What is Automated Penetration Testing?

Insha
Oct 15, 2024
Automated penetration testing uses tools to scan systems for security vulnerabilities without needing manual intervention. These tools simulate attacks on APIs, applications, or networks to identify weaknesses like broken authentication or data leaks. Security teams use the results to quickly fix issues and strengthen defenses in the APIs. It’s a faster, more efficient way to test for security flaws compared to manual testing.
This blog explores automated penetration testing, highlighting its benefits, challenges, and comparison to manual testing.
What is Automated Penetration Testing?
Automated penetration testing involves using software tools to actively simulate cyber attacks on systems, networks, or applications. These tools scan for vulnerabilities, assess their severity, and attempt exploitation to gain unauthorized access. The process is streamlines, rapidly identifying security weaknesses and generating reports with remediation recommendations.
Importance of Automated Penetration Testing
Automated penetration testing quickly finds security issues in the organization’s systems without needing manual effort. It allows security teams to test the apps regularly, making sure they stay secure after the update.
With automated tools, security teams can identify vulnerabilities faster and fix them before hackers can exploit them. It saves time and resources while providing accurate results. This approach helps keep the data safe, boosts the security defenses, and builds trust with the users. Regular automated testing makes the apps more secure and reliable.
Benefits of Automated Penetration Testing
Automated penetration testing offers numerous benefits that enhance an organization's security posture and streamline the vulnerability assessment process. Let's explore the key benefits:
Efficiency
Automated Penetration Testing speeds up the testing process by automating repetitive tasks. Security teams can conduct assessments quickly and efficiently without manual effort. By streamlining the process, it allows for faster identification of vulnerabilities. This automation enhances overall security productivity.
Scalability
Automated tools can handle large and complex networks, applications, and systems. This scalability makes it easier for organizations to assess the security of their entire infrastructure. Whether small or large, the tools adapt to the size of the environment. Scalability ensures that no part of the infrastructure is left untested.
Consistency
Automated Penetration Testing ensures consistent testing methodologies across multiple assessments. By automating processes, it reduces the likelihood of human error and provides thorough coverage. Security teams can rely on consistent results for each test. This consistency leads to more accurate and reliable assessments.
Timeliness
Automated testing enables frequent and regular security assessments, keeping up with evolving threats. Organizations can perform real-time testing as new vulnerabilities emerge. This helps keep systems secure by addressing issues quickly. Timely testing ensures continuous security across the infrastructure.
Cost-Effectiveness
Automating penetration tests eliminates the need for extensive manual labor. It reduces the time and resources required for each test, resulting in long-term cost savings. Organizations benefit from increased efficiency without the added expense of hiring additional personnel. Cost-effectiveness makes automated testing a valuable solution.
Checks To Perform in an Automated Pentest
Automated penetration testing includes several crucial checks to ensure comprehensive security assessment. Let's explore the key areas to focus on during an automated pentest.
Vulnerability Scanning
Security engineers run automated scans to detect known vulnerabilities in the organization’s systems, applications, and network infrastructure. These scans help to quickly identify areas that need attention and patching.
By using regularly updated vulnerability databases, security engineers ensure that they test the systems against the latest threats. Automated vulnerability scanning provides ongoing protection against potential security risks.
Configuration Auditing
Security engineers review the configurations of the devices and systems and compare them to industry best practices and security standards.
This process helps identify misconfigurations that could lead to security breaches. Security engineers audit configurations regularly to ensure that all systems follow secure guidelines. Configuration auditing minimizes risks caused by human error or oversight.
Authentication Testing
Automate the tests to evaluate the strength of the authentication mechanisms, including password policies and multi-factor authentication.
This helps ensure that attackers cannot compromise authentication systems through methods such as brute force or credential stuffing. By testing session management and login attempts, verify the integrity of access controls. Authentication testing ensures secure and proper identity verification.
Authorization Testing
Assess the effectiveness of access controls to confirm that only authorized users can access sensitive data. By testing various user roles and permissions, ensure that unauthorized actions are blocked. This process checks for issues like privilege escalation and improper access rights. Authorization testing safeguards against unauthorized access to critical resources.
