Many security teams perceive API security as a big challenge that is beyond their capabilities due to insufficient internal expertise and resources. To address this challenge, API security Vendors or API Security Companies provide specialized tools and services that include hidden API detection, weakness scanning, and threat monitoring. They help security teams with API protection without building everything from scratch, especially with the growing number of APIs.
This blog explores who are API security vendors, the top ten API security vendors and their unique strengths. Learn more about how to choose the right API security vendor.
Who are API Security Vendors?
API Security Vendors are specialized API security platforms that focus exclusively on protecting Application Programming Interfaces (APIs) from attacks and vulnerabilities. These vendors develop comprehensive security platforms that monitor, analyze, and defend the critical API infrastructure security teams rely on for digital operations.
API security vendors have emerged as essential partners for security teams which are planning to undergo digital transformation, as API’s have become prime targets for cyber attackers seeking to access sensitive data. Their platforms integrate with existing security infrastructure while providing specialized protection for threats.
10 Best API Security Vendors
The API security vendor market is diverse, with numerous security platforms serving industries such as financial services, healthcare, and others.
The following API vendor lists are created by identifying vendors specializing in API security, offering solutions like API discovery, vulnerability scanning, runtime protection, and compliance management.
Akto.io
Akto API security platform is crafted specifically for modern application and product security teams. Throughout the DevSecOps pipeline it delivers a wide array of solutions including continuous API discovery, sensitive data protection and security posture management.
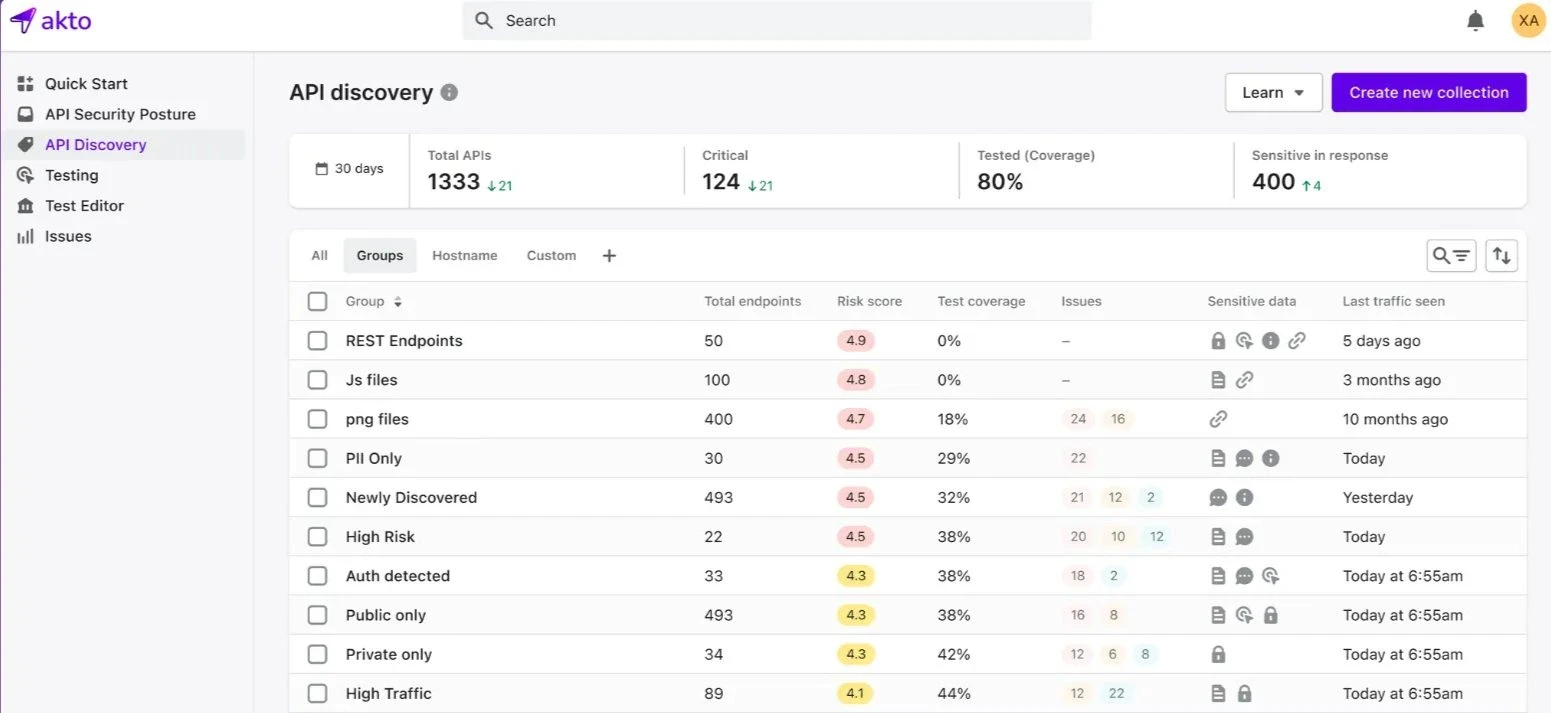
Features:
The platform detects internal public and third-party APIs, including sensitive zombie and shadow types.
