Best Wallarm Alternatives and Competitors
Check out the top 10 Wallarm alternatives and competitors to boost your API security and protection in 2025.

Kruti
Jan 16, 2025
APIs accelerate innovation and connectivity across industries. Organizations are exposed to vulnerabilities because of the increased dependence on APIs. Organizations need robust solutions to protect data, prevent breaches, and comply with regulations.
Wallarm Security is known for its real-time threat detection, behavior analytics, and adaptive threat defense. While its capabilities are amazing, organizations frequently look into alternatives to meet specific requirements. This blog discusses the top ten alternatives to Wallarm Security, providing organizations with information to help them choose the best solution for their needs.
Top 10 Wallarm Security Competitors
Here are the top 10 competitors of Wallarm to help organizations make informed decisions based on their unique needs.
1. Akto API Security
Akto is an API security platform that uses automatic algorithms to find APIs, examine traffic, and detect possible risks in real-time. Akto connects easily with existing systems and workflows which makes it ideal for organizations of all sizes.
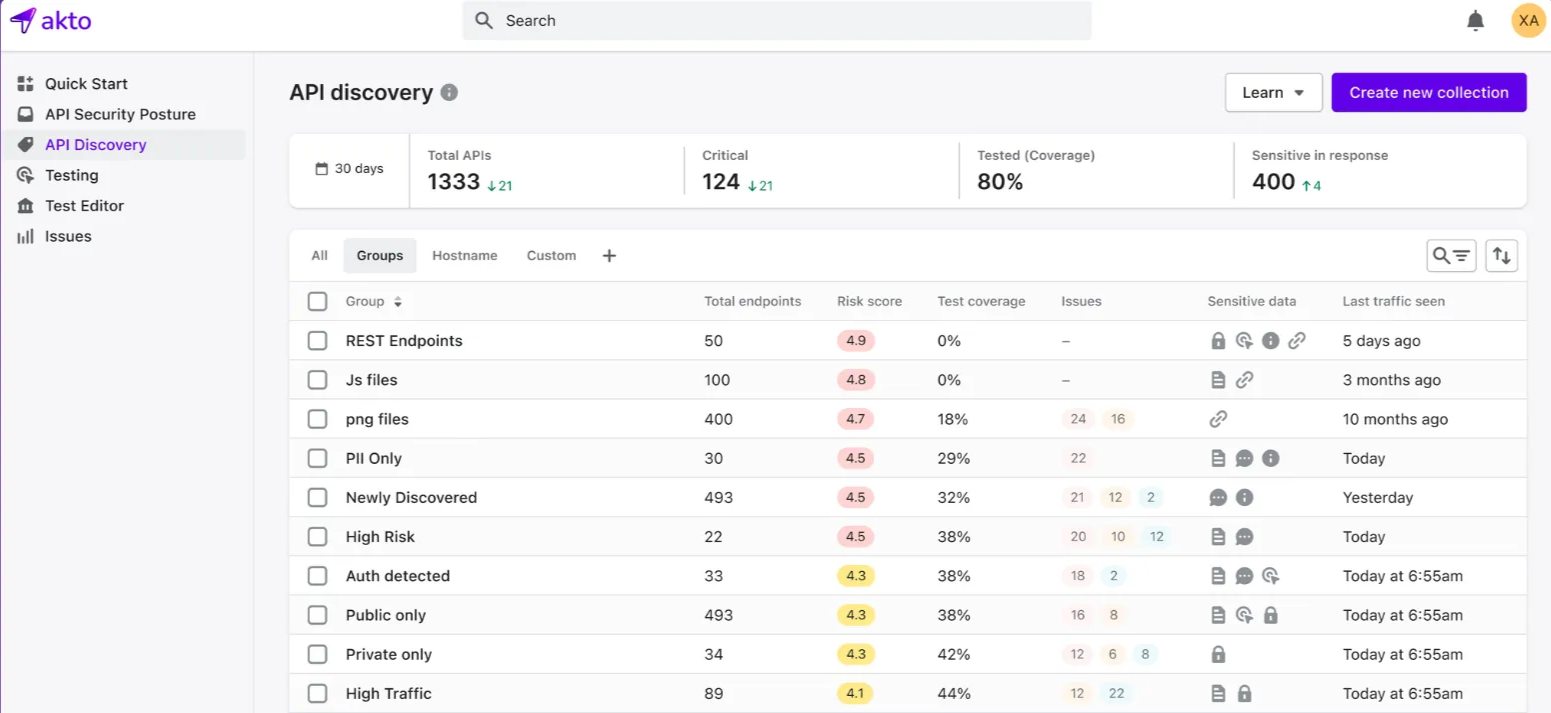
Source: Akto.io
Features Akto API Security
Automatic API Discovery: It automatically finds all APIs in the ecosystem.
