Roku Data Breach - 15000 Customers affected!
Roku revealed a data breach that affected more than 15,000 customers for unauthorized purchases of hardware and streaming subscriptions.

Medusa
Mar 19, 2024
Roku, a digital media and streaming content company offers streaming sticks, boxes, home automation kits, sound bars, light strips, and TVs running its specialized OS. This allows users to access services like Netflix, Hulu, and Amazon Prime Video.
Roku lets users buy subscriptions to streaming services through their accounts. When you sign up for these subscriptions, Roku saves your credit card info for future use.

Roku
When customers add a subscription, Roku actively stores their credit card information in their online accounts for easy future purchases.
Unfortunately, Hackers used the Open Bullet 2 or SilverBullet cracking tools to breach Roku accounts by brute-forcing usernames and passwords.
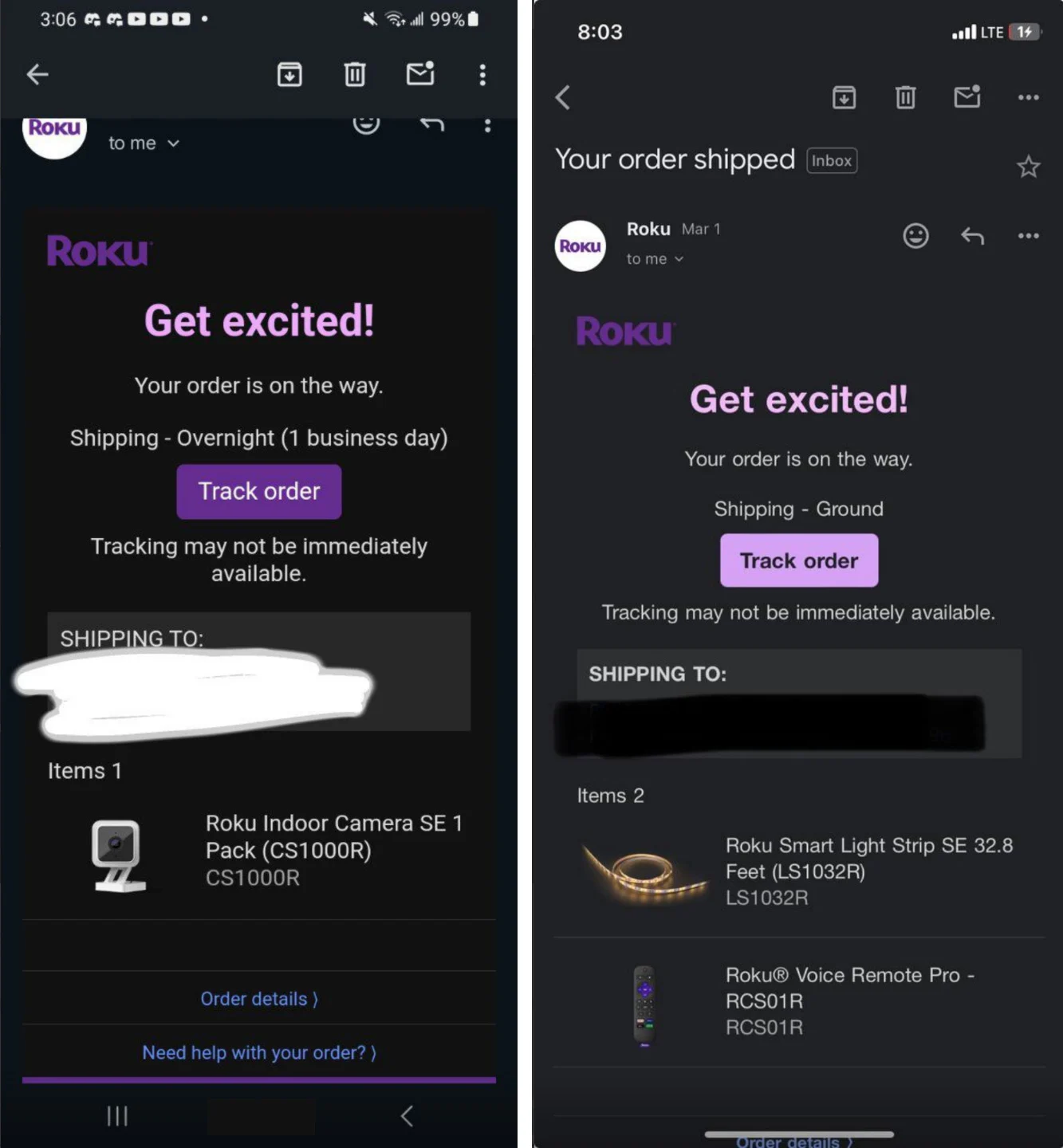
fraud purchases
What happened in the Roku data breach?
Hackers breached and sold over 15,000 Roku accounts for $0.50 each, using these accounts for unauthorized hardware and subscription purchases.
The hackers exploited stored credit card information and performed a credential-stuffing attack to gain unauthorized access to passwords and email addresses. They locked out the users and made purchases without sending confirmation emails. In response, Roku secured the accounts, mandated password resets, and refunded the unauthorized charges. Nevertheless, without two-factor authentication, the vulnerability of Roku accounts persists post-breach.