Data Security Testing
Verify the encryption strength of data both in transit and at rest, ensuring that sensitive data remains protected from unauthorized access. This includes testing for proper encryption algorithms and key management practices. Data security testing helps detect vulnerabilities that could expose personal or sensitive information. Protecting data through strong encryption is essential for compliance and privacy.
Web Application Testing
Use automated tools to scan web applications for common vulnerabilities like SQL injection, cross-site scripting (XSS), and insecure direct object references (IDOR). These tools simulate attacks to uncover potential weaknesses that could be exploited. Web application testing ensures that apps are secure against external threats. It helps protect user data and prevent unauthorized access.
Network Penetration Testing
Automate tests to identify weaknesses in the network infrastructure, such as open ports, weak encryption protocols, and misconfigured firewalls. These tests help security teams detect potential entry points that attackers could exploit. Network penetration testing ensures that firewalls, routers, and other devices are properly secured. This testing strengthens the network defenses against cyber threats.
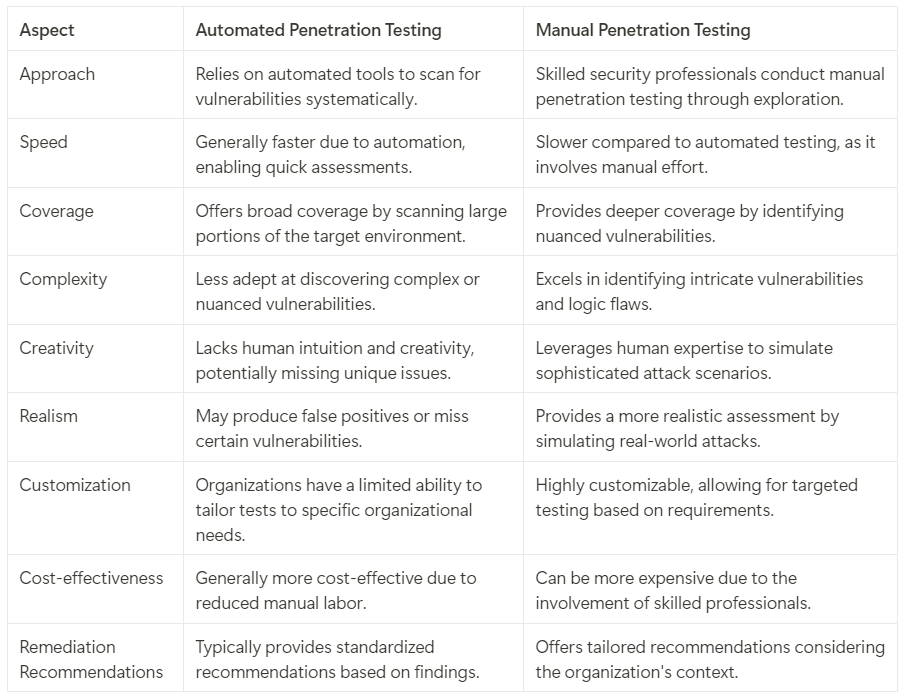
Manual vs Automated Penetration Testing
Let's compare automated penetration testing with manual penetration testing to understand their distinct characteristics and use cases.
Automated Penetration Testing Tools
Let's explore some popular automated penetration testing tools and resources that can enhance security assessment capabilities.
