Best Netsparker Alternatives and Competitors
Explore the top 10 Netsparker alternatives and competitors in 2025 for advanced web application security.

Kruti
Jan 22, 2025
APIs have become essential for modern organizations because they allow simple data sharing and integration. Netsparker is a popular web application security platform specializing in monitoring and protecting APIs. It specializes in automated vulnerability identification which allows organizations to discover and fix API vulnerabilities before attackers exploit them.
This blog explores the top Netsparker alternatives and gives organizations options to select the API security solution.
Top 10 Netsparker Security Competitors
Netsparker offers complete API security solutions, but other alternatives have distinct features and capabilities that are customized to a variety of organization requirements. Here are top 10 Netsparker alternatives and competitors.
1. Akto
Akto is an API security platform that helps organizations detect vulnerabilities regularly. It easily combines with CI/CD workflows to ensure the platform protects APIs before installation. Akto allows security engineers to protect APIs from new threats by providing behavioral analysis and automatic threat detection. This is lightweight, easy-to-use software, making it an excellent choice for small and medium-sized organizations and one of the best Netsparker alternatives.
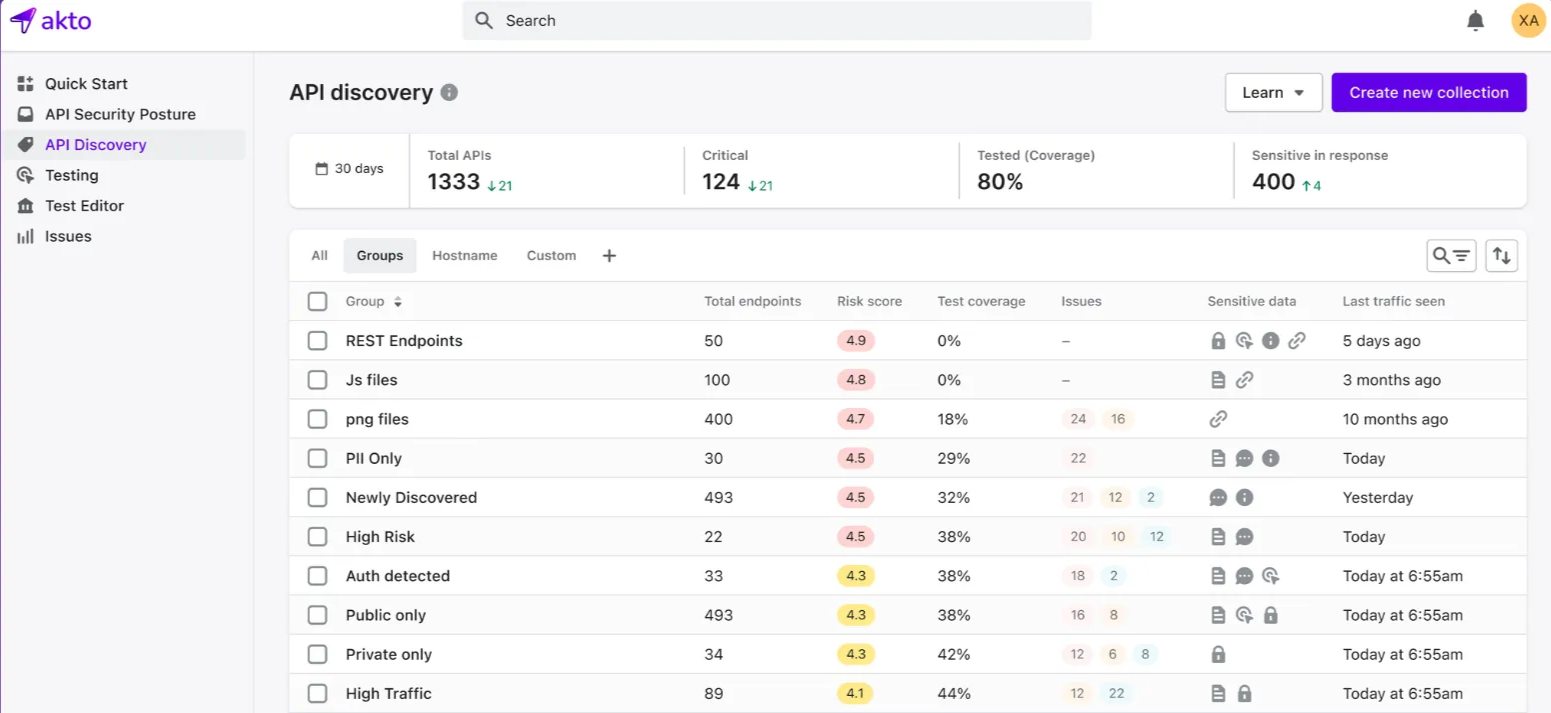
Features of Akto API
Automated API Discovery: It identifies all APIs across environments and ensures comprehensive security.
