Best Traceable Alternatives and Competitors
Discover the best Traceable alternative in 2025 to enhance your API security and protect against threats and vulnerabilities.

Kruti
Jan 24, 2025
APIs make organizations vulnerable to security risks such as data leaks, API abuse, and logic-based attacks. As organizations use APIs they have to handle sensitive data and use advanced security solutions to reduce threats, ensure regulatory compliance, and maintain user trust.
Traceable API Security excels in offering AI-driven insights and real-time threat detection. Leveraging Traceable’s features, like API Security Data Lake, provides comprehensive visibility, analyzing every API transaction for vulnerabilities and risks. Other features like automated API discovery, user behavior analytics, and compliance support make it a trusted solution for organizations to protect their digital ecosystems.
This blog talks about top Traceable API Security alternatives and helps organizations choose platforms that match their requirements, budgets, and goals.
Top 10 Traceable Security Competitors
Here are the top competitors to Traceable API Security with each offering strong solutions to protect the APIs.
1. Akto API
Akto is an API security platform that finds hidden risks, vulnerabilities, and misconfigurations across an organization’s API landscape. They also offer an automatic API discovery tool to monitor API traffic regularly. Akto focuses on behavioral risk analysis and gives deep insights into API behavior and attack vectors.
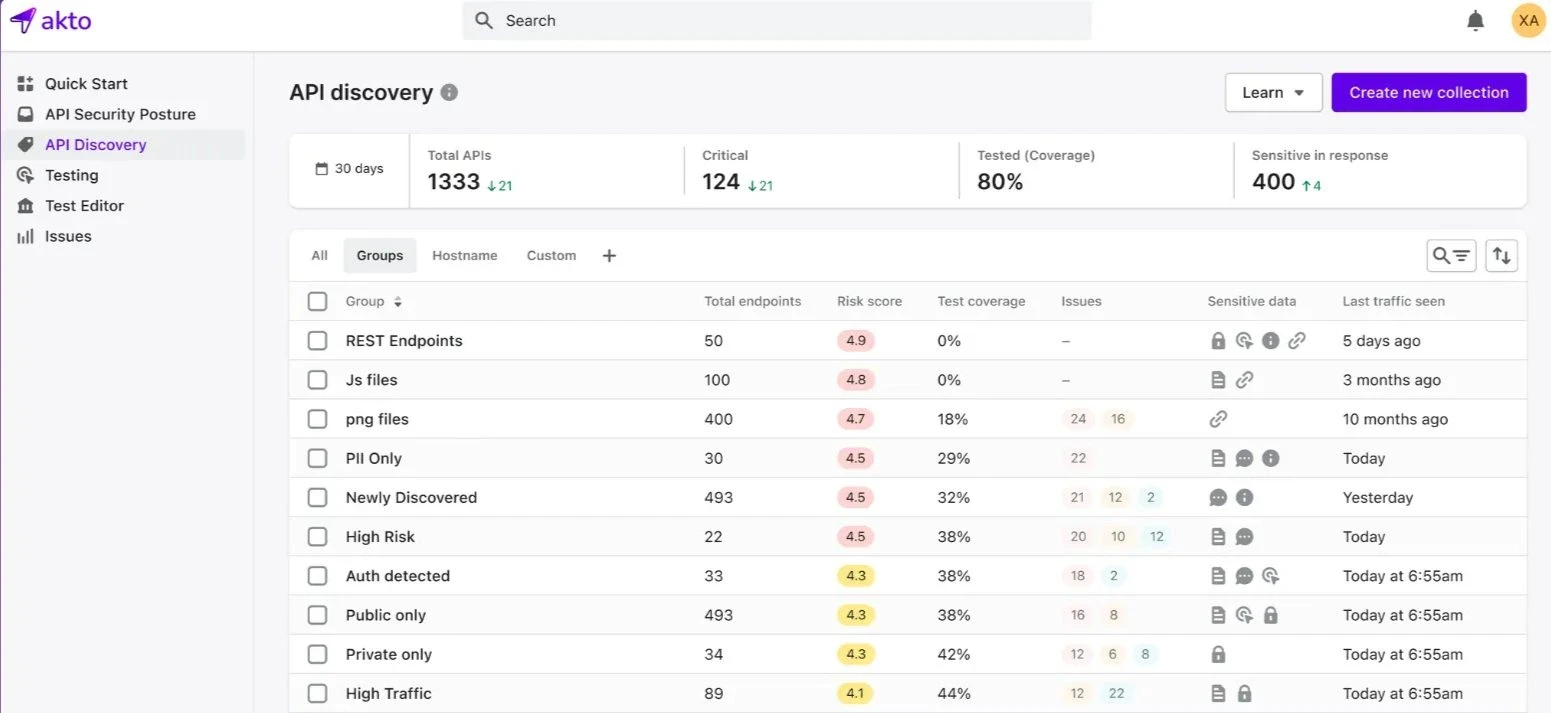
Features of Akto API
API Discovery: Akto provides complete API discovery and finds both documented and undocumented.