Real-Time Threat Detection: It checks traffic in real-time to find and prevent security threats quickly.
Follows Adherence Rules: Follows compliance standards like GDPR, HIPAA, and PCI-DSS.
Alert System: Sends notifications in response to specific threats or actions.
DevSecOps Implementation: Easily integrates with CI/CD pipelines to provide smooth workflows.
Advantages of Akto API Security
Rapid Installation: Quick and simple installation that reduces setup time.
Scalable Solution: Easily changes according to different environments of different sizes.
Complete Protection: It provides API security in every phase, from development to production.
Affordable: It is less expensive than other platforms.
Best For
Akto is for organizations of all sizes that want an affordable solution and follow compliance rules. It easily connects in existing systems and focus on automating security processes while reducing expense.
2. Akamai Security
Akamai Security protects APIs in cloud settings. It is a solution that protects against DDoS attacks, malicious traffic, and other weaknesses. Akamai has a large Content Delivery Network (CDN) that reduces inactivity and provides strong protection.
Source: Akamai
Features of Akamai Security
Customized Security Policies: It provides customized policies to protect APIs and handle traffic.
Traffic Management: Detects and blocks harmful traffic before it can cause problems.
DDoS Protection: Shields APIs from distributed denial-of-service attacks, keeping them secure and available.
Real-Time Monitoring: Keeps an eye on API activity around the clock and responds instantly to threats.
Flexible Infrastructure: Akamai uses its vast CDN to ensure persuasive, fast, and secure API performance even with increasing traffic while maintaining network security.
Advantages of Akamai Security
High Performance: The global coverage by the CDN of Akamai guarantees that APIs function at their optimum with very minimal delays during high traffic.
Full Protection: Provides full protection against DDoS attacks, malicious traffic, and other security issues.
Flexible Security Policies: Organizations can set policies and edit them based on the needs of the organization.
Global Coverage: Multiple organizations around the world are users of Akamai’s infrastructure.
Disadvantages of Akamai Security
Expensive for Smaller Businesses: The price may stand as a huge hindrance for small to medium enterprises.
Challenging to Install: Due to a lack of skills and experience, sometimes the setup may take longer than anticipated.
Limited API-Related Data: Compared to other platforms, there is little insight available regarding APIs.
Best For
Akamai Security proves to be most appropriate for large organizations with an excessive amount of API traffic due to its proprietary DDoS protection. It ensures bot management while also optimizing performance. It uses a global infrastructure to ensure that the APIs are reliable and secure.
3. Imperva Security
Imperva Security provides complete security services, including API security, web application firewalls, and DDoS protection. It detects and reduces weaknesses by monitoring API activities for various threats.
Source: Imperva
Features of Imperva Security
Threat Detection: It uses machine learning to detect API risks.
Automatic Policy: This feature provides automatic threat mitigation policies.
Real-time Monitoring: Regularly monitors API traffic to detect any unusual activities.
Scalability: It works for large organization situations with a high number of API requests.
Advantages of Imperva Security
Strong Protection: Provides robust protection for high-value APIs.
Advanced Insights: Provides deep insights to improve threat intelligence.
DDoS Protection: Effective protection against automated DDoS attacks.