Real-Time Threat Detection: Monitors API traffic to detect malicious activity before it happens.
Behavioral Threat Detection: It uses machine learning to find irregular API usage patterns.
Role-Based Access Control (RBAC): Ensures users have permissions corresponding to their responsibilities.
Seamless CI/CD Integration: Seamless integration into development pipelines to ensure ongoing protection.
Advantages of Akto API
Comprehensive API Discovery: Ensures that no API is unprotected.
Easy-to-Use Interface: An easy-to-use interface simplifies installation and management.
Regular Analysis: It provides useful insights into possible risks.
Cost-Effective: Ideal for start-ups and medium-sized organizations.
Lightweight Design: Minimal impact on system performance.
Best For: Ideal for startups and small and medium-sized organizations that want a developer-friendly API security platform that can integrate with CI/CD workflows and DevSecOps teams seeking a lightweight, cost-effective solution.
2. Tenable Inc.
Tenable is a leading cybersecurity platform that provides complete vulnerability management solutions, including API security features. It allows organizations to find and handle vulnerabilities in their systems, including web applications and APIs, by improving network and data security. Tenable offers complete risk analysis and monitors current infrastructure rather than depending on API security, making it one of the top Netsparker alternatives.
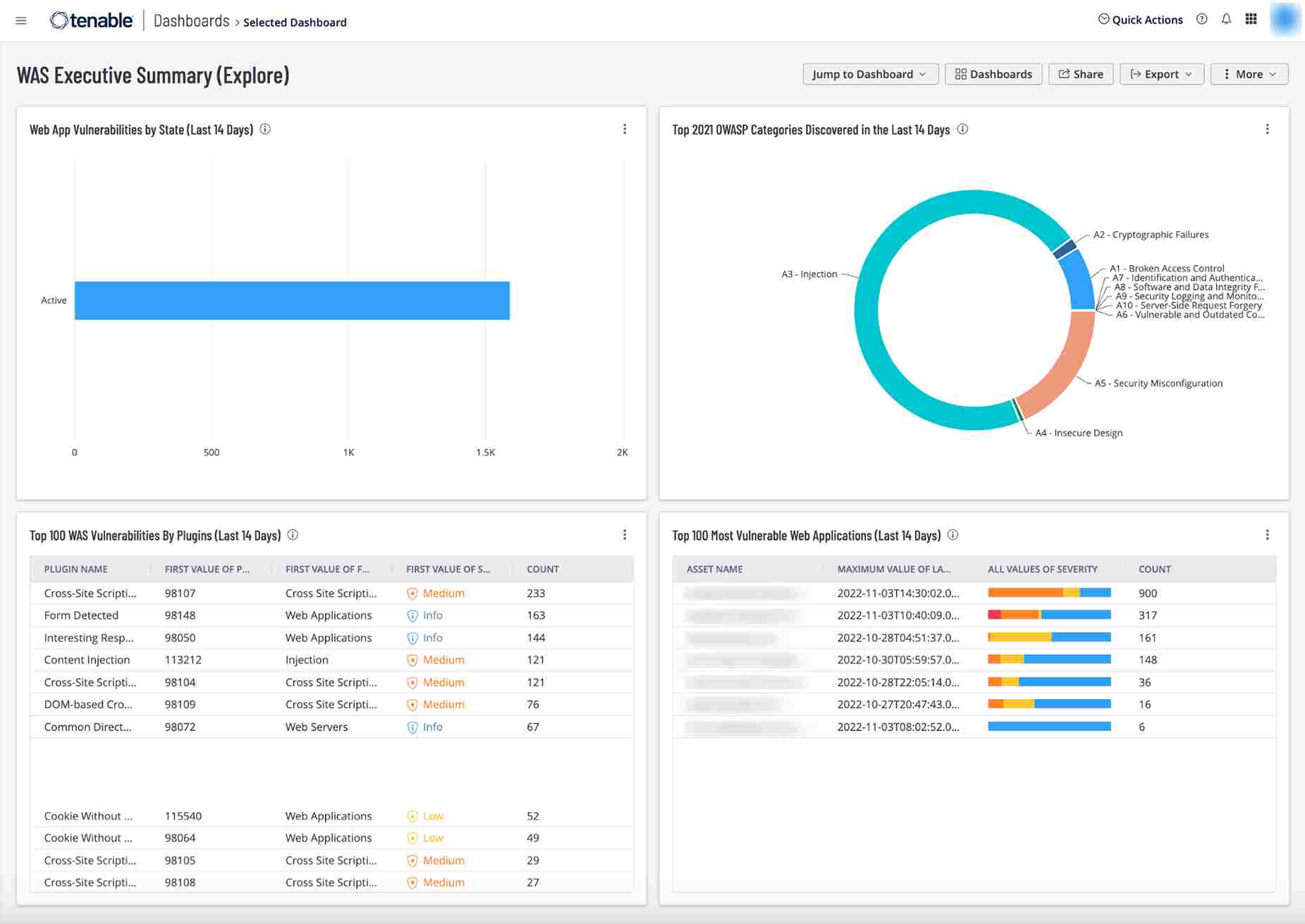
Source - Tenable Inc
Features of Tenable Inc.
