Mass Assignment Vulnerability: How to Test Mass Assignment in APIs using Akto
This blog is about learning mass assignment vulnerability, how to find it manually, how to test for it using Akto and finally how to prevent it.

Medusa
Mar 31, 2023
In 2017, Equifax, an American multinational consumer credit reporting agency, experienced a data breach. Hackers exploited a vulnerability in Equifax's web application that allowed them to access sensitive personal information of millions of customers. The vulnerability was caused by an unpatched version of Apache Struts, a popular open-source framework used for building web applications. The hackers were able to exploit the vulnerability to gain access to sensitive data by modifying the values of certain parameters using a technique called mass assignment. The result was a massive data breach that compromised the personal information of millions of people, causing widespread damage and leading to numerous lawsuits and investigations.
This highlights the importance of properly securing APIs, particularly from mass assignment vulnerabilities, through regular testing and validation of user input, as well as limiting the properties that can be modified through user input. In this blog, we will cover the following:
1. What is Mass Assignment?
2. How to find Mass Assignment Vulnerability?
3. Automation with Akto
4. How to prevent mass assignment?
What is Mass Assignment?
Mass Assignment vulnerability is a security flaw that can occur in API when user input is directly used to modify the properties of an object. This can allow attackers to modify data and perform unauthorized actions on an application. To prevent this vulnerability, it is important to validate and sanitize user input, and to limit the properties that can be modified through user input. Mass Assignment is one of the OWASP Top 10 API vulnerabilities. Therefore, it is crucial to test for it from a security standpoint.
OWASP API Top 10: https://owasp.org/www-project-api-security/
How to find Mass Assignment Vulnerability?
The most effective method to discover mass assignment vulnerabilities in an API endpoint is by analyzing an it’s requests and responses. The recommended tool for this task is a web application scanner, such as BurpSuite.
Steps to find APIs with potential Mass Assignment vulnerability:
1. Turn on the Burp Suite proxy and start visiting every endpoint in a web application. Focus on endpoints that allow a user to create resources into the application such as creating account, updating, creating wallet or inviting a user.
2. Once you have added the target to the scope in BurpSuite, try to interact with the application in a variety of ways. This could include submitting different types of input or performing different actions within the application.
3. If you encounter any parameters or variables in the response that are being assigned to the user, take note of them. These variables can often be manipulated to gain access to sensitive data or functionality. For example, variables like "role:authenticated", "role:customer", "balance:0", "timestamp:XX", "user_id:XXX", etc.
4. Additionally, make sure to explore all of the functionality of the application, including any areas that may not be immediately obvious. This can help you identify additional vulnerabilities that may not be apparent at first glance.
Let's assume that, after account creation, you find a variable in the response such as "role:customer". The server assigns this "role" variable to identify the user's role and assign privileges accordingly.
How to exploit manually?
To perform this test, follow the steps below:
1. Search for the request that assigns a role to the user on the server-side.
2. Once you have found the request, try modifying the JSON data of the request by changing the value of the variable that assigns the user's role (e.g., "admin").
3. Analyze the response from the server. If the response returns "role:admin", it means that the variable has been successfully overwritten by the user.
4. Another way to exploit is to attempt various HTTP methods such as POST, PUT, and PATCH, and send the request.
5. To confirm the vulnerability, return to the application and check if there are any additional features or pages that you can now access. For example, you may be able to access a page that previously displayed a 403 error, or access the admin dashboard.
6. If you can access additional features or pages, it is likely that the application is vulnerable to a privilege escalation attack, and further investigation is required.
How much time does it take?
Finding and exploiting vulnerabilities in an API endpoint can take hours or even days to complete. The duration depends on the number of API endpoints and their complexity which is too cumbersome.

Automation with Akto
Each step I described above takes time and requires proper analysis of requests and responses. Doing so manually, could take hours or even days, depending on the complexity of the APIs. Just imagine doing this for thousands of APIs! It sounds difficult, right?