Policy Automation: Automated enforcement of security policies for greater efficiency.
High Availability: Uses a solid infrastructure to ensure minimal downtime.
Disadvantages of Imperva Security
Difficult Installation: Initial installation can be difficult which may affect configuration.
Expensive for Small Businesses: The pricing might be a little difficult for small businesses.
Not as Flexible: Less flexible than other API security platforms.
Best For
Imperva is meant for large enterprises that require strong, comprehensive API security comprising threat detection as well as bot management and DDoS mitigation. It provides customizable features to organizations with strong security requirements and a big volume of API traffic.
4. Cequence Security
Cequence Security is an API security solution that protects APIs, mobile apps, and websites. It uses AI and machine learning to continuously analyze API traffic for threats. It allows organizations to reduce their attack surface in real-time. It handles attacks, fraud, and data breaches for better performance of applications.
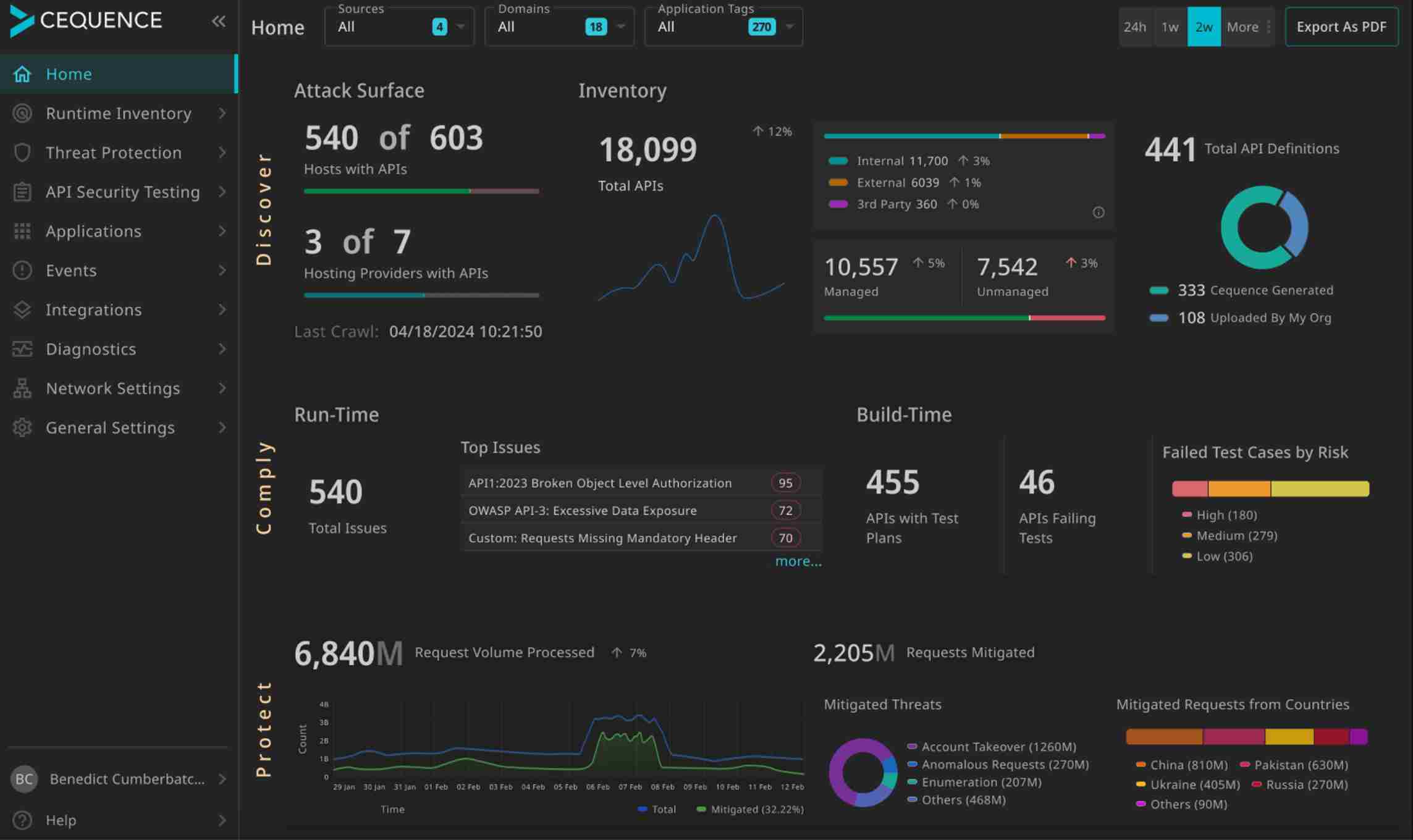
Source: Cequence
Features of Cequence Security
Threat Detection, AI-Powered: Real-Time Detection and Mitigation of Advanced Threats Using Artificial Intelligence
Bot and Credential Stuffing Protection: Discovers and stops hostile bot activities against APIs.