Akto
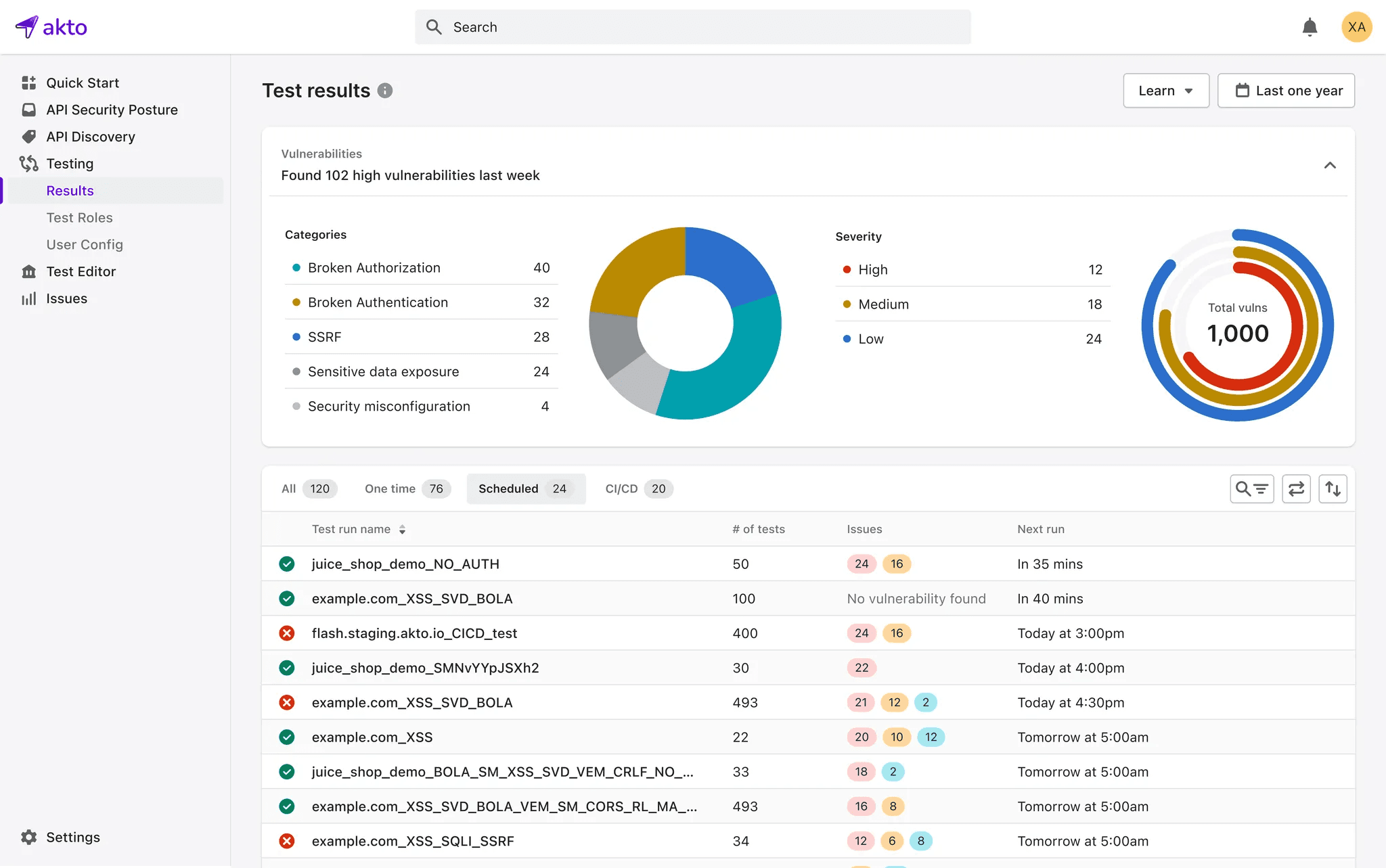
Akto is a comprehensive API security platform designed to help organizations protect their APIs from vulnerabilities. Akto offers features such as real-time monitoring, automated security testing, and API inventory management, allowing security teams to discover and mitigate risks effectively. The platform integrates seamlessly into development workflows, making it easy to identify sensitive data, misconfigurations, and potential threats across APIs.
Nmap
Nmap is a powerful network scanning tool used for network discovery and vulnerability scanning. It helps security teams identify open ports, services, and potential vulnerabilities in networks. Nmap is widely used for mapping network infrastructure and uncovering weaknesses.
With its range of features, Nmap can quickly scan large networks, revealing hosts, operating systems, and detailed service information. Security professionals rely on Nmap to perform penetration testing, network audits, and monitoring. It’s flexible, allowing for both basic and advanced scans to suit different security needs.
Metasploit
Metasploit is a popular framework for developing, testing, and executing exploit code against remote targets. It provides a robust environment for penetration testers to simulate real-world attacks. Metasploit enables security teams to find and exploit vulnerabilities in networks and applications.
OpenVAS

OpenVAS is an open-source vulnerability scanning tool that identifies security issues in networks. It helps organizations detect misconfigurations and vulnerabilities across their infrastructure. OpenVAS provides detailed reports to guide remediation efforts.
