Trello Data Breach: 15 Million Email Addresses Exposed
Trello's Data Breach exposed 15 million email addresses of users due to an unsecured API.

Muze
Jul 24, 2024
A recent security breach exposed over 15 million Trello email addresses due to an unsecured API. Learn what happened, the impact on users, and how organizations should protect themselves from such breaches.
What Happened?
Attackers have leaked the email addresses of approximately 15 million users of Atlassian's task management tool, Trello, on the dark web.
Users organize data and tasks into boards, cards, and lists using Trello, an online project management tool. Over 3,000 organizations worldwide use it.
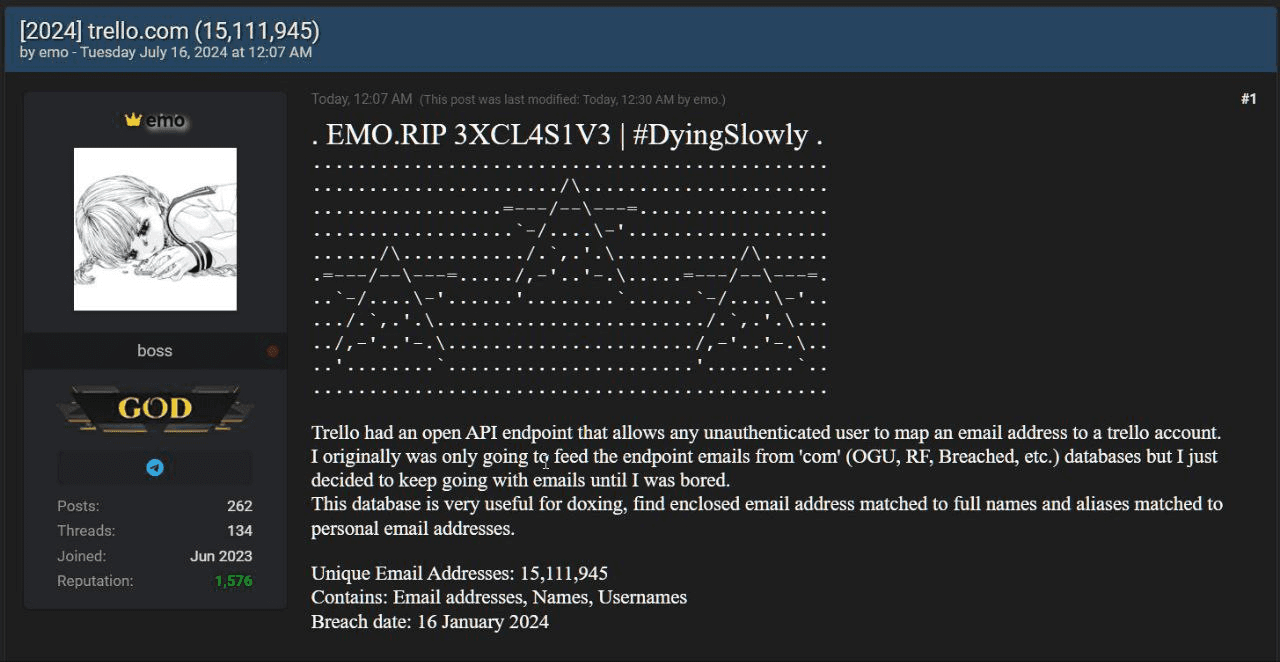
In January 2024, a threat actor named Emo exploited Trello's unsecured API to gather over 15 million email addresses linked to Trello accounts, which Atlassian owns. Emo created a list of 500 million email addresses and used the API to identify those associated with Trello. By combining the returned account information, Emo generated member profiles for over 15 million users.
On July 16, Emo shared the entire list of 15,111,945 profiles on the Breached hacking forum for eight site credits (worth $2.32). This data breach was added to the Have I Been Pwned (HIBP) database on January 22, 2024.
HIBP helps people check if their data has been compromised in any breach. Adding this breach to HIBP alerts millions of affected users, urging them to change passwords and watch for phishing attempts using their exposed information.
Impact on Users
The email leak from Trello boards directly impacts users by exposing their email addresses to phishing attacks. Attackers can now impersonate trusted entities to steal sensitive information or credentials. Due to the availability of their emails to malicious actors, users also face a higher risk of spam and targeted scams.
Vulnerability: Unsecured REST API
Attackers exploited Trello’s open API endpoint, allowing any unauthenticated user to query public information about profiles based on users' Trello ID, username, or email address.
An unsecured REST API lacks proper authentication and access controls, making it vulnerable to unauthorized access. For example, an API endpoint without authentication checks could let anyone retrieve sensitive user data simply by requesting it with a known email address. This highlights organizations' need for robust security measures to protect user information.
How can Akto help?
With Akto, organizations can identify unsecured API endpoint vulnerabilities with a click. Security engineers must import the API collection and run multiple tests to uncover potential weaknesses. Additionally, security teams can create custom templates using the Akto test library, allowing for tailored security assessments.
How Can Users Protect Themselves?
Change Passwords: To prevent unauthorized access, immediately change your Trello password and any other account that uses the same password.
Enable Two-Factor Authentication (2FA): Turn on 2FA on Trello and other accounts to add an extra layer of security.
Watch Out for Phishing: Be cautious of unexpected emails and avoid clicking on links or downloading attachments from unknown sources.
Final Thoughts
This incident shows how important it is for organizations to secure APIs to protect user data. Trello users must stay alert for phishing attacks and adjust their privacy settings. Atlassian took steps to fix the issue, but users should always be cautious and proactive about their online security. At the same time, organizations must update their security measures regularly to secure their infrastructure from data breaches.
Keep reading
API Security
8 minutes
NIST Cybersecurity Framework
The NIST Cybersecurity framework provides organizations with a set of standards, guidelines, and practices to develop strong cybersecurity practices for managing cybersecurity risks effectively.
API Security
7 minutes
API Security Audit
An API Security Audit evaluates APIs, identifies potential risks, and strengthens the organization's defenses against security breaches and cyber-attacks.
API Security
8 minutes
Security Information and Event Management (SIEM)
SIEM aggregates and analyzes security data across an organization to detect, monitor, and respond to potential threats in real time.
Experience enterprise-grade API Security solution