Detects API Vulnerability: Akto helps find common API vulnerabilities such as incorrect access control, data exposure, and installation issues.
Largest API Security Test Library Database: Akto provides one of the most extensive API security test libraries, covering issues like open redirects, SQL injection, and command injection.
Connects with CI/CD Pipeline: Akto connects easily with CI/CD pipelines by detecting vulnerabilities automatically and providing deep reports.
Advantages of Akto API
Akto protects both internal and external APIs, including third-party services by protecting complex ecosystems.
The platform allows to monitor APIs regularly by allowing security teams to respond to threats quickly.
Akto is designed for big organizations with extensive API systems that require automatic vulnerability discovery.
Best For: Big organizations with large API ecosystems and need to perform continuous monitoring and risk analysis of both internal and external APIs.
2. Akamai API Security
Akamai is a security solution based on the cloud. It offers complete solutions to protect APIs, websites, and applications. It is known for its content delivery network (CDN), which effortlessly works with its other features, like API protection against cyber-attacks and DDoS threats.
Source - Akamai
Features of Akamai API Security:
Advanced Threat Detection: Akamai uses machine learning techniques to find and reduce attacks on APIs.
API Firewall: Provides an API-specific firewall that helps filter out malicious traffic.
Behavioral Analytics: Akamai’s solution uses behavior-based analysis to detect irregular patterns in API usage.
Advantages of Akamai API Security
Akamai’s extensive CDN and global presence ensure that API traffic is protected from threats at scale, regardless of location.
It offers a multi-layered defense strategy, including real-time traffic analysis, DDoS protection, and web application firewall (WAF) capabilities.
Disadvantages of Akamai API Security
Akamai’s security offerings can be complex to use and manage, especially for smaller teams or businesses without a dedicated security team.
Small to medium-sized businesses may find it expensive, particularly for complete API protection.
Best For: Big organizations with high API traffic or those seeking flexible security that match with their overall web and app security environment.
3. Cloudflare
Cloudflare is a well-known provider of performance and security solutions for websites, APIs, and applications. It prioritizes attack prevention, ensures maximum uptime, and offers regular insights into API traffic.
Source - Cloudflare
Features of Cloudflare
Bot Mitigation: Cloudflare offers advanced mitigation features and helps to secure APIs.
Rate Limiting: Provides customizable rate limiting for API calls, preventing abuse and overuse of resources.
API Monitoring and Logging: Real-time monitoring and logging of API traffic to detect malicious behavior or unusual traffic patterns that could indicate an attack.
Advantages of Cloudflare
Cloudflare’s platform is known for its user-friendly interface and ease of integration into existing infrastructures.
It is suitable for organizations of all sizes, offering scalable solutions that grow with the organization’s needs.
Cloudflare leverages its large network to provide threat intelligence that helps in detecting and mitigating attacks globally.
Disadvantages of Cloudflare
While Cloudflare is excellent for general security, it might not have the same depth of API-specific features as specialized API security platforms.
Some features may be too expensive for smaller organizations.
Best For: Organizations looking for API protection with strong threat prevention and finding risks across various web applications.
4. Cequence Security
Cequence Security is an API security solution that focuses on finding and managing the risks associated with API traffic, particularly in complex multi-cloud environments.
Source - Cequence
Features of Cequence Security
API Protection: Cequence Security protects from these advanced attacks, such as authentication bypass, data leakage, and traffic anomalies, using its API protection.
Automated API Discovery: This will automatically discover APIs across on-premises and cloud environments to ensure visibility into all the attack surfaces.
Risk Detection and Management: It gives out detailed risk scoring and insights on API vulnerabilities that help security teams to prioritize issues based on the impact.
Advantages of Cequence Security
Cequence excels at real-time detection and mitigation, ensuring that APIs are secured against evolving threats.
It is for large organizations with complex API ecosystems and offers including third-party integrations.
Disadvantages of Cequence Security
The solution may require more effort to deploy across larger and more complex environments, especially if API architectures are not well-documented.
Some features need understanding to use them.
Best For: Large organizations with complex API architectures that need regular security and risk management.
5. APIsec
APIsec is an automatic API security testing platform that helps organizations find and reduce API weaknesses. APIsec makes sure that the APIs are secure in the software development lifecycle SDLC.