Security teams use OpenVAS to perform regular scans, ensuring that all systems are continuously monitored for new and existing threats. Its comprehensive vulnerability database allows for accurate identification of potential risks, making it easier to prioritize fixes. OpenVAS is also highly customizable, enabling users to tailor scans to their specific needs.
Burp Suite
Burp Suite is a comprehensive platform for web application security testing. It includes tools for scanning, crawling, and exploiting vulnerabilities in web applications. Security professionals use Burp Suite to assess web apps for issues like SQL injection and XSS.
It allows users to intercept and modify web traffic, making it easier to analyze application behavior and identify flaws. With its automated scanning capabilities, Burp Suite quickly finds security issues, while its manual testing features provide in-depth analysis. Professionals rely on Burp Suite's extensibility to customize and enhance their testing processes, using plugins and extensions to address specific security needs.
Nessus

Nessus is a vulnerability scanner that identifies security vulnerabilities, misconfigurations, and malware in networks and web applications. It helps organizations improve their security posture by providing detailed reports on weaknesses.
Security teams rely on Nessus to perform comprehensive scans, covering everything from operating systems to databases, network devices, and applications. Nessus quickly highlights issues like outdated software, weak passwords, or improper configurations, making it easier for teams to prioritize and remediate risks. Its user-friendly interface and customizable scanning options allow for tailored assessments to meet specific security needs.
OWASP ZAP (Zed Attack Proxy)
OWASP ZAP is an open-source tool for web application security testing. It helps developers and testers find vulnerabilities during the development and testing phases. ZAP offers both automated and manual scanning capabilities to detect common web vulnerabilities like SQL injection, cross-site scripting (XSS), and broken authentication.
Security teams use ZAP to actively test web applications, intercept traffic, and analyze responses to uncover potential security issues. Its user-friendly interface and robust set of features make it easy to integrate into any development workflow.
SQLMap
SQLMap is an automated tool that identifies and exploits SQL injection vulnerabilities in web applications. It helps security teams take control of vulnerable databases by automating the detection and exploitation process.
With SQLMap, security engineers can uncover and manipulate data, extract information, and even escalate privileges within compromised databases. The tool simplifies the process of finding SQL flaws by supporting a variety of databases and injection techniques. It offers customizable options for testing, from basic identification of vulnerabilities to more advanced attacks like data retrieval and database structure mapping.
Acunetix

Acunetix is a web vulnerability scanner that identifies and helps remediate security issues in web applications. It scans for vulnerabilities like SQL injection, XSS, directory traversal, and other web-based threats that could expose sensitive data.
Organizations use Acunetix to proactively secure their web apps by automating the detection of security flaws and providing actionable reports for quick remediation. Its powerful scanning engine is capable of detecting a wide range of vulnerabilities, including complex and hidden threats.
With features like continuous scanning, detailed vulnerability analysis, and integration into development pipelines, Acunetix empowers security teams to protect web applications effectively, ensuring data integrity and compliance with security standards.
Which Automated Pentesting Solution to Choose?
Determining the right automated penetration testing solution requires evaluating the organization's specific needs, budget constraints, and technical requirements. Start by assessing the requirements, and consider factors such as the size of the network, the complexity of the organization’s systems and applications, and any compliance requirements.
Compare the features of different solutions, focusing on capabilities like vulnerability scanning, configuration auditing, and web application testing. Ensure the solution offers scalability so it can grow with the organization as the network expands. Compatibility with the existing infrastructure, including operating systems, databases, and applications, is crucial to avoid integration challenges.
Accuracy is another key factor—evaluate how well the solution detects vulnerabilities while maintaining a low false positive rate. Consider the level of support offered, such as technical support, detailed documentation, and training resources to ensure smooth implementation.
Also, review the total cost of ownership, accounting for licensing fees, maintenance, and any additional expenses like training or customization. Finally, seek feedback through customer reviews and recommendations from trusted peers or industry experts. These insights help determine which solution provides the best value for the organization’s specific needs.
Challenges of Automated Penetration Testing
Despite its many benefits, automated penetration testing faces several challenges that organizations must address to ensure effective security assessments. These include:
False Positives
Automated tools may generate false positives, flagging issues that do not pose real security risks. This can lead to wasted time and resources as security teams investigate non-existent vulnerabilities. Addressing these false alarms reduces efficiency and may delay critical remediation efforts. False positives challenge the reliability of automated testing.
