APIs help in providing easy communication between various services, platforms, and systems. They also enable data sharing and integration for various platforms, from mobile applications to cloud-based services, which boost digital transformation. However, as usage of API is increasing, they become great targets for attackers.
Endpoints often expose APIs, expanding the attack surface for hackers. A poorly secured API can result in account hijacking, data leaks, system breaches, and financial losses. Attackers exploit flaws like weak access controls, poor authentication, and misconfigured endpoints to disrupt operations or gain unauthorized access.
This blog explores the OWASP API Security Top 10 risks and offers strategies to mitigate them.
Top 10 OWASP API Security Standards
APIs pose security weaknesses that malicious actors can exploit. The top 10 OWASP API security standards focus on possible breaches and threats that can reveal sensitive data and disrupt services. It is important to understand these security weaknesses to build a secure ecosystem for APIs.
1. Broken Object Level Authorization (BOLA)
Broken Object-Level Authorization (BOLA) arises when API endpoints fail to check if the user has proper authorization for a specific object. Attackers can check or modify unauthorized data when APIs do not enforce object-level access rules. APIs run many requests for data objects, and if these requests are not checked properly, attackers can change them to get unauthorized access and manipulate other users’ data. APIs that give object access based on user input without verifying permissions pose a security risk.
Organizations often overlook these attacks, so they must develop an effective security strategy to authenticate every API request correctly. This problem is common in APIs that handle personal, financial, or private information. Exploiting BOLA can result in data breaches, identity theft, and privacy violations.
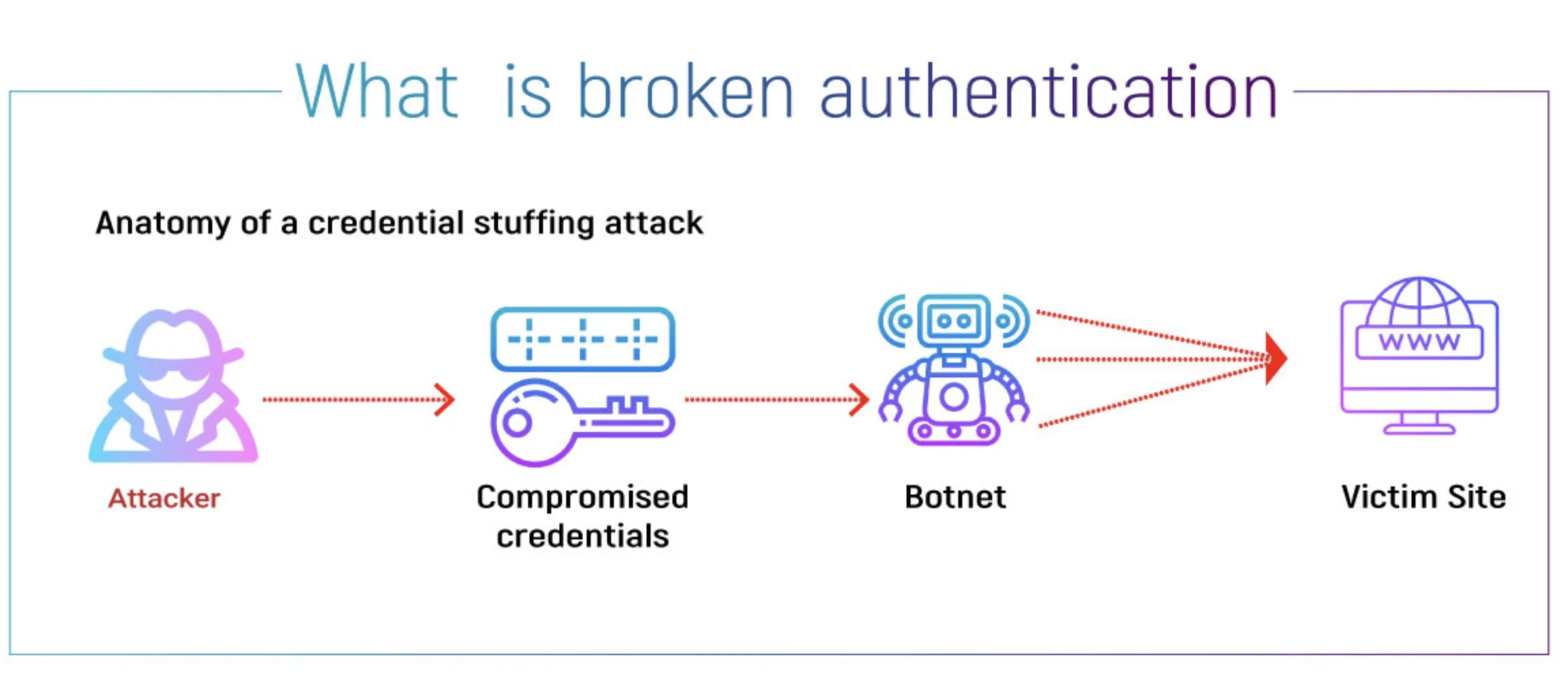
2. Broken Authentication
Source: https://prophaze.com/wp-content/uploads/2023/03/What-is-Broken-Authentication.jpg
Broken authentication occurs when users do not properly implement authentication or session management mechanisms. Authentication helps verify a user’s identity before accessing any application or service. If authentication weakens, attackers can gain unauthorized access to APIs, resulting in security breaches or system compromise.