Deep Vulnerability Scan: Identifies vulnerabilities across networks, online apps, and APIs.
Regular Monitoring: Provides real-time updates on security status throughout the infrastructure.
Prioritization Based on Risk: Prioritizes high-risk vulnerabilities for effective remediation.
Cloud Integration: Easily interfaces with cloud environments and services to ensure comprehensive API security.
Advantages of Tenable Inc.
Scalable for Large Enterprises: Can handle complicated, multi-cloud systems.
Real-Time Monitoring: Provides continuous supervision of overall infrastructure security.
Detailed Risk Reporting: In-depth reporting to help make informed decisions.
Disadvantages of Tenable Inc.
Complex Configuration: Initial setup may require professional expertise.
High Pricing Structure: Smaller organizations and startups may find it expensive.
Cloud-Heavy Focus: Some on-premises environments may find it less robust compared to hybrid or cloud capabilities.
Best For: It is for big organizations that need a full and flexible API and vulnerability management solution that covers networks, servers, and APIs. It is for organizations with complex infrastructures and needs deep risk analysis and regular monitoring.
3. Qualys
Qualys is a compliance and cloud-based security platform that offers vulnerability management, continuous monitoring, and API security. Its cloud-based architecture allows for smooth development and integration with current IT systems. Qualys provides real-time insights and actionable data on vulnerabilities, allowing organizations to secure their APIs efficiently across several settings.
