Best OWASP ZAP Alternatives and Competitors
Explore the top OWASP ZAP alternatives in 2025 to enhance your web application security and vulnerability testing.

Kruti
Jan 20, 2025
API security is critical for organizations that depend on APIs for data exchange and require strong safety to prevent breaches, keep sensitive data, and maintain industry compliance.
OWASP ZAP Security is a platform for identifying vulnerabilities in web applications using dynamic application security testing (DAST). It provides features like automated scans, proxy detection capabilities, and incorporation options for ongoing security testing.
This blog explores the top OWASP ZAP alternatives to help security engineers make the right decisions for their organizations.
Top 10 OWASP ZAP Security Competitors
OWASP ZAP is a strong platform for protecting APIs, but organizations should look at alternatives for additional features that meet their preferences and modern CI/CD workflows. Below are the top 10 OWASP ZAP alternatives and competitors, each with unique API security features.
1. Akto
Akto is an API security platform that helps organizations protect their APIs with automated vulnerability scanning and threat detection. The platform smoothly combines with CI/CD pipelines and allows security engineers to monitor and protect APIs throughout the development lifecycle. Akto adjusts to the changing needs of various API configurations and provides complete data to help organizations protect their APIs.
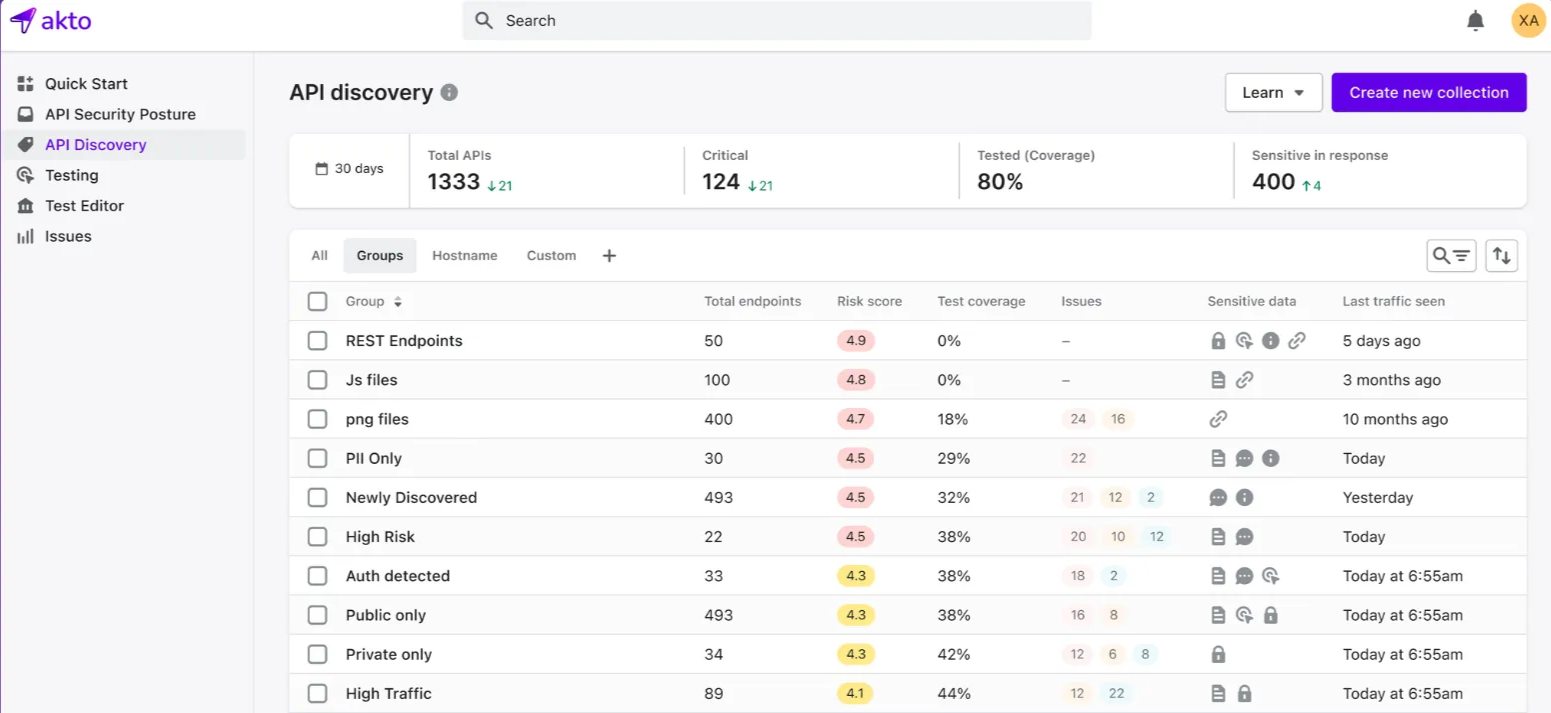
Source: Akto.io
Features of Akto
Automatic Vulnerability Detection: It allows the detection of vulnerability automatically and reduces the need for manual testing.
Regular Monitoring: Monitors APIs regularly to ensure security during development and deployment.
Deep Reporting: It Provides complete reports to reduce security risks.
Seamless CI/CD Integration: Easily interfaces with CI/CD pipelines to ensure continuous security testing.
Advantages of Akto
Flexible Dashboards: Security teams can create dashboards to display vital security information.
Quick Alerts: Provides instant notifications of vulnerabilities for quick response.
Best For: Akto is ideal for organizations with dynamic APIs that require automated security monitoring. It is intended for organizations who already use CI/CD pipelines and are looking for a platform that works easily into their workflows.
2. Burp Suite
Burp Suite is a security platform that scans web apps and APIs using human and automated testing methods. It allows security engineers to analyze the security of web applications and APIs. Burp Suite is among the best OWASP ZAP alternatives for vulnerability testing.
