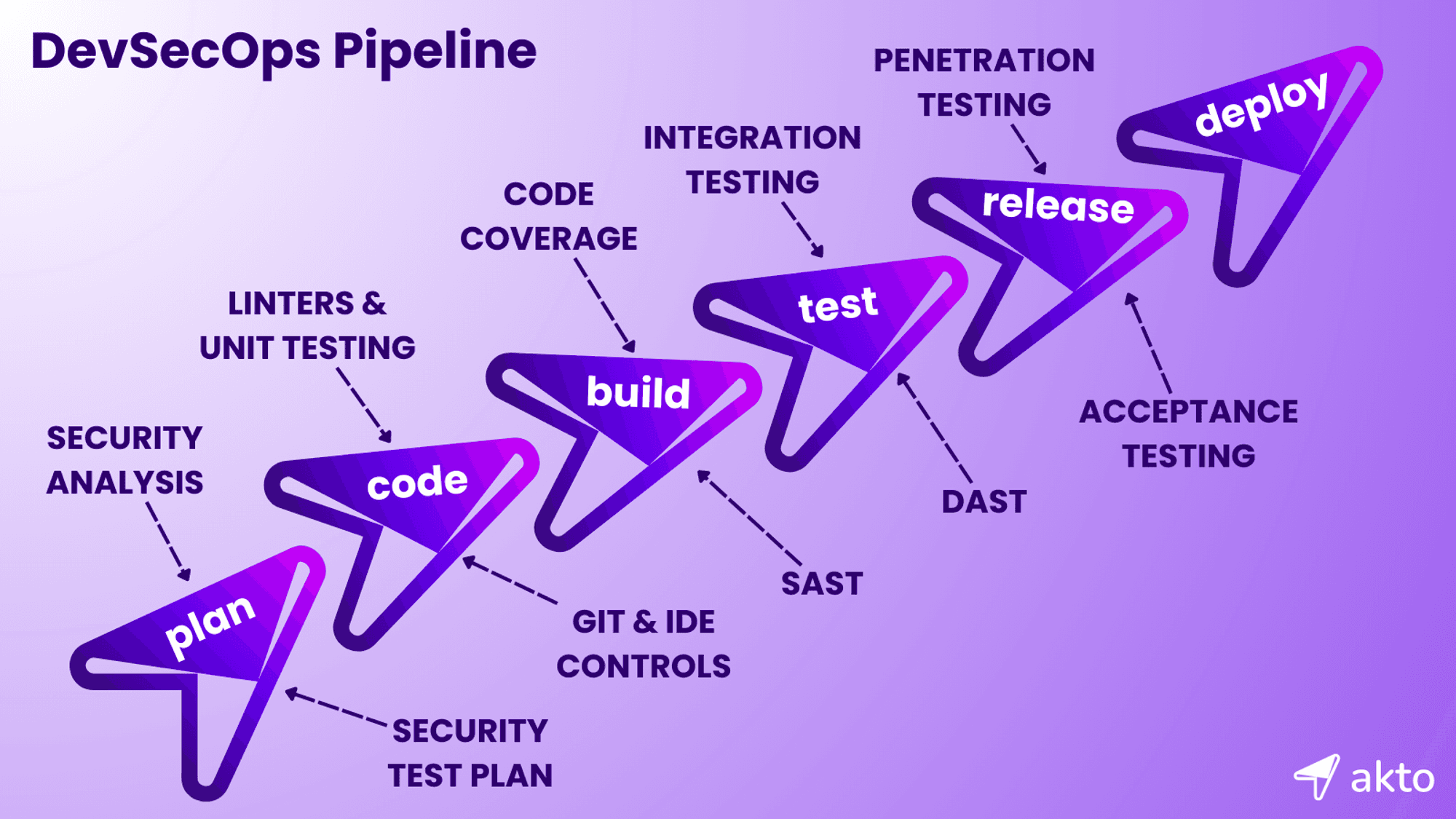
Strategies
DevSecOps Strategy: 7 Strategies to Implement DevSecOps in Your Organization
Introduction to DevSecOps Strategy
DevSecOps emerged from the recognition that waiting until the end of the production cycle to address security was both inefficient and risky. With this approach, security is no longer the responsibility of just one team. Instead, it is infused throughout the entire development lifecycle. By “shifting security left”, DevSecOps ensures that vulnerabilities are identified and mitigated long before they reach the production environment.
But why does any of this matter? In today’s age, a single vulnerability can cost an organization millions, not just in financial terms but also in lost customer trust and brand reputation. By integrating security from the beginning, DevSecOps isn’t just about producing secure software, but it is about creating resilient businesses in an age of relentless cyber threats.
As we navigate this blog, we’ll journey through the strategies to effectively implement DevSecOps, enabling organizations to not just stay ahead of threats, but also foster innovation in a secure environment.
Understanding the DevSecOps Ecosystem
DevSecOps is more than just a buzzword. It is a fundamental shift in how organizations approach developing software. It represents the integration of Development (Dev), Security (Sec), and Operations (Ops) into one cohesive and streamlined process. Let’s take a look at the various aspects of DevSecOps.