Behavioral Analytics: Monitors API traffic behavior to detect abnormalities and prevent attacks.
Detailed Insights: Provides in-depth information into API traffic and performance.
Automatic Risk Mitigation: Automatically reduces risk in response to growing risks.
Advantages of Cequence Security
Complete Protection: Offers full protection against bot management and fraud.
Customizable Policies: Allows customization of regulations to tailor security to API needs.
Low Latency: Designed to have a minimal impact on application performance.
Scalable: Suitable for both small and large organizations.
Disadvantages of Cequence Security
Complex Configuration: Requires initial setup and fine-tuning to maximize the system.
Cost: Startups may find it expensive.
Dependence on Artificial Intelligence: It highly depends on AI, which may overlook some of the most specialized threats that need to be checked.
Best For
Ideal for organizations who want an AI-powered solution to protect APIs against threats such as bot attacks, credential stuffing, and fraud. It is for organizations with high traffic and security needs that require real-time and automated protection.
5. AWS Web Application Firewall (WAF)
AWS WAF is for organizations that need to defend applications from online threats in order to maintain API security. It allows organizations to create their own security rules to protect APIs, websites, and applications hosted on AWS. AWS WAF connects easily with other AWS services so it is chosen by organizations that use the AWS ecosystem.
Source: AWS WAF
Features of AWS WAF
Customizable Web Security Rules: Allows the creation of security rules to protect APIs and applications.
Threat Control: Detects and minimizes threats.
Real-Time Monitoring: Gives information about traffic to identify malicious patterns.
Connects with AWS Services: Works smoothly with other AWS tools.
Advantages of AWS WAF
Easy Integration: AWS combines easily with organizations that use AWS as their primary cloud provider.
Inexpensive: Pricing is flexible and based on usage and the number of rules.
Flexible: Can handle heavy traffic and change workload without compromising performance.
Disadvantages of AWS WAF
Fewer Features: In comparison to other API security platforms, the security features are less advanced.
Dependence on AWS: It is dependent on AWS and lacks hybrid or multi-cloud deployment use cases.
Best For
AWS WAF is for organizations that already use AWS infrastructure and need a scalable, cost-effective API security solution to combat common web threats.
6. Prisma Cloud
Prisma Cloud is a complete cloud security platform that offers API security with many other capabilities. Prisma Cloud allows to check and control over API traffic while also defending against a variety of risks with improved threat intelligence and extensive integration with cloud environments.
Source: Prisma Cloud
Features of Prisma Cloud
API Security Monitoring: Regularly checks API traffic for suspicious activity.
Cloud-Native Integration: Works smoothly with cloud-native environments such as AWS, Azure, and Google Cloud.
Advanced Threat Detection: Uses machine learning and threat intelligence to detect complex attacks.
Compliance Automation: Assists in ensuring compliance with GDPR, PCI-DSS, and HIPAA regulations.
Risk Assessment: Identifies and addresses security issues throughout the API lifespan.
Advantages of Prisma Cloud
Comprehensive Cloud Security: provides end-to-end protection for cloud-based environments.