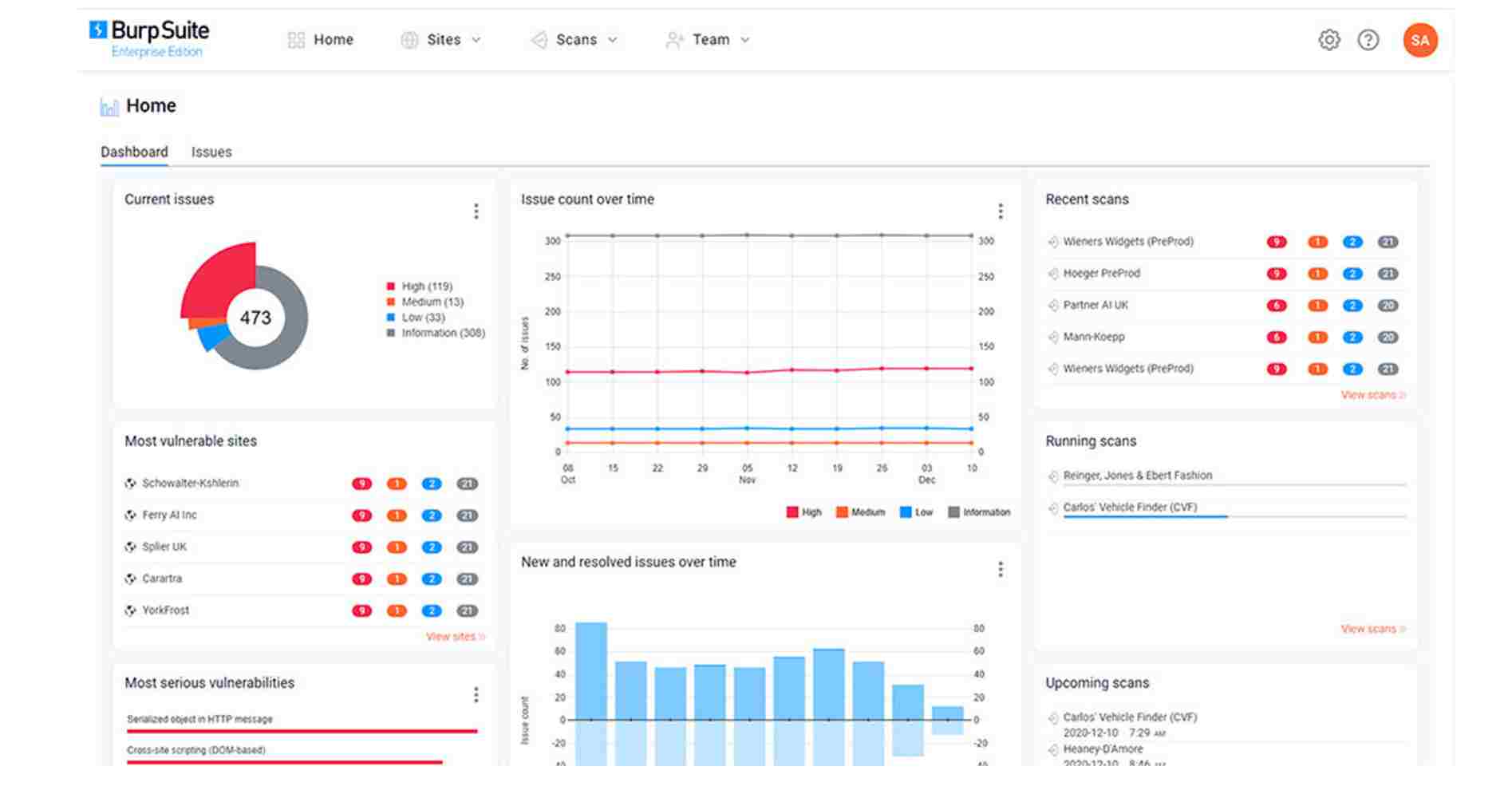
Source: Burp Suit
Features of Burp Suite
Vulnerability Scanning: Scans and finds vulnerabilities in web applications and APIs.
Customizable Testing: Create scanner profiles to meet unique testing needs.
Manual Testing Support: Provides tools for performing manual penetration testing to find complex vulnerabilities.
Reporting: Provides vulnerability reports by highlighting vulnerabilities and giving fixation advice.
Expandable: Plugins can expand the tool to find and fix security threats.
Advantages of Burp Suite
Comprehensive Testing Capabilities: Supports automated and manual testing for detailed vulnerability evaluations.
Deep Reporting: Provides complete reports and helps organizations to detect and resolve vulnerabilities.
Active Community: Burp Suite has a wide user base and provides a variety of tools and plugins.
Disadvantages of Burp Suite
Required Resources: It can be demanding for the system to perform deep scans.
Hard to Understand: Beginners may struggle to understand and use all of its features.
Costly: it may be expensive for smaller organizations.
Best For: Burp Suite is for security experts testing web apps and APIs, both manually and automatically. It’s for organizations who are looking for a complete vulnerability management and penetration testing solution.
3. Netsparker (now Invicti)
Netsparker is now referred to as Invicti which is a web application and API security scanner that finds vulnerabilities automatically. It uses modern technology to discover and prioritize significant vulnerabilities, making it appropriate for both small and large organizations. Invicti allows to deeply scan APIs and focuses on giving accurate results and reducing false positives.
Source: Netsparker
Features of Netsparker
Automated Vulnerability Scanning: Detects flaws in web applications and APIs automatically.
Low False-Positive Rate: Provides reliable results by limiting false positives and identifying only actual vulnerabilities.
Combine with CI/CD Pipelines: Easily combines with CI/CD pipelines and allows for continuous security testing.
Detailed Vulnerability Reporting: Provides deep reports with fixation advice.
Advantages of Netsparker (now Invicti)
Accurate Scanning: Low false positives reduce the amount of time spend evaluating unneeded concerns.
Flexible: Able to handle complex problems and adjust to the needs of large companies.
Deep Reports: Use vulnerability reports to prioritize and resolve issues.
