What is API Pentesting?

Insha
Oct 15, 2024
API pentesting, also known as API penetration testing, checks an API for security weaknesses by simulating attacks. Security teams test for weak authentication, insecure data transfer, or access control problems. The goal is to find and fix vulnerabilities before attackers can exploit them, ensuring the security of the API and its correct functionality. This helps protect against common threats and keeps the API safe from harm.
This blog explains API penetration testing, highlights common vulnerabilities, and shares methods for securing APIs with best practices.
What is API Penetration Testing?
API penetration testing assesses vulnerabilities in software interfaces. It involves discovering, enumerating, and fuzzing API endpoints to uncover flaws such as injection attacks or authentication weaknesses.
To secure APIs, security engineers validate authentication mechanisms, session management, and data validation to prevent unauthorized access and data manipulation. It also evaluates error handling, rate limiting, and TLS encryption to ensure secure communication.
By identifying and addressing these weaknesses, API penetration testing helps mitigate the risk of data breaches and unauthorized access, enhancing overall system security.
Example
Consider a simple e-commerce application that uses an API to manage checkouts. The checkout API endpoint could resemble this: http://example.com/api/checkout. This endpoint could accept POST requests containing JSON bodies like the following:
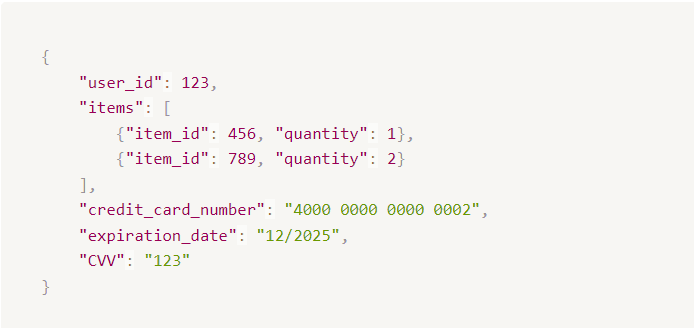
Let’s evaluate the vulnerability of this endpoint to attacks. Here's how you might proceed.
To test for an authentication bypass, change the user_id to another user’s ID and observe if the API properly authenticates the request. If the API fails to enforce proper authentication, it may allow pentester to perform actions as another user, such as checking out items.
For input validation, send incorrect data types, like a string instead of an integer, to fields such as user_id. If the API doesn't validate these inputs, it could lead to vulnerabilities, potentially allowing attackers to manipulate the system.
Next, ensure that the API uses HTTPS to protect credit card information. If the API transmits sensitive data without encryption, attackers could intercept it. For error-based attacks, send malformed JSON and observe how the API handles it.
If the API returns detailed error messages, it may leak sensitive information. Lastly, test rate limiting by sending a large number of requests in a short time. If the API lacks proper rate limiting, it could be vulnerable to denial-of-service (DoS) attacks, leaving the system at risk.
Importance of API Penetration Testing
API penetration testing is crucial for uncovering vulnerabilities before attackers exploit them. It helps identify security flaws like broken authentication, authorization issues, and data leaks that could compromise sensitive information.
Regular testing ensures that APIs remain secure against evolving threats and helps organizations comply with security standards and regulations. It provides valuable insights into the security posture of the application, enabling swift remediation of risks. By testing APIs, teams can proactively protect their systems, prevent data breaches, and build user trust. A secure API infrastructure enhances overall organization resilience.
What Vulnerabilities Does API Pentesting Uncover?
API penetration testing reveals various vulnerabilities that could weaken an application's interface security. These vulnerabilities include:
Injection Flaws
Attackers can exploit injection flaws by manipulating API inputs to run unauthorized commands on the database. Security engineers test for SQL injection and NoSQL injection by sending malicious queries through input fields or parameters to see if the API improperly processes them.
These attacks allow attackers to access, modify, or delete data without proper authorization. By identifying and fixing these vulnerabilities, security teams ensure that the API properly validates and sanitizes inputs, preventing harmful commands from executing on the database.
Broken Authentication
Attackers can exploit broken authentication if the API uses weak authentication methods. Security engineers test for issues like brute force vulnerabilities, where attackers try many password combinations to break in, and weak password policies, which make it easier for attackers to guess or steal passwords.