Over 100 sensitive data types including SSNs credit card information and tokens can be identified with options to add custom data types.
Integrates security testing into the CI/CD pipeline covering OWASP API top 10 vulnerabilities authentication authorization and business logic testing.
API Security management functions to both prevent breaches and maintain compliance standards.
Through testing processes deliver identification and remediation of authentication and authorization vulnerabilities.
F5
F5 API Security offers advanced API protection against threats that establishes secure data exchange and compliance. It also provides real-time threat detection, AI driven anomaly detection and access controls to prevent security threats.

Image source: F5
Features:
The platform protects against distributed denial-of-service events robotic intrusions and application programming interface exploitation.
AI-driven API security and anomaly detection.
Implements measures to regulate API traffic flow while controlling access permissions.
The system enables CI/CD pipeline integration to support DevSecOps.
Enhanced API analytics combined with real-time threat intelligence.
Cloudflare
Cloudflare’s security solutions provide advanced protection against many API threats like vulnerability exploits, data abuse and data leaks.
Image source: Cloudflare
Features
Provides API Gateway with built-in authentication and authorization.
Rate limiting and bot mitigation for API abuse prevention.
It has features like Automated threat intelligence and anomaly detection.
Protects API traffic with TLS encryption and WAF protection.
Integrates easily with cloud-native environments occurs without disruption.
Zed Attack Proxy (ZAP)
ZAP is a free open source application security scanner which was developed by OWASP (Open Web Applications Security Project). It identifies vulnerabilities in the web applications by evaluating and intercepting traffic between different web browsers and servers.