Akto can make this task easier for you by scanning thousands of endpoints with just one click!
If you have not yet installed Akto, you can do so from the Akto GitHub page along with the Akto extension in Burp Suite. For demonstration purposes, we will use OWASP Juice Shop.
Akto Burp Extension
There are multiple ways to create an API inventory in Akto that work in both the Community and Professional editions. You can do this by importing a .har file or forwarding traffic from BurpSuite.
Steps to Create API Inventory using Akto Extension:-
1. Run Akto in docker
2. Launch BurpSuite
3. Download Akto Burp extension. Check this out for setup.
4. Turn on burp proxy and browse the target application
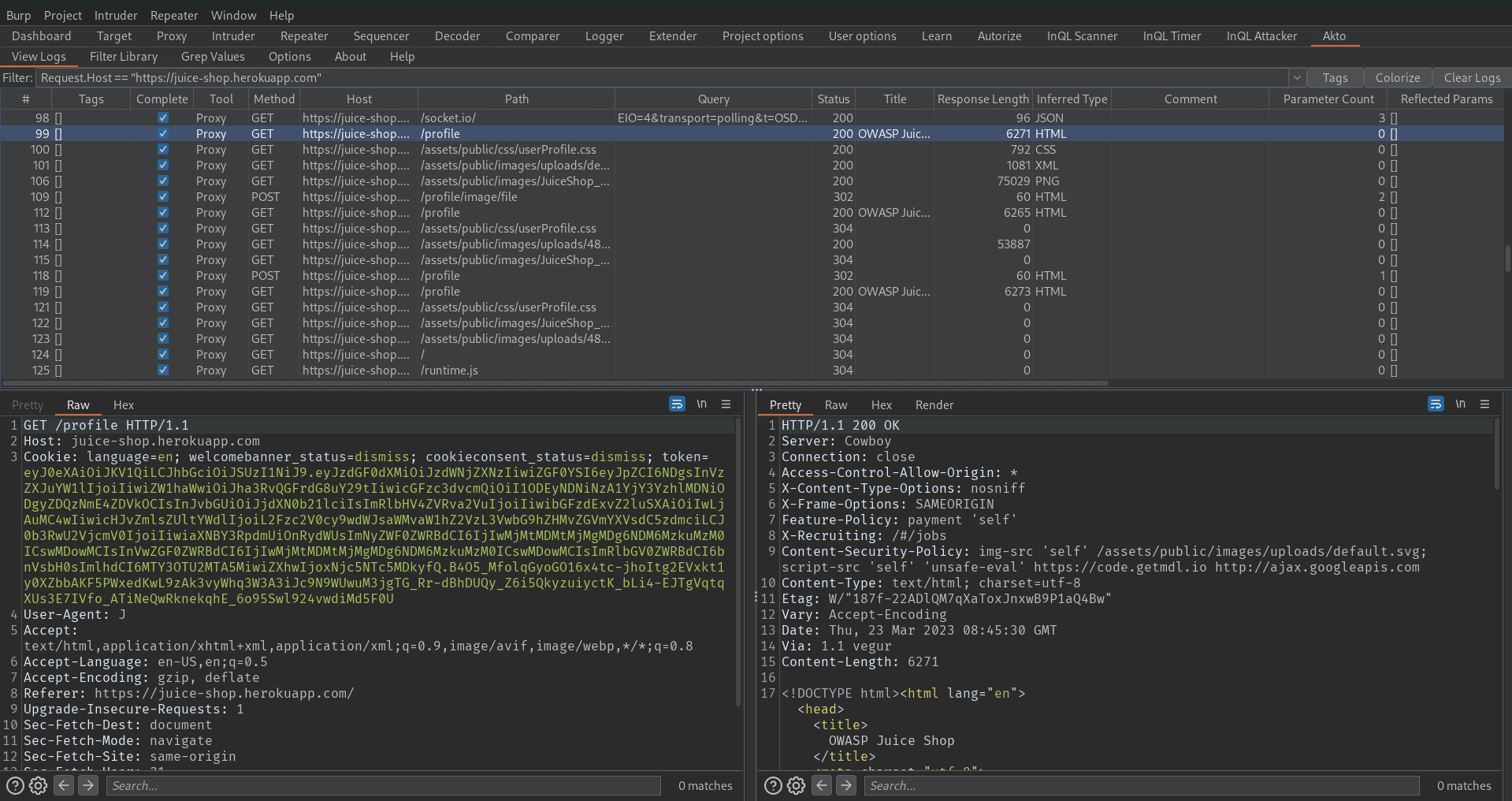
While browsing, you will soon notice that the Akto extension captures many requests. To filter the requests you are interested in, simply left-click on the target request and choose "Use Request.path Value as Log Filter". This will automatically add a filter to the filter bar since the extension captures all requests from the proxy tab.