They also check for improper session management, where sessions remain active too long or are not securely handled, allowing attackers to hijack them. Fixing these weaknesses ensures that only authorized users can access the API.
Insecure Direct Object References (IDOR)
Insecure Direct Object References (IDOR) occur when an API exposes internal identifiers, like file IDs or user IDs, without properly verifying whether the user is authorized to access those resources. Attackers can exploit this by modifying the identifiers in their API requests to access data that doesn't belong to them.
For example, if an API request uses a URL like /user/1234/profile, an attacker might change the 1234 to another user’s ID, such as 5678, to access someone else's profile or sensitive information.
XML External Entity (XXE) Attacks
XML External Entity (XXE) attacks occur when attackers exploit weaknesses in XML processors. These processors might incorrectly process external entities within XML documents, allowing attackers to gain access to sensitive data or execute arbitrary code on the server. This vulnerability is especially dangerous because it can also be used to target internal systems or even access files on the host machine.
Broken Access Controls
Broken access controls happen when APIs fail to enforce proper authorization, leading to unauthorized access to sensitive endpoints or functionalities. This vulnerability allows users without the necessary permissions to access or manipulate data and perform actions that should be restricted.
It can result in users gaining access to confidential information, modifying records, or using administrative features they shouldn't have access to. This flaw typically arises when the API doesn't properly check or enforce user roles and permissions, leaving critical functions exposed to potential misuse.
Security Misconfiguration
Security misconfiguration occurs when APIs are left vulnerable due to incorrect or default security settings. This often includes the use of default credentials, open access to unnecessary services, or overly permissive settings that give users more access than they should have.
These misconfigurations make it easier for attackers to exploit the system, gaining unauthorized access or manipulating data. Common causes include failing to disable default accounts, not restricting permissions, or mismanaging security protocols, leaving the API exposed to potential threats.
Cross-Site Scripting (XSS)
Cross-site scripting (XSS) occurs when APIs reflect user-supplied data in responses without properly validating or sanitizing it. This allows attackers to inject malicious scripts into web pages, and the browsers of other users who view the page execute these scripts.
These malicious scripts can perform a variety of harmful actions, such as stealing sensitive information, hijacking user sessions, or redirecting users to malicious websites. XSS is particularly dangerous because it can affect a large number of users by exploiting a single vulnerability in the API's handling of input and output data.
API Pentesting Methodology
API penetration testing follows a systematic methodology to uncover vulnerabilities and strengthen the security of APIs. The process involves several key steps:
Discovery
During API penetration testing, start by identifying all available API endpoints, including undocumented or hidden ones. Use techniques like automated endpoint scanning to map the API's structure and dynamic traffic analysis to observe how it interacts with other systems. Manual inspection of API documentation or source code helps spot potential inconsistencies or overlooked APIs that automated tools might miss.
Analyze error messages, outdated API versions, or misconfigured routes, as they can reveal valuable information about hidden endpoints. Cross-reference findings from automated tools with manual exploration to ensure comprehensive coverage, leaving no endpoint untested.
This thorough discovery process plays an essential role for identifying vulnerabilities that attackers could exploit, making it a key step in API penetration testing.
Enumeration
Thoroughly document every aspect of the API to ensure a comprehensive testing process. This includes mapping out all API endpoints, parameters, supported methods (such as GET, POST, PUT, DELETE), and data structures. The goal is to have a complete understanding of how the API functions and interacts with other systems.
Start by listing each endpoint, which represents specific functions or services that the API provides. For every endpoint, document input parameters, including headers, cookies, query strings, and body data.
These parameters define how the API accepts data from users or other services, making them crucial to test for security weaknesses. Also, note the types of data each parameter accepts—whether strings, numbers, or more complex objects—and any validation mechanisms in place for data handling.
By cataloging these details, security engineers can easily identify weak spots where the API may be vulnerable to attacks like injection, improper input validation, or insufficient access controls. For instance, if a parameter lacks strict data validation, attackers could inject malicious code.
Fuzzing
Fuzzing tests how an API handles unexpected or bad data by sending random, incorrect, or unusual inputs to see if the API reacts in ways that reveal security flaws. By using fuzzing tools or custom scripts, this process helps uncover vulnerabilities in the system. For more comprehensive testing, security teams can use dynamic wordlists to generate diverse inputs and widen the scope of potential issues detected.
