Introduction DevSecOps Best Practices
The digital world is constantly evolving, and the way we develop software has to keep pace. From the traditional waterfall model, to the agile model, and now the DevSecOps paradigm, software development has undergone significant transformation. Security, however, has often been an afterthought. It is regularly bolted on at the end of the development process as an afterthought. Our aim is to challenge this outdated approach and set the stage for understanding why security must be an integral part of the development lifecycle as we discuss the best practices for secure software development.
Understanding the DevSecOps Paradigm
DevSecOps is more than just a buzzword. It is a fundamental shift in how organizations approach developing software. It represents the integration of Development (Dev), Security (Sec), and Operations (Ops) into one cohesive and streamlined process. Let’s take a look at the various aspects of DevSecOps
The Merging of Development, Security, and Operations
In traditional development models, the development, security, and operations teams would often work in silos. This led to delays, miscommunication, and potentially vulnerabilities! DevSecOps breaks these barriers down and creates a collaborative environment where all three teams can work together throughout the whole development lifecycle.

Development
This is where the actual code is written, tested, and prepared for deployment. In a DevSecOps approach, security practices are integrated right from the design stage, ensuring that security is considered at every step of development
Security
Unlike the traditional models, where security is often added later (or not at all), in DevSecOps, security measures are embedded from the beginning. Security teams work directly with developers to identify and mitigate risks early on. This proactive approach to security reduces vulnerabilities as well as the likelihood of a massively expensive late-stage security fix.
Operations
DevSecOps emphasizes automation and continuous monitoring in the operations phase. This ensures that security measures are always up-to-date and that issues are addressed swiftly. Automation also keeps the software development lifecycle quick and approachable for everyone involved.
Importance of API Security in DevSecOps
In the era of interconnected applications and services, Application Programming Interfaces (APIs) have become a critical component of modern software architecture. APIs enable different systems to communicate with each other. This provides easy integration and functionality between applications that would otherwise not be able to communicate. However, the surge in APIs also brings a new set of security challenges that must be addressed.

Threats and Risks
APIs can be exposed to various security threats, such as:
Injection Attacks: Attackers can inject malicious code or commands that the API might execute. This can lead to data breaches and other vulnerabilities.
Broken Authentication: Weak authentication mechanisms can allow unauthorized access to sensitive information and functionality
Sensitive Data Exposure: Insecure communication or improper handling of data can lead to sensitive information being leaked
API Abuse: Abuse of APIs by sending excessive requests can lead to Denial of Service (DoS) attacks. Rendering the API unusable.
Check out the OWASP Top 10 API Security Risks for a complete list!
Role of DevSecOps in API Security
Within the DevSecOps paradigm, security is integral. And API security remains a main target for attackers. The collaboration between development, security, and operations teams ensures that API-related risks are identified and mitigated as early as possible in the development lifecycle. Some of the ways this can happen is:
Secure Design: Security must be considered in the design phase of API development. This includes proper authentication, authorization, and data handling practices.
Continuous Monitoring: APIs must be continuously monitored for unusual or malicious activity. This will promise prompt detection and response to any threats.
Automated Testing: Automation in security testing can help identify vulnerabilities in APIs quickly and consistently.
Compliance and Regulations: Following regulatory requirements related to data protection and privacy is critical in API security.
How Vendors Like Akto Address These Challenges
Akto provides specialized tools and solutions tailored for API security. These tools can be integrated seamlessly within the DevSecOps process, providing robust protection against common API threats.
Best Practice 1: Incorporate Security from Day One
In the fast-paced world of software development, there is a tendency to prioritize speed and functionality at the expense of security. The DevSecOps philosophy challenges this approach by making the embedding of security right from the beginning of a project important. Some of the ways that security can be embedded in the beginning phases, for example the requirement analysis and design phase, are as follows:
Security Requirements: From the outset, security needs to be identified as a core requirement, alongside the functionality requirements. This includes what data will be handled, who will have access, and what measures will be used to protect that data.
Threat Modeling: Early stages of development should include identifying potential threats and determining how to mitigate those risks. This helps to design a secure architecture.
Secure Design Principles: Utilizing secure design principles, such as principle of least privilege and defense in depth, ensures that security is completely embedded in the entire design of the software, not just added at the end.

Benefits of Early Integration
Cost-Effective: Catching vulnerabilities early in the development process is more cost-effective than fixing them later in deployment.
Enhanced Security Posture: A security-first approach creates a more robust defense against potential threats. This protects both the application and the data it handles.
Compliance Alignment: By considering security from the start, the development process is more likely to align with any legal or regulatory requirements your organization may have.