Deep Integration: Works smoothly with cloud infrastructure and services.
Advanced Threat Intelligence: Uses machine learning to detect and respond to developing threats.
Compliance Focus: Helps organizations in meeting their regulatory compliance requirements.
Granular Control: Provides smooth control over API security policies.
Disadvantages of Prisma Cloud
Difficult to Implement: Setup and configuration can be tough without experienced security professionals.
Expensive for Smaller Organizations: it may be costly for smaller businesses with less budget.
Additional Modules Required: Some functions are only available in membership.
Best For
Prisma Cloud is for large organizations with cloud-native designs that require robust security across APIs, infrastructure, and apps.
7. Signal Sciences
Signal Sciences provides an advanced online application security platform with API protection. It uses real-time monitoring and behavior-based threat detection to identify possible risks to APIs and other online services. Signal Sciences offers simple solutions with reliable API security without needing complex configurations.
Source: Signal Sciences
Features of Signal Sciences
Behavioral Threat Detection: Uses machine learning to detect and mitigate abnormal API behavior.
API Security Monitoring: Monitors API traffic for potential vulnerabilities and criminal activity.
Real-time Protection: Provides an immediate response to security risks.
DevOps Integration: Integrates seamlessly with DevOps procedures to ensure continuous security.
Customizable Rules: Enables the establishment of custom security policies for API traffic.
Advantages of Signal Sciences
Simple to implement: User-friendly interface and interoperability with existing systems.
Continuous Protection: Provides ongoing monitoring without interfering with API performance.
Disadvantages of Signal Sciences
Non-Web API Visibility: This may not give as thorough coverage for all API types.
Best For
Signal Sciences is for organizations that want a security solution that detects abnormal API behavior and is connected to DevOps setups. It is intended for teams seeking flexible API protection with few configuration needs.
8. Trustwave
Trustwave is a cybersecurity platform that offers a variety of security solutions including API security in web applications with API protection tools. Trustwave helps organizations in protecting APIs against vulnerabilities, threats and fraud.
Source: Trustwave
Features of Trustwave
API Protection with Threat Intelligence: Provides full API security through integrated threat intelligence.
Vulnerability Scanning: Detects and resolves vulnerabilities in APIs and apps.
24/7 Monitoring: Offers continuous monitoring to detect and neutralize risks in real-time.
Compliance Management: Assists organizations to meet industry-specific compliance rules.
Advanced Reporting: Provides full security reports to help organizations with auditing.
Advantages of Trustwave
Complete Security Solutions: Provides full protection in network security, endpoint protection, and more.
Expert Support: They provide a team of cybersecurity specialists for increased protection.
Compliance Rules: Follows compliance rules such as PCI-DSS, HIPAA, and GDPR.
Customizable Solutions: Customizes security services to meet the demands of specific organizations.
Disadvantages of Trustwave
Expensive: Small scale organizations may find it expensive.
Complex installation: The initial installation may need expert assistance.
Less API Focus: It lacks API security focus unlike other API security platforms.
Best For
Trustwave is for organizations that require a full cybersecurity solution with robust API security features. It's for organizations that need advanced threat protection and regulatory compliance.
9. Radware
Radware is a cybersecurity platform that protects APIs, web applications, and networks from malicious attacks. Radware is known for providing complete threat information and real-time attack mitigation. It protects sensitive data with machine learning and behavioral analytics. It is designed for organizations that want outstanding performance and strong security in current application architectures.