Authentication Testing
Authentication testing evaluates the strength of an API’s authentication mechanisms to ensure they can withstand attacks. Techniques such as brute-force attacks use different combinations of usernames and passwords are repeatedly tested to gain access.
Another method involves token manipulation, attackers alter authentication tokens like JWTs to check if the API can be bypassed or if they can gain unauthorized access. This technique ensures that the API properly validates tokens and prevents tampering.
Testing also includes checking for weak password policies, improper session management, and vulnerabilities in multi-factor authentication (MFA). This involves assessing how the API handles login attempts, session expiration, and token renewal processes to uncover flaws that attackers could exploit.
Authorization Testing
Authorization testing ensures that an API enforces access controls correctly across different user roles and permission levels. Start by identifying the various user types, such as regular users, administrators, or external partners, and test whether each role has access only to the resources it is authorized to use.
To check for horizontal privilege escalation, attempt to access resources or data belonging to other users within the same role. For example, try retrieving another user's personal information or performing actions outside of the permission level. This verifies if the API properly restricts users from accessing resources, they shouldn't.
For vertical privilege escalation, test whether users can elevate their privileges beyond their role, such as a regular user gaining administrative rights. Attempt actions reserved for higher-privileged users, like modifying system settings or accessing sensitive data. This ensures that the API enforces proper role-based access controls (RBAC) and prevents unauthorized privilege elevation.
Additionally, test for direct object reference vulnerabilities by manipulating URLs, IDs, or tokens to access restricted resources. This helps confirm that the API securely validates permissions before granting access, ensuring proper authorization checks are in place.
Session Management Testing
Session management testing ensures that an API properly handles user sessions and keeps them secure. Focus on session tokens, cookies, and session-related parameters to identify vulnerabilities. One key task is checking if session tokens are random and unpredictable, as predictable tokens make it easier for attackers to guess and hijack active sessions.
Test how the API handles session expiration to ensure that sessions expire after a reasonable period of inactivity or upon logout. If sessions remain active for too long, the risk of session hijacking increases, allowing attackers to take control of active sessions.
Check for vulnerabilities like session fixation, where an attacker forces a user to use a known session ID. By manipulating the session ID, attackers can take over a user’s session after they log in. Also, confirm that the API regenerates session tokens during key events, like logging in or elevating privileges, ensuring security throughout the session lifecycle.
Evaluate the security of cookies storing session data. Ensure that developers mark cookies as secure and have appropriate flags like HttpOnly and SameSite to prevent attacks like cross-site scripting (XSS) or cross-site request forgery (CSRF). These measures protect cookies from unauthorized access or manipulation, safeguarding user sessions.
Data Validation
Testing an API’s input validation mechanisms ensures that the system can handle different types of data without exposing vulnerabilities. This includes identifying issues like SQL injection, where attackers send malicious code through input fields to manipulate the database, or Cross-Site Scripting (XSS), where attackers can inject harmful scripts to affect users’ browsers.
Start by sending various types of input to the API, including strings, numbers, special characters, and potentially harmful data. Test boundary values, such as extremely large or small numbers, to determine if the API properly handles these edge cases. This helps ensure that developers ensure the API's validation rules are strict enough to prevent unexpected behaviors that could create security risks.
Also test for evasion techniques, where attackers attempt to bypass validation by encoding inputs in different formats like HTML encoding, URL encoding, or Unicode. This evaluates how well the API can detect and block disguised malicious inputs.
Ensure strong validation on both client-side and server-side. While client-side validation helps catch errors early and improves user experience, focus on robust server-side validation to prevent attackers from bypassing security measures by sending direct API requests. This dual-layer approach helps maintain data integrity and security.
Error Handling
Thoroughly testing an API’s error handling ensures it doesn’t expose sensitive system information or give attackers clues to exploit vulnerabilities. The focus is on how the API responds to unexpected inputs, failed requests, or processing errors, specifically examining error messages, status codes, and other details that the system returns.
Start by sending incorrect or malformed requests, such as invalid parameters, unauthorized access attempts, or broken queries, to observe how the API reacts. Look for overly detailed error messages that could reveal internal system information, like database structures, server configurations, or software versions. This helps ensure that no critical details expose themselves through error responses.