Best Practice 2: Continuous Security Training
The landscape of cybersecurity changes rapidly. Threats evolve every day, and yesterday’s defenses may not be adequate to fend off tomorrow’s attacks. To maintain a good security posture, continuous security training is crucial. Here’s a detailed look at this vital practice within the DevSecOps approach.
Keep Teams Updated with Emerging Threats and Mitigation Techniques
Regular Training Sessions: Regular workshops, webinars, and training ensure that team members are kept aware of the latest threats and security measures to prevent them.
Utilizing Real-World Scenarios: Training should include real-world examples and practical exercises relating to your business. This builds hands-on experience in dealing with actual security threats.
Encourage Certifications: Encouraging team members to obtain professional security certifications can help deepen their expertise and commitment to security.
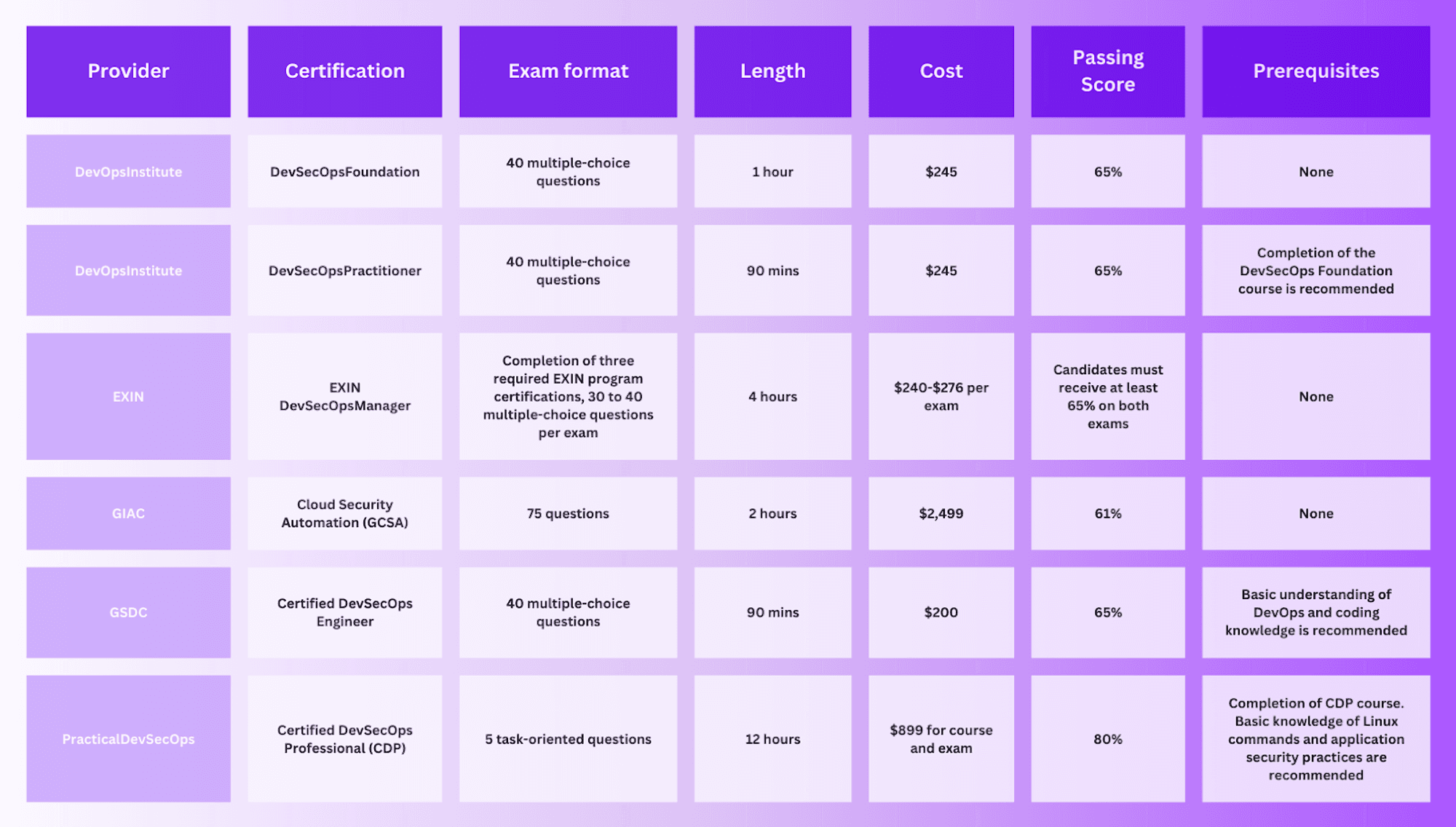
Best DevSecOps certification:
Why Continuous Security Training is Essential
Adapt to New Threats: The cyber threat landscape is constantly changing. Continuous training ensures that the team can adapt to any new security threats and deploy appropriate defenses.