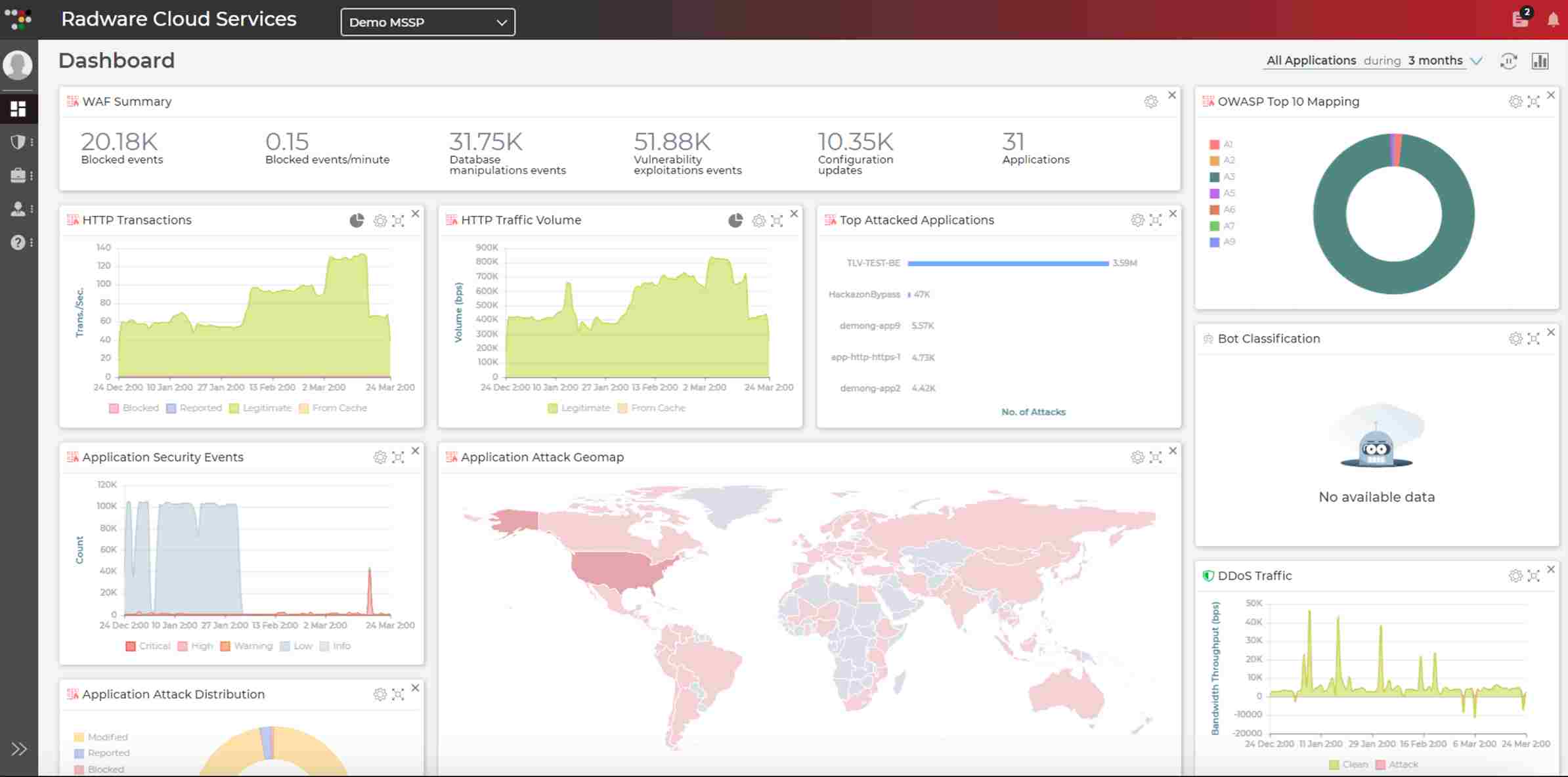
Source: Radware
Features of Radware
API Protection: Detects and mitigates API vulnerabilities in real-time, focusing on SQL injection and cross-site scripting.
DDoS Protection: Uses new features to reduce large-scale DDoS attacks.
Bot Management: Detects and prevents malicious bot traffic that targets APIs.
Behavioral Analytics: Detects abnormalities with machine learning and behavioral analytics.
Cloud-Native Security: Integrates easily with cloud environments, providing hybrid security solutions.
Advantages of Radware
Real-time Threat Detection: Provides immediate protection against API-related threats.