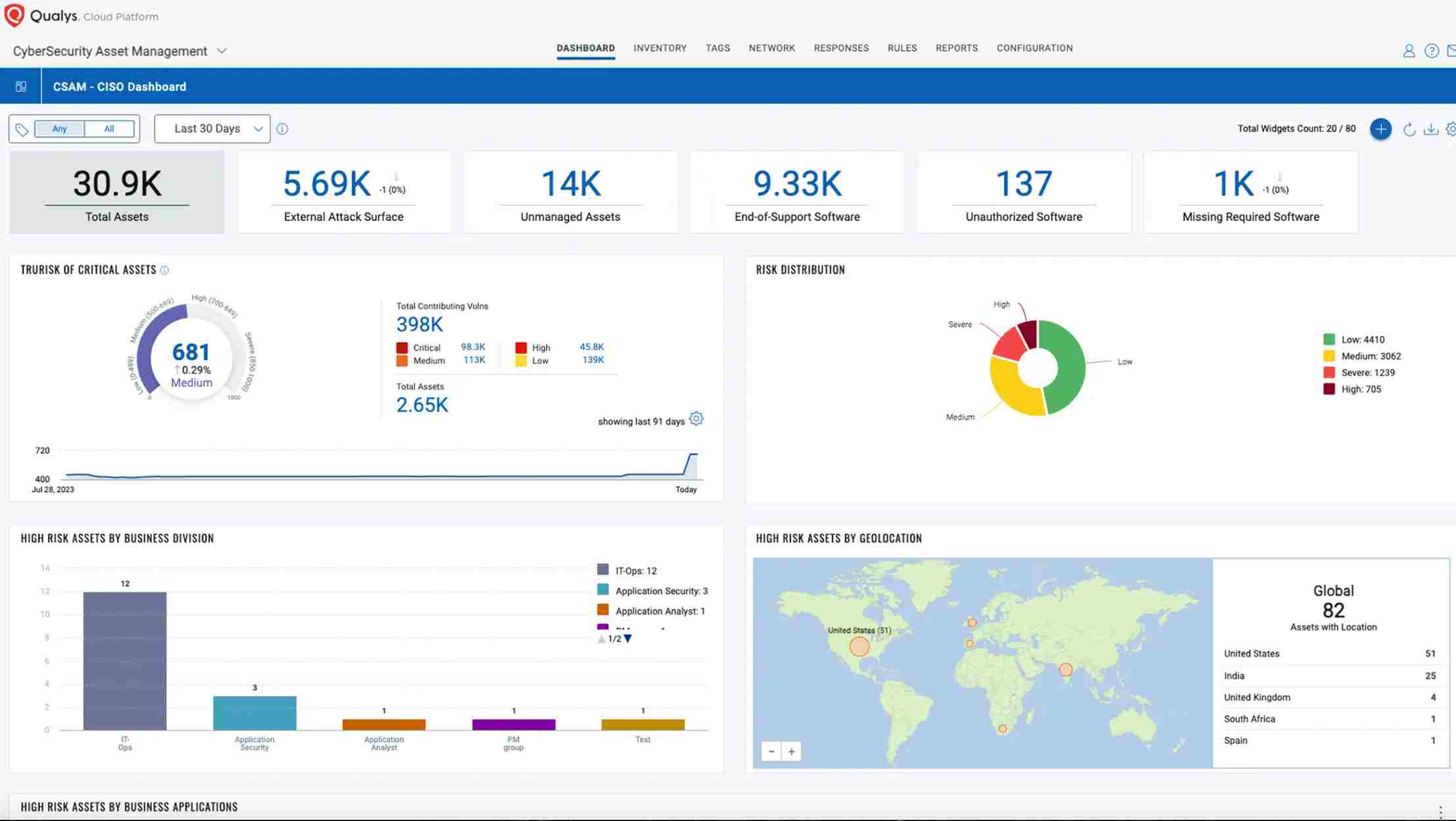
Source - Qualys
Features of Qualys
Automatic Vulnerability Scan: Detects vulnerabilities automatically across APIs and systems.
Regular Monitoring: Checks traffic and IT assets for irregular behavior or vulnerability signals.
Integrated Patch Management: Provides a specific module for quickly fixing vulnerabilities, although it does not automatically integrate with other systems.
Works on Cloud: Easily scales according to the needs of large organizations.
Comprehensive Compliance Coverage: Ensures vulnerability management and security meet industry standards.
Advantages of Qualys
Continuous Security: Enables real-time threat identification and monitoring.