Common types of broken authentication include weak passwords, a lack of MFA, poor session management, and exposed API keys. These allow attackers to bypass authentication using credential stuffing, brute-force attacks, and session hijacking. Another issue is insecure user session management, which allows attackers to gain access to active user sessions, impersonate actual users, and fail to protect session IDs. It can also result in account takeovers and data leaks, making users easy targets for attackers.
3. Broken Object Property Level Authorization (BOPLA)
Broken Object Property Level Authorization (BOPLA) occurs when an API fails to enforce authorization at an object's property (field) level, allowing attackers to access or modify restricted fields of data objects. This may reveal sensitive information and violate the access rules.
This issue is common in APIs that handle user authorization, financial data, or personal information. Attackers can modify data without proper security constraints and update or delete restricted data. This can have serious consequences and result in unauthorized system modifications, privilege escalation, and exposure of sensitive data. Apply strong property-level access controls to prevent such attacks.
4. Unrestricted Resource Consumption
Unrestricted resource consumption can significantly affect API stability and performance. It occurs when an API uses excessive system resources, which can result in slowdowns, system failures, and increased operating costs. APIs without resource limitations can also result in denial-of-service (DoS) attacks.
One typical example is APIs that enable batch processing, such as file uploads or mass database changes. With no restrictions, attackers can send repetitive queries that use memory, CPU, or bandwidth, reducing API performance. Without rate limitation, excessive requests can overload APIs, reducing availability for actual users. This is especially important for publicly exposed or high-traffic APIs. Enforcing usage restrictions improves service reliability and reduces resource exhaustion.
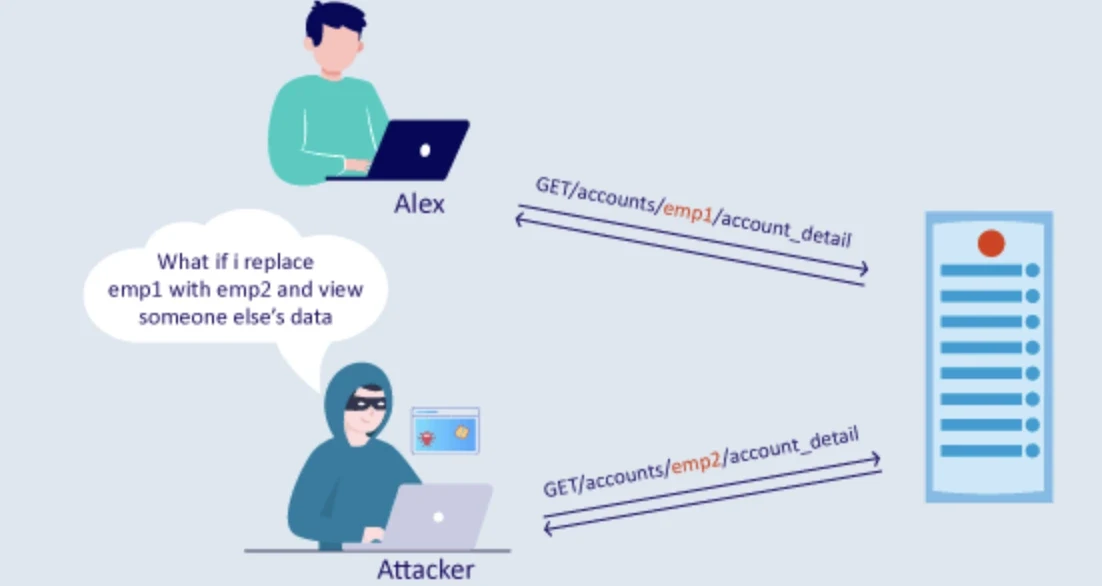
5. Broken Function Level Authorization
Source: https://www.indusface.com/wp-content/uploads/2022/01/API52019-Broken-Function-Level-Authorization.png
Broken Function Level Authorization is a significant security weakness that occurs when an API fails to enforce specific functions or operations permissions properly. This issue may allow unauthorized users to perform actions above their intended access level, and they can have access to privileged activities such as account modification and administrative functions.