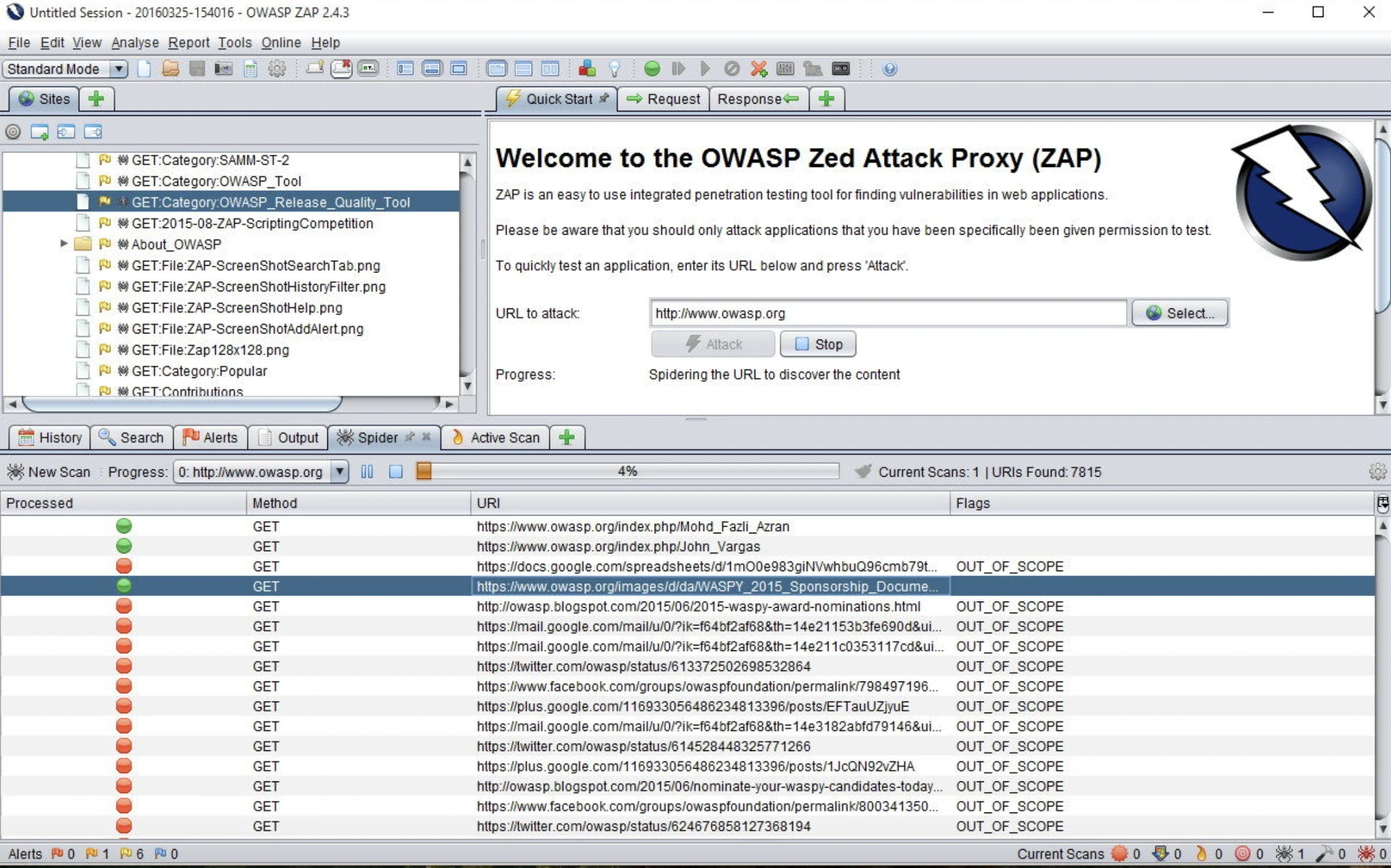
Image source: ZAP
Features:
Common vulnerability detection through automated API security scanning systems.
Detection techniques include both passive and active scanning methods to identify potential threats.
It is web-based interface which is designed for user-friendliness and it is combined with automation support.
It has integrated API fuzzer for security testing.
It can integrate with DevSecOps workflows.
Wallarm
Wallarm is a API security platform that offers advanced API security solutions for evolving web applications. It provides instant protection against API attacks to ensure safe development throughout the API lifecycle.

Image Source: Wallarm
Features:
Provides real time incident response and threat detection.
It has machine based anomaly detection.
Offers API Discovery and Inventory Management.
Provides security against OWASP API Top10 vulnerabilities.
Easily provides integration with cloud based environments.
SALT Security
SALT Security is one of the leading API security platform. It specializes in securing API’s from security attacks and vulnerabilities. It offers comprehensive API security by using machine learning and behavioral analytics.

Image Source: Salt Security
Features:
Offers Continuous API discovery and risk assessment for API's.
It has Machine learning-based attack detection and mitigation features.
Provides Security against API abuse and zero-day attacks.
Security compliance through API posture management.
Examination of API traffic combined with user behavior patterns becomes deeply visible.
Imperva API Security
Imperva API Security is part of Imperva's comprehensive application security suite, offering continuous API discovery and protection. It automatically detects and classifies API endpoints, assesses associated risks, and provides strong defense against common API security threats.