Integrated with Existing Systems: Works seamlessly with other security solutions and IT infrastructure.
Adherence Management: Assists organizations in complying with security regulations.
Easy Interface: It has an easy interface that simplifies vulnerability management for IT teams.
Disadvantages of Qualys
Pricing for Small Businesses: Small organizations and startups may find it expensive.
Dependence on the Cloud: Not suited for organizations that need on-premises solutions.
Best For: It is for organizations of all sizes who want platforms based on the cloud for vulnerability management software that allows complete security, compliance, and regular monitoring. It is for organizations that need flexible solutions across several IT environments.
4. Pynt
Automated API security testing allows organizations to find vulnerabilities before they grow. It makes APIs strong before deployment and reduces risks. It combines easily with existing CI/CD systems and ensures deep testing without interruptions in the workflow.
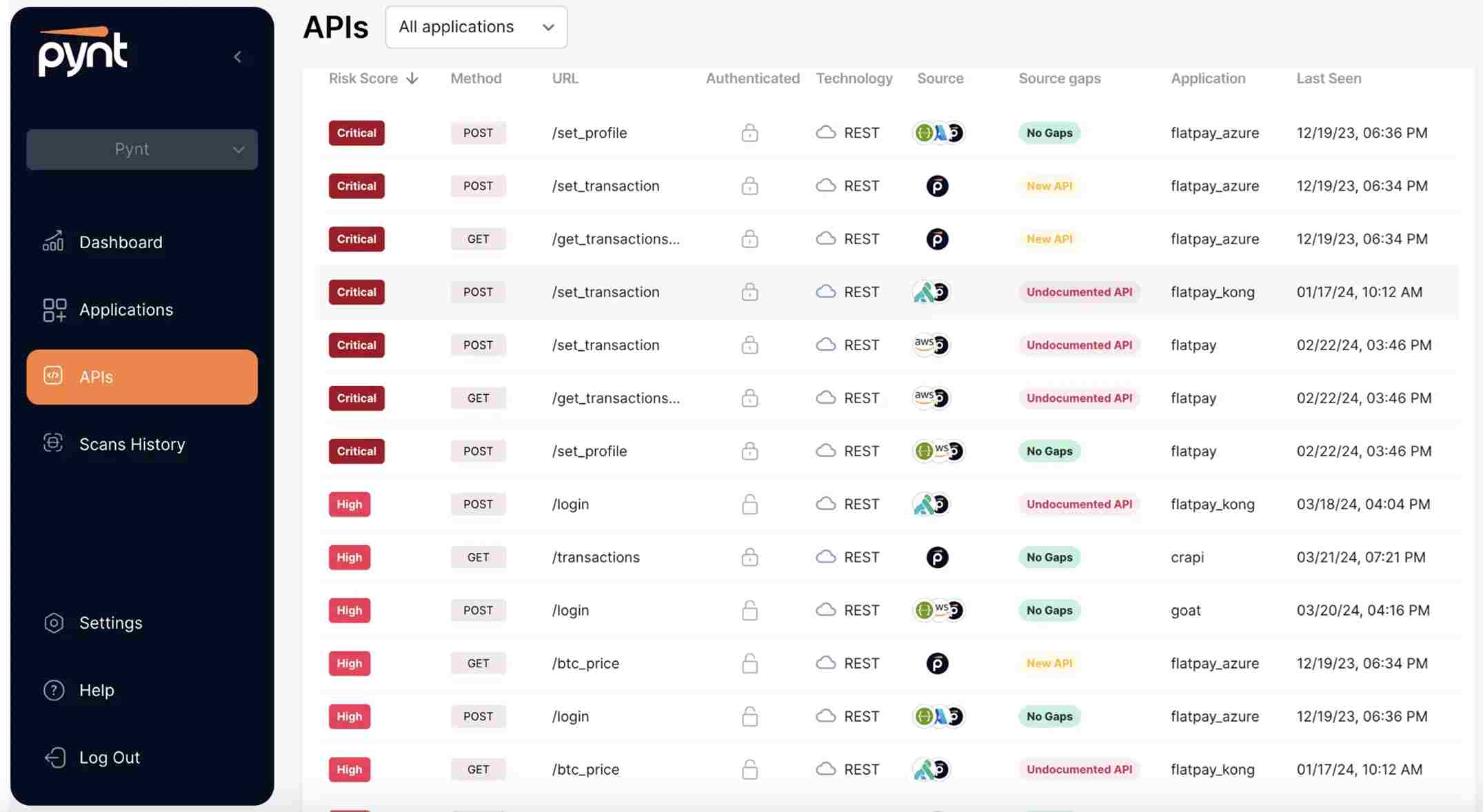
Source - Pynt
Features of Pynt
Automatic Security Testing: Pynt performs automatic analysis with zero human intervention.