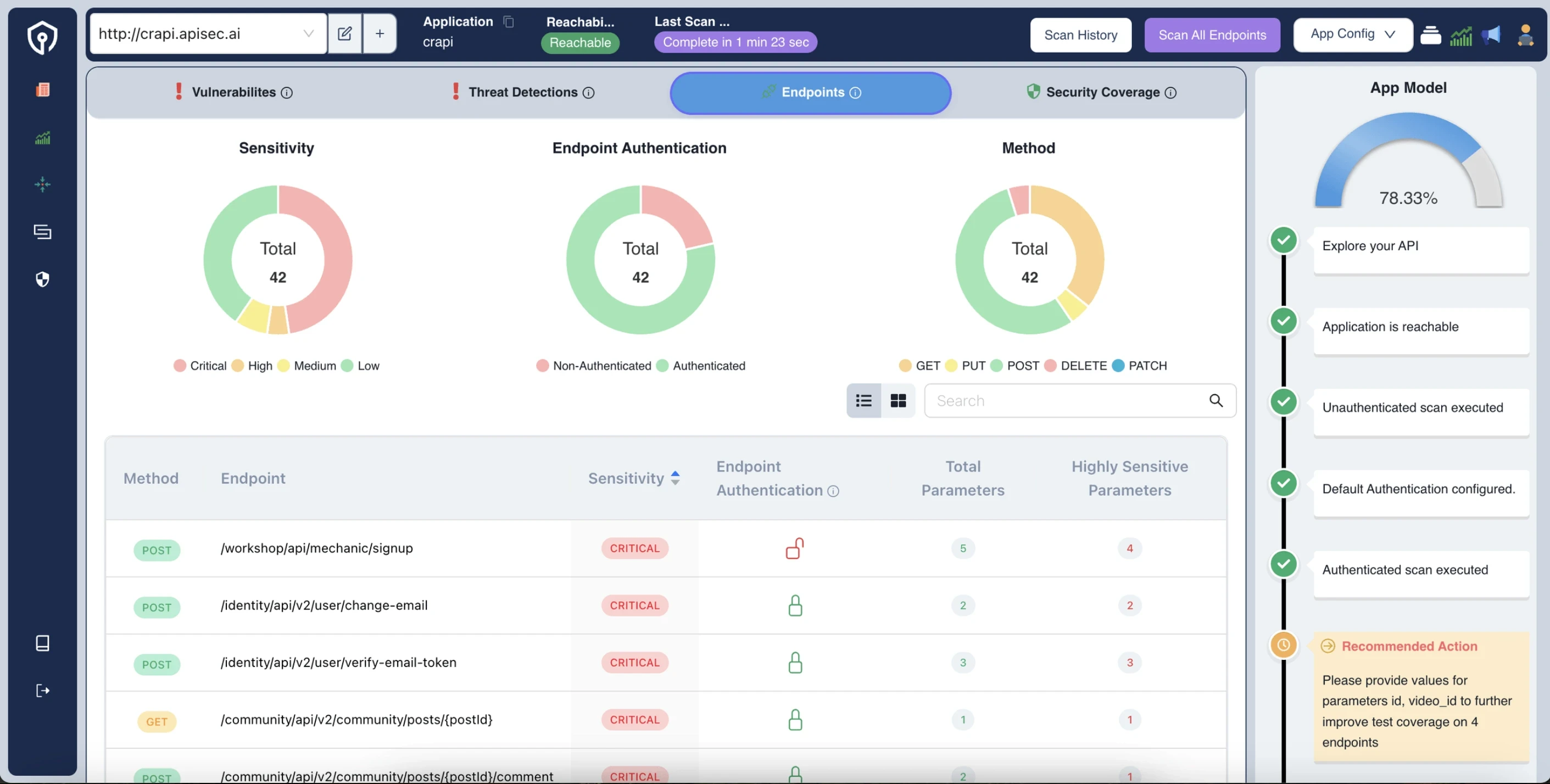
Source - APIsec
Features of APIsec
Automated Tests: APIsec carries out complete and automated security testing for identifying vulnerabilities, configuration errors, and security gaps.
Combines with DevOps Pipelines: Easy integration with the CI/CD pipeline which empowers security teams to test APIs regularly.
Flexible: Allows handling massive testing, thereby supporting organizations with high API volumes. Deep Reports: Gives deep reports along and fixation solutions.
Advantages of APIsec
Ensures vulnerabilities are found early in development by saving time and resources.
Minimal setup and maintenance and connects easily with automated workflows.
Works with various platforms to match various environments.
Disadvantages of APIsec
It lacks API management or monitoring features.
Some features might require training to use it fully.
Best For: Organizations looking for strong and automatic API security testing to connect to their SDLC processes.
6. Neosec
Neosec specializes in securing APIs through real-time behavioral analysis, helping organizations detect and respond to threats as they happen.