Who was affected by the Roku data breach?
The Roku data breach affected over 15,000 customers, a diverse range of users who rely on the platform for entertainment. The incident exposed all users, from casual viewers to dedicated streamers, to the risk of unauthorized access and fraudulent transactions.
How did this data breach happen?
A hacker can import custom configs (configuration files) into these (Open Bullet 2 or SilverBullet ) programs to execute credential stuffing attacks against specific websites like Netflix, Steam, Chick-fil-A, and Roku.
Threat actors had used a Roku config to conduct credential-stuffing attacks for months. They bypassed brute force attack protections and captchas by using specific URLs and rotating through proxy server lists. The hackers then sold the successfully hacked accounts on stolen account marketplaces for as low as 50 cents.
What is Credential Stuffing?
In a credential-stuffing attack, attackers utilize stolen account credentials, such as usernames and passwords, that have been obtained from other data breaches. These ill-gotten credentials are then used in large-scale automated login attempts against a targeted web application, in this case, the Roku platform. The objective of such an attack is to gain unauthorized access to user accounts, often leading to misuse of sensitive personal information.
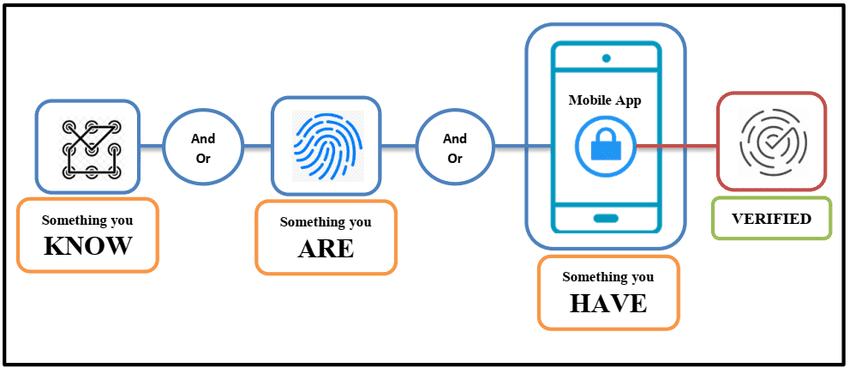
Why is Multi-factor Authentication important?
Multi-factor authentication
Multi-factor authentication (MFA), also known as two-factor authentication (2FA), is a security process where users need to provide two or more different authentication factors to confirm their identity. This additional layer of security goes beyond just a username and password.
Here's how users can implement multi-factor authentication:
Username and Password: Users should enter their username and password as the first authentication factor, as they would do in traditional login processes.
Second Factor: After users input their username and password, the system will prompt them to provide a second factor of authentication. This second factor could be something users possess (like a smartphone or hardware token), something inherent to them (like a fingerprint or other biometric data), or something they remember (like a PIN or answer to a security question).
Authentication: After users provide both factors, the system will confirm their identity. If the system successfully validates both factors, it will grant access to the users.
So, even if a hacker gains a user's credentials through a data breach, they would still need to overcome the second layer of authentication, which could involve a physical device the user owns or biometric data. This extra step significantly increases the difficulty for unauthorized users to access an account, thereby defending the account owner's sensitive personal and financial information. The implementation of MFA can help avoid situations like the Roku data breach.
How can Akto detect broken authentication proactively?
This type of situation arises when the authentication is not robust. Attackers can exploit weak or broken authentication in various ways, making it crucial to test for vulnerabilities.
Akto, a powerful tool for API authentication testing, has 100+ tests for authentication and authorization testing to help you identify vulnerabilities. See how it works.
Roku breach Mitigations
To minimize the risks associated with such data breaches and attacks, follow these steps if you are a Roku user or use similar platforms:
Change your passwords regularly: Periodically updating your password can protect against credential-stuffing attacks.
Choose unique passwords: Don’t use the same password across multiple platforms. A compromise on one platform could trigger a domino effect of breaches on other platforms.
Enable two-factor authentication (2FA): This security measure requires a second form of verification in addition to a password and enhances your account security.
Final Thoughts
Remember, your data is valuable - treat it carefully. Credential stuffing, where attackers use stolen login details from other breaches, is a common attack. Two-factor authentication, requiring a second proof of identity, strengthens security and makes it harder for these attacks to succeed. Additionally, conduct regular authentication testing to identify vulnerabilities proactively.
Keep reading
API Security
8 minutes
NIST Cybersecurity Framework
The NIST Cybersecurity framework provides organizations with a set of standards, guidelines, and practices to develop strong cybersecurity practices for managing cybersecurity risks effectively.
API Security
7 minutes
API Security Audit
An API Security Audit evaluates APIs, identifies potential risks, and strengthens the organization's defenses against security breaches and cyber-attacks.
API Security
8 minutes
Security Information and Event Management (SIEM)
SIEM aggregates and analyzes security data across an organization to detect, monitor, and respond to potential threats in real time.
Experience enterprise-grade API Security solution