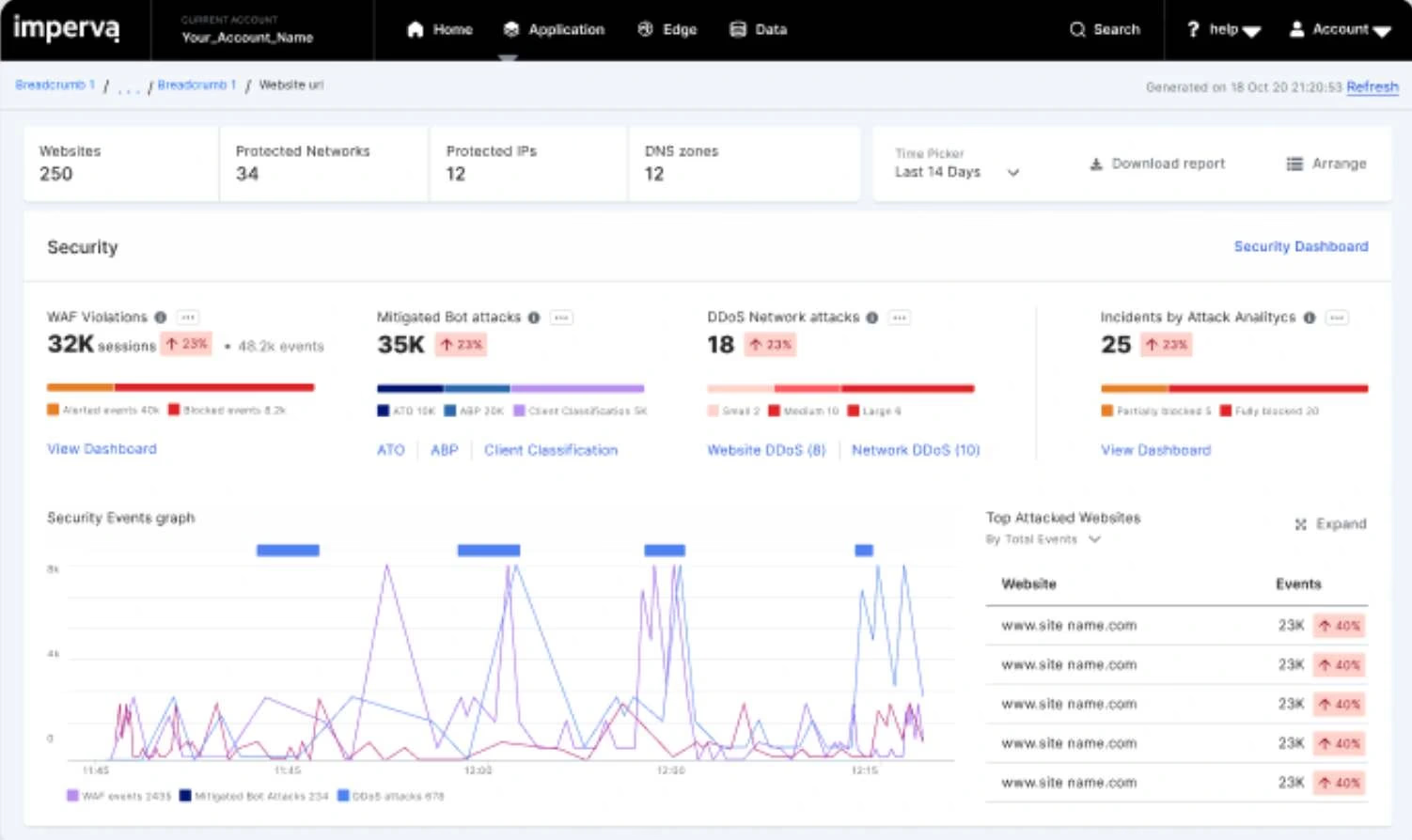
Image source: Imperva
Features:
Identifies every API endpoint through automatic detection and classification processes.
APIs are protected from Distributed Denial of Service attacks.
Delivers strong defense mechanisms to counter multiple threats.