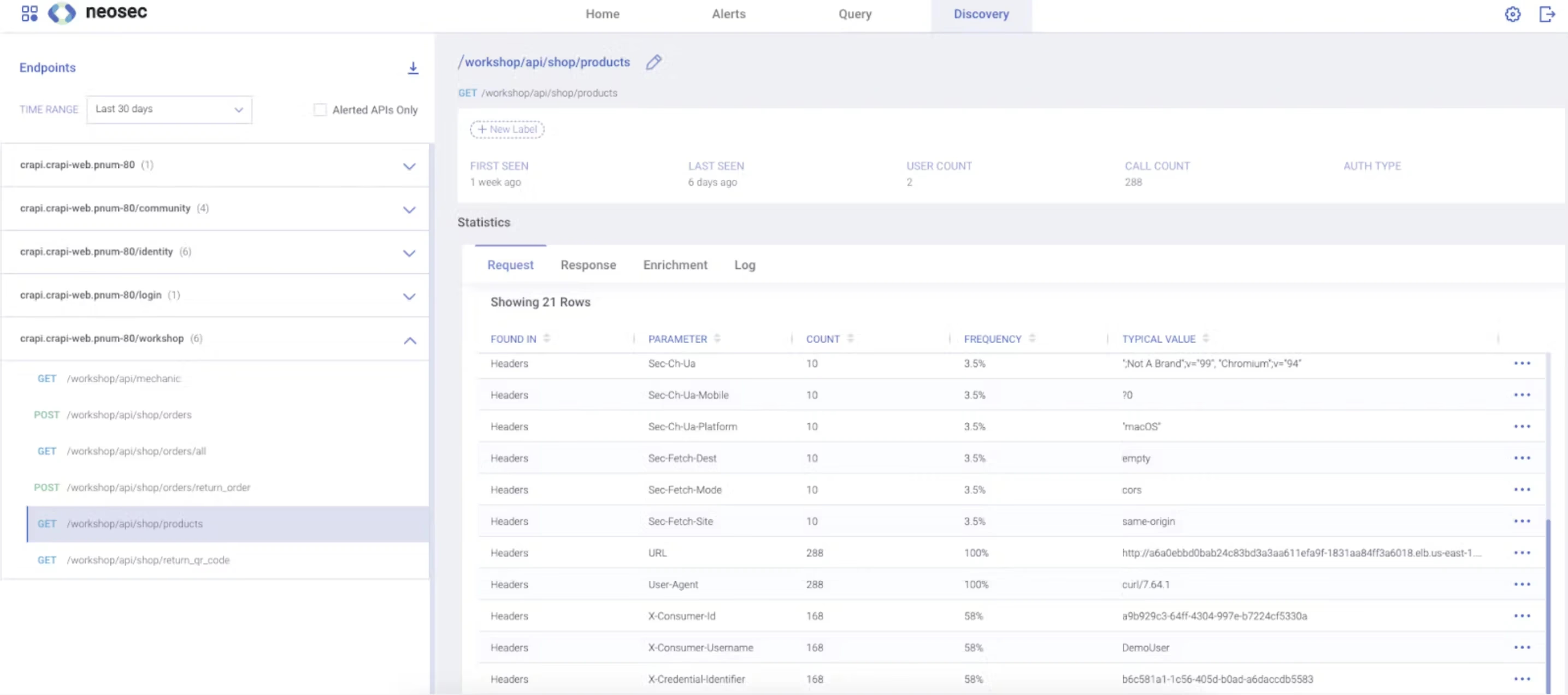
Source - Neosec
Features of Neosec
Behavioral API Protection: Neosec monitors API traffic patterns to detect irregular behaviors for possible threats.
Automated Risk Management: Automatically categorizes and prioritizes risks based on irregularities by allowing teams to fix high-priority vulnerabilities first.
Advantages of Neosec
Offers continuous monitoring of API traffic, ensuring instant threat detection and response.
Provides deep insights of risks by helping security teams to fix threats easily.
Disadvantages of Neosec
It is complex to setup and expensive for startups.
It lacks complete API management and lifecycle security features.
Best For: Large organizations with complex API environments that require real-time security monitoring and advanced behavioral analytics.
7. Salt Security
Security is one of the major API security companies, specializing in protecting APIs at scale through its AI-driven platform. The solution by the company uses machine learning to detect real-time threats and mitigate them for APIs before such attacks can happen. Salt Security is famous for its deep behavioral analysis and anomaly detection capabilities.