Enforcing the concept of least privilege ensures that the system provides each user only the permissions required to do their tasks. This reduces the possibility of unauthorized function execution. Use function-level access control on the server rather than depending entirely on the client-side mechanisms that attackers can exploit. Organizations should apply proper role-based access control (RBAC), attribute-based access control (ABAC), or policy-based access control (PBAC) to effectively defend their APIs against broken function-level authorization attacks.
6. Unrestricted Access to Sensitive Business Flows
Unrestricted Access to sensitive business flows occurs when an API does not implement adequate access controls, allowing attackers to exploit necessary company operations or manipulate sensitive workflows. This vulnerability can have major consequences, especially for systems that handle financial transactions, supply chain activities, and other essential business operations.
This might result in malicious activities like unauthorized financial transactions, bulk data extraction, and exploiting business logic vulnerabilities. Attackers can automate the usage of these flows to exploit system vulnerabilities at scale. If organizations fail to secure them, attackers can immediately manipulate critical company workflows, posing financial and operational risks.
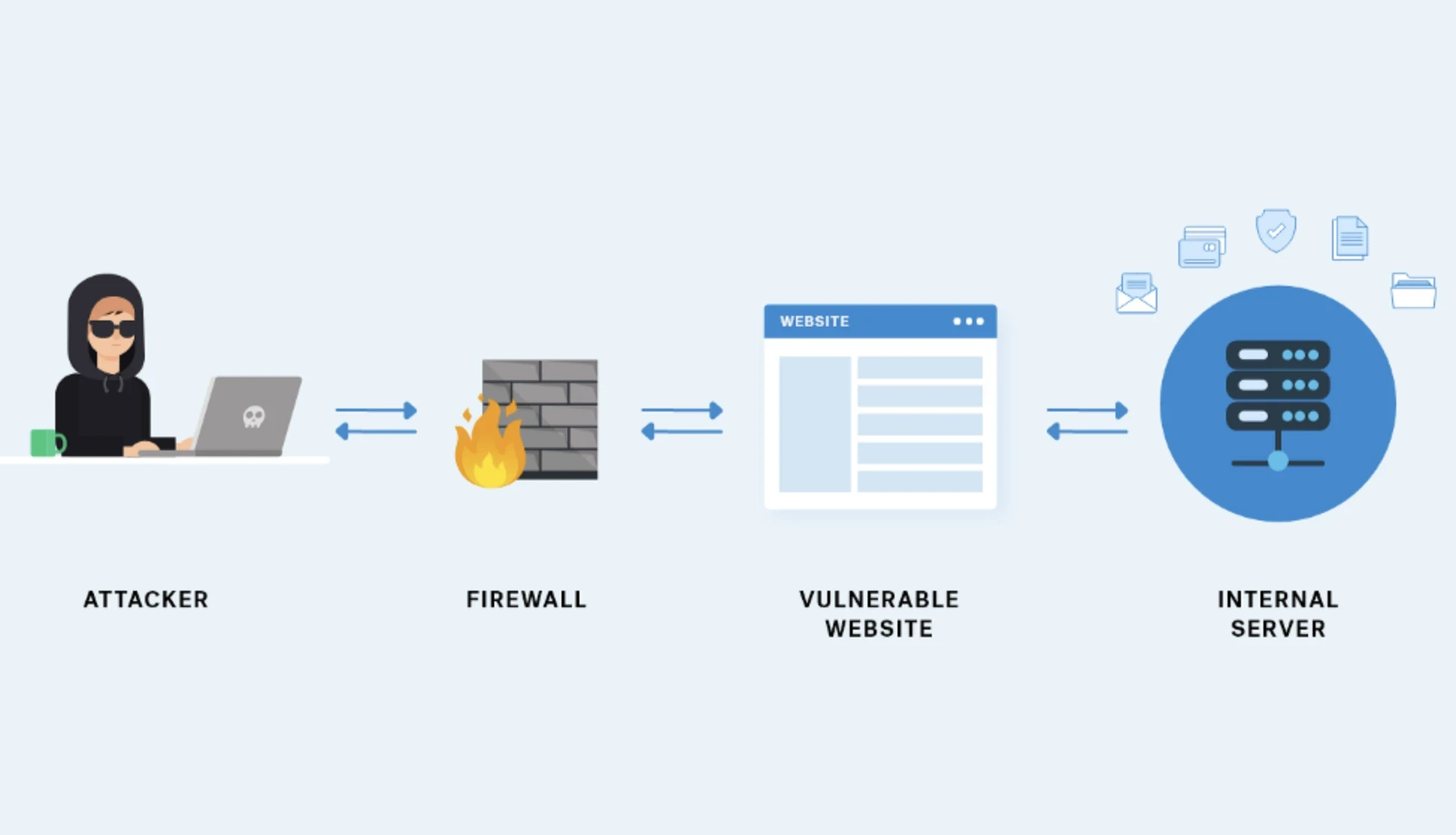
7. Server Side Request Forgery (SSRF)
Source: https://www.cobalt.io/hubfs/Imported_Blog_Media/SSRF-1.png
Server-side request Forgery (SSRF) is a significant security vulnerability that allows an attacker to modify a server into requesting internal and external resources that it should not access. This can lead to exposure of data, unauthorized access to data, and other possible consequences for organizations, such as credential theft, service abuse, or internal network reconnaissance.
In this attack, malicious actors can exploit functionality in a web application that accept user input for requests or URLs. They can direct the server to make requests to unauthorized internal services by manipulating the inputs.
8. Security Misconfiguration
Security misconfiguration occurs when security settings for an application, server, or API are missing, outdated, or poorly used. This includes default system configurations, insufficient network settings, or verbose error messages that reveal essential data. These misconfigurations allow attackers to check, modify, or steal data and exploit the system through malicious activities.
A single misconfiguration can expose an entire network to attacks, so organizations should take proactive security measures to secure API authentication, configurations, and access control. By staying alert and using proper security policies, organizations can minimize the risk of security misconfigurations.