Seamless integration with additional Imperva security platforms to provide comprehensive security protection.
Tracks API traffic to identify and mitigate potential threats promptly.
IBM API Connect
IBM API Connect is a comprehensive API management tool that delivers end-to-end security features, analytic functions, and governance controls. It enables easy integration between different applications and services and supports both on the premise and cloud deployments.

Image source: IBM API Connect
Features:
API Gateway Security designed with integrated authentication mechanisms and encryption features.
Advanced threat protection and traffic monitoring.
Has API analytics for usage and security insights.
Implements automated systems to enforce compliance policies.
Enforces scalable systems across combined hybrid and multi-cloud platforms.
StackHawk
StackHawk is an advanced API Security and DAST (Dynamic Application Security Testing) tool that can integrate easily into CI/CD pipelines. This enables security teams to identify and remediate security threats before they hit the production.
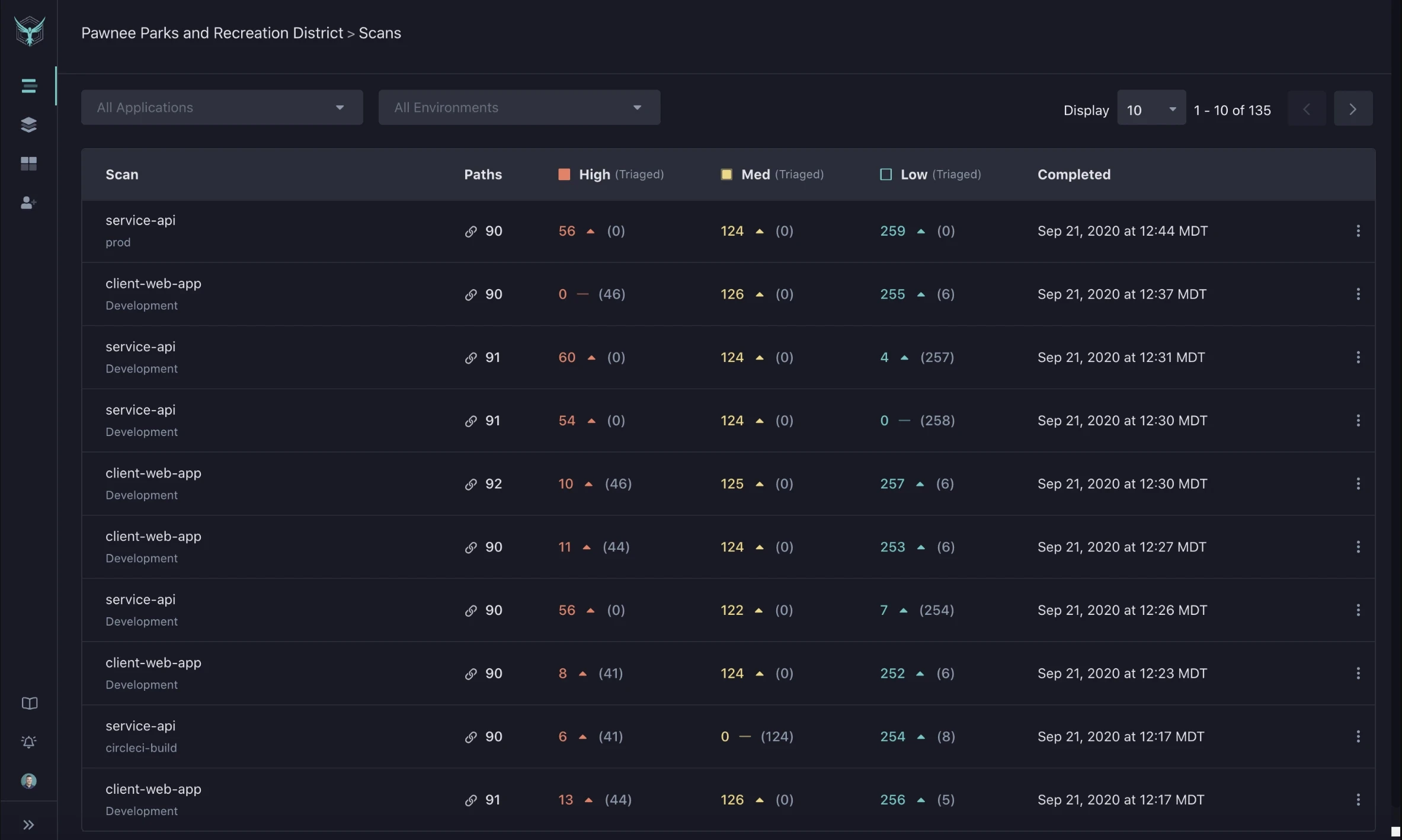
Image Source: StackHawk
Features:
During development phases it executes automated security scans for APIs.
