Best Rapid7 Alternatives and Competitors
Discover the 10 best Rapid7 alternatives and competitors in 2025 to improve your cybersecurity and threat detection.

Kruti
Jan 21, 2025
APIs allow seamless communication between applications and services. As these integrations become more widespread, the risks connected with insecure APIs increase. Organizations need advanced techniques to protect sensitive data, prevent illegal access, and comply with regulatory requirements.
Rapid7 is an API security platform that provides features including real-time threat detection, comprehensive behavior analytics, and automated incident response. Security engineers use it to detect vulnerabilities, assume risks, and protect organizational information from new threats.
This blog covers the 10 best alternatives to Rapid7. It gives details about various alternatives to Rapid7 and helps organizations find the right solution that meets their requirements.
Top 10 Rapid7 Competitors
Rapid7 provides complete protection for security needs. Organizations can check and compare these alternatives based on their features. Here are the top 10 competitors of Rapid7 :
1. Akto
Akto is an API security platform that defends API endpoints with precision and efficiency, making it a top rapid7 alternative. It smoothly connects with CI/CD pipelines and focuses on real-time monitoring, which makes it a popular choice among modern organizations. Akto makes the complex job of protecting APIs against ever-evolving risks easier by making use of AI-driven insights and automating compliance.
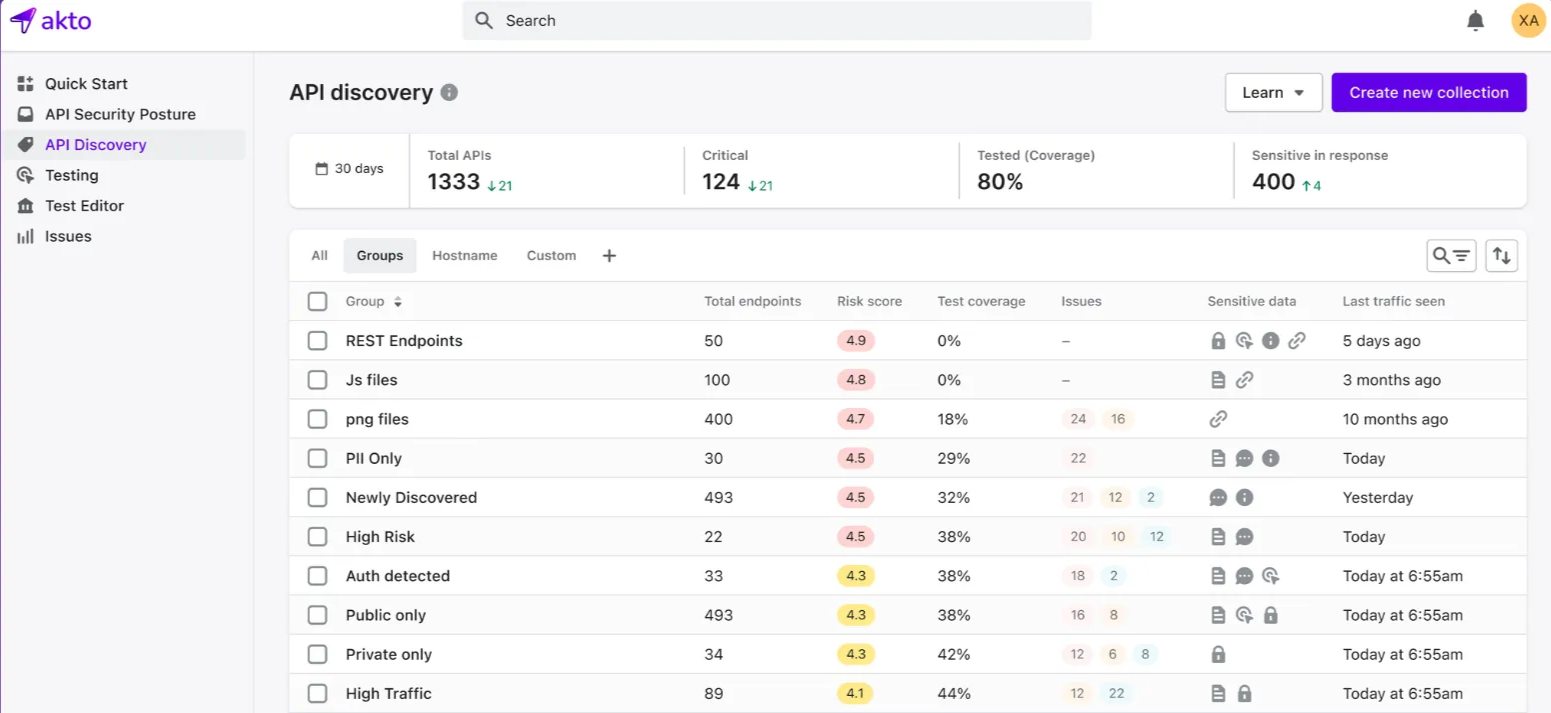
Features of Akto
Continuous API Vulnerability Scanning: Akto scans API vulnerabilities continuously to detect and resolve possible threats regularly.