The Merging of Development, Security, and Operations
In traditional development models, the development, security, and operations teams would often work in silos. This led to delays, miscommunication, and potentially, vulnerabilities! DevSecOps breaks these barriers down and creates a collaborative environment where all three teams can work together throughout the whole development lifecycle.
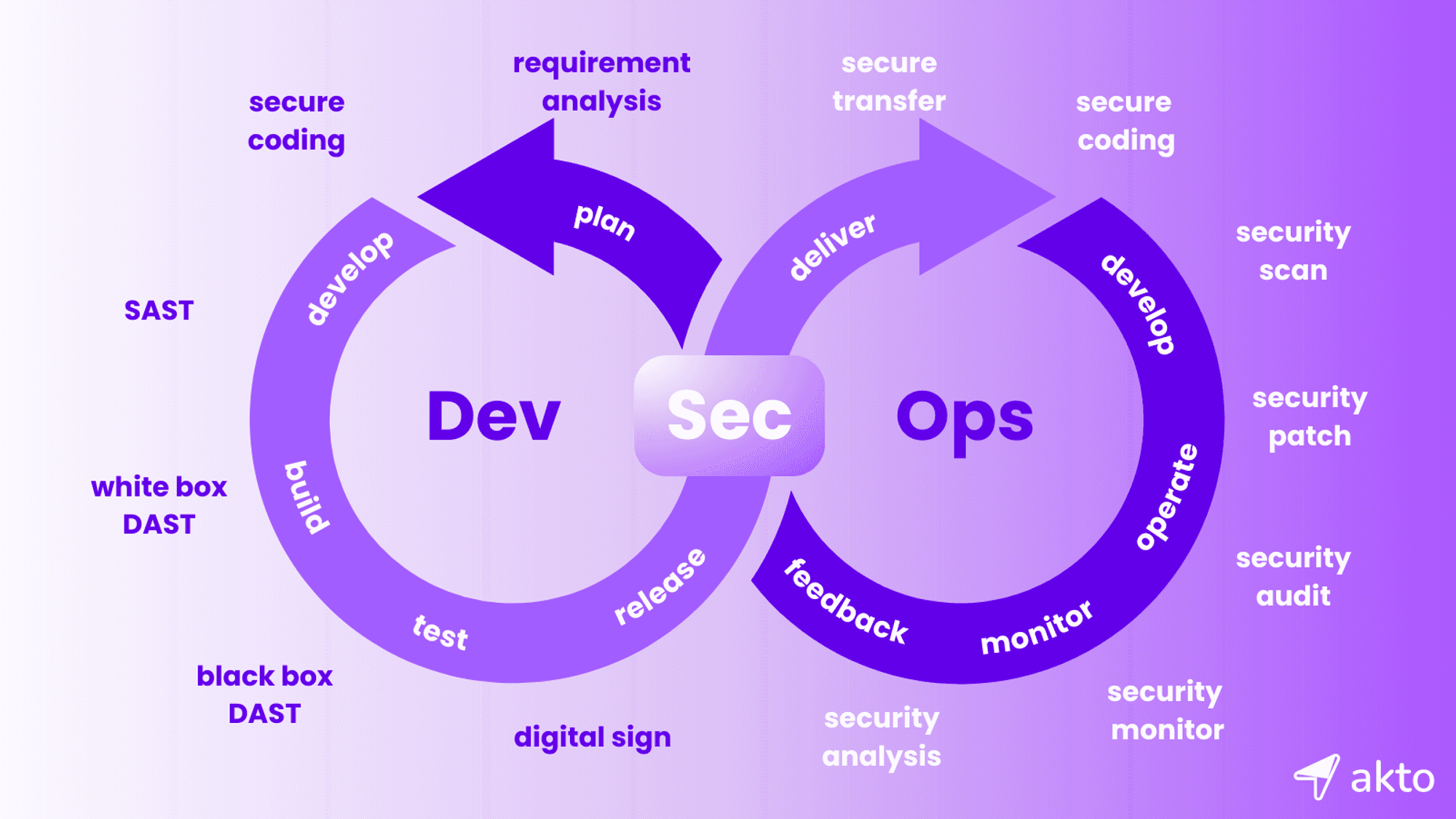
Development
This is where the actual code is written, tested, and prepared for deployment. In a DevSecOps approach, security practices are integrated right from the design stage, ensuring that security is considered at every step of development.
Security
Unlike the traditional models, where security is often added later (or not at all), in DevSecOps, security measures are embedded from the beginning. Security teams work directly with developers to identify and mitigate risks early on. This proactive approach to security reduces vulnerabilities as well as the likelihood of a massively expensive late-stage security fix.
Operations
DevSecOps emphasizes automation and continuous monitoring in the operations phase. This ensures that security measures are always up-to-date and that issues are addressed swiftly. Automation also keeps the software development lifecycle quick and approachable for everyone involved.