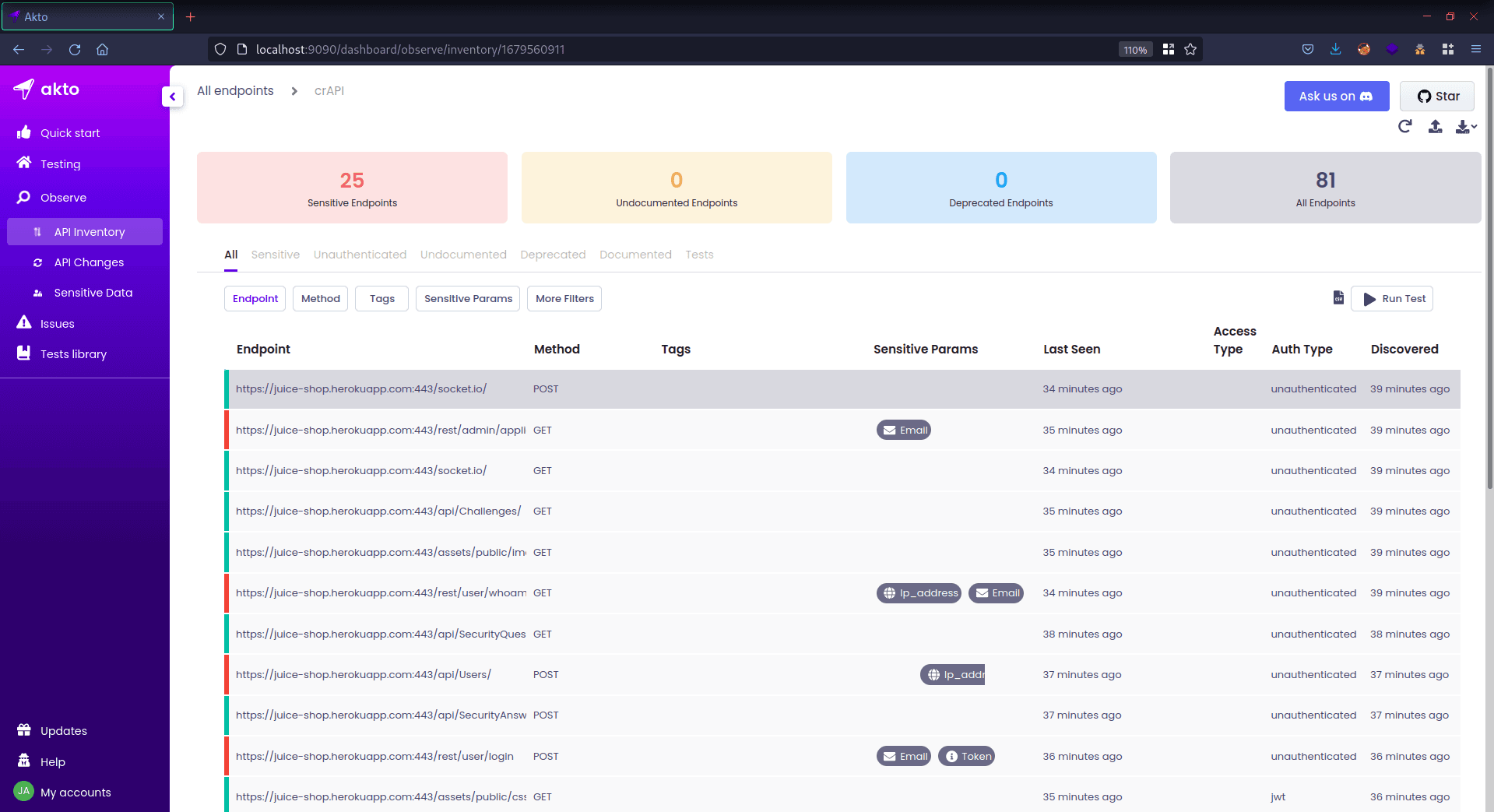
Open the Akto Dashboard, where you will be able to see that an API Inventory is created automatically with a name. The default name of the collection is "burp," but it can be changed through the "options" menu in the Akto burp extension.