Role-Based Access Control (RBAC): It uses role-based access control to ensure the user's permission is aligned with their responsibilities.
Threat Detection: It utilizes AI-based solutions to detect abnormal patterns of API traffic, which can, in turn, prevent the attack.
Adherence Reporting: Akto generates reports to meet reporting requirements.
Deep Threat Analysis: It delivers insights on security issues to allow proper remediation.
Advantages of Akto
Real-Time Monitoring: Provides constant visibility into API security.
Enterprise-Grade Scalability: Meets the demands of increasing infrastructures.
CI/CD Integration: Easily connects with DevOps operations.
User-Friendly Interface: Makes API security administration easier with intuitive tools.
Frequent Updates: Respond to emerging threats with regular feature updates.
Best For: It is for those organizations in need of an API security solution that regularly scans, easily connects to business processes, and helps in vulnerability management, Akto is best rapid7 alternative.
2. Qualys
Qualys is a complete cloud-based security platform that provides solutions for vulnerability management, API security, and compliance. It provides a flexible and centralized approach and is used by organizations of all sizes. Qualys threat intelligence and sophisticated automation tools make it smoother to manage complex security setups.
Source - Qualys
Features of Qualys
Complete Vulnerability Management: Identifies and prioritizes threats in all digital assets, including APIs.
Cloud-Based Architecture: Ensures easy deployment and scalability.
Automated Compliance Checks: Validate configurations against industry requirements.
Scalable API Monitoring: Adapts to the security requirements of dynamic infrastructures.
Global Threat Intelligence: It provides actionable data to fight emerging threats.
Advantages of Qualys
Centralized Dashboard: It provides a uniform view of assets and security risks.
Real-Time Threat Detection: It detects vulnerabilities as they emerge.
Wide Integration Capabilities: It supports many third-party solutions.
Highly Scalable: Supports organizations with various infrastructure complexity.
Automated Reporting: It reduces manual effort in the area of compliance and threat management.
Disadvantages of Qualys
Complex Initial Setup: Configuration could demand more efforts and skills.
Expensive: Pricing can be very costly for smaller organizations.
Hard to Learn: Complex functions are hard to understand.
Best For: It is for organizations looking for the best rapid7 alternatives that provide a full security platform, including flexible and centralized vulnerability management and automated compliance features.
3. Tenable
Tenable is a vulnerability monitoring and cyber-security solution that offers full support for APIs, network security, and broader IT architecture. Tenable provides robust technology and allows security professionals to assess and manage the attack surface as well as fix problems.
Source - Tenable
Features of Tenable
Comprehensive Cyber Exposure Analysis: Mapping and quantifying organizational threats.
API Security Integration: Provides API integration to enhance security workflows and extend coverage across the attack surface.
Real-Time Threat Insights: Delivers timely and actionable threat insights to help reduce risks effectively.
Supports Various Environments: Supports hybrid, cloud, and on-premises environments.
Follows Compliance Rules: Follows security rules to industry regulations.