API Security: A Pillar of DevSecOps
APIs, while critical for functionality, have unfortunately also become prime targets for cyber attackers. An insecure API can provide a gateway for malicious actors to access sensitive data, disrupt operations, or even execute unauthorized commands.
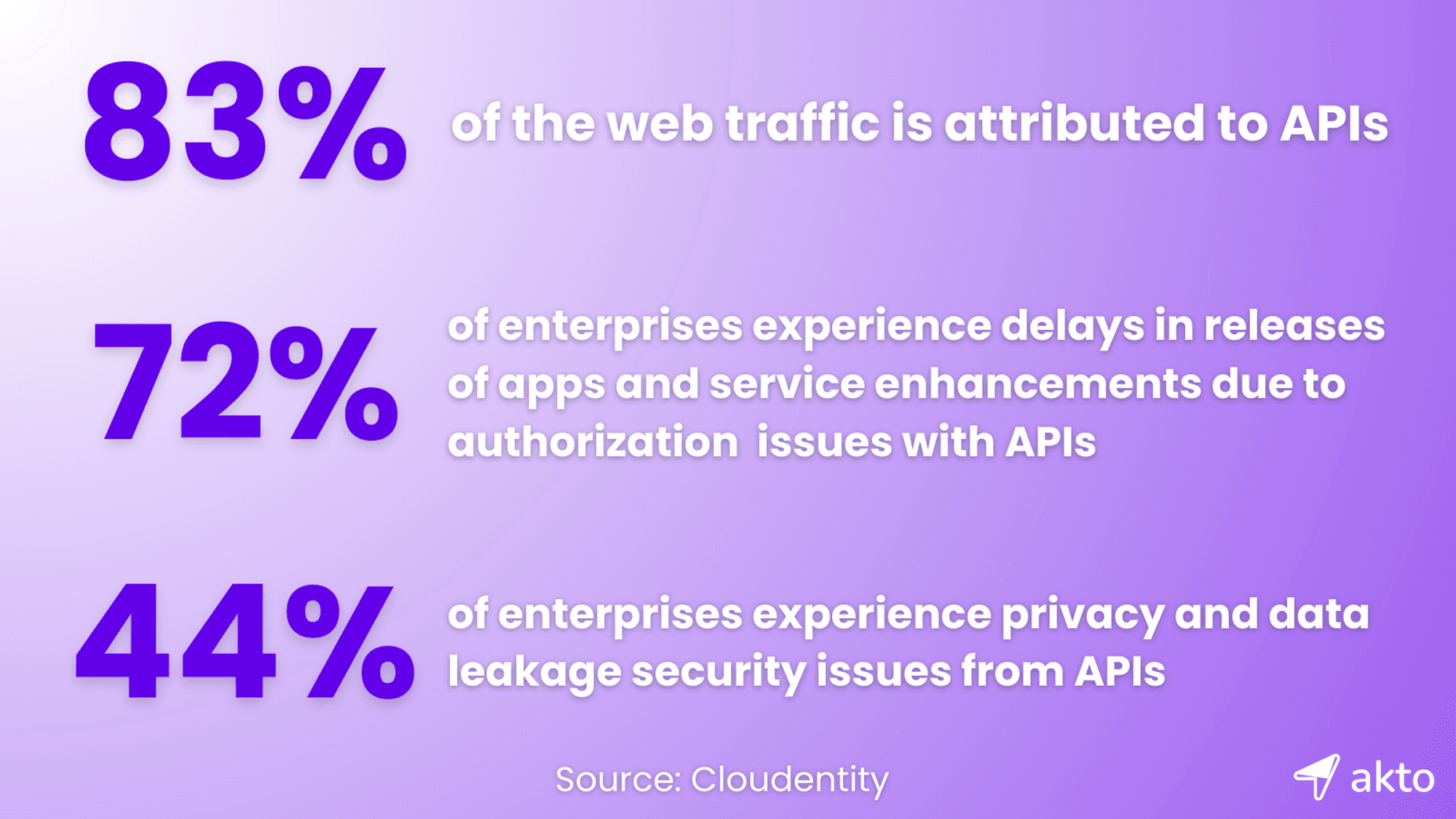
By giving API security the attention it deserves, organizations can strike a balance between harnessing the power of APIs while safeguarding their digital assets in the evolving world of DevSecOps.
DevSecOps Strategy 1: Secure Leadership Buy-in
DevSecOps Strategy 2: Foster a Culture of Collaboration
DevSecOps Strategy 3: Continuous Education and Training
DevSecOps Strategy 4: Integrate Security into CI/CD
DevSecOps Strategy 5: Adopt Security-as-Code
DevSecOps Strategy 6: Engage in Continuous Monitoring & Feedback
DevSecOps Strategy 7: Ensure Comprehensive API Security
Strategy 1: Secure Leadership Buy-in
In the world of DevSecOps, which combines software development, security, and operations, it's super important that the people at the top of a company, like CEOs and managers, really support and push for security. When they do this, it sends a clear message to everyone in the company that security isn't just a small part of the job - it's a big deal and key to everything they do. This support means teams get the right tools and feel motivated to tackle the challenges in integrating security into their development and operations processes. When leaders are all-in on DevSecOps, it creates a kind of wave effect that spreads through the whole company, making the shift to DevSecOps smoother and more effective.