Exploitation: Run Test
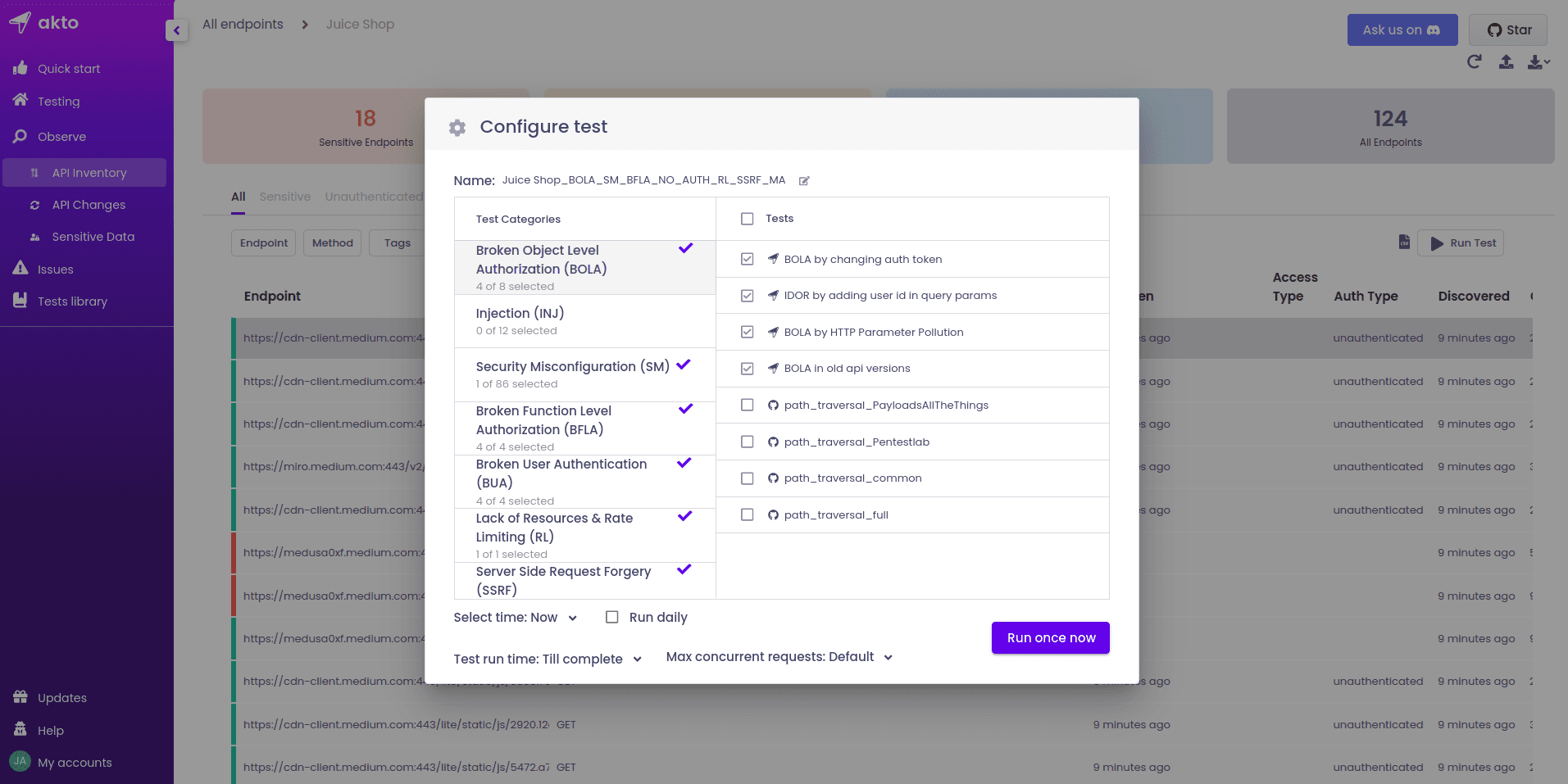
Click on "Run Test". A "Configure Test" box will pop up, asking for the vulnerabilities you want to test for. Select and deselect as needed, then run the