Foster a Security Culture: Regular training emphasizes the importance of security across your organization. This will foster a culture where everyone involved takes responsibility for the protection of the system.
Reduce Human Error: Many security breaches begin from simple mistakes. Proper training helps minimize these errors by educating team members on best practices.
Best Practice 3: Automate Security Testing
In the era of rapid software development, manual security testing can become a massive bottleneck. This can delay releases and leave room for human error. Automation in security testing is a solution that not only will accelerate the process, but also in some cases can enhance accuracy. Here’s how and why it plays a crucial role within the DevSecOps approach. Some examples of tools being used for automated testing are Snyk and Akto.
Integrating Automated Security Checks into the CI/CD Pipeline
Continuous Scanning: Automated security testing tools can scan the code continuously as it’s developed. Identifying vulnerabilities early and allowing for immediate remediation.
Integration with Development Tools: Modern security testing tools can be integrated with the popular development platforms. This makes it easier to incorporate security checks without disrupting the development flow.
Customizable Testing Scenarios: Automation allows for customization to test specific scenarios that are relevant to the application’s context. This can enhance the accuracy of the testing process.
Try yourself with Akto.
Benefits of Automated Security Testing
Speed and Efficiency: Automated testing significantly reduces the time required for security testing, enabling quicker releases without sacrificing security posture.
Consistency: Automation ensures that the same tests are rung every time, eliminating variations that might occur with manual testing and enhancing the reliability of the results.
Scalability: As the codebase grows, automated testing can easily scale to cover any new code. This will make sure your testing is always comprehensive.
Best Practice 4: Implement Version Control and Audit Trails
Version control and audit trails are foundational in maintaining the integrity and traceability of the code within a DevSecOps environment. Below we will discuss why.
Maintain a Clear Record of Code Changes and Who Made Them
Version Control Systems (VCS): VCS such as Git allows developers to track every change made to the codebase. This provides a detailed history of the codebase. This helps in identifying when and where vulnerabilities were introduced and enables rapid rollback if necessary.
Audit Trails: An audit trail logs actions performed within the system, including changes, access, and operations. This will make sure that there is a clear and unalterable record, crucial for compliance and investigation purposes.
Benefits of Version Control and Audit Trails
Accountability: Clear tracking of who made changes promotes responsibility and accountability.
Integrity: Ensuring that only authorized people can make changes preserves the integrity of the codebase.
Compliance: For industries subject to regulatory requirements, proper version control and audit trails are often mandatory.
Best Practice 5: Adopt a Zero Trust Architecture
Zero Trust Architecture (ZTA) has become a cornerstone of modern security strategies, especially in DevSecOps. Let us briefly explore the components of ZTA and why it is so crucial.
Never Trust, Always Verify - The Mantra of Zero Trust
No Implicit Trust: Unlike traditional models that often trust anything inside the network, zero trust never assumes trust. Every request, whether internal or external, must be verified.
Least Privilege Access: Access is restricted to only what’s needed to perform a task. This reduces the potential attack surface as much as possible.

Benefits of Zero Trust in DevSecOps
Enhanced Security: By verifying every request, zero trust minimizes the risk of insiders and compromised devices gaining unauthorized access to assets.
Compliance Alignment: Zero trust can help meet various regulatory requirements by ensuring strict access controls.
Below are the benefits Akamai experienced by switching to zero trust architecture:
Minimized risk by providing access to only necessary applications - not full corporate network access.
Removed network complexity associated with legacy technologies, including backhauling VPN traffic to a central data center.
Improved productivity by enabling streamlined access for Akamai’s workforce, as well as for third parties.
Reduced IT appliance and process overhead associated with providing access to employees from newly acquired companies.
Enabled automation, orchestration, visibility and analytics over workloads, networks, people and devices to secure data.
Enhanced user experience across devices, including mobile, with faster and more reliable application delivery.
Cut costs with more efficient allocation of IT resources; fewer hours spent updating, managing, and maintaining hardware and software means more time for strategic imperatives.
Reduced help desk requests associated with application access.
Best Practice 6: Use Threat Modeling
Threat modeling is a proactive approach to identifying, managing, and mitigating potential threats in a system. It is a vital part of the DevSecOps methodology that provides insights into possible vulnerabilities.
Identifying Potential Threats and Design Countermeasures
Understanding Attack Surfaces: Threat modeling begins by understanding the system’s attack surfaces, including data flow, entry points, and potential areas of exploitation.
Risk Analysis: By analyzing the identified threats in our attack surface, developers can prioritize them based on severity and likelihood.