Case Study:
A leading financial services firm needed to integrate security into its software development lifecycle to protect sensitive data and comply with regulations. The company struggled with traditional departmental silos, slowing down development and increasing security risks. Top executives, including the CEO and CTO, prioritized security, endorsed policy changes, and invested in advanced security tools and training. Results were:
Improved collaboration between development, operations, and security teams.
Reduced security incidents and faster software deployment.
Shifted the company culture towards prioritizing security in all projects.
Strategy 2: Foster a Culture of Collaboration
In DevSecOps, which blends software development, security, and operations, the real key to success is how well people work together. In many companies, different departments like developers, security experts, and operations teams work separately. This often leads to problems and missed security issues because they're not sharing information or working as one team. DevSecOps tries to change this by getting everyone to work together towards one main goal: making software that's not only good but also secure.
In this kind of teamwork, security isn't just the job of one team; it becomes everybody's business. This means more eyes and brains are looking out for any security risks, which makes the software safer.
Case Study: A tech startup, specializing in cloud solutions, struggled with slow product development and security issues due to isolated working of development, operations, and security teams. Leadership implemented a DevSecOps approach, focusing on team collaboration. To also help startups, read our recommendation on top 25 startup tools.
Actions:
Formed cross-functional teams combining development, operations, and security expertise.
Instituted regular joint meetings for cohesive project and security discussions.
Established shared goals and incentives to promote collective responsibility.
Results:
Faster software release cycles.
Reduced security breaches.
Enhanced team cohesion and morale.
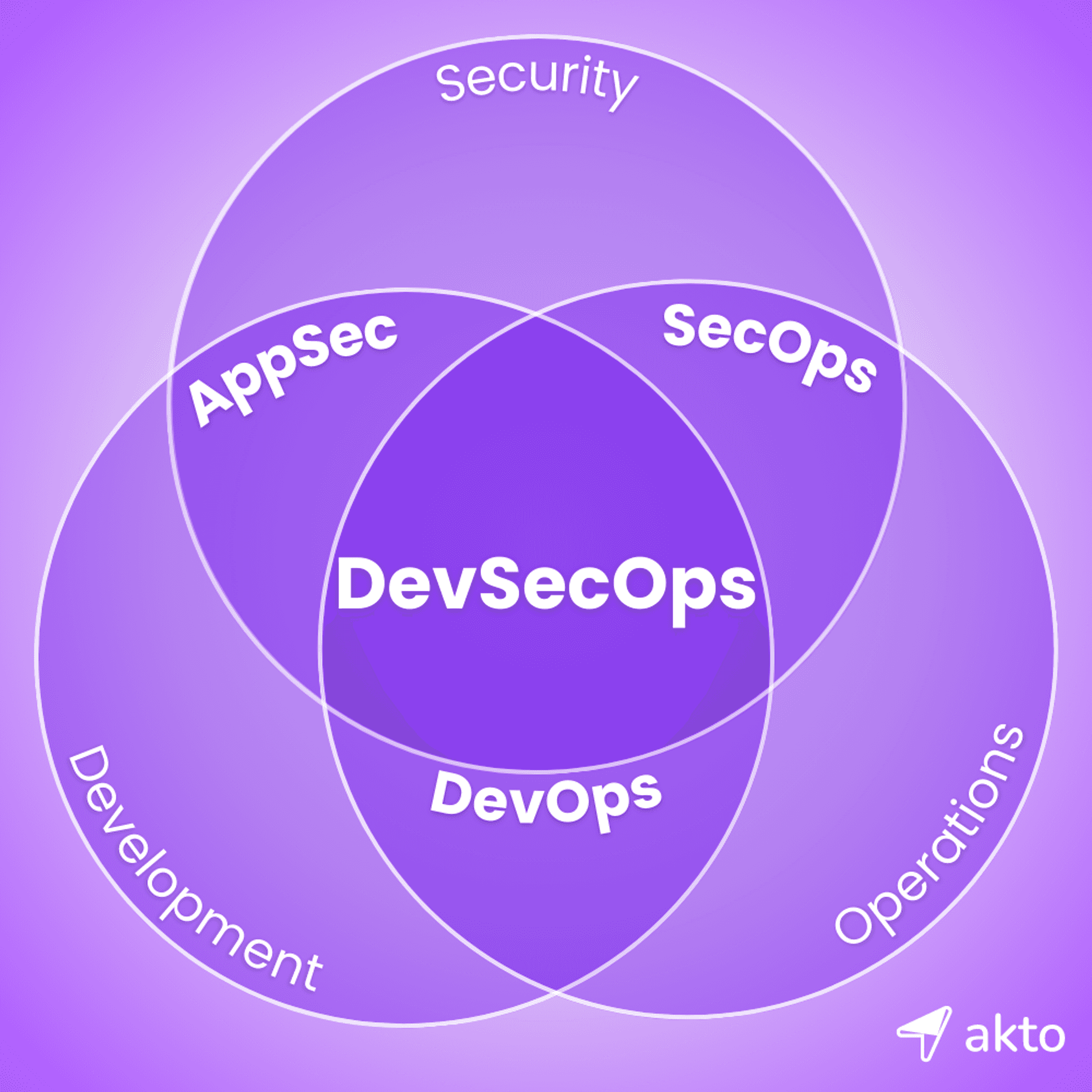
Strategy 3: Continuous Education and Training
In the world of cybersecurity, things change really fast. What's safe today might not be tomorrow. To keep up with these changes, it's important for companies, especially those following DevSecOps (a mix of development, security, and operations), to constantly learn and train their teams. It's not enough to set up security measures once; teams need to keep learning about the newest security practices and threats. Regular training helps everyone stay sharp and ready to prevent problems before they happen, instead of just fixing them after they happen.