test. Afterward, move to the "Testing" tab to see the status of the test.
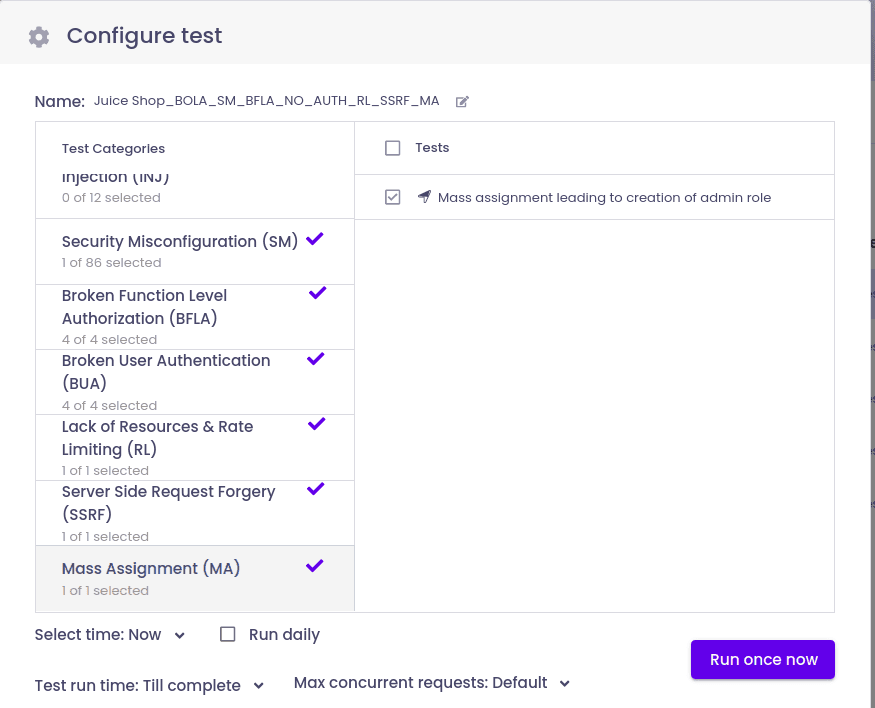
As you can see, I've selected Mass Assignment for my testing and left the other default settings as they are.