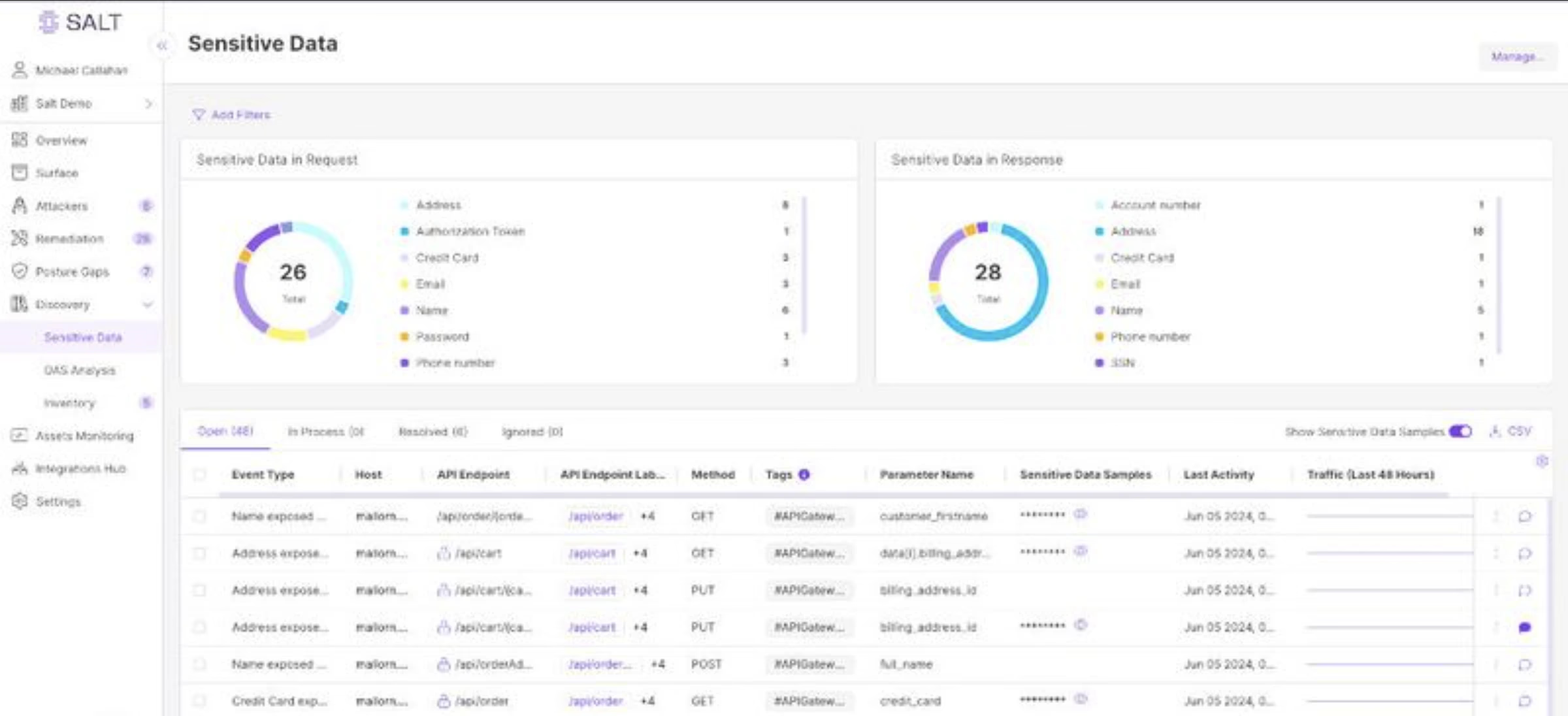
Source - Salt Security
Features of Salt Security
API Risk Identification: Salt employs AI for the identification of vulnerabilities and threats on the API through the assessment of traffic, user behaviors, and transaction patterns.
Real-Time Threat Detection: The platform provides real-time monitoring and automatically mitigates threats, including unauthorized access, data leakage, and other API-specific attacks.
Comprehensive API Protection: Salt Security includes a broad array of features, such as automated threat detection, risk management, and monitoring of both external and internal APIs.
Advantages of Salt Security
The AI engine can identify emerging threats, which reduces the time to detect and respond to attacks.
Salt Security’s proactive threat mitigation ensures that organizations are protected without needing manual intervention.
Designed for large-scale operations, Salt Security can manage complex, distributed API ecosystems.
Disadvantages of Salt Security
The solution may require extensive setup and integration with existing systems, especially for organizations with complex API environments.
Salt Security’s comprehensive features come at a higher price, which could be challenging for smaller organizations or startups.
Best For: Big organizations with complicated API setups that require strong AI-based threat solutions to identify and automatically lessen risks.
8. Wallarm
Wallarm is a security platform for APIs that protects APIs, microservices, and web apps against modern threats, including OWASP API Top 10 plus other malicious threats. This mainly focuses on automated processes with minimal manual configuration and offers high accuracy to the order of low errors.