Connect Easily with CI/CD Pipelines: It connects seamlessly with CI/CD pipelines and performs security checks throughout the development process.
Complete Vulnerability Detection: Performs complete tests to find potential API vulnerabilities.
Advantages of Pynt
Customized Testing: Changes to specific organizational requirements.
Deep Insights: Provides thorough information for addressing vulnerabilities.
Disadvantages of Pynt
Hard to Learn: For the best results, initial training may be required.
High Initial Costs: Pricing may not suit smaller organizations.
Dependence on Automation: Manual testing has limited flexibility.
Best For: Organizations looking for an automated and scalable API security solution with excellent CI/CD integration.
5. Burp Suite
Burp Suite is a platform to test web applications and APIs. It offers various features for security testing and allows API security as well as vulnerability detection. It has various tools to perform manual and automatic testing. Burp Suite finds vulnerabilities such as SQL injections and XSS and provides information to fix them.
Source - Burp Suite
Feature of Burp Suite
Complete Security Testing: Identifies a wide array of vulnerabilities in web applications and APIs.
Automated Crawling: Web applications are scanned automatically for quick potential problem identification. API crawling might be needed to configure differently.
Advanced Manual Testing Tools: Includes exploit tools used manually like Repeater, Intruder, and Sequencer.
Extensible Platform: The level of extensibility is great with both third-party plugins and extension support along with custom scripts through BApp Store and API.
Detailed Reporting: Creates comprehensive reports with practical remedial techniques.
Advantages of Burp Suite
Comprehensive Vulnerability Coverage: Finds a wide range of vulnerabilities in web applications and supports API testing
Extensive Customization: Plugins and extensions make it possible to customize almost anything.
Regular Testing: Performs regular testing and allows to quickly detect security issues.
Easy to Use Interface: It is an easy-to-use interface that allows security teams to explore and test APIs.
Active Community: A large user community that provides assistance and resources.
Disadvantages of Burp Suite
Hard to Understand: This may be hard for beginners or those who are unfamiliar with security testing.
Expensive: Pricing may be costly for smaller organizations or startups.
Heavy Resources: Large-scale testing may consume significant system resources.
Best For: Security engineers and penetration testers seeking a sophisticated, customized solution for comprehensive web application and API security testing. Ideal for medium to big organizations that need both automated and manual vulnerability assessments.
6. Rapid7
Rapid7 offers a large collection of security tools that include vulnerability management, application security, and API security. It allows organizations to proactively handle vulnerabilities, detect API threats, and maintain compliance. Rapid7 focuses on automation to reduce manual work and accelerate cleanup. The platform connects smoothly with existing security systems which results in an organized approach to threat management.
Source - Rapid7
Features of Rapid7
Vulnerability Management: Detects and resolves vulnerabilities across APIs and networks.
Real-Time Threat Detection: Provides ongoing monitoring of API activity for potential threats.
Automated Solution: Offers automated remediation options to avoid risks quickly.
Compliance Monitoring: Ensures that API security meets industry standards and laws.
Connects Easily: Easily connects to current security infrastructures.
Advantages of Rapid7
Comprehensive Coverage: Secures APIs, applications, and networks.
