3 New Ways to Detect Improper API Inventory, OWASP API9:2023
Akto has introduced new features related to Improper Inventory Management that allow you to organize your inventory with tags and recognize hidden APIs to better your security testing.

Raaga Srinivas
Apr 9, 2024
Improper Inventory Management (OWASP API9:2023) refers to the lack of proper management and organization of APIs, which could lead to security vulnerabilities. It includes situations where APIs are not documented, or forgotten after creation, but are still active and accessible. Proper inventory management involves organizing your API inventory with tags and recognizing these hidden APIs to improve your API security testing.
Akto now provides solutions to these challenges!
Discover Shadow APIs
Shadow APIs are APIs that are not publicly documented or are forgotten after creation but are still active and can be accessed. These APIs could potentially be exploited by attackers, making them a significant security risk.
For instance, an e-commerce company might have developed an API to handle payments. This API was documented and used during a big sale event, but after the event ended, the team forgot about it and moved on to other projects, leaving the API undocumented and out of sight. Despite not being in active use, the API is still live and capable of processing payments. This is an example of a Shadow API.
Akto now creates an API collection titled ‘Shadow APIs’ when testing your APIs with Akto.
This lets you test these previously undiscovered APIs for vulnerabilities with Akto’s Test Editor.
Here’s how you can identify them on Akto:
Added ‘Partner’ access type for APIs
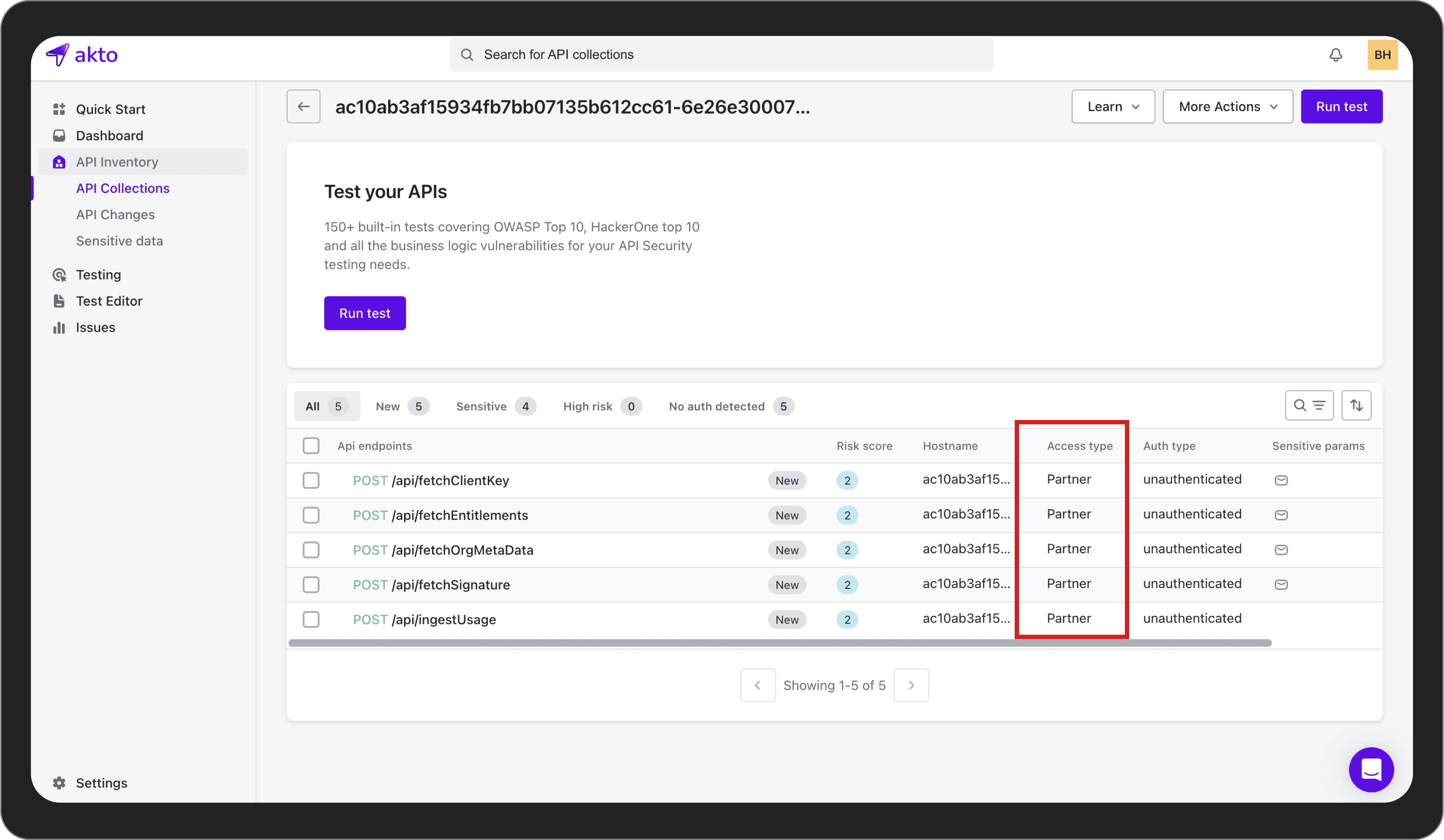
In API security, an access type refers to the level of permissions or the type of access that an API provides. It determines what actions can be performed via the API and what data can be accessed. Previously, Akto only tagged public and private APIs as access types.
However, there could also exist ‘Partner’ APIs. A 'Partner' API refers to APIs that are not open to the public but are shared with specific partners or third parties for business purposes.
For example, Fintech deals not only with the APIs of their clients and internal APIs but also with banks that facilitate their transactions. These require a higher level of trust and often operate with more permissions and access to data than public APIs. Check out our documentation on how to configure access types with Akto.
Added Staging and Production tags to each API Collection

Staging and Production tags are used to categorize API Collections based on their development stage. The 'Staging' tag is typically used for APIs that are in the testing or pre-production phase. These APIs are not yet released to the public and are used for testing purposes. On the other hand, the 'Production' tag is used for APIs that are fully developed, tested, and released for use by the public or end users.
Akto now lets you tag your API collections under ‘Collection Type’. Learn how to do this from our docs.
Final Thoughts
We are constantly adding new features to improve our capabilities, the API discovery and security testing process, and bringing in relevant use cases for our users. Check out some of our resources to see other new features we’ve introduced:
Keep reading
API Security
8 minutes
NIST Cybersecurity Framework
The NIST Cybersecurity framework provides organizations with a set of standards, guidelines, and practices to develop strong cybersecurity practices for managing cybersecurity risks effectively.
API Security
7 minutes
API Security Audit
An API Security Audit evaluates APIs, identifies potential risks, and strengthens the organization's defenses against security breaches and cyber-attacks.
API Security
8 minutes
Security Information and Event Management (SIEM)
SIEM aggregates and analyzes security data across an organization to detect, monitor, and respond to potential threats in real time.
Experience enterprise-grade API Security solution