Broad Vulnerability Coverage: Includes the OWASP Top 10 and other vulnerabilities.
Disadvantages of Netsparker (now Invicti)
Complex for Beginners: Some features and installation options may be difficult for beginners to understand.
Needs Resources: Deep scans demand a significant amount of resources.
Expensive: The pricing plan may be costly for small organizations.
Best For: Invicti is an effective automated security solution for organizations of all sizes with complex web application and API security need
4. Qualys Web Application Scanning (WAS)
Qualys Web Application Scanning (WAS) is a platform for organizations operating in the cloud. It allows them to scan web apps and APIs for vulnerabilities. As part of the Qualys Cloud Platform, organizations can regularly monitor and secure web applications. Qualys WAS offers powerful automatic scanning and integration features, making it perfect for organizations that require continuous online security.
Source: Qualys
Features of Qualys
Automated Vulnerability Scanning: Regularly scans web apps and APIs for weaknesses.
Cloud-Based Platform: Provides scalability and flexibility in cloud deployment.
Combine with Qualys Cloud Platform: Combines easily with other security solutions on the Qualys platform.
Compliance Management: Helps to achieve compliance obligations by implementing security best practices.
Comprehensive Vulnerability Coverage: Identifies weaknesses in web apps, APIs, and underlying systems.
Advantages of Qualys
Expandable Cloud-Based Solution: Easily expandable to meet increasing web security requirements.
Comprehensive Reporting: Includes detailed vulnerability findings and specific remedy actions.
Disadvantages of Qualys
Limited Customization: Security engineers may find the reporting and scanning choices restrictive.
Required Cloud Infrastructure: The cloud-based nature may not be suitable for organizations that restrict their cloud resources.
Expensive: May be too expensive for small organizations with less funds.
Best For: Qualys WAS is for organizations that are based on the cloud and looking for a flexible platform that follows adherence rules. It is for big organizations that have complex security needs.
5. Acunetix
Acunetix is a comprehensive web vulnerability scanner that detects and mitigates security problems across web apps and APIs. Its powerful scanning algorithm detects SQL injections, cross-site scripting, and other important flaws. It smoothly integrates with CI/CD pipelines to enable DevSecOps approaches.
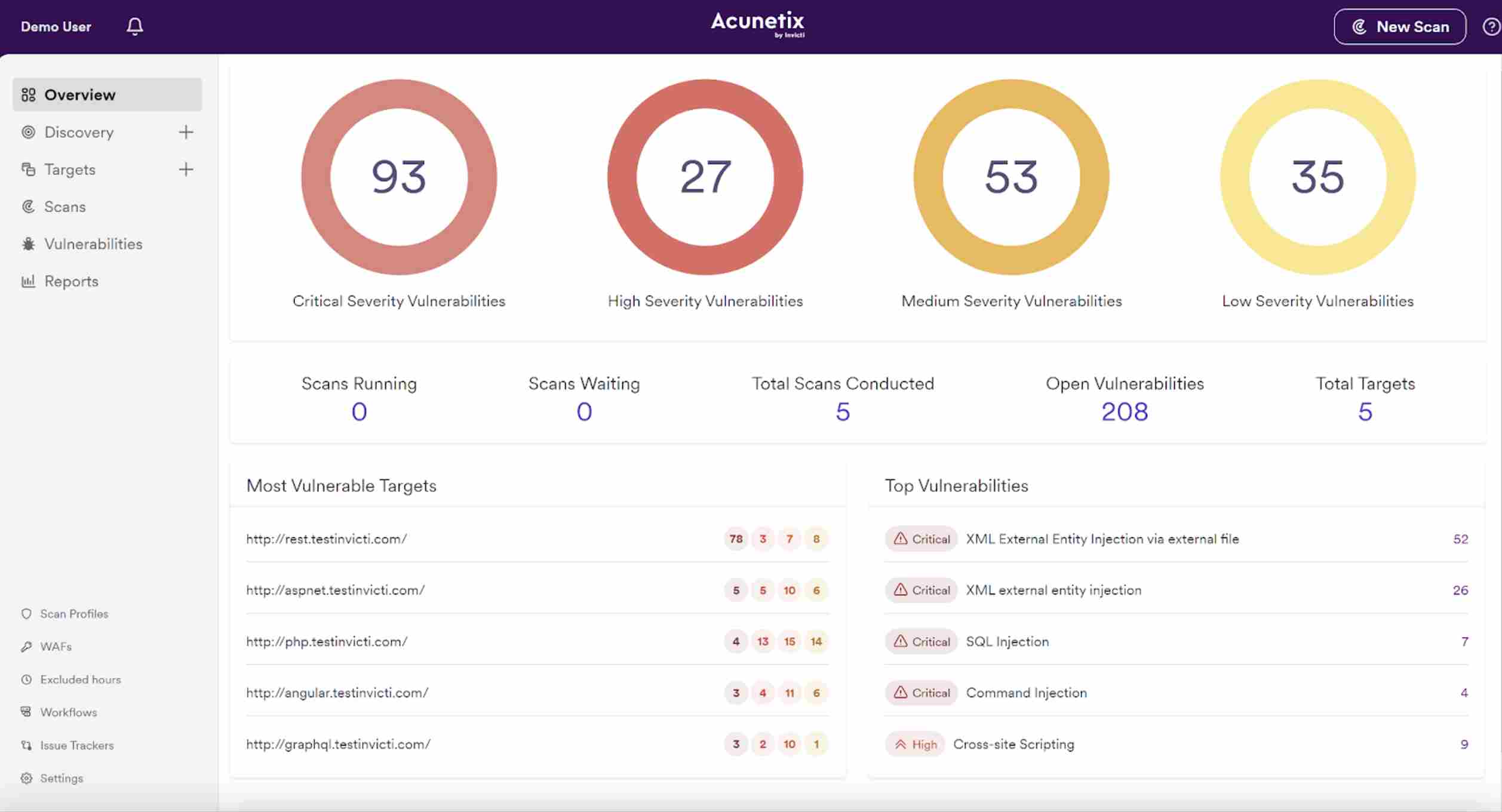
Source: Acunetix
Features of Acunetix
Vulnerability Detection: Identifies multiple vulnerabilities, including the top ten OWASP.