Best DevSecOps Certifications
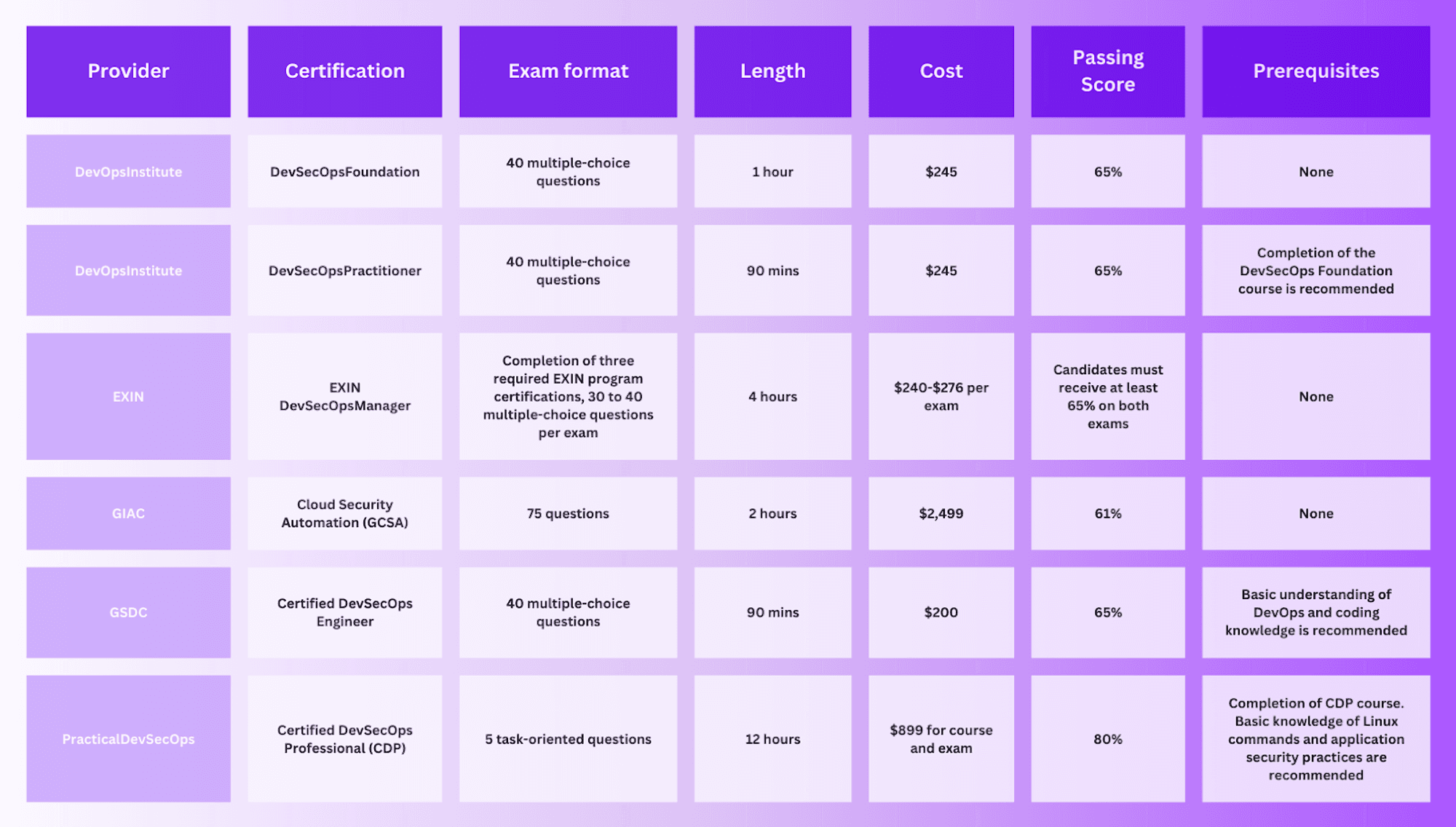
In the world of DevSecOps, knowledge truly is power. With informed teams, organizations can navigate the intricate maze of cybersecurity, ensuring their software remains both innovative and secure.