9. Improper Inventory Management
APIs often have outdated, undocumented, or shadow endpoints that organizations fail to manage or protect. Attackers can use these abandoned APIs to exploit vulnerabilities that organizations have not fixed or adequately secured. Outdated endpoints can expose important data or allow unauthorized access without effective API version control and monitoring. Additionally, poor API inventory management causes security concerns and regulatory problems.
10. Unsafe Consumption of APIs
Organizations depend on third-party services for the APIs, but sometimes they fail to check external responses properly, which may possibly lead to unsafe consumption of APIs. Blindly trusting external APIs might result in data leaks, injection attacks, security breaches, or unauthorized transactions. APIs often serve as a bridge between different services, so if organizations do not correctly check API responses, attackers can manipulate data or exploit vulnerabilities.
For example, an application uses an external API for user authentication or financial transactions without first checking the API's responses. In that case, attackers can exploit the API, inject malicious code, bypass authentication, or gain unauthorized access to sensitive information. Similarly, an application using data from an unverified API without sanitization may lead to injection attacks and result in data damage or system compromise.
Final thoughts
API security is crucial since they are a common attack vector for attackers, which leads to sensitive data exposure and business logic. The OWASP Top 10 API Security detects security weaknesses such as broken authentication, unauthorized access, and security misconfiguration which marks the importance of strong security procedures. Organizations must implement strong authentication, authorization, rate limitation, and continuous monitoring to avoid breaches.
Akto is an API security platform that detects vulnerabilities, prevents attacks, and monitors real-time API traffic. Organizations benefit from automated API discovery, which provides complete visibility over all APIs, including shadow and outdated endpoints. Real-time security monitoring detects anomalies as they occur, preventing risks from escalating. Akto connects easily with DevSecOps workflows, improving security without disturbing development.
Schedule a demo today to learn how Akto can help you protect your APIs and avoid security breaches.
Want to learn more?
Subscribe to Akto's educational emails for essential insights on protecting your API ecosystem.