Automatic Scanning: Scans huge and complex applications without human involvement.
Support Multiple Systems: Supports multiple operating systems, including Windows, Linux, and Mac OS.
Safety Reporting: Offers full adherence reports for PCI DSS, HIPAA, and other standards.
Continuous Integration: Integrates with CI/CD technologies to perform automatic security tests.
Advantages of Acunetix
High Accuracy: Intelligent detection algorithms reduce false positives, resulting in higher accuracy.
Fast Scanning: Provides quick scans without sacrificing detail or accuracy.
User-Friendly Interface: Even non-experts can easily navigate and configure the system.
API Security Testing: Includes specialized tools for thorough API testing.
Disadvantages of Acunetix
Cost: The price may be higher than certain options.
Learning Curve: Advanced features can require training for successful use.
Resource-Intensive: Scanning large apps might need significant system resources.
Best For: Organizations looking for an automated vulnerability scanning platform use this platform. Ideal for organizations that want compliance reports and smooth CI/CD connection and want high accuracy with low false positives.
6. AppSpider
AppSpider is an automated online application and API vulnerability scanning tool that performs extensive security testing on dynamic web apps. Users use AppSpider to detect vulnerabilities in both old and new application structures, including APIs.
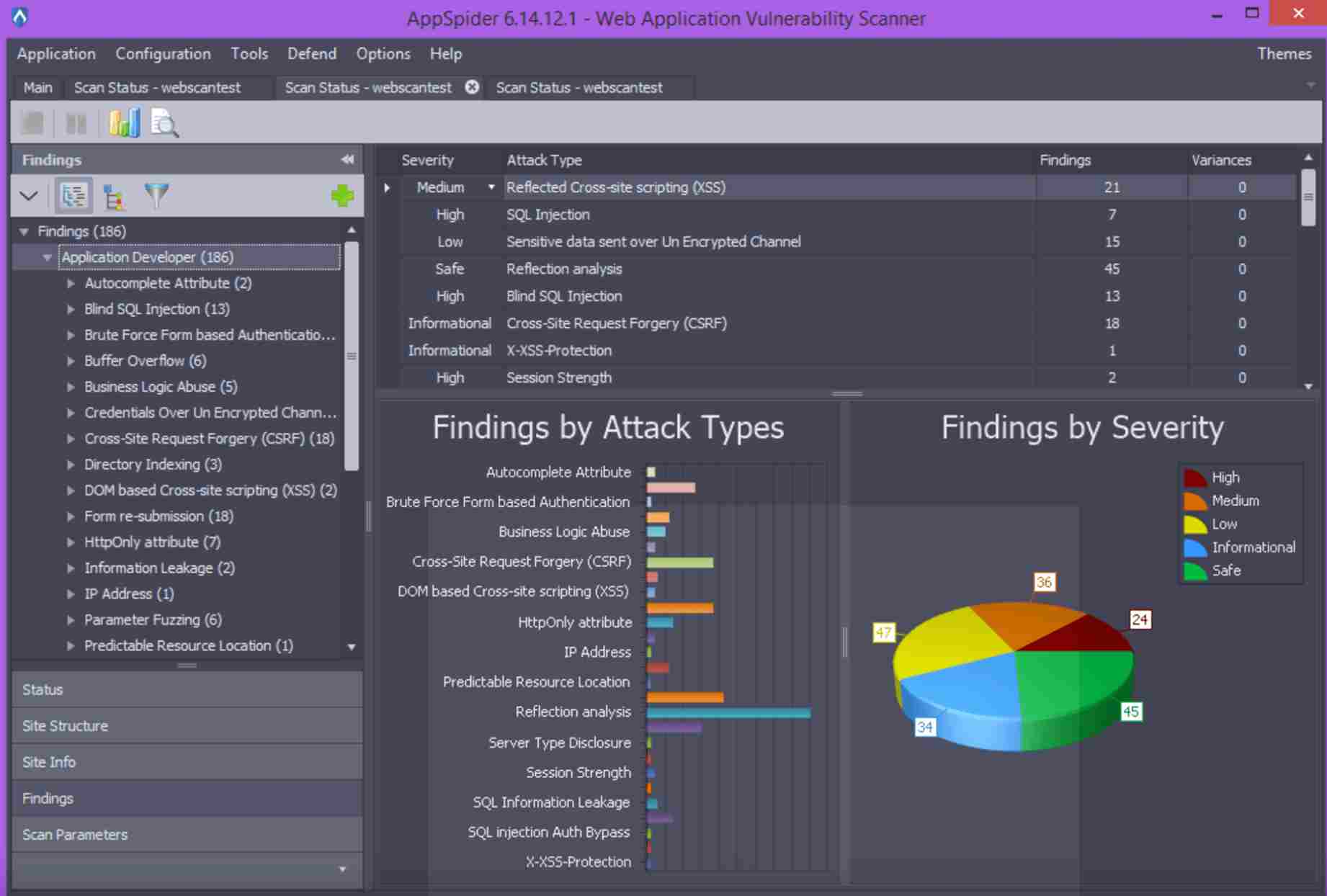
Source: AppSpider
Features of AppSpider
Dynamic Scanning: Identifies vulnerabilities through dynamic crawling and scanning techniques.
API Security Testing: Identifies weaknesses in REST and SOAP APIs.
Vulnerability Detection: Identifies vulnerabilities during scans and provides deep insights.
Deep Reporting: Provides deep vulnerability reports with fixation solution.
Combine with CI/CD Workflows: Easily combine with CI/CD pipelines for regular security testing.
Advantages of AppSpider
Deep Vulnerability Detection: Detects a wide range of vulnerabilities, including those particular to APIs.
User-Friendly Interface: It makes it easy for security engineers to configure and operate.