Test for consistent error handling, where a secure API returns generic, non-informative messages like “An error occurred” or "Invalid request" without revealing specifics. Consistent error messages prevent attackers from gaining insights into unprotected endpoints or weaknesses through input manipulation.
Rate Limiting and Throttling
Actively test the rate limiting and throttling mechanisms of an API to ensure it can handle excessive traffic and prevent abuse. Simulate various traffic patterns, including legitimate and malicious requests, to evaluate how effectively the API limits requests within a specific time frame. This helps protect the API from Denial of Service (DoS) attacks, where attackers flood the system with requests to overwhelm it.
Begin by assessing the rate-limiting algorithms in place and test whether the API correctly limits requests from a single user or IP, preventing anyone from exceeding usage thresholds. Also, check how the API responds when rate limits are exceeded, such as returning a 429 status code (Too Many Requests) and delaying further requests for a defined period.
Push the API under different load conditions, simulating typical usage spikes and abnormal traffic surges. This ensures that the rate limiting and throttling mechanisms maintain stability during sudden traffic influxes. Testing verifies the system can handle high traffic volumes without becoming unresponsive or vulnerable to resource exhaustion.
Sensitive Information Exposure
Examine API responses, headers, and metadata carefully to detect any instances of sensitive information exposure. Focus on identifying leaks of personally identifiable information (PII), such as usernames, email addresses, phone numbers, or other private data that should never appear in API responses. Also, check for system configuration details like server names, software versions, or internal IP addresses, which could give attackers valuable insights into the system’s architecture.
Simulate different user roles or privileges to see if users can access information they shouldn’t. For example, check whether regular users can view admin-level data or other users' personal information. This ensures that the API properly enforces access controls and prevents unauthorized exposure of sensitive data.
Best Practices Review
Review an API's security measures to ensure they follow industry standards, such as the OWASP API Security Top 10, which highlights the most common security risks. Check whether the API uses strong cryptographic algorithms to protect sensitive data, ensuring that encryption is up-to-date and securely implemented.
Evaluate access controls to confirm that users can only access the data and functions they are authorized to use. This prevents unauthorized users from viewing or altering sensitive information, ensuring proper role-based access management.
API Pentesting Tools
API penetration testing tools empower security professionals to identify vulnerabilities and strengthen API defenses effectively. Here are some popular tools used for API penetration testing:
Akto
Akto is an API Security Platform designed to automate the identification of API vulnerabilities. Security engineers can easily import the API collection using various methods listed here. Once imported, select the desired tests and click “Run” to start vulnerability scanning. Akto simplifies API security testing by streamlining the process, making it efficient for developers and security teams.
Burp Suite
Burp Suite is a comprehensive web application security tool that provides powerful features for testing APIs. It allows security teams to intercept and modify requests, making it easy to analyze and manipulate API traffic. Burp Suite also includes automated scanning features to detect vulnerabilities in APIs. Its robust set of tools helps security professionals conduct in-depth testing of API endpoints.
OWASP ZAP (Zed Attack Proxy)
OWASP ZAP is an open-source web application security scanner that offers extensive features for API testing. It provides both automated scanning and manual testing capabilities to uncover vulnerabilities in APIs. With its user-friendly interface, ZAP enables testers to intercept API requests and simulate attacks. It's a popular choice for security professionals looking for a free and effective API testing tool.
Postman
Postman is an API development and testing tool that allows security teams to send requests and inspect responses in a straightforward interface. It simplifies the process of automating testing workflows by providing features for scripting and test automation. Postman also enables developers and security engineers to manage API collections and share them easily with development and security teams. Its comprehensive functionality makes it a go-to tool for API development and testing.
Nmap
Nmap is a network scanning tool that security professionals can use to discover APIs and identify open ports and services. It helps in mapping out the API landscape by scanning the network and detecting potential security issues. Nmap’s versatility allows security teams to find exposed APIs and determine which services are running. Its powerful scanning features make it a valuable API discovery tool and security analysis.
SQLMap
SQLMap is a popular tool designed to detect and exploit SQL injection vulnerabilities in APIs and web applications. It automates the process of finding SQL injections, allowing security teams to easily exploit vulnerabilities and extract sensitive data. SQLMap’s advanced capabilities make it a crucial tool for identifying weaknesses in databases that security teams access through APIs. It streamlines the testing process for one of the most common vulnerabilities.