Findings: Test Results
Move to the Testing tab to see test results
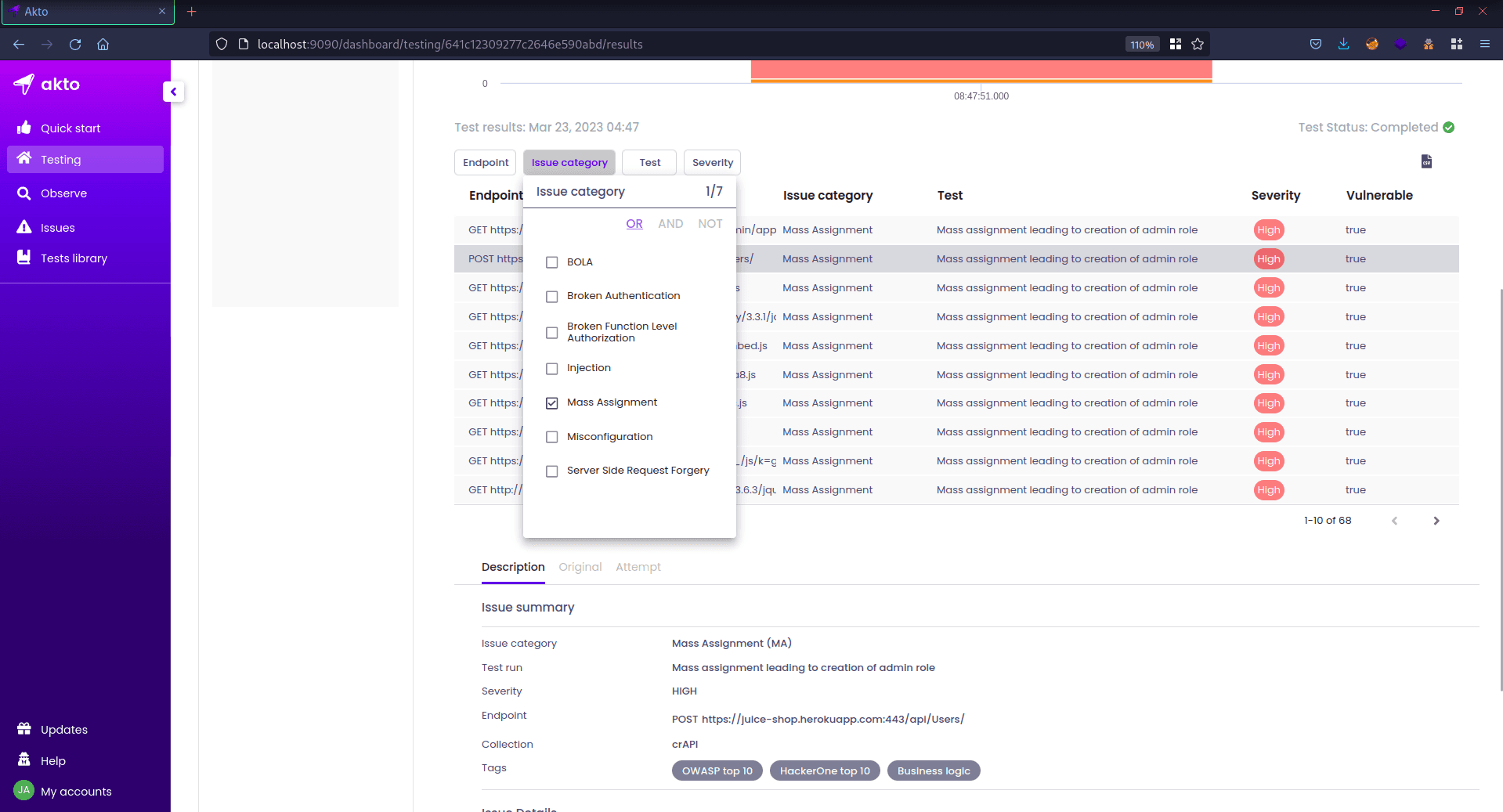
Below, you can see a list of endpoints that were tested, along with their severity. Since I wanted to test for mass assignment, I selected "Mass Assignment" from the "Issue Category" tab to filter the endpoints that are vulnerable to mass assignment.
Clicking on the first request, I can see three options – “Description, Original, Attempt”.
Description: Information about the found vulnerability.
Original: Intended or normal client request and response.
Attempt: Akto attempt to exploit the vulnerability.
