API Security involves practices and technologies designed to secure Application Programming Interfaces (APIs) against different types of attacks and abuse while ensuring secure interaction and information transfer between various different systems. Since sensitive data are generally processed within them, ranging from personal and financial information to organization data and beyond, these have become ideal targets for cyberattacks.
An effective API security protects against risks like SQL injection, cross-site scripting (XSS), and distributed denial-of-service (DDoS) attacks. Additionally, compliance with industry standards like GDPR and HIPAA requires strong API security, which helps organizations comply with the law, avoid legal penalties and maintain users' trust.
This blog explores the top 10 API Security Best practices to guide security engineers on how to protect their API against various security threats and vulnerabilities.
Let's get started!
10 Best API Security Best Practices
Strong Authentication & Authorization
Encryption for Data in Transit, Rest, and Storage
Validate & Sanitize All Inputs
Regularly Update & Patch APIs
Data Integrity Checks
Logging of API Activity
Regular Code Reviews
Prioritize API Governance & Risk Assessment
Throttling Requests with API Quotas
Follow OWASP API Security Guidelines
Protecting APIs is more critical than ever. Following are the 10 best practices that every organization should implement to ensure robust API security:
1. Strong Authentication & Authorization

Source: https://www.ssl2buy.com/wp-content/uploads/2019/04/authentication-vs-authorization.jpg
Strong authentication mechanisms like OpenID Connect, or SAML, and strong authorization mechanisms like OAuth 2.0 improve API security. Security engineers should also implement Multi-factor authentication as it provides an additional layer of protection. For sensitive information, organizations should also use biometric authentication that verifies users through unique biological traits.
2. Encryption for Data in Transit, Rest, and Storage
Security engineers should use encryption for data as it guards data, whether in transit or at rest. Organizations with large datasets can secure data using symmetric encryption, which encrypts and decrypts with a single key. Asymmetric encryption is another efficient encryption technique, using a set of keys (a public key for encryption and a private key for decryption), thus not requiring sharing a secret key.
Security engineers can use techniques like Transport Layer Security (TLS), Secure File Transfer Protocol (SFTP), and Secure Copy Protocol (SCP) to encrypt the data while transmitting it. Encryption ensures that sensitive data is kept confidential over a network. When data is kept at rest, organizations can store sensitive files with encryption or fully encrypt the drives before storing, thus avoiding access by unauthorized individuals.
3. Validate & Sanitize All Inputs
Organizations should adopt input validation that explicitly defines clear validation rules on what fields are required, valid value ranges, and data types because it proves that incoming data follows expected formats and, by doing so, eliminates harmful inputs that can easily break the system's integrity. Security Engineers may leverage a tool like JSON Schema in enforcing such rules.
Meanwhile, sanitization removes a potentially harmful element, reducing the risk of a malicious attacks. Proper validation safeguards data integrity and enhances overall system security.
4. Regularly Update & Patch APIs
Regular update and patching of the API is one of the best practices to protect the API since delaying patches and updates leaves the APIs vulnerable to security breaches. Organizations can have an extensive update and patch management that includes continuous monitoring of API infrastructure, implementing strict firewall rules, and updating the infrastructure regularly.
Security Engineers can keep their API services secure through updates and patching, thus ensuring that sensitive data is not compromised with regard to security threats.
5. Data Integrity Checks
Regular data integrity monitors and ensures that a sensitive data of the APIs are unchanged during any transit. Hashing is one of the methods that verifies a data integrity and converts data into unique hashed values. Developers can identify any unauthorized access or modifications by comparing the data of hashed value and a original value. It checks whether the received data is in accordance with the original data that was actually sent by the server. Thus, it safely executes the requests against standardized policies, which increases the security of the API.