Scalable to Huge Organizations: Can manage big, sophisticated applications and API environments.
CI/CD Integration: Enables smooth integration into development pipelines for continuous testing.
Disadvantages of AppSpider
High Resource Consumption: Scanning large apps can be resource-intensive, requiring significant computational power.
Complex for Beginners: Beginners may struggle to properly comprehend and use some functions.
Pricing: This may be higher for smaller businesses or teams.
Best For: AppSpider is excellent for organizations that need automated, scheduled scanning of web apps and APIs. It is ideal for medium to big organizations with complicated security testing requirements.
7. Pynt
Pynt is a specialized API security testing tool that works flawlessly throughout the development process. It detects API vulnerabilities while guaranteeing compliance. Pynt is lightweight and developer-friendly, focusing on simplicity and efficiency in improving API security.
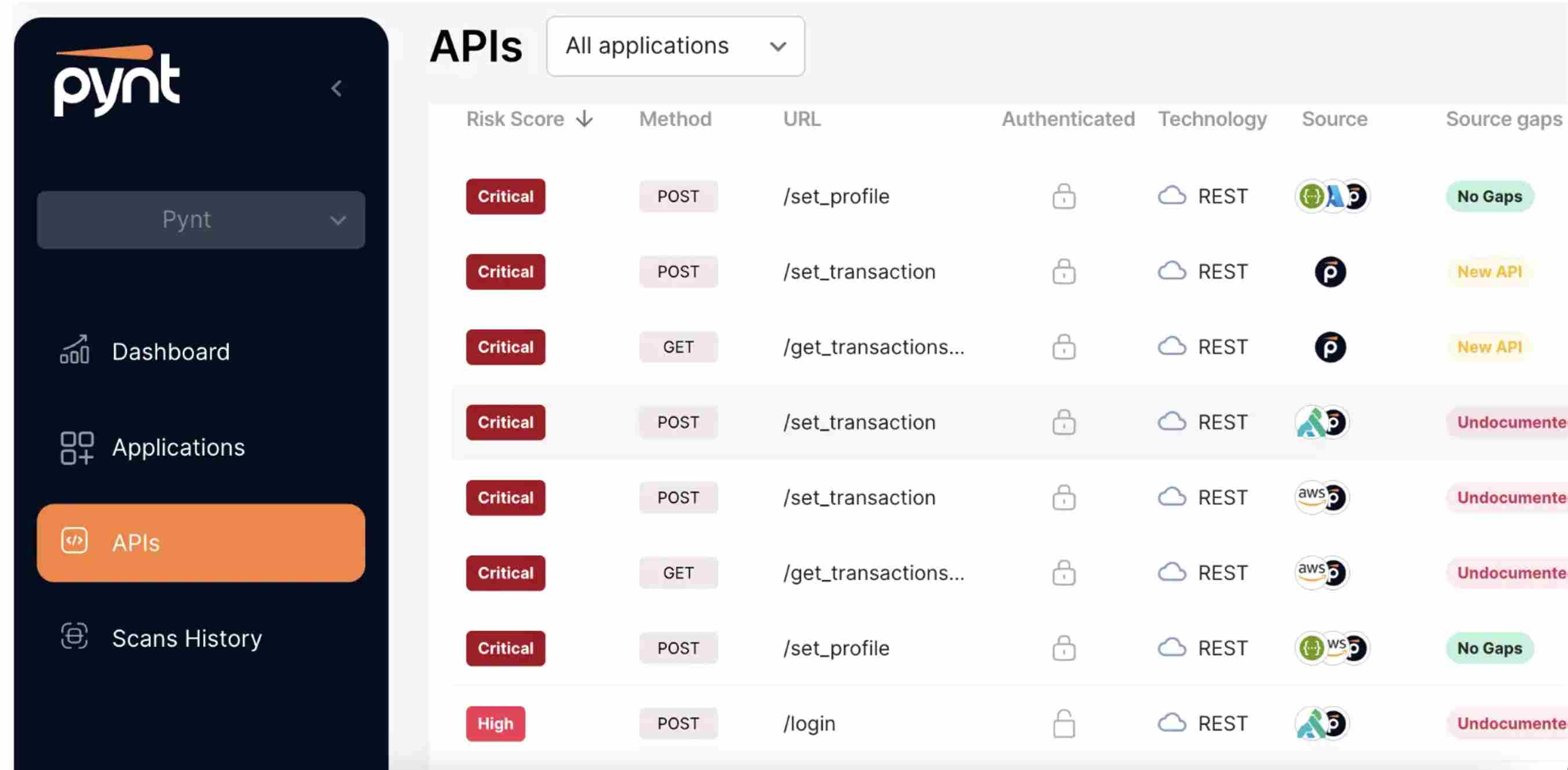
source: Pynt
Features of Pynt
API-Centric Scanning: Identifies security flaws at APIs – for example, broken object-level permission.
CI/CD Incorporation: Merges API security assessments directly into the development process.
Automated Examination: Develops and executes automated security tests with relatively low effort.
Live Reporting: Offers prompt feedback, enabling repairs that much sooner.
Developer-Friendly Architecture: Tuned for ease of use and fit with developer workflows.
Advantages of Pynt
Lightweight Solution: Minimal effect on performance and resources.
Immediate Feedback: Prompt identification of security issues with an equally prompt possibility for remediation.
Easy To Use: A very friendly interface for developers.
Disadvantages of Pynt
Narrow Scope: It was aimed only at API security and not broader application security solutions.
Smaller Feature Set: This may not meet enterprise-level security requirements.
Dependence on CI/CD: Ideally used in environments with established DevOps techniques.
Best For: It is for API security teams that work in fast-paced DevSecOps environments and want to connect security checks directly into CI/CD pipelines.
8. Glitch Secure
Glitch Secure is a security tool based on the cloud for startups and small organizations. It prioritizes ease of use and accessibility while offering critical application security features. Glitch Secure provides strong security features that help protect organizations from threats, vulnerabilities, and potential breaches.