Advantages of Tenable
Deep Risk Assessment Tools: It gives complete information on vulnerabilities.
Multi-Environment Support: It supports cloud, hybrid, and on-premise environments.
Customizable Reporting: Customizes findings to address specific organizational needs.
Regular Resolves Threats: It provides tools for solving problems before they grow.
Smooth Integration: Organizations can easily integrate it into different security applications, making it a Rapid7 alternative.
Disadvantages of Tenable
Complex Interface: The rich feature interface could be a steeper learning curve for first-time users.
Expensive Licensing: Pricing may exceed the budget for smaller organizations
Best For: It suits organizations that want a vulnerability management solution with deeper risk assessment compatibility with several applications.
4. Fortinet
Fortinet is a cybersecurity platform that includes network security, endpoint protection and the cloud security technology. Fortinet is known for its FortiGate firewall series, which provides robust and versatile protection against current threats, providing secure organizational operations across a wide range of environments.
Source - Fortinet
Features of Fortinet
Next-Generation Firewalls: Advanced firewalls that combine threat intelligence with application control.
Unified Threat Management: Implements antivirus, anti-malware, and intrusion prevention technologies.
Cloud Protection: Ensures full protection for multi-cloud and hybrid cloud environments.
Zero Trust Access: Allows secure access for all users, devices, and applications.
AI-Powered Threat Detection: Regularly detects and reduces risks using artificial intelligence.
Advantages of Fortinet
Complete Security Suite: Checks various areas of network and application security.
Flexible: Provides solutions for organizations of all sizes, including SMBs and corporations.
Performance: Rapid threat detection with minimum impact on network performance.
Integrates Easily: smoothly with third-party products and systems.
Worldwide Support: Provides complete documentation and a strong customer support network.
Disadvantages of Fortinet
Complex for Beginners: Some features may need technical skills during configuration which may be hard for beginners.
Pricing: Premium products and enterprise solutions can be costly.
Complex Interface: Beginners may find the UI (user interface) overwhelming.
Best For: Fortinet is for organizations which looking for the best rapid7 alternative and need a complete cybersecurity solution, especially those with complicated network infrastructures. It is for organizations that require advanced threat detection and protection.
5. Veracode
Veracode secures software through static, dynamic, and interactive testing on its application security platform, making it one of the top 10 Rapid7 alternatives and competitors. It gives developers and security teams the tools they need to detect vulnerabilities early and maintain secure coding standards throughout the development lifecycle.
Source - Veracode
Features of Veracode
Static Application Security Testing (SAST): Detects flaws in source code during development.
Dynamic Application Security Testing (DAST): Scans running programs for runtime vulnerabilities.
Software Composition Analysis (SCA): Evaluates the hazards associated with third-party and open-source libraries.
Secure Coding Training: It provides materials to assist developers in implementing secure coding methods.
Detailed Analytics: Provides actionable insights for ongoing security improvements.
Advantages of Veracode
Comprehensive Testing: It includes various methods of application security testing.
Easy for Developers: Integrates with all popular development tools and workflows.
Flexible: Appropriate for organizations of any size and level of complexity.
Detailed Reporting: Provides more accurate information to help with decision-making.
Strong Community Support: Includes full documentation and forums.
Disadvantages of Veracode
Pricing: Expensive for smaller organizations and startups.
Learning Curve: Certain features take time to learn.
False Positives: Can occasionally flag issues that are not actual vulnerabilities.
Best For: Veracode is ideal for organizations searching for rapid7 alternatives and competitors that prioritize safe software development and DevSecOps methods. Banking and healthcare organizations that must follow strict adherence standards will benefit most from this solution.
6. CheckMarx
Checkmarx is a security solution that protects APIs in every phase of the software development lifecycle. It offers complete testing tools and integrates easily with CI/CD pipelines that allow secure and efficient development.
Source - CheckMarx
Features of Checkmarx
Static Code Analysis (SCA): Identifies vulnerabilities in codebases early in development.
Interactive Application Security Testing (IAST): It combines runtime and static analysis to deliver accurate results.