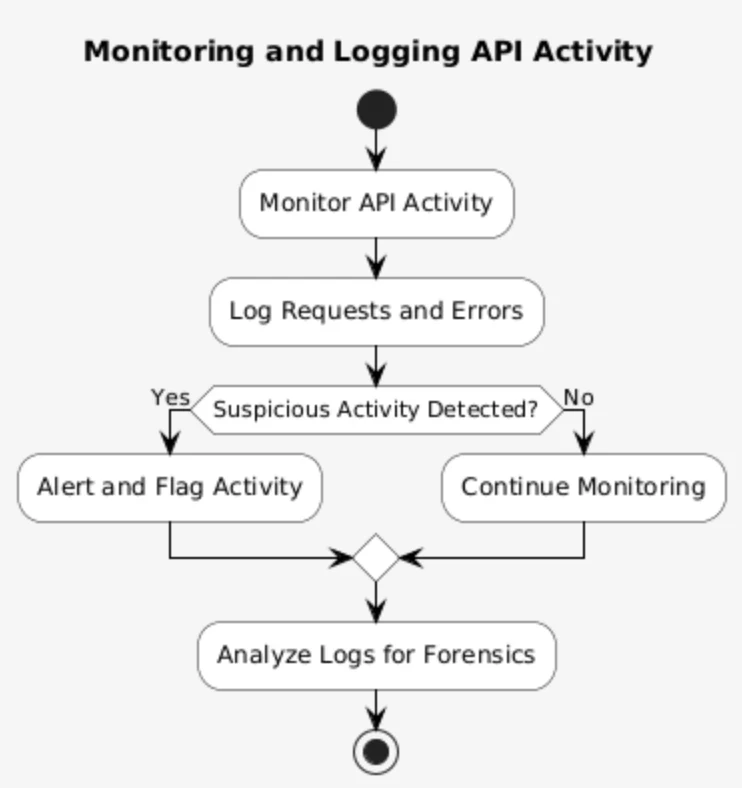
6. Logging of API Activity
Source: https://iha089.org.in/wp-content/uploads/2024/11/Monitoring-and-Logging-API-Activity.png
Auditable event logging strengthens API security by analyzing a failed login attempts and large transactions. Insufficient logging can lead to ranking 10th on the OWASP list, eventually making it a security risk. Improper logging may prevent alarms from triggering during an active attack, leaving threats undetected.
Inadequate logging may bring a site rank 10th on the OWASP list and eventually be an insecure website. Inappropriate logging may also keep alarms from getting triggered when threats are actually acting in an active attack.
A well-implemented security log allows effective monitoring of user activity and identifying suspicious behavior of the APIs. Upon detecting any threat, security teams can build a thresholds, parameters, or rules to increase data protection.
7. Regular Code Reviews
Regular code reviews improve software quality effectively. These reviews allow early detection of API vulnerabilities before attackers exploit them.
There are various ways to implement regular code reviews. Security teams can schedule meetings to review recent API changes. The security team thoroughly reviews all updates, especially those involving open-source tools.
8. Prioritize API Governance & Risk Assessment
API governance is one of the best practices for developing, managing, and deploying APIs within an organization. This ensures security, consistency, and scalability across the complete API ecosystem.
On the other hand, Risk Assessment is the process of detecting, analyzing, and evaluating threats and security weaknesses that may affect APIs.
Combining both API governance and risk assessment gives high-quality and secure APIs and also minimizes security risks. It provides an effective management of the API also increases API security ensuring well-structured API environment.