Case Study
A healthcare company with a significant online presence was facing challenges in protecting patient data due to the rapidly evolving API threats. Their teams were skilled but not up-to-date with the latest cybersecurity trends and threats, leading to potential vulnerabilities in their systems. The company decided to integrate continuous education and training into its DevSecOps strategy.
Actions Taken:
Regular Training Workshops: They started hosting frequent workshops on the latest cybersecurity practices and emerging threats.
Online Learning Platforms: The company provided access to online courses for employees to learn at their own pace.
Cybersecurity Drills: They conducted regular simulated cyber-attacks to prepare their teams for real-world scenarios.
Results:
The teams became more adept at identifying and preventing security risks.
There was a significant reduction in security incidents.
The company maintained a high standard of data protection, crucial in the healthcare sector.
Strategy 4: Integrate Security into CI/CD
Continuous Integration and Continuous Deployment (CI/CD) are like a fast-moving assembly line for software, where new updates are made and released quickly. But with speed comes the risk of missing security issues. To avoid this, it's important to include security checks right into this fast-moving process. This means every bit of code is checked for security issues as it's being developed and before it's released. By doing this, security becomes a natural part of making software, making it more effective and reducing the chance of mistakes.
Case Study
A fast-growing e-commerce company was rapidly developing and updating its online platform but faced challenges in maintaining security due to the quick pace of changes. The company's rapid development cycle often overlooked security checks, leading to vulnerabilities in their platform. To tackle this, the company decided to integrate security directly into their CI/CD pipeline.
Actions Taken:
Automated Security Scans: They implemented automated tools that scanned new code for security issues as soon as developers wrote it.
Security as a Part of Code Review: Security checks were made a mandatory part of the code review process before any code could be merged into the main codebase.
Regular Security Training: Developers were trained to understand and implement secure coding practices.
Results:
The company saw a drastic reduction in security issues in their platform.
Faster and safer release cycles were achieved, maintaining the speed of development without compromising on security.
Increased confidence in the security of new features and updates.
Strategy 5: Adopt Security-as-Code
Think of "Security-as-Code" (SaC) as building a house with security features directly in the walls, rather than just adding locks and alarms after the house is built. In software development, instead of adding security at the end or using separate tools, SaC means writing the code in a way that it's already secure from the start. Developers include security rules and practices as they write the code. This approach helps catch and fix security problems early in the process, which is much better than trying to patch them up later.