Open-Source Analysis: Scans open-source components for possible vulnerabilities.
Developer Collaboration Tools: Aids developers and security teams to collaborate better.
Advantages of Checkmarx
Early Detection: Identifies weaknesses early in the development process.
Easy Integration: Integrate with the major development tools or platforms easily.
Easy for Developers: Dedicated to enhancing coding skills through training and support.
Scalable Solutions: It is suitable for both small teams and large organizations.
Actionable Insights: It provides specific recommendations for remediation of vulnerabilities.
Disadvantages of Checkmarx
Costly: Smaller teams may consider it too expensive.
Setup Complexity: The first configuration might be difficult for non-technical users.
Performance Impact: Large codebases may take longer to analyze.
Best For: Checkmarx is one of the best alternatives to Rapid7 for organizations focused on secure code development and looking for seamless integration with their DevSecOps pipelines.
7. Invicti
Invicti previously known as Netsparker is a web application security solution and help organizations to protect web applications and APIs by using both interactive and dynamic testing.
Source - Invicti
Features of Invicti
Automated Vulnerability Scanning: Scans for SQL injection and XSS vulnerabilities among others.
Deep Reporting: Provides comprehensive reports usable in security and compliance audits.
Connects with CI/CD Pipelines: Instantly connects to development workflows for automated testing.
Multi-Platform Support: Security for online applications in multiple environments.
Advantages of Invicti
Accuracy: Proof-based scanning ensures accuracy and avoids false positives.
Flexible: Changes according to organizations with various needs and complex environments.
Time-Saving: Saves time by successfully automating repetitive scanning activities.
Strong API Security: Protects APIs from modern threats.
Disadvantages of Invicti
Cost: Advanced features might be costly for smaller teams.
Limited Offline Features: Rely heavily on cloud-based functions.
Customization: There is limited flexibility in personalizing scans.
Best For: Invicti is ideal for organizations that want accurate and automated web application security testing. It is especially advantageous for teams that want a Rapid7 alternative and want to include security in their development operations.
8. Burp Suite
Burp Suite serves as a leading online application security platform and leads as a top alternative to Rapid7. Security professionals and developers use it for penetration testing, vulnerability assessments, and online application security.
Source - Burp Suite
Features of BurpSuite
Web Vulnerability Scanning: Detects important weaknesses like SQL injection and cross-site scripting.
Penetration Testing Tools: Supports both manual and automated penetration testing.
Customizable Extensions: Allows organizations to create plugins that provide additional functionality.
Collaborative Features: Encourages teamwork among security and development professionals.
Detailed Reporting: Provides deep analysis and recommendations for improvement.
Advantages of BurpSuite
Trusted Tool: Security testing professionals throughout the world use it
Community Support: A large user base with several resources and forums.
Regular Updates: Provides regular updates on new features.
Disadvantages of BurpSuite
Hard to Learn: Starting out may be difficult for beginners.
Cost: Premium features might be costly.
Resource-intensive: Extensive testing may reduce system performance.
Best For: Burp Suite is for security professionals and organizations that perform strict penetration testing and vulnerability analysis.
9. Black Duck
Black Duck offers software composition analysis (SCA) and identifies vulnerabilities to ensure license compliance in open-source components, making it a leading Rapid7 alternative. It allows organizations to protect their codebases while adhering to legal and regulatory constraints.