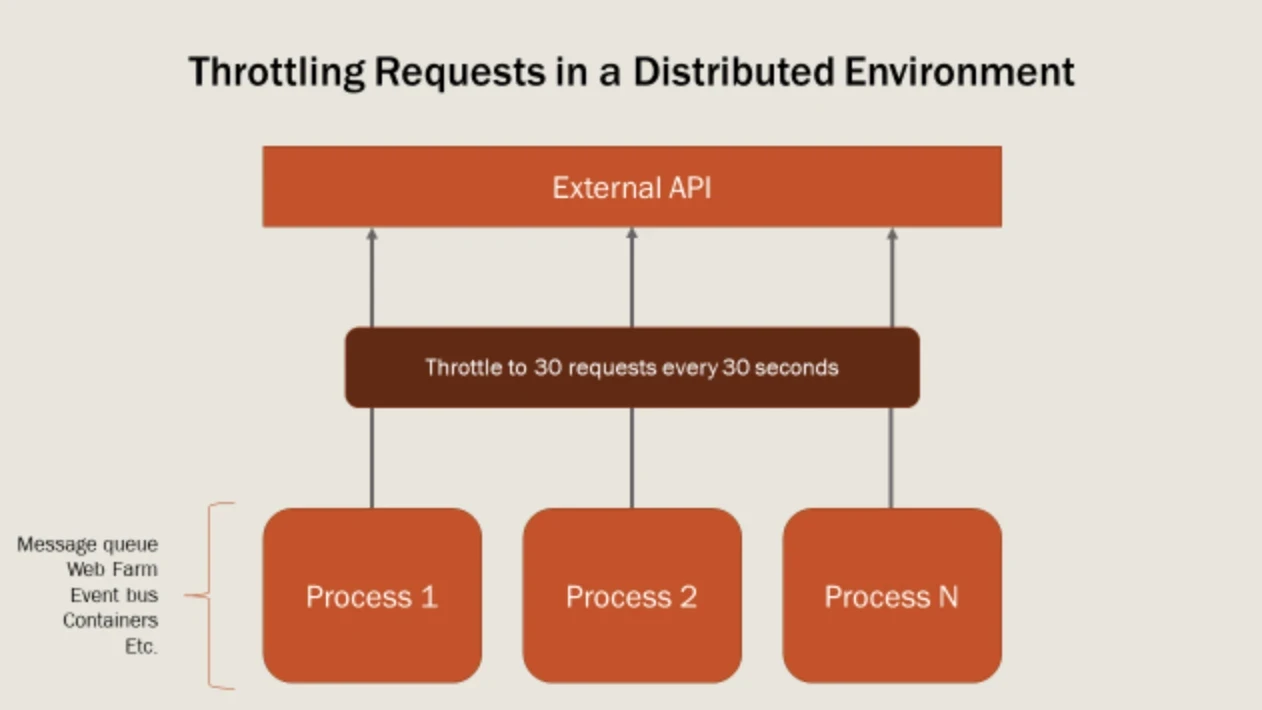
9. Throttling Requests with API Quotas
Source: https://www.codeproject.com/KB/IP/5260913/distributed-environment.png
Rate limiting protects APIs by controlling the requests and monitoring the traffic within a specific time frame. The system blocks the requests or the IP address and returns an error if the application exceeds the set threshold. Throttling API requests effectively prevent abuse. Security teams can prevent a unauthorized access of APIs by capping requests per second (RPS), which ensures the stability of the backend resources and better performance of the system.
10. Follow OWASP API Security Guidelines
Following the OWASP guidelines is the another best practice for API security. It provides security engineers with an extensive guide to protect against major security risks such as broken Object-Level Authorization (BOLA), broken Function-Level Authorization (BFLA), and Server-Side Request Forgery (SSRF).
Final Thoughts
Implementing solid API security best practices is therefore crucial for sensitive data protection, compliance, and application resilience from ever-evolving cyber threats. Organizations must regularly monitor, validate, and enforce security measures for the mitigation of risks and ensured secure API interaction.
The continuous API security testing platform of Akto is completely automated, meaning it can continuously detect vulnerabilities in real-time. Organizations can thereby proactively find and remediate security gaps that would otherwise pose a potential threat. Register for a free Akto demo today and help strengthen your API security strategy through cutting-edge, automated protection.
Schedule a demo with Akto to learn more about its API security features.
Want to learn more?
Subscribe to Akto's educational emails for essential insights on protecting your API ecosystem.