Deep Analysis: Provides behavioral analysis to detect threats.
Cloud and On-premises Flexibility: Supports cloud and on-premises environments.
Disadvantages of Radware
Complex Configuration: It can be time-consuming and requires security expertise.
Costly: Radware's solutions has higher subscription rate.
Best For
Radware is for big organizations with high API traffic and advanced security requirements. It provides organizations strong threat and DDoS protection that works in both cloud and on-premises environments.
10. Fortinet
Fortinet offers full cybersecurity solutions with security solutions, such as API protection with the FortiWeb Web Application Firewall. Fortinet combines complete insight into network traffic with advanced AI-driven threat detection and helps organizations secure APIs while mitigating various security issues.
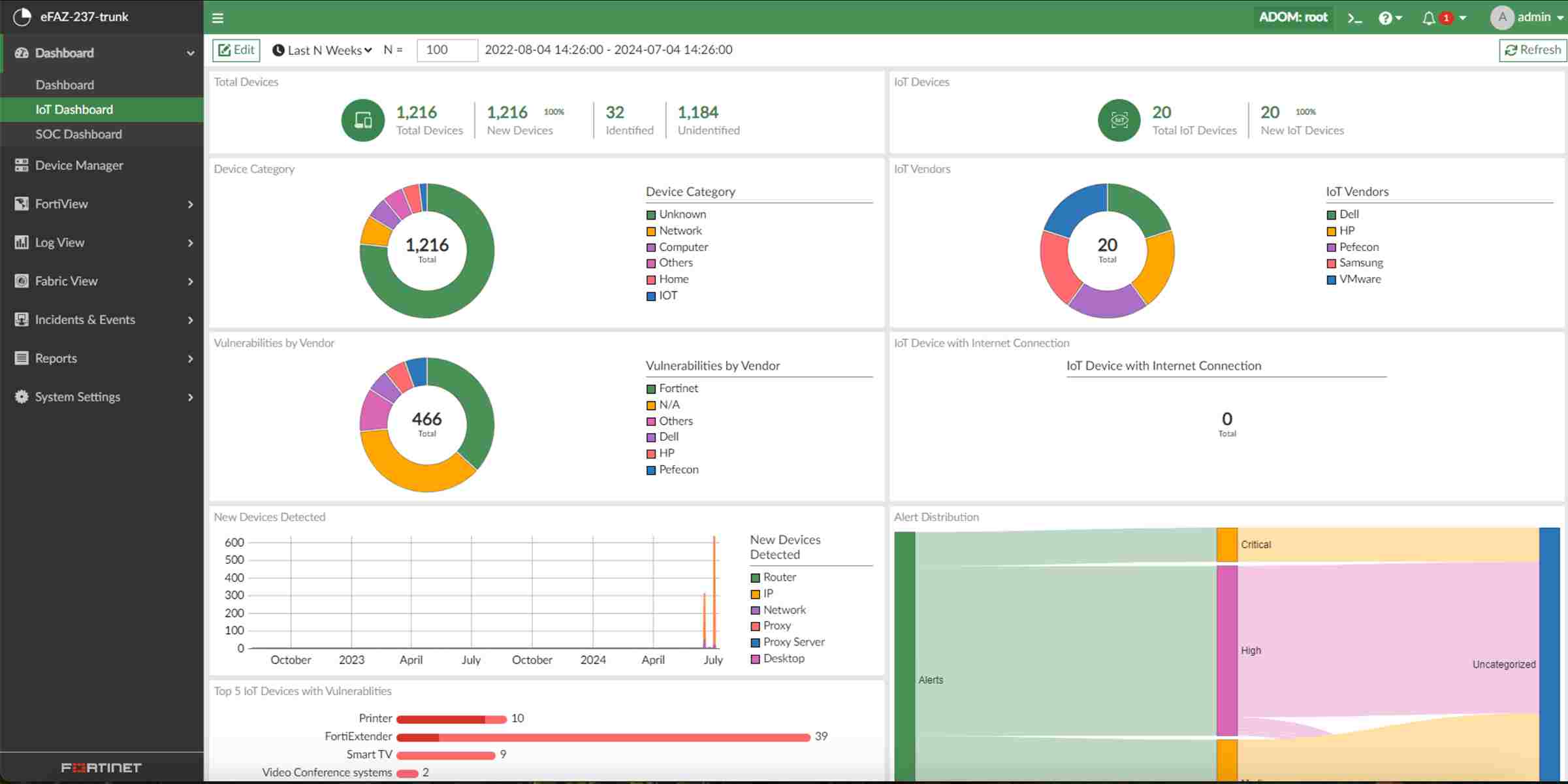
Source: Fortinet
Features of Fortinet
API Protection with FortiWeb WAF: Filters harmful traffic and enforces security regulations.