Kiterunner
Kiterunner is a security testing tool specifically built for API testing, offering both automated scanning and manual testing features. It allows users to efficiently test large numbers of API endpoints and integrates with other tools to enhance testing capabilities. Kiterunner is designed to help identify vulnerabilities in APIs quickly. Its specialized focus on API security makes it a powerful addition to any testing toolkit.
Best Practices for API Penetration Testing
Implementing robust security measures is crucial for protecting APIs from vulnerabilities. Here are some best practices to consider when conducting API penetration testing:
Authentication
Avoid using Basic Auth and instead, rely on standard authentication methods such as JWT to secure the APIs. Do not attempt to create your own authentication, token generation, or password storage solutions, as it is always safer to follow established standards.
Implement security measures like Max Retry and jail features to protect logins from brute force attacks. Always encrypt all sensitive data, ensuring it remains secure both during transmission and storage.
Input
Use the appropriate HTTP method for each operation, such as GET for reading, POST for creating, PUT/PATCH for replacing or updating, and DELETE for deleting records. Respond with 405 Method Not Allowed if the request does not match the correct method for the resource.
Validate the content-type in the request's Accept header (Content Negotiation) to ensure that the system only accepts supported formats like application/xml or application/json , and respond with 406 Not Acceptable if it doesn't match.
Additionally, verify the content-type of any posted data to ensure it conforms to accepted formats, such as application/x-www-form-urlencoded, multipart/form-data, or application/json. Validate all user inputs rigorously to prevent vulnerabilities like XSS, SQL Injection, and Remote Code Execution.
Output
Include security headers like X-Content-Type-Options: nosniff, X-Frame-Options: deny, and Content-Security-Policy: default-src 'none' in response to enhance security. Remove any fingerprinting headers like X-Powered-By, Server, or X-AspNet-Version to reduce information leakage.
Ensure the content-type of the response matches the data returned; for instance, if you're returning application/json, the response should have the corresponding content-type header. Never return sensitive data such as credentials, passwords, or security tokens in the response. Provide the correct HTTP status code based on the outcome of the operation, such as 200 OK, 400 Bad Request, 401 Unauthorized, or 405 Method Not Allowed, to maintain proper communication with the client.
JWT
Use a randomly complex key (JWT Secret) to make the token highly resistant to brute force attacks. Always enforce the algorithm on the backend, such as HS256 or RS256, instead of relying on the header to specify it.
Set a short token expiration time (TTL, RTTL) to limit the window of vulnerability in case the token is compromised. Avoid storing sensitive data in the JWT payload, as it can be easily decoded. Additionally, keep the data payload minimal since JWT is often passed in headers, and headers have a size limit.
Fuzzing
Send random input values like alphabets, numbers, or special characters into fields and analyze the responses to identify vulnerabilities. Use fuzzing techniques on input such as JSON parameters, API paths, or URL parameters to test how the API handles unexpected data.
Fuzz the API version by altering paths like /api/v1/cart to /api/{FUZZ}/cart, and test different path segments by fuzzing specific parts of the URL, such as /api/v2/FUZZ, to uncover potential security weaknesses or unhandled inputs.
Final Thoughts
Security engineers must maintain the security of the application that uses APIs through rigorous API Penetration Testing. They can significantly reduce the risk of data breaches and unauthorized access by actively testing for vulnerabilities and implementing strong security measures.
Security is a continuous process, not just limited to the initial deployment of an API. Engineers must regularly test, monitor, and update security controls to ensure APIs stay secure as new threats emerge.
To achieve comprehensive API security and improve development practices, explore the benefits of Akto. With Akto's solutions, organizations can proactively protect their APIs from vulnerabilities. Book your demo today and take the first step toward more secure and efficient API management.
Explore more from Akto
Blog
Be updated about everything related to API Security, new API vulnerabilities, industry news and product updates.
Events
Browse and register for upcoming sessions or catch up on what you missed with exclusive recordings
CVE Database
Find out everything about latest API CVE in popular products
Test Library
Discover and find tests from Akto's 100+ API Security test library. Choose your template or add a new template to start your API Security testing.
Documentation
Check out Akto's product documentation for all information related to features and how to use them.