Automation for Efficiency: Reduces the need for manual involvement in threat detection and cleanup.
Scalable Solution: Suitable for organizations of all sizes, from small to medium-sized organizations.
Disadvantages of Rapid7
Expensive: Startups may find pricing expensive.
Hard to Install: It is tough to install, and initial installation needs proper understanding.
Dependent on Cloud: Less appropriate for on-premises environments.
Best For: Organizations looking for an automated security solution that manages API, network, and application security and want to expand their security operations while staying compliant with industry requirements.
7. Postman
Postman is one of the popular testing tools for APIs. It supports functional and performance testing in developing and testing an API. Generally, it offers developers and teams tools for testing, debugging, and monitoring APIs. Security teams do not primarily use it as a security tool, but custom scripts and external integration help carry out basic security testing.
Source - Postman
Features of Postman
Automatic API Testing: Performs automatic API testing and allows functional and performance testing of APIs.
Security Testing with Scripts: Security teams can write custom scripts to test for security scenarios like authentication or rate-limiting concerns.
API Monitoring: Constantly evaluates API safety and performance.
Easy Collaboration: Teams can work on API development and testing.
Advantages of Postman
Easy Interface: Developers with limited security knowledge will find it easy to use.
Continuous Monitoring: Ensures that APIs stay secure throughout their lifecycle.
Extensive Integrations: Works with other security products to provide better protection.
Disadvantages of Postman
Reduced Security Features: There is no automated vulnerability scanning and deep security testing in Postman.
Basic Security Testing: Lacks penetration testing features, unlike other platforms.
Requires Understanding of Postman: To gain optimum results, users must know the Postman environment.
Best For: This is for small and medium-sized organizations that need a simple tool to test, debug, and monitor APIs during development. Postman also supports basic security testing through scripting and integrations with security tools.
8. Checkmarx
Checkmarx provides various security testing tools, including robust API security capabilities, as part of its broader application security platform. It has a dependable approach to detecting vulnerabilities across APIs and the software development life cycle. Checkmarx excels at integrating with DevSecOps procedures, allowing security teams to address API security concerns proactively.
Source - CheckMarx
Features of Checkmarx
Static Application Security Testing (SAST): Analyzes source code to identify vulnerabilities before deployment.
Dynamic Application Security Testing (DAST): Examines APIs and web apps in real time for potential risks.
CI/CD Integration: Integrates seamlessly with DevSecOps pipelines to ensure continuous security.
Vulnerability Reporting: Generates thorough reports with solutions and recommendations.
Advantages of Checkmarx
Comprehensive Coverage: Enables both static and dynamic security testing.
Deep Insights: Provides deep and actionable vulnerability reports.
Advanced Analytics: Provides significant data for increasing API security.
Disadvantages of Checkmarx
Complex Setup: Implementation may require professional expertise.
Pricing Structure: Smaller organizations may find it expensive.
Resource Intensive: Comprehensive analysis may require significant computing resources.
Best For: It is for organizations looking for a complete API security solution that connects with DevSecOps workflows and regularly finds and fixes API vulnerabilities throughout the development lifecycle.
9. OWASP ZAP (Zed Attack Proxy)
It is an open-source security testing tool that is used for protecting web applications. It has advanced features for API penetration testing and vulnerability scanning. OWASP ZAP also provides active and passive scanning modes, and developers and security teams use it to detect and mitigate API security issues.
Source: OWASP ZAP
Features of OWASP ZAP
Active and Passive Scanning: Provides manual and automated scanning options for complete security assessment.
Customizable Add-Ons: It supports extensions to improve functionality, making it extremely customizable.
WebSocket Support: Enables testing of WebSocket-based APIs.
Integration with DevOps Pipelines: Uses CI/CD tools to integrate security testing into the development process.
Cross-Platform Compatibility: Runs on different operating systems that are Windows, Linux, and macOS.
Advantages of OWASP ZAP
Free & Open Source: Offers a complete toolkit at no expense, making it available to all organizations.
Extensive Documentation: Provides extensive tutorials and community to help organizations.