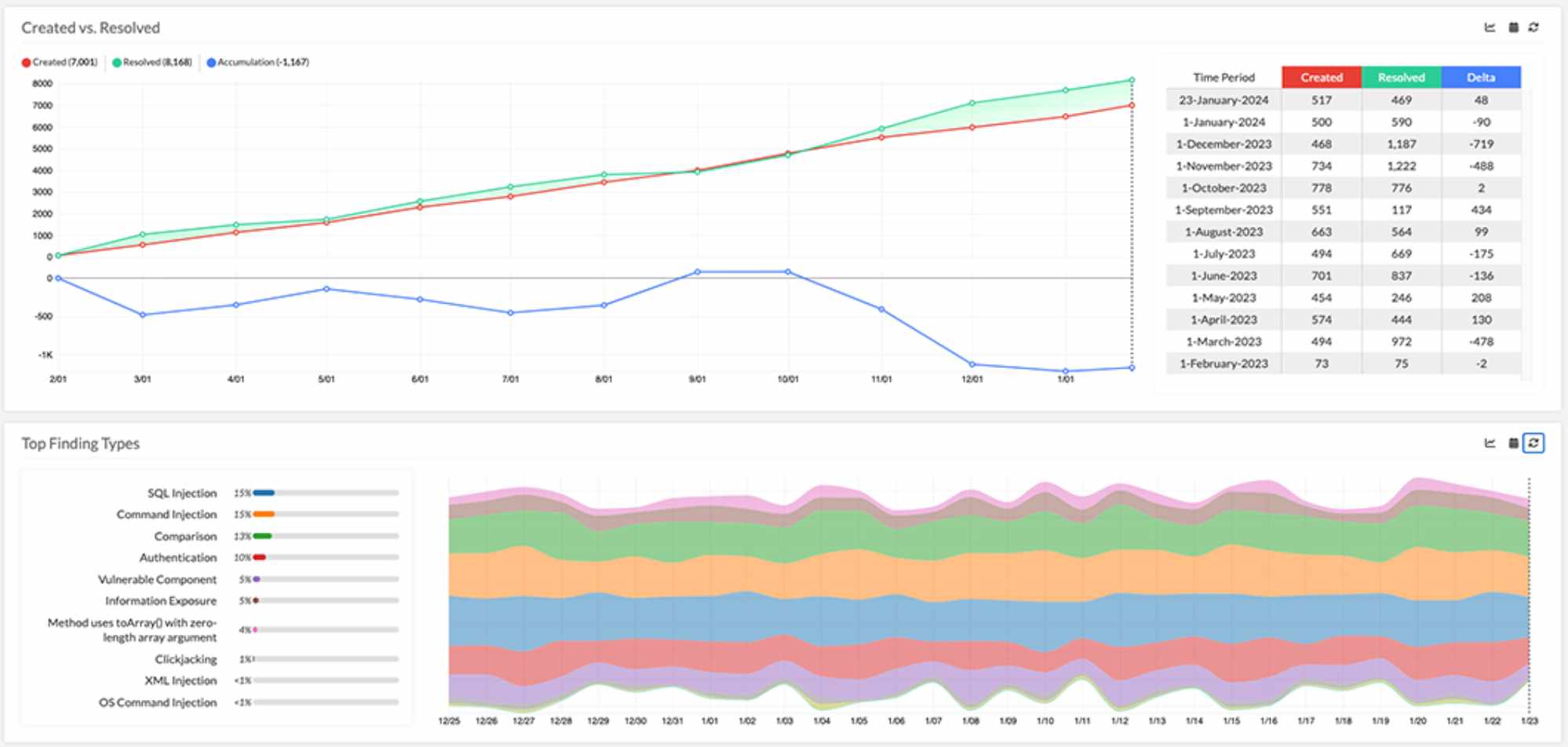
Source - Black Duck
Features of Black Duck
Open Source Vulnerability Scanning: It identifies potential third-party libraries and dependencies risks.
Adherence Rules: Implements adherence to open-source licensing obligations.
Policy Management: Allows the creation of custom security and licensing policies.
Integration with CI/CD: It integrates seamlessly and automatically performs scans during the development process.
Deep Reporting: Provides deep insights into risks and preventive methods.
Advantages of the Black Duck
Adherence Assistance: Follows legal and regulatory adherence rules.
Flexible: Applicable to both small and big organizations.
Friendly for Developers: It is easy for developers to combine easily with development procedures.
Deep Insights: Gives specific recommendations for dealing with vulnerabilities and licensing issues.
Disadvantages of Black Duck
Cost: Premium features might be costly for smaller organizations.
Complexity: Some technical knowledge is required to properly set up.
False Positives: Occasionally detects less important faults.