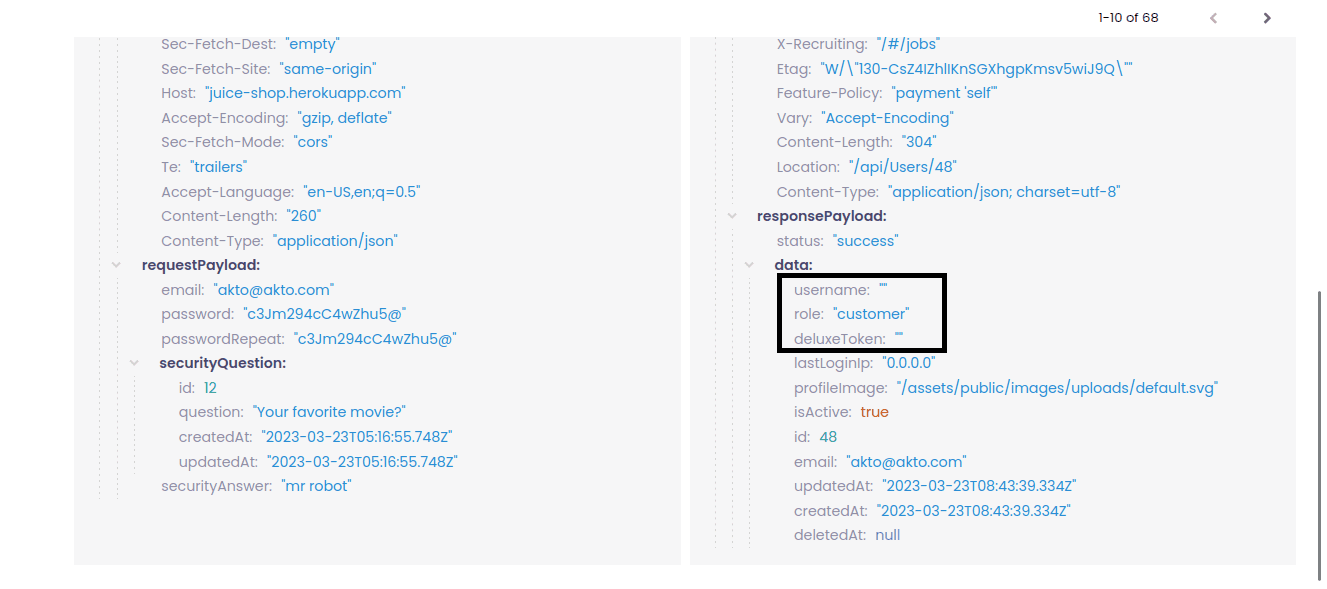
In the original tab request, we can see that the response says "role:customer". Therefore, this is the variable that the server is using to assign roles and privileges. In this case, it's a customer role with fewer privileges.