Limited Context Awareness
Automated tools cannot understand complex business logic or nuanced attack scenarios. Without human intuition, they may miss vulnerabilities that require contextual awareness. This limitation makes it harder to detect issues specific to an organization’s workflows or logic. Context is crucial for identifying targeted threats.
Detection of Logic Flaws
Automated testing often struggles to identify logic flaws that require manual analysis of the application's behavior. Without understanding how the system operates functionally, it is harder to spot these vulnerabilities. Detecting logic flaws usually requires human insight and cannot be fully automated. Manual testing complements automated efforts here.
Overlooking Zero-Day Vulnerabilities
Automated tools rely on known signatures and patterns, making them ineffective against zero-day exploits. Emerging threats that have not been identified or documented can remain undetected. This gap in detection leaves organizations vulnerable to new attacks. Automated tools need regular updates, but even then, zero-day risks persist.
Complex Environments
Automated testing may struggle to assess complex network architectures, cloud environments, or interconnected systems. Navigating through these systems often requires manual configuration or intervention. Automated tools might miss vulnerabilities that arise from complex setups. Complexity challenges the capabilities of automated tools.
Best Practices for Automated Pentesting
Implementing these best practices empowers organizations to maximize the effectiveness of their automated penetration testing efforts and enhance their overall security posture.
Choose the Right Tools
Select reliable automated pentesting tools that match your application’s environment and security needs. Tools like OWASP ZAP, Burp Suite, and Nessus each have unique strengths suited for different scenarios. Carefully evaluate each tool’s features and compatibility with your systems. The right tool ensures the accurate detection of vulnerabilities.
Define Clear Objectives
Establish specific goals for what you aim to achieve with automated testing. Clearly define whether you're looking to find common vulnerabilities like SQL injection or ensure compliance with security standards. This clarity helps tailor your testing efforts for better results. Objectives provide a focused approach to vulnerability scanning.
Regularly Update Tools and Vulnerability Databases
Update the pentesting tools and vulnerability databases frequently to ensure they catch the latest security flaws. Constant updates are made to vulnerability databases as new threats emerge. By keeping your tools current, you enhance the accuracy of your security assessments. Regular updates ensure you don't miss critical vulnerabilities.
Validate and Prioritize Findings
After completing automated scans, validate the results to reduce false positives. Prioritize the identified vulnerabilities based on their severity and potential impact on your systems. This process helps allocate resources efficiently and address the most critical issues first. Effective validation and prioritization streamline the remediation process.
Combine with Manual Testing
Complement automated testing with manual testing to uncover complex vulnerabilities. Automated tools might miss certain logic flaws or business logic vulnerabilities that require a human touch. By combining both approaches, you gain a comprehensive view of your security posture. Manual testing adds depth to your vulnerability assessments.
Integrate into Development Pipelines
Integrate automated pentesting into your CI/CD pipelines for early detection of security issues. Testing during the development cycle allows teams to fix vulnerabilities quickly before deployment. This proactive approach ensures secure code delivery and reduces risks. CI/CD integration makes security a seamless part of the workflow.
Final Thoughts
Automated penetration testing offers benefits like efficiency, scalability, and cost-effectiveness, but it also comes with challenges. Issues like false positives, limited context awareness, and the potential to overlook zero-day vulnerabilities highlight the importance of manual testing as a complement to automated efforts. The effectiveness of automated tools relies on their configuration and the expertise of the team using them.
For comprehensive API security, consider the benefits of Akto. Akto helps organizations proactively protect their APIs from vulnerabilities and improve development practices. Book a demo today to take the first step toward more secure and efficient API management.
Explore more from Akto
Blog
Be updated about everything related to API Security, new API vulnerabilities, industry news and product updates.
Events
Browse and register for upcoming sessions or catch up on what you missed with exclusive recordings
CVE Database
Find out everything about latest API CVE in popular products
Test Library
Discover and find tests from Akto's 100+ API Security test library. Choose your template or add a new template to start your API Security testing.
Documentation
Check out Akto's product documentation for all information related to features and how to use them.