Effortlessly integrates with DevSecOps workflows.
Detection mechanisms for OWASP API Top 10 vulnerabilities.
Adjustable protection protocols combined with examination settings.
Detailed security reports for API risk assessment.
Cequence
Cequence delivers API security and bot mitigation solutions which guard against automated threats and API abuse. It provides UAP (Unified API Protection) platform which integrates compliance, discovery, and protection capabilities to secure API against various threats.
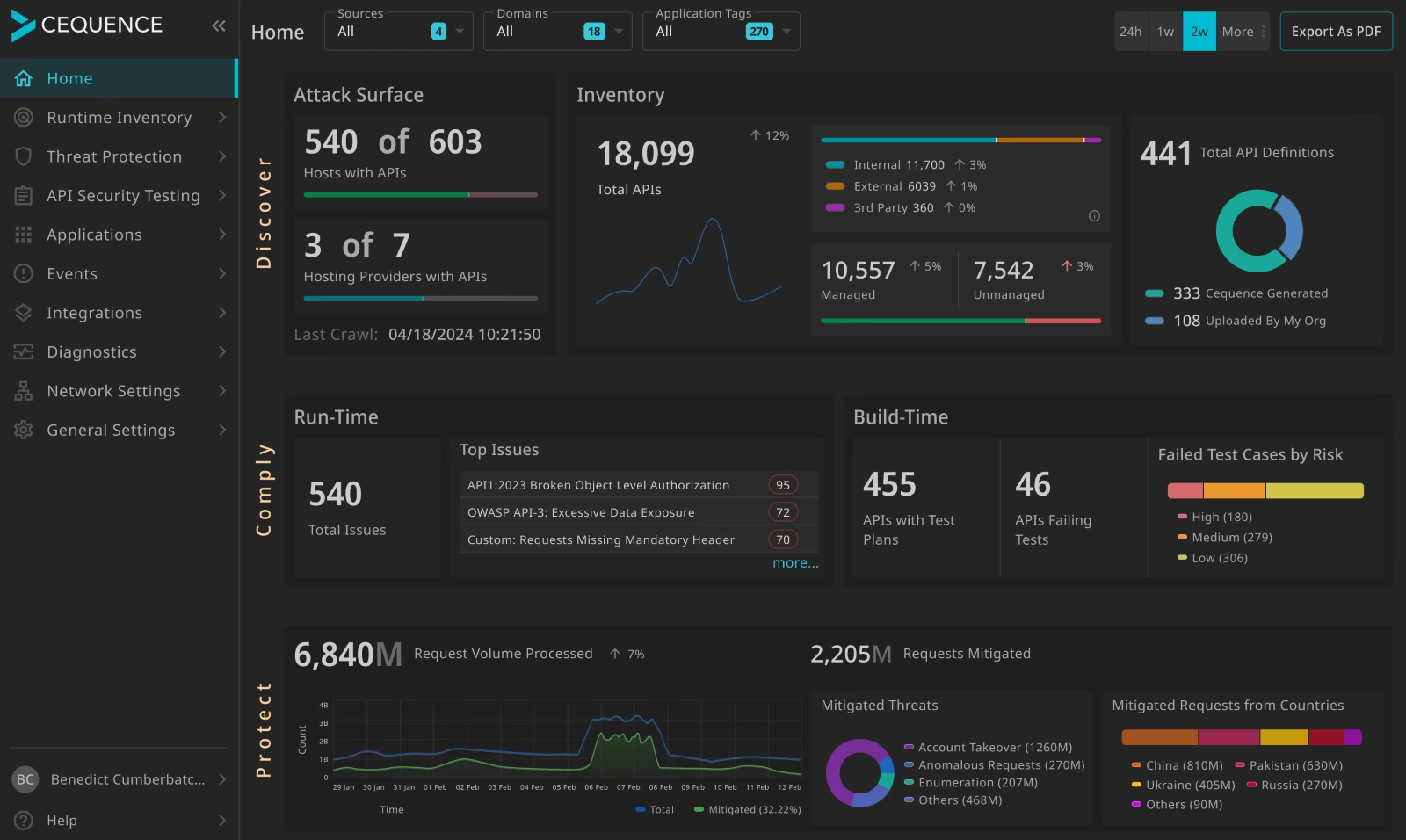
Image source: Cequence
Features:
Detection and prevention of API attacks through AI-driven methods.