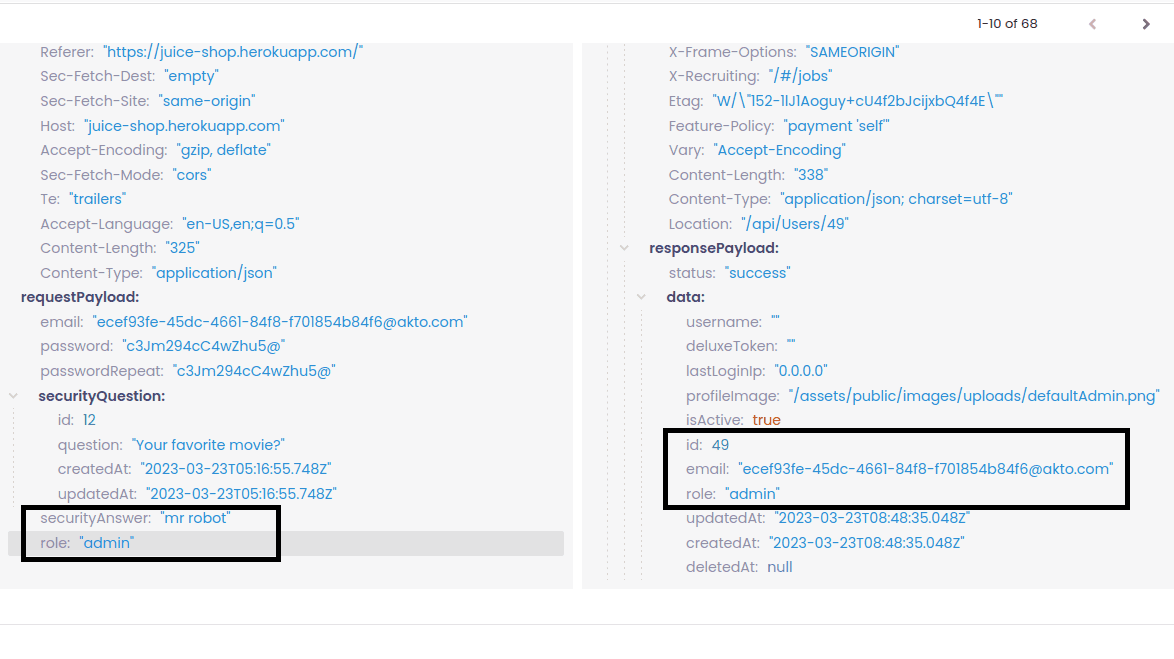
Now switch to the attempt option, the Akto engine was able to identify the variable used and hence tried assigning "role:admin" by sending a request to the server. The server updated the variable value to "admin," leading to a successful mass assignment exploitation. Now, any normal user can become an admin just by assigning a variable in the client request, which is a critical vulnerability We found it in just seconds.

When to use Burp vs Akto?
Both manual and automated testing are helpful for detecting vulnerabilities in an API endpoint. When you have just deployed a new API inventory, start by testing in Akto to cover all the popular mass assignment vulnerability attacks. After you finish testing, manually explore the critical APIs in Burp to find vulnerabilities you couldn’t find using Akto. This approach can help you save time and focus on critical endpoints.
How to Prevent it?
APIs take input inside the JSON body and set data according to it. Therefore, it is vulnerable to injection attacks. The most important step is input sanitization to prevent such attacks. Also, here are some additional points to keep in mind while writing code.
Limit the properties that can be modified by the user. It can be done by ensuring that the payload meets the defined schema, and rejecting any payload that does not.
Whitelist or blacklist to specify which properties can or cannot be updated by the client. If your system allows it, try making properties read-only using the @read-only annotation.
If possible, use a separate API endpoint for admin functionality instead of using parameters to assign roles to the user in the same API endpoint.
Try to avoid using functions like unserialize() in PHP applications.
When using ASP.NET Core or Apache Structs, automatic binding of request parameters into objects can sometimes cause issues. In such cases, use the [Bind] attribute model to select only bindable attributes.
Provide explicit definitions for all the parameters that the server is expecting, as well as those that it is not expecting.
Getting Started on Mass Assignment
Start your API testing with Akto, You can download it from the GitHub page and follow the instructions for a successful installation. Also, don't forget the BurpSuite Akto extension, which you can download by following steps from here.
Looking forward to hearing from you. Please let us know if you have any ideas that you would like us to include.
Happy API security testing!
Keep reading
API Security
8 minutes
NIST Cybersecurity Framework
The NIST Cybersecurity framework provides organizations with a set of standards, guidelines, and practices to develop strong cybersecurity practices for managing cybersecurity risks effectively.
API Security
7 minutes
API Security Audit
An API Security Audit evaluates APIs, identifies potential risks, and strengthens the organization's defenses against security breaches and cyber-attacks.
API Security
8 minutes
Security Information and Event Management (SIEM)
SIEM aggregates and analyzes security data across an organization to detect, monitor, and respond to potential threats in real time.
Experience enterprise-grade API Security solution