Countermeasures Design: Based on the analysis, appropriate mitigations and countermeasures can be designed to hopefully eliminate the identified threats.
Benefits of Threat Modeling
Proactive Security: Threat modeling allows teams to anticipate and prepare for potential threats, rather than having to react to them after an incident occurs.
Enhanced Communication: By creating a visual model of potential threats, different team members can understand the threat landscape of the application and collaborate on security considerations more effectively.
Alignment with Security Goals: Threat modeling ensures that security measures are aligned with the organization’s overall security goals as well as any regulatory requirements.
Best Practice 7: Engage in Regular Code Reviews
Code reviews are a fundamental part of software development, particularly within the DevSecOps approach. They do not only increase code quality but also play a significant role in security.
Peer Reviews to Detect Flaws and Enhance Code Quality
Collaborative Inspection: Regular code reviews involve team members collaboratively inspecting any code changes. This peer-review process brings diverse perspectives, helping to identify potential flaws and vulnerabilities.
Security Focused: By specifically looking for security issues during code reviews, teams can catch and fix security-related bugs before they become real problems in a production environment.
Benefits of Regular Code Reviews
Early Detection of Vulnerabilities: Identifying security issues during the development stage can save time, money, and other resources later on.
Knowledge Sharing: Code reviews enable teams to learn from one another, spreading security awareness and best practices throughout the team.
Quality Assurance: Beyond security, regular code reviews increases the chances that code meets quality standards, enhancing the overall development and maintainability of the software.
Best Practice 8: Stay Updated and Patch Regularly
Keeping software up-to-date and applying patches promptly is a simple, yet often overlooked, practice that plays an important role in maintaining your organization’s environment in DevSecOps. Let’s dive in and take a look at why that is.
Importance of Keeping All Systems and Tools Updated
Closing Vulnerabilities: Updates often include fixes to security vulnerabilities. Delaying updates leaves the system exposed to known risks that can be exploited, that instead should be easily avoided.
Staying Ahead of Threats: Regular updates ensure that the software is equipped with the latest security measures to fend off emerging threats.
Challenges and Best Practices in Regular Updating and Patching
Automation: Where possible, automating updates ensures that patches are applied as soon as they are made available.
Testing: Updates should be tested in a controlled environment before being deployed to the production environment. This will make sure that the update or patch is not introducing any new issues.
Monitoring: Continuous monitoring of the systems will alert the team to any unpatched or outdated components that may pose a security risk to the environment.
Benefits of Adopting DevSecOps Best Practices
The adoption of DevSecOps best practices is not just about enhancing security. It brings a plethora of other benefits that contribute to the overall success and agility of an organization. Here we will speak on some of the benefits below.
Enhanced Security Posture
Proactive Protection: By integrating security throughout the development lifecycle, vulnerabilities are identified and addressed earlier. This will reduce the risk of breaches in the future.
Compliance Alignment: DevSecOps practices often align well with any regulatory requirements. This will help organizations maintain compliance with any industry standards.
Better Team Collaboration
Unified Goals: DevSecOps breaks down any silos between development, security, and operations teams. Thus fostering a collaborative environment where everyone works towards a common security goal.
Knowledge Sharing: Regular training, code reviews, and collaboration tools foster a culture where knowledge and best practices are continuously shared across the team.
Reduced Costs
Early Detection of Issues: By catching and fixing security flaws early in the development process, organizations can avoid costly late-stage changes or breaches.
Automation and Efficiency: Automating security testing and other practices in the DevSecOps pipeline saves time and resources, allowing for more efficient development cycles.
Conclusion
Reflecting on the holistic approach to security in software development, it’s evident that DevSecOps represents more than a trend or set of tools. It is a mindset that places security at the heart of the entire software development lifecycle. From incorporating security from day one to fostering continuous learning, automating security testing, and staying ahead with regular updates, these practices embody a forward-thinking approach.
Adopting these best practices will lead to an enhanced security posture, better team collaboration, reduced costs, and overall, a more resilient software environment. As the digital landscape continues to evolve, embracing DevSecOps becomes an essential aspect of staying competitive and secure. Encouragement for security professionals to be at the forefront of DevSecOps is not merely a suggestion. It is a necessity for modern organizations seeking to thrive in a rapidly changing technological world.
Are you ready to delve deeper into the world of DevSecOps? The journey towards secure software development starts with a commitment to learning and implementing these best practices. Now is the time to take the plunge into the promising world of DevSecOps. Join the community of professionals mastering the best practices in secure software development. Together, we can build a more secure and innovative future.
For more information, check out this webinar by Akto on API Security in DevSecOps.
Want to learn more?
Subscribe to Akto's educational emails for essential insights on protecting your API ecosystem.