Advanced Threat Intelligence: Uses machine learning and artificial intelligence to identify new and evolving API risks.
DDoS Mitigation: Provides strong protection against a large volume of DDoS attacks and malicious traffic.
Follows Compliance: Helps organizations meet regulatory compliance requirements.
Centralized Security Management: Offers a single platform for managing API security and other cybersecurity operations.
Advantages of Fortinet
Complete Security Solutions: Combines API protection, network security, and threat intelligence.
Scalable and Adaptable: Ideal for organizations of different kinds, from SMBs to big organizations.
Easy Implementation: Connects with other Fortinet solutions to create a full security architecture.
Disadvantages of Fortinet
Complex Configuration: Requires skilled professionals to configure and optimize properly.
Expensive: It can be expensive for small and medium-sized organizations.
Fewer API Features: It only provides WAF protection, unlike other platforms.
Best For
Fortinet is for big organizations that need complete security solutions, including network and API security. It provides AI-driven threat detection to organizations that want everything in a single security solution.
How to Choose the Best API Security Solution for Business
Selecting the proper API security solution entails examining a variety of factors to ensure that it is apt to organizational needs as well as enhancing the overall security posture.
1. Scalability and Performance
The security solution should be capable of handling existing API traffic as demand continues to increase and exceed where it is now. They should be able to manage high-traffic conditions and also provide features such as global CDNs plus load balancing of APIs to enhance delivery without compromising on security.
2. Usability and Integration
Check if they have simple dashboards, automation, and simple installation that provide smooth operation. Easy interaction with CI/CD pipelines, monitoring tools, and cloud platforms makes workflows much more efficient and connects easily with the customer’s existing infrastructure, which also improves overall security.
3. Cost Considerations
The price is the most important factor in adding value to an API security solution. Companies need to know how much they can spend and ensure that the features they need for security are not compromised. Good cost management will provide strong protection and not hurt the budget.
4. Threat Protection
For the highest level of defense that keeps pace with sophisticated and ever-changing assaults, Advanced Threat Protection is a must for APIs. It should be in a position to detect and mitigate attacks such as injection attacks, abuse at the point of compromised credentials, and automated bot activity among others in real-time. Prompt monitoring with flexible responses is routine practice to keep private data safe and systems protected from breaches.
5. Compliance Needs
Regulatory compliance is the main factor for organizations that are in industries like healthcare, finance, e-commerce, etc. Platforms automate compliance through pre-configured policies and wide audit logs, helping organizations follow GDPR, HIPAA, and PCI-DSS regulations. Integrated reporting capabilities ease audits and lessen the burden of compliance.
Final Thoughts
API security is essential for securing private data while following regulatory compliance. API security is important for organizations across all industries. Wallarm Security is an excellent API security solution but checking alternatives will help organizations know about other platforms according to their specific operational demands, budgets, and technology environments.
For organizations looking for a full and affordable API security solution can choose Akto. It focuses on automation, and real-time protection, and is easy to install with existing workflows. It is perfect for organizations that want to secure APIs without the high cost of enterprise-grade solutions.
Secure the APIs with confidence. Schedule a demo now to consider Akto a reliable partner in protecting the digital ecosystem.