Best For: Black Duck is the top rapid7 alternative and competitor for organizations that use open-source components in software development. It is for organizations with stringent adherence criteria and a focus on decreasing security concerns.
10. ManageEngine
ManageEngine actively monitors operations, protects APIs, and delivers comprehensive IT management tools with API security features. It is a cost-effective alternative for small and medium-sized organizations.
Source - ManageEngine
Features of ManageEngine
Integrated IT Management: Provides solutions for managing IT operations and security.
API Traffic Analysis: Monitors API interactions to detect suspicious activity.
Patch Management: Keeps systems up to date with the newest security updates.
Customizable Dashboards: Offers customizable views for monitoring and analysis.
Advantages of ManageEngine
Cost-Effective Solutions: Provides affordable tools to SMBs.
Complete Services: Provides complete IT operations and security management solutions.
Simple Interface: Simplifies management with a simple dashboard.
Regular Updates: Ensure that tools are still relevant to new issues.
Customizable Features: Adjusts to specific organizational needs.
Disadvantages of ManageEngine
Limited Advanced Features: Larger organizations will miss out on some high-end features.
Focus on Small and Medium-Sized Organizations: Large organizations may struggle to scale.
Configuration Takes Time: The initial setup might be time-consuming.
Best For: MangeEgine is perfect for small to medium-sized organizations seeking a rapid7 alternative that is a cost-effective, integrated solution for IT management and API security.
How to Choose the Best API Security Solution
Selecting an API security solution is important to protect private information and allow to connect easily with an organization's digital ecosystem. With so many options, organizations should identify key factors to help them make the right decision for their specific needs.
1. Adaptable
As organizations grow, API security needs are complex. An API security solution must handle growing data volumes, manage increasing user access, and adapt to infrastructure changes. The platform has to be flexible and adapt to new APIs or endpoints by protecting APIs without impacting the operations. Flexibility is important to keep the security measures effective while allowing the growth of the organization and making the digital ecosystems dynamic.
2. Connect With Existing Systems
A top 10 rapid7 alternative and competitor solutions should combine easily with all the systems like CI/CD pipelines, identity management tools, and threat intelligence platforms. Effective integration increases efficiency by streamlining procedures and reducing disturbance during installation. Choose solutions that include pre-built interfaces and compatibility with existing tools to reduce time while also ensuring that security protocols are consistent with organizational processes.
3. Real-Time Threat Detection and Response
Proactive API security necessitates ongoing monitoring and immediate response to threats. Solutions that combine regular threat detection, machine learning algorithms, and automated fixation methods are essential for quickly fixing vulnerabilities. These features enable organizations to reduce threats before they escalate, resulting in a secure digital environment.
4. Compliance and Regulatory Support
Organizations in regulated industries must comply with specialized security standards such as GDPR, HIPAA, and PCI-DSS. Automated reporting and adherence standards in API security solutions streamline compliance requirements. Integrated compliance technologies help organizations avoid risks, save manual workload, and protect their reputation.
5. Cost-Effectiveness and ROI
Budget limits necessitate a compromise between comprehensive functionality and affordability. When considering rapid7 alternative, factor in the total cost of ownership, which includes license, implementation, and continuing maintenance. Solutions that deliver long-term value while remaining within the organization give a high return on investment.
Final Thoughts
Rapid7 Security is a strong API security platform that offers complete threat detection, vulnerability management, and compliance features. However, organizations look for solutions that are better suited to their needs, scalability requirements, or budgets. Rapid7 alternatives offer a variety of capabilities, integrations, and specific skills. It enables organizations to choose security solutions that fit their needs.
Akto is designed specifically for current API ecosystems, offering real-time threat detection, seamless interaction with CI/CD pipelines, and AI-powered insights for proactive protection. Its user-friendly interface, scalability, and focus on API-specific vulnerabilities make it an excellent solution for organizations that value API security. Akto enables security engineers to stay ahead of changing threats while keeping workflows efficient.
Ready to see how Akto can elevate the API security strategy? Schedule a demo today.
