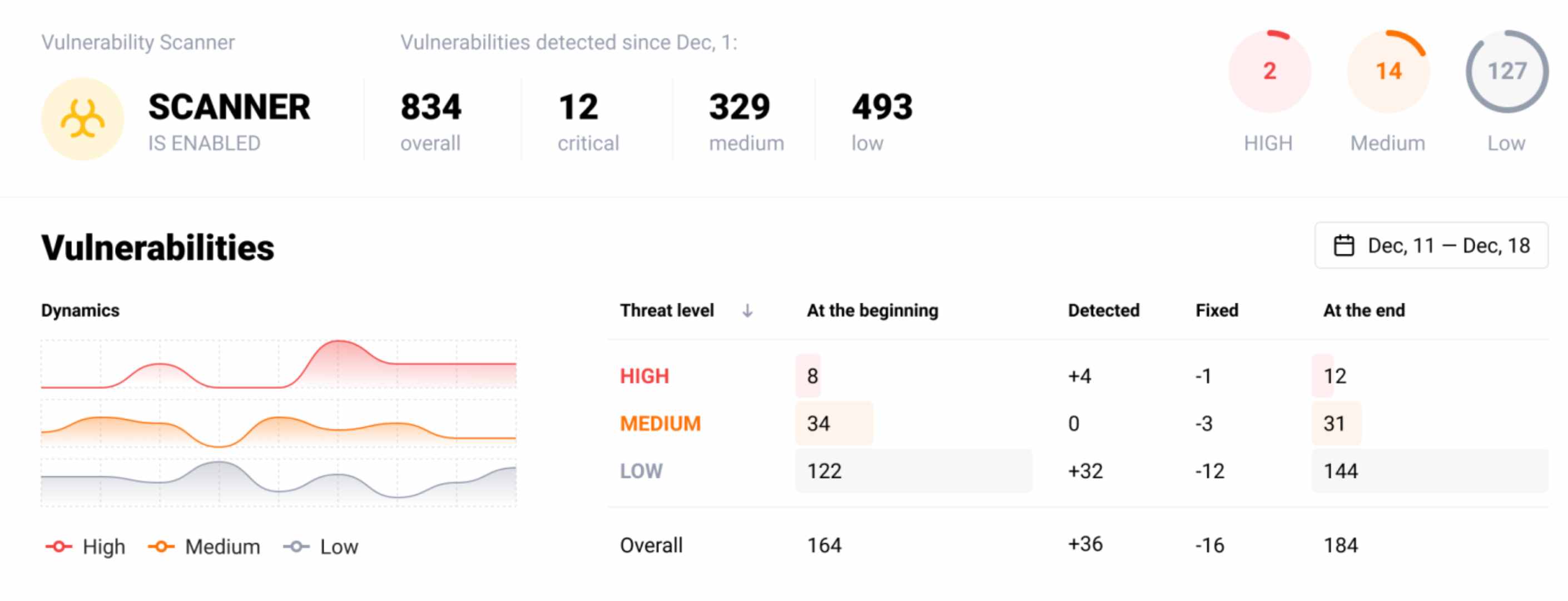
Source: Wallarm
Features of Wallarm
Bot Attack Protection: Secures APIs from unwanted traffic and manages vulnerabilities.
Attack Protection: Offers robust defense against DDoS attacks targeting APIs.
Security in Cloud Environments: It protects APIs that are host on popular cloud platforms like AWS, GCP, and Azure.
Flexible Security Policies: Adapts security policies dynamically based on API traffic patterns.
Advantages of Wallarm
Cloud-Based Platform: Ideal for organizations that currently use cloud-based apps and services.
Real-Time Protection: Detects and mitigates security risks in real-time.
Inexpensive: Ideal for organizations that use cloud-based infrastructures.
Disadvantages of Wallarm
Skills Required: Smaller teams will need extra skills to install it effectively.
Expensive: Smaller organizations might not be able to afford it.
Best For: Wallarm is for SaaS and large organizations that want advanced protection against DDoS, bots, and evolving API threats.
9. Akamai API Security
Source: Akamai
Akamai is a content delivery network (CDN) which helps to enhance the authenticity, performance and security of websites, applications and other internet-based services. It offers security features like DDoS protection and also reduces latency to boost the speed of delivery for websites and applications.
Features of Akamai API Security
Comprehensive Discovery and Visibility: Akamai provides vast discovery capabilities, helping organizations to get complete visibility of their unified API ecosystem.