Continuously provides API detection combined with threat evaluation.
Defensive measures against robotic intrusions and credential stuffing attacks.
Analyzes API behavior to detect anomalies.
Integration process with cloud and hybrid environments is seamless with its advanced features.
Choosing the Right API Security Vendor
An ideal API Security vendor can help security teams protect their APIs against multiple cyber threats, which ensure secure digital ecosystem. To choose an ideal API security vendor or API security companies, security teams should carefully evaluate numerous aspects such as:
Assess Scalability and Performance
Selecting a security platform that maintains performance while scaling efficiently is crucial. Assess the vendor's capacity to manage large traffic volumes while supporting load balancing mechanisms and sustaining minimal latency levels. The platform must dynamically adjust resources to handle fluctuating workloads while maintaining optimal functionality across varying conditions.
Check Compatibility with Existing Systems and Workflows
Existing systems including development and monitoring tools should experience flawless integration with the API security platform. Determine if the vendor maintains multiple API protocols and standards which enable legacy system updates without major overhaul. The security measures can work with your current workflows effortlessly without causing any disruptions, if there is compatibility.
Check Regulatory Compliance and Industry Standards
Make sure that the vendor's API platform complies with regulatory standards. Verify that the API security platform supports compliance requirements pertinent to your industry, such as GDPR, HIPAA, or PCI DSS. This alignment not only protects data but also mitigates the risk of legal implications.
Vendor Support and Updates
Reliable customer support and regular updates are important for maintaining strong security. Analyze vendor's support infrastructure such as response times and the availability of support channels. Ensure that the vendor is committed to provide timely updates and patches to address emerging threats and vulnerabilities, thereby ensuring continuous protection for your APIs.
Cost Considerations and Return on Investment
While cost is a significant factor, it is important to determine the value and security the API platform provides for the investment. Evaluate the pricing and licensing models of API security platform by considering your budget constraints and evaluate whether the cost aligns with the value offered. Some platforms provide flexible licensing options, such as pay-per-use or enterprise-level licensing, allowing scalability according to requirements.
Final Thoughts
To choose the right API vendor, it is very important for security teams to ensure seamless integration, security, and optimal performance. With numerous options available, understanding each vendor's strengths helps in making an informed decision. Prioritizing security, scalability, and compatibility ensures long-term success in API management.
By evaluating top API vendors and their unique capabilities, you can select the best fit for security teams needs. An all round API vendor helps improve efficiency, minimize risks and support growth. Explore your options carefully and invest in a vendor that aligns with your goals.
Akto.io is an ideal API security vendor for organization’s security teams that offers real-time API discovery, continuous monitoring, and automated security testing. It helps identify vulnerabilities, enforce security policies, and protect APIs from potential threats. With Akto, security teams can secure their API ecosystems effortlessly without disrupting operations.
Secure APIs effortlessly and Get Started with Akto. Book a demo today!
Want to learn more?
Subscribe to Akto's educational emails for essential insights on protecting your API ecosystem.