Customizable and Extensible: Add plugins and configure the tool to meet their needs.
Disadvantages of OWASP ZAP
Steep Learning Curve: For beginners, mastering can require a significant amount of time and effort.
Limited Support: Depends on community support rather than personalized customer service.
Best For: OWASP ZAP is ideal for security engineers and teams that value flexibility and customization. It is for organizations with professionals who can use its advanced features for deep penetration testing and vulnerability checks.
10. Astra Security
Astra Security is a complete security solution for APIs, websites, and applications. Its API security services include vulnerability scanning, compliance reporting, and complete evaluation of risks. Astra Security is well-known for its simplicity and efficiency, making it suitable for small to medium-sized organizations looking for a clear yet efficient security platform.
Source - Astra Security
Features of Astra Security
Continuous Vulnerability Scanning: Automatically detects and reports API and application vulnerabilities.
Compliance Reporting: Assists organizations in complying with standards such as GDPR, PCI DSS, and HIPAA.
Penetration Testing: Combines automatic scanning with skilled hand testing to provide a full security analysis.
Security Dashboard: Provides a clear, centralized view of vulnerabilities and remediation efforts.
Advantages of Astra Security
Complete Security Testing: Provides both automatic and manual penetration testing for the best coverage.
Regular Alerts: Provides regular alerts and informs teams about the threats as they occur for quick response.
Affordable Pricing: Provides flexible options ideal for small to medium-sized organizations.
Disadvantages of Astra Security
Limited Advanced Features: Enterprise-level platforms may not have as many sophisticated tools.
Not Ideal for Large Organizations: It is designed primarily for smaller companies.
No Free Tier: Unlike several competitors, Astra does not provide a free version for small projects.
Best For: Astra Security is best for small to medium-sized organizations that need automated vulnerability scanning, manual testing, and compliance help and want a user-friendly platform for API and application security.
How to Choose the Best API Security Solution for an Organization
Choosing the correct API security solution is an important step toward protecting APIs from emerging threats and vulnerabilities. Here is what to consider when selecting an API security solution:
Security Capabilities and Coverage
The API security solution should possess the basic features to protect against a broad range of vulnerabilities. Choose solutions that offer automatic vulnerability identification, real-time threat monitoring, and behavioral analytics on a large scale. Regular monitoring ensures the system finds threats as early as possible, responds to them accordingly, and provides effective protection against various threats.
Integration of Development Pipelines
A secure API solution must seamlessly work with an organization's CI/CD process. This ensures that security is always an automated part of the development process, which helps in catching and removing vulnerabilities as early as possible. It connects easily with CI/CD systems and allows security engineers to simplify workflows, find issues during development, and maintain security without affecting the development flow.
Flexibility
API security solution should be flexible and can meet an organization's growing needs. This requires dealing with an increase in the traffic of API, managing more complexity as an organization adds more APIs to its system and adapting to this changing security landscape. To support infrastructure requirements, organizations must also select a system that offers different flexible deployment options, such as both cloud and on-premise deployment.
Usability and UI
While the solution must have sophisticated capabilities like AI-based threat detection, it needs to be easy to use. A well-designed interface allows security engineers to see traffic, find vulnerabilities, and act appropriately with quick speed. Dashboards should clearly report to help teams function better.
Final Thoughts
Netsparker is a web and API security solution that features advanced features, such as automated vulnerability detection, real-time threat monitoring, and behavior analytics. But organizations can also look at other options for their unique needs and financial plans. There are numerous options similar to Netsparker, which meet the varied requirements of firms. This site offers many traits, such as complete automation to API-related protections with adaptability and integration potential. Each site has its benefits that help firms pick a solution addressing the particular security needs of the firm and its goals.
Akto is a developer-centric platform that makes real-time threat detection, behavior-based analysis, and seamless integration into modern development workflows. They have an easy-to-use interface and are for organizations of any size in the pursuit of API security effective, fast scalable.
Schedule a demo today to learn about how Akto can help organizations with API security.