Source - Wallarm
Features of Wallarm
API Discovery: Automatically identifies all APIs, including shadow and zombie APIs, by analyzing their usage.
Threat Prevention: Protects against API-specific vulnerabilities such as injection attacks, data leaks, and unauthorized access.
Incident Response: Provides regular threat visibility with alerts and automated incident management.
Focus on the Cloud: It supports environments like AWS, GCP, Azure, and IBM Cloud.
Advantages of Wallarm
Addresses a wide range of threats for various API protocols like REST, GraphQL, and SOAP.
Minimal installation requirements and easy connection with DevSecOps workflows.
Designed for large environments that need reliable API protection of their data.
Disadvantages of Wallarm
Its enterprise focus may make it less accessible for smaller businesses or simpler projects.
Some advanced capabilities may be cost-prohibitive for startups.
Best For: Organizations looking for robust, automated API security solutions tailored to cloud-native applications.
9. Apigee API Management
Apigee, now part of Google Cloud, is an enterprise API management leader that secures, manages, and monitors APIs. Apigee combines API security with developer tools and analytics that help organizations safely secure APIs without sacrificing high performance and scalability.
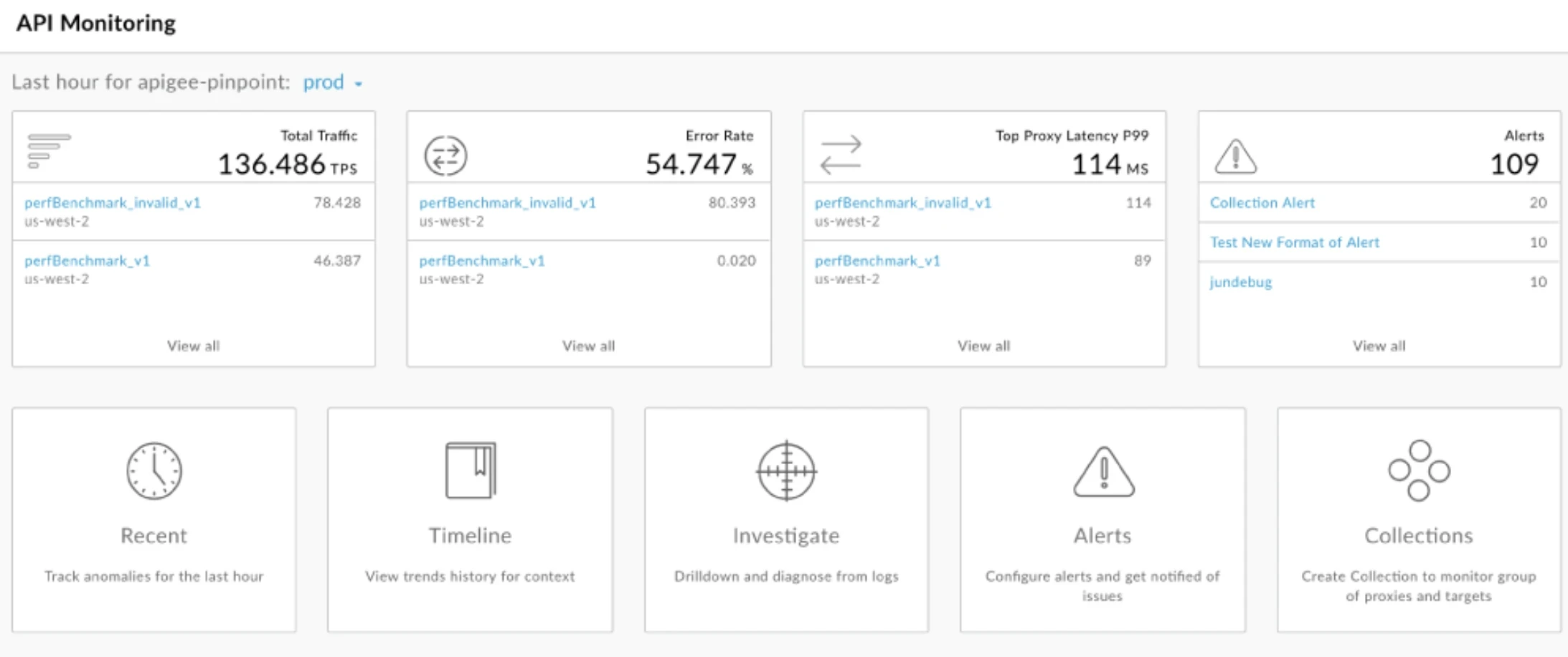
Source - Apigee
Features of Apigee API Management
API Gateway: Apigee’s API gateway manages API traffic and helps secure API calls through authentication and rate limiting.