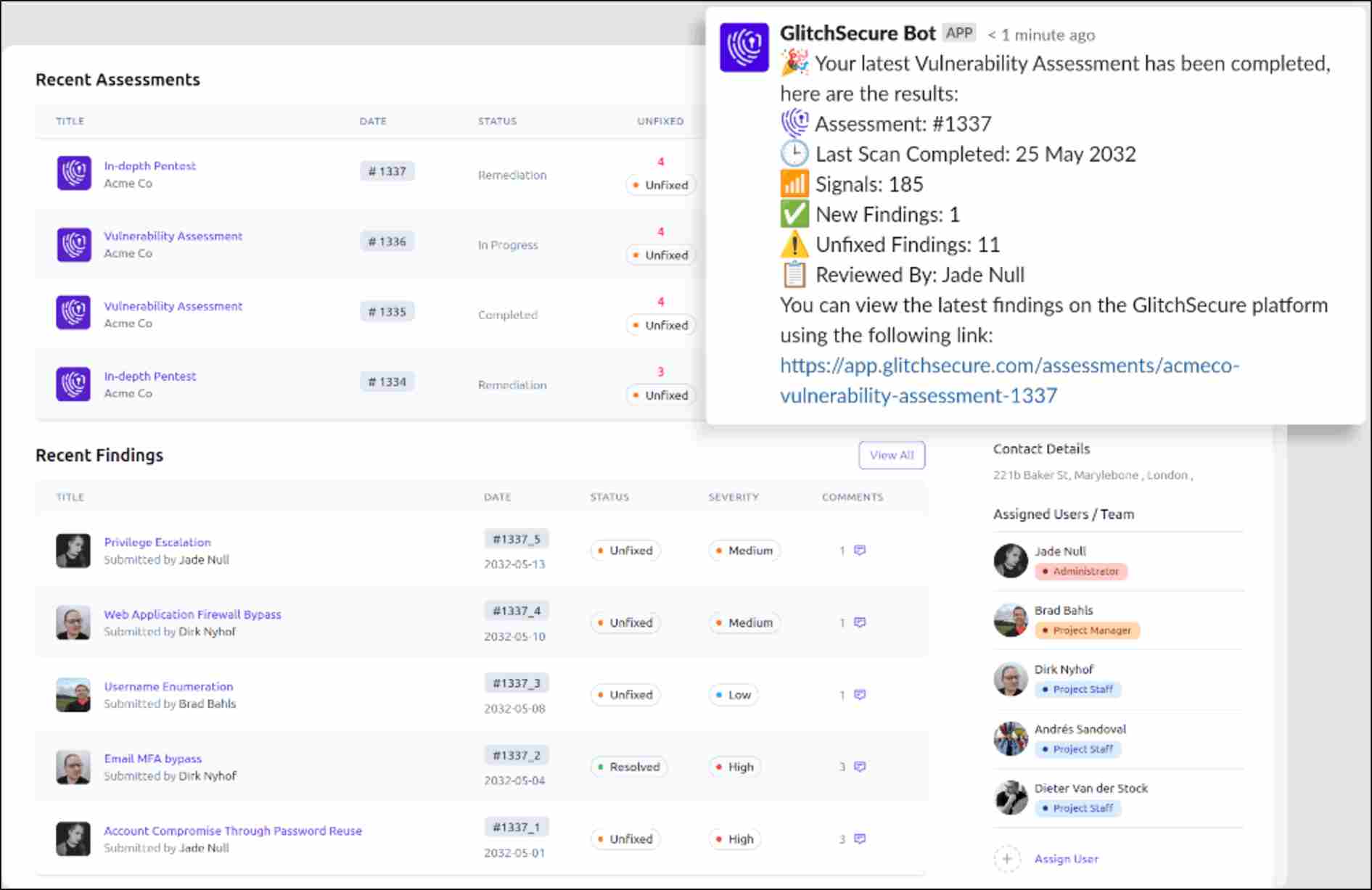
Source: Glitch Secure
Features of Glitch Secure
User-Friendly Dashboard: Simplifies security administration through an easy interface.
Flexible Architecture: Easily adjusts to the organization's growth and growing needs.
Affordable Solution: Offers different pricing for startups and small organizations.
Advantages of Glitch Secure
Easy Setup: Quick to deploy without requiring substantial technical knowledge.
Budget-Friendly: The smaller teams might benefit from affordable price alternatives.
Deep Monitoring: Performs deep monitoring to address important vulnerabilities and threats.
Based on Cloud: This platform is based on the cloud so it is available from anywhere with the internet.
Disadvantages of Glitch Secure
Limited Advanced Features: This may not be adequate for larger companies with complex security needs.
Basic Customization: There is less flexibility in personalizing security tools.
Dependence on the Internet: Requires stable Internet access for proper operation.
Best For: Startups and small teams seeking an easy-to-use, comprehensive application security solution. Ideal for organizations that want security during the early development stages and value ease of use and cost-effectiveness.
9. Data Theorem
Data Theorem is a security platform that protects mobile and web applications. It performs regular vulnerability detection and automatic security scans and provides deep insights to help organizations secure sensitive data and assure compliance. Data Theorem combines smoothly into development workflows to provide greater protection without affecting productivity.