Real-Time Threat Detection: With the help of behavioural analytics and machine learning the security and development teams can handle the possible threats and suspicious activities of APIs**.**
User-Friendly Dashboard: Akamai’s user-friendly dashboard helps security teams to easily understand their APIs status and respond to potential threats without requiring any technical training.
Advantages of Akamai API Security
Quick Setup: The easy setting up of this platform helps security teams to effectively and quickly implement their security measures.
Protection Across Different Environments: Akamai supports various setups whether hybrid, on-premises or cloud. This ensures the complete protection of APIs regardless of their hosting platforms.
Real-Time Alerts: It’s real-time alert system helps in detecting suspicious activities and possible threats quickly.
Disadvantages of Akamai API Security
Cost Considerations: 1. The subscription plans for this platform can be expensive for the organisations with low budgets.
Complexity in Configuration: The initial configuration of this tool can be complicated for security professionals, causing challenges in implementation and management without any proper security knowledge.
Dependence on Internet Connectivity: Any interruption in the stability of the internet connectivity can affect the security measures of the security teams leaving APIs being vulnerable.
Best For: Best for medium-sized organizations that need a cost-effective API security solution without the complexities of enterprise-level options.
10. Salt Security
Salt Security is one of the strongest API security platform companies focusing primarily on advanced threats, behavioral analytics, and protection in real-time. They make organizations equipped to protect APIs and defend against emerging data breaches.
Source: Salt Security
Features of Salt Security
Real-Time Threat Detection: Uses behavioral analytics to detect and mitigate risks as they emerge.
Automated Security Policies: Automatically combines security policies across APIs.
Detailed Insights: Provides deep insight into API traffic based on security trends.
Robust Security: Manages large settings and high API traffic volumes to provide security.
Advantages of Salt Security
Detailed API Security: Checks various API security risks, such as risk assessment, abnormality detection, and real-time monitoring.
Strong Behavioral Analytics: Provides deep insights on API activity, enabling the detection of even small threats.
Scalability: Ideal for large organizations with complex and dynamic API infrastructures.
Immediate Threat Response: Detects and minimizes threats during the API lifecycle.
Follows Compliance: Supports industries with strict regulatory requirements, including banking, healthcare, and technology industries.
Disadvantages of Salt Security
Costly: The platform is tailored for mid-to-large organizations, making it potentially expensive for smaller startups.
Complex Installation: It is hard to install so security engineers need experts for regular management.
Best For: Salt Security is for big organizations and industries with strict security requirements, such as banking, healthcare, and technology, where API security is important.
How to Choose the Right API Security Solution for Your Business
Choosing the right API security solution is important to protect sensitive data and for smooth running business operations. Here are important factors to make the right decision:
Determine Business Needs
Organizations should check their GraphQL, REST and SOAP APIs before choosing an API security solution. Check complexity and size of the organization's API infrastructure. The solution should meet these needs and comply with GDPR, HIPAA, and PCI-DSS. Choose a security solution that can find cyberattacks, misconfiguration, and poor access regulations to protect the organization’s API ecosystem.
Easy Integration
An API security solution should work easily with the organization's development and deployment processes. It works with CI/CD pipelines, version control systems, and DevOps frameworks. Choose a solution with less installation time and compatibility with existing platforms for no interruptions to daily operations.
Real-Time Threat Detection
An API security solution should be able to find various security weaknesses, wrong configurations, and many other attacks in real-time. Anomaly detection, rate limitation, and automatic notifications help security teams in spotting unusual behavior and attacks early in the development lifecycle. The teams can respond to various threats with real-time threat detection, limiting breach and attack damage.
Scalability and Flexibility
As organizations grow and API usage varies, the security solution must scale. It should support additional API types, handle growing API traffic, and work perfectly with changing requirements. Many organizations use cloud or hybrid environments where it should work well. Scalable security solutions maintain performance and security as organizations grow.
Detailed Reporting and Insights
The API security solutions should provide detailed information about API performance and security. They should be able to discover vulnerabilities, understand their causes, and provide full reports on security solutions. They should adhere to compliance requirements to assist the organization in risk management and protection.
Final Thoughts
There are several alternatives to Noname Security. Each addresses a different organization's needs. When choosing a solution, consider the size of the organization, the industry, and the complexity of security. Check these options further, request demos, and speak with experts to determine the best API security solution for the organization.
provides API security with detailed vulnerability analysis and real-time threat detection and combines easily with DevOps operations. It provides AI-driven analytics and regular monitoring which allows security engineers to quickly detect and remove risks before they develop. Akto provides easy UI and scalability which is ideal for organizations looking API security without sacrificing performance or flexibility.
Want to know more about Akto? book a demo now.