See if you can spot the security fix in the code below! Catching issues like this early is key.
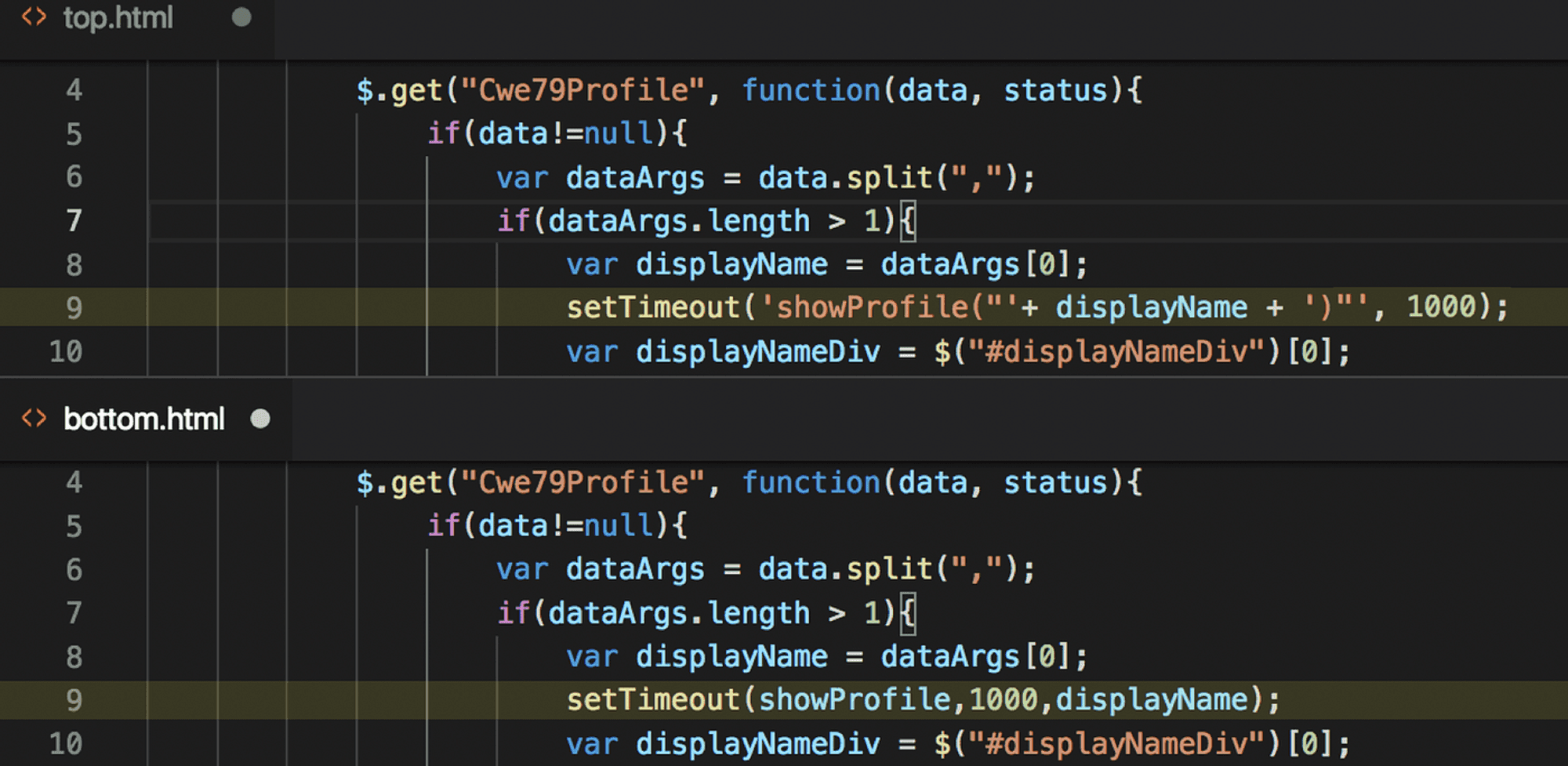
Embracing Security-as-Code doesn’t just result in more secure applications. It fosters a developer mindset where security considerations are second nature. This shift ensures that as applications evolve, their security foundations remain unshakeable.
Case Study
A financial institution was developing an online banking application but faced challenges in ensuring robust security due to the sensitive nature of financial transactions. Traditional security measures were proving inadequate, as they were mostly applied after the main development, leaving room for vulnerabilities. The institution decided to implement Security-as-Code to enhance their application's security.
Actions Taken:
Integrating Security in Development: Developers started integrating security protocols directly into the application's code.
Security-Oriented Code Reviews: Code reviews now included rigorous security checks as a standard practice.
Ongoing Security Training: The development team received continuous training in the latest security practices and how to implement them in coding.
Results:
Significant reduction in vulnerabilities within the application.
Enhanced security of financial transactions, gaining customer trust.
Reduced need for post-development security fixes, saving time and resources.
Strategy 6: Engage in Continuous Monitoring & Feedback
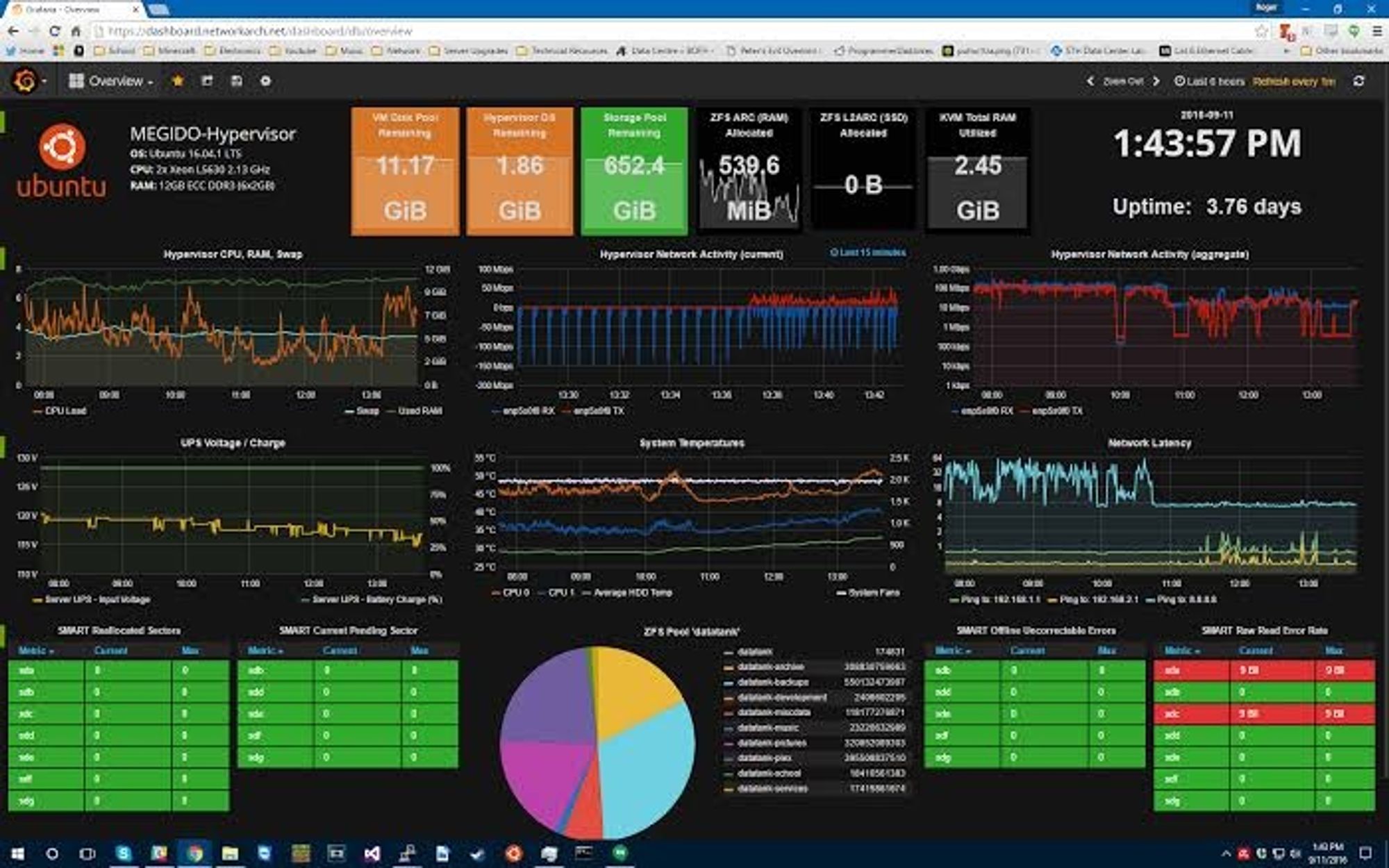
Imagine DevSecOps as a high-tech security system in a building. Even with the best locks and alarms, it's essential to keep an eye out for any unexpected issues that might come up. This is where continuous monitoring comes in - it's like having cameras and sensors constantly checking for anything unusual. If something seems off, the system quickly alerts the security team so they can fix the problem right away. This ongoing vigilance helps catch and address potential security threats before they cause real harm.
Look at this example of a Grafana dashboard.
Case Study
An online retailer with a vast digital platform was facing challenges in managing cybersecurity threats due to the increasing complexity of their operations. Despite having robust security measures in place, they struggled to identify and respond to new vulnerabilities promptly, which posed a risk to customer data and trust. To address this, they introduced a comprehensive continuous monitoring and feedback system.
Actions Taken:
Deployment of Monitoring Tools: The company set up advanced monitoring tools, like Grafana dashboards, to constantly scan their digital infrastructure for any signs of security breaches or vulnerabilities.
Instant Alert System: They integrated an alert mechanism that notified the security team immediately upon detecting any anomalies.
Rapid Response Protocols: A protocol was established for quick assessment and response to identified issues, ensuring swift action.
Results:
The system detected several previously unnoticed vulnerabilities, allowing for timely fixes.