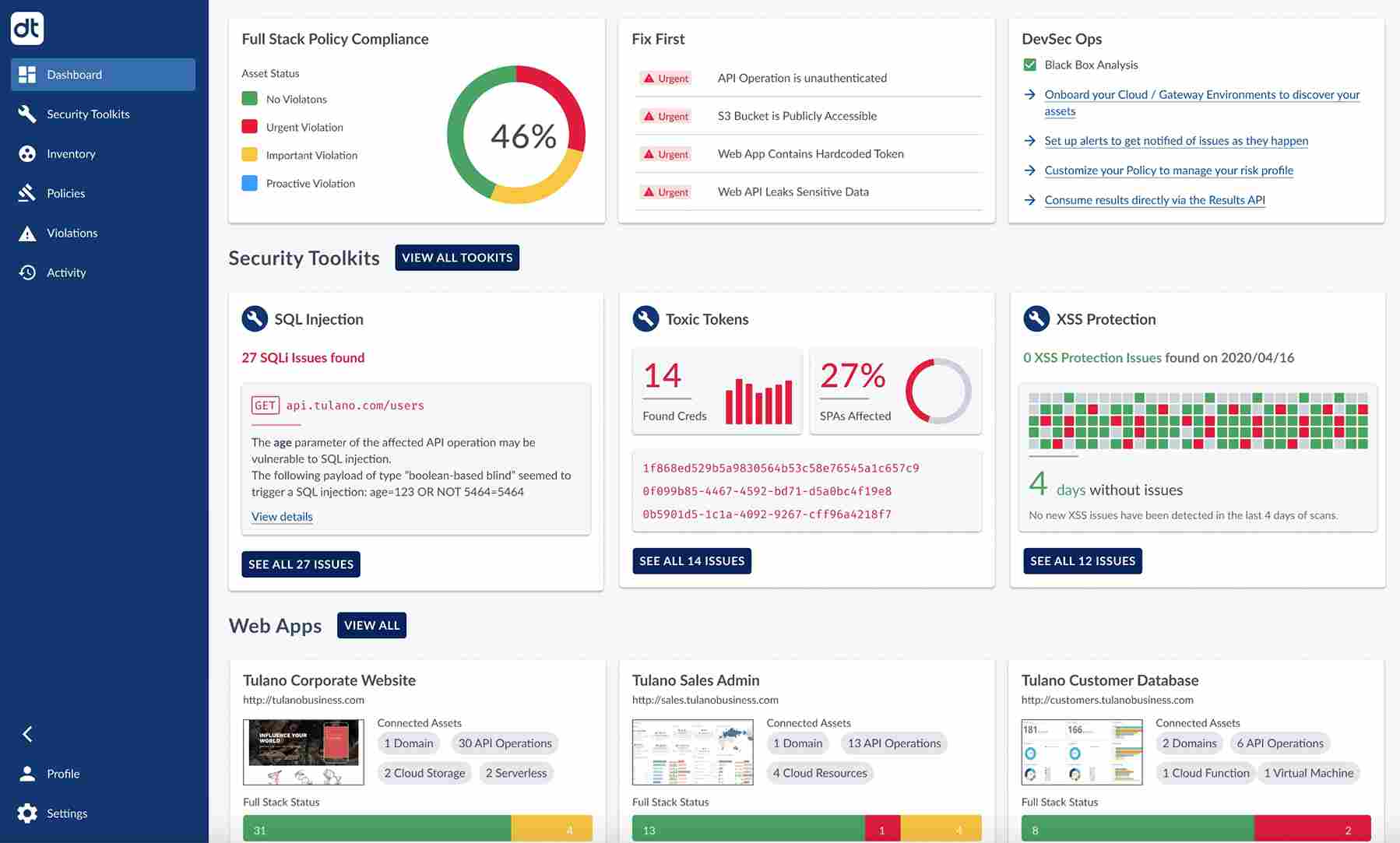
Source: Data Theorem
Features of Data Theorem
Automated Scanning: Automatically scans and detects vulnerabilities.
Follow Compliance Rules: Follow adherence rules according to industry standards such as GDPR, HIPAA, and PCI-DSS.
Deep Reporting: Provides deep security reports with fixation advice.
Seamless Integration: Easily interfaces with CI/CD pipelines to assist DevSecOps processes.
Advantages of Data Theorem
Complete Security: It protects both mobile and web applications.
Immediate Insights: Provides quick alerts and deep insights to resolve issues quickly.
Easy-to-Use Interface: Provides an easy-to-use interface to developers and security teams.
Flexible Solutions: Adapts to companies of different sizes and phases of development.
Disadvantages of Data Theorem
Cost: Small organizations may find advanced features costly.
Learning Curve: Beginners may need instruction during the first setup and usage.
Limited Offline Functionality: This relies largely on cloud infrastructure, and it may be difficult to use offline.
Best For: Data Theorem is for organizations who want full security solutions to protect mobile and web applications. Organizations that want a platform that smoothly integrates security into their development processes will find Data Theorem suitable.
10. Astra Security
Astra Security is an API and website security solution that offers real-time protection against cyber attacks. It protects websites and APIs by detecting malicious programs, scanning vulnerabilities, and installing firewalls. Astra uses both proactive and reactive security measures to protect applications from known and unknown attackers.