Security Policies: It provides various security policies, which include OAuth, API management, and IP whitelisting, to guarantee secure access to APIs.
Analytics and Monitoring: Apigee provides deep insights of API performance and security by offering deep reports on usage, vulnerabilities, and possible attack attempts.
Advantages of Apigee API Management
Apigee excels not just at security but also at providing API lifecycle management, including design, monitoring, and version control.
As part of Google Cloud, Apigee provides enterprise-level scalability, which is ideal for large organizations that are handling vast amounts of API traffic.
Apigee integrates seamlessly with other Google Cloud services, offering a unified cloud security and management experience.
Disadvantages of Apigee API Management
Apigee’s advanced configuration and customization options may be difficult for teams without API management experience.
It is expensive for small to mid-sized organizations because of the costly premium features.
Best For: Big organizations that already use Google Cloud, or those looking for a complete API management solution with strong security features.
10. Imperva API
Imperva provides comprehensive API security as part of its larger application security suite. CloudVector boosted its API security capabilities by allowing it to get connected with the other tools available in the Imperva platform. Organizations can protect their data from unknown and known threats.
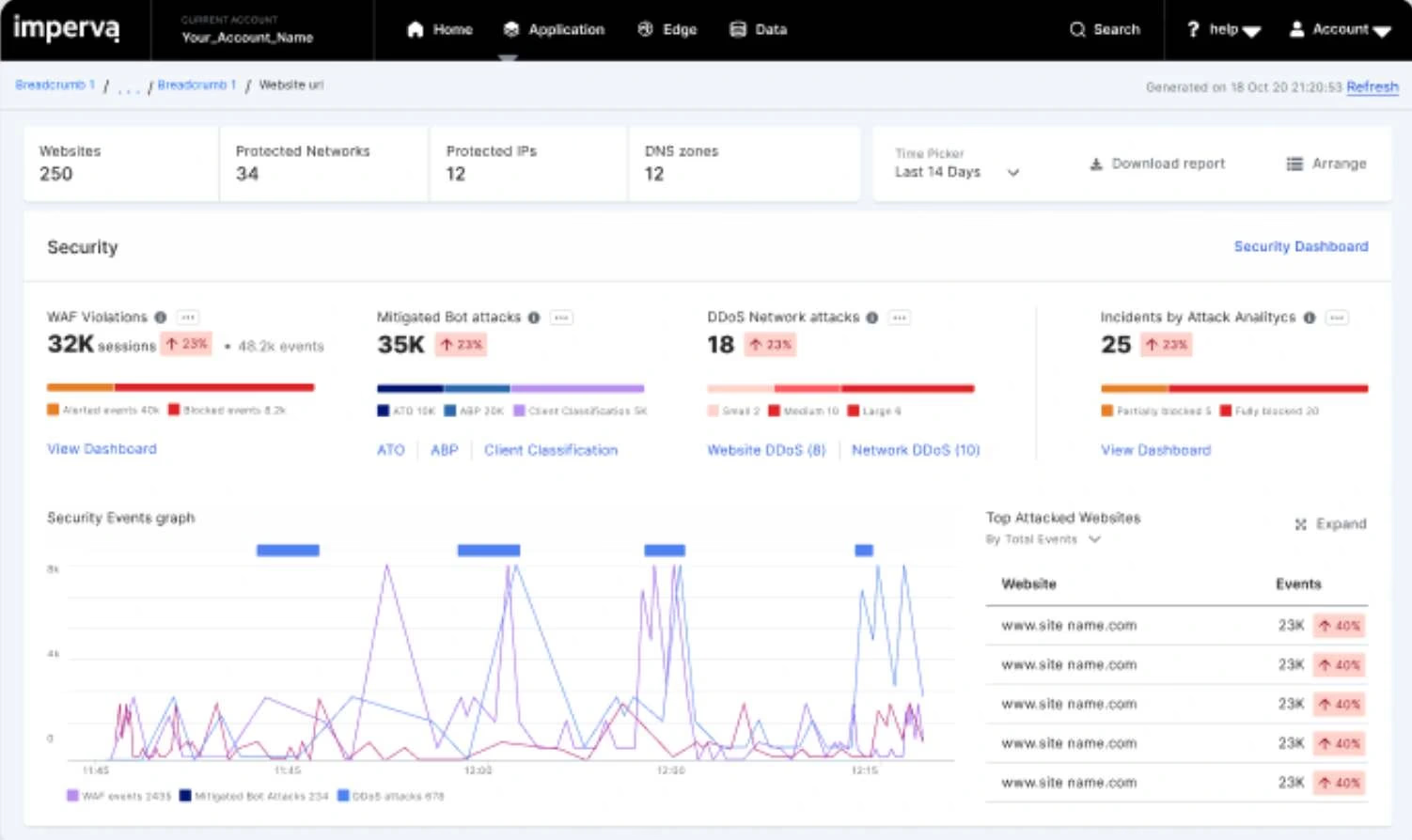
Source - Imperva
Features of Imperva API
Multiple Deployment Options: Offers cloud-managed security and the "API Anywhere" solution for on-premises or private cloud environments, allowing organizations to maintain control over their data while securing APIs.