Response time to security incidents was significantly reduced, minimizing potential damage.
The retailer maintained high customer trust levels due to their effective handling of security issues.
Strategy 7: Ensure Comprehensive API Security
APIs (Application Programming Interfaces) are like the connectors that let different software talk to each other. They're super important in modern tech because they make it easy for different applications to work together. However, because they connect different systems, they can also be a weak spot where hackers might try to break in. To prevent this, it's important to focus on API security. This means not just using basic security measures but also special tools and strategies designed for the unique ways APIs work. Think of it like adding extra strong locks specifically designed for the type of door you have. Companies like Akto offer these special tools to make sure your APIs are safe, which is crucial for keeping your entire digital system secure.
Challenges in Implementing DevSecOps
Cultural Resistance: Shifting from traditional methods to a collaborative DevSecOps model can face resistance. The key is to cultivate an understanding that this shift is not about assigning blame but about collective ownership and continuous improvement.
Skill Gaps: DevSecOps requires a fusion of development, operations, and security skills. Addressing gaps through training and hiring becomes essential.
Tool Overload: While tools are vital, it is easy to become overwhelmed with a plethora of options. Selecting the right tools that align with specific organizational needs is paramount.
Adapting to Speed: DevSecOps accelerates software delivery. Balancing this speed while ensuring comprehensive security checks can be a challenge initially.
While the path to DevSecOps might have its fair share of obstacles, the destination- a resilient, agile, and secure software delivery process, makes the journey worth every challenge encountered.
Conclusion
The digital landscape has transformed, and with it, the expectations for software development and security have evolved. DevSecOps, an integration of Development, Security, and Operations, isn’t just another buzzword. It is a necessity in today’s fast-paced, threat-laden environment.
While the strategies and insights discussed above provide a roadmap for implementing DevSecOps, it is essential to remember that this journey is unique for every organization. The challenges faced, while universal in some aspects, will often be tailored to an organization’s specific needs and legacy systems.
However, amidst the strategies, tools, and challenges, one message rings clear: proactive security isn’t an optional add-on, it is foundational.
Further reading
What is DevSecOps?: Introduction to DevSecOps, its evolution, and significance.
The Roadmap to DevSecOps Adoption: Step-by-step approach to adopting DevSecOps
Building a DevSecOps Culture: Cultivating a security-aware culture within the teams
DevSecOps Applications in 6 Industries [Examples and Case Studies]
Want to learn more?
Subscribe to Akto's educational emails for essential insights on protecting your API ecosystem.