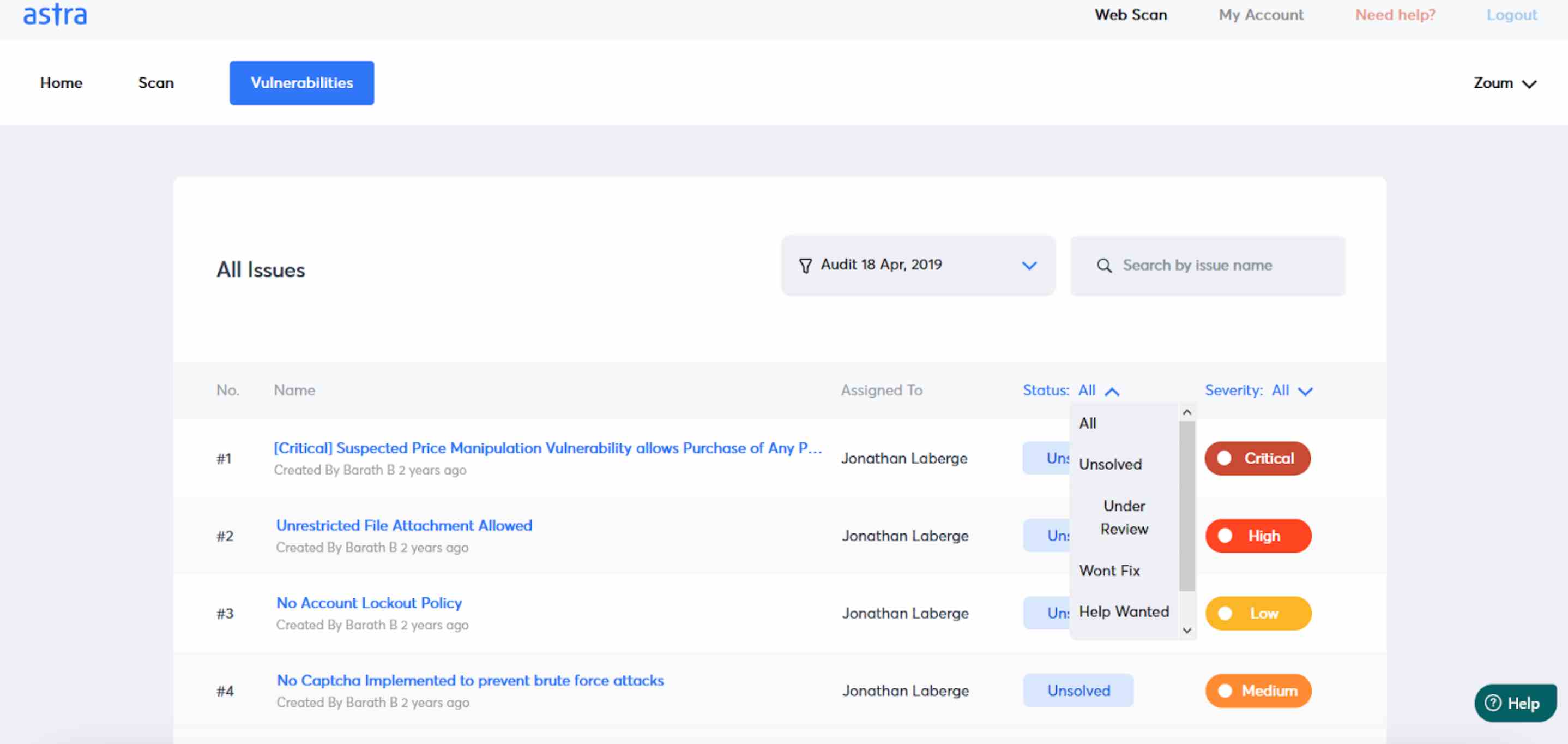
Source: Astra Security
Features of Astra Security
Threat Detection: Monitors APIs and webpages for malicious activity and vulnerabilities.
Malware Detection and Removal: Detects and removes malware from websites and APIs.
Firewall Protection: A strong firewall protects web applications and APIs from external threats.
Vulnerability Scanning: Looks for flaws in online apps and APIs to avoid breaches.
Detailed Security Reports: Provides actionable information about threats and vulnerabilities.
Advantages of Astra Security
Comprehensive Vulnerability Scanning: Run thorough tests to detect a wide range of vulnerabilities in various applications and APIs.
User-Friendly Dashboard: A simple interface for monitoring security status, team progress, and repair efforts.
Seamless Tool Integrations: Easily integrates with major CI/CD technologies, increasing productivity and communication.
Disadvantages of Astra Security
Limited Testing Features: This one lacks some testing features compared to other platforms.
Expensive: Startups may struggle to pay the pricing structure.
Ongoing Monitoring: Security engineers must actively monitor the system to ensure regular protection.
Best For: Astra Security is best suited for organizations seeking real-time security solutions for their websites and APIs. Astra Security is for organizations seeking security against cyber threats and viruses.
How to Choose the Best API Security Solution
Selecting the appropriate API security solution is essential for protecting sensitive data, ensuring compliance, and reducing security threats. Here are five considerations that can help organizations make the proper decision.
Evaluate Coverage and Detection Capabilities
A strong API security platform will fix all possible weaknesses including those from the OWASP Top 10 such as SQL injection, cross-site scripting (XSS), and authentication issues. It must be capable of monitoring and reviewing every major security risk, present and emerging. Choose the platforms that offer static and dynamic analyses and deep reviews of APIs and prevent vulnerabilities throughout the development cycle.
Integration into Existing Development Workflows
API security technologies should integrate with the practices of development and deployment that are current. Such solutions as those that support CI/CD pipelines, for example, allow for continuous security testing during development and enable the developer to fix vulnerabilities while still in development. The integration options with platforms will keep productivity flowing without the burdensome impact on the development process and thereby continue security as a consideration rather than an afterthought.
Scalability and Flexibility
As the organization grows, API security requirements will change. Select a solution that can handle growing traffic, complex environments, and strong security threats of an organization. Choose the solution that can meet organization demands, whether through cloud-based platforms for easy scalability or on-premise solutions for highly sensitive data environments.
Easy to Use and Report
The solution should be simple to use and have simple dashboards and detailed reporting. Security engineers must quickly analyze data and respond to vulnerabilities with little training required. Good reporting should find weaknesses and also give useful steps to take plus repair actions. It will greatly enhance the decision-making process.
Cost and Support
Check pricing models to see if they fall within the budget of the organization and deliver powerful features and capabilities. Consider the level of customer service and resources. A great support team is worth its weight in gold when it comes to addressing major vulnerabilities and issues quickly with professional assistance.
Final Thoughts
OWASP ZAP Security is an open-source security platform that offers complete tools for finding vulnerabilities in APIs and web applications. Its adaptability, passive threat detection, and strong community support make people highly regard it.
There are other alternatives to OWASP ZAP that offer different levels of expertise, automation, and integration with modern development workflows. These solutions provide extensive security measures while also meeting other organizational needs, such as scalability, ease of use, and improved API-specific protections.
Akto stands out as an excellent choice because of its emphasis on API security. Akto focuses on real-time vulnerability detection and behavior analytics, which are essential for today's API-driven systems. It easily integrates with existing operations and allows automation by providing huge benefits in ensuring full API security. To know more, schedule a demo now!