Unified Application Security: Imperva API Security is fully combined with other Imperva products, including Web Application Firewall (WAF), DDoS protection, and Advanced Bot Protection (ABP).
Protection Against OWASP API Security Top 10: Imperva helps protect data from the top API vulnerabilities as identified by OWASP by enhancing threat detection and mitigation.
API Attack Analytics: Imperva's built-in analytics provide regular insights of API attacks by improving the security monitoring process.
Advantages of Imperva API
It connects easily with WAF, DDoS protection, and Bot Protection.
Whether an organization uses a public cloud, hybrid, or on-prem infrastructure, Imperva provides the flexibility needed for diverse environments.
Imperva's unified management makes it easy to find and handle various threats from one platform.
Disadvantages of Imperva API
Due to its broad feature set, smaller businesses might find it more complex than they need.
Some advanced features might be locked behind higher pricing tiers, which could be cost-prohibitive for smaller organizations.
Best for: Imperva is a medium and big organization looking for an API security solution that can easily connect with their workflows and protect them from vulnerabilities.
How to Choose the Best API Security Solution
In choosing an API security solution, organizations must weigh a number of factors to determine which platform best suits their size, growth trajectory, and security needs. Here's how to choose the best API security solution:
Understand API Security Needs
Before choosing the API security solution, organizations should know their needs and the challenges they are facing. First, create an overview of the API ecosystem, including the types of APIs used by organizations and their roles in operations. Check if these APIs are public or private because every API has different security threats. Checking the API landscape it will help to identify vulnerabilities and choose the right solutions to protect them.
Next, check the current security posture to find security gaps. Then, review all existing controls concerning authentication, authorization, encryption, and threat detection. Reflecting on previous occurrences or weaknesses identifies recurring issues while being mindful of requirements for type of industry compliance, including, for example, GDPR or HIPAA, the implemented solution needs to comply with this regulatory mandate.
Finally, think about flexibility and connection features. It should connect with current tools, CI/CD pipelines, and monitor systems. Match the solution with other organizational objectives by collaborating with stakeholders across the development and security teams to ensure full protection.
Check Features
As per security needs, organizations can evaluate features to ensure the solution aligns with their priorities. Some features to include:
Regular Threat Detection: Organisations with the most stringent operational environments in risk require real-time threat detection. Solutions like Salt Security and Traceable, driven by AI, analyze behaviour, detect anomalous behaviour, and block breaches even before they take place.
Ease of Use and Developer Friendly: Organizations should choose simple and easy-to-use solutions that automatically find and fix security problems.
Flexible: Organizations with increasing API traffic should select flexible systems. Choose platforms that provide API Management and connect with Google Cloud by allowing organizations to grow their API infrastructure without worrying about security vulnerabilities.
Deep Analysis and Reporting: Choose platforms that provide deep analysis and relevant reports of API usage and security risks.
Pricing
API security solutions differ depending on the size of the organization and the functionalities required. Smaller enterprises with fewer APIs should choose for inexpensive pricing. Some API security services provide cost-effective solutions allowing affordable protection without affecting budgets.
Scalability becomes increasingly important as organizations grow. Many solutions provide pricing structure that adjusts to changing requirements. While more expensive, these technologies provide support as organizations grow.
Big organizations will need strong platform that offers flexible pricing based on API count, users, or traffic volume. They should provide strong advanced protection features. Many platforms provide free trials, allowing organizations to test the platform before purchasing it and confirm it is the best fit for their security needs.
Final Thoughts
The size of the organizations, complexity of the API infrastructure, and specific security demands all influence the best API security solution for that organization. As organizations grow, they should choose flexible and developer-friendly platforms to match the growing API ecosystems.
Large organizations should invest in leading-edge, AI-based security software, such as Salt Security and Traceable, to be competitive in real-time threat detection along with behavioral analytics, which are essentials in large environments and complex system deployments where advanced security is absolutely needed to avoid penetration. To find the best API security solution, organizations should check these alternatives in detail. Among all the alternatives, Akto is strong, cost-effective, and flexible with various API security features. It will help organizations to boost the security of organizations. It connects easily with current workflows and has developer-friendly design. Schedule a demo to explore how Akto matches with the security needs.
