Cloud Penetration Testing Methodology

Insha
Oct 15, 2024
Cloud penetration testing is the process of simulating cyberattacks on cloud-based systems to identify security weaknesses. It helps ensure that cloud services, such as storage, applications, and networks, are secure from potential threats. Security engineers assess configurations, access controls, and data protection. The goal is to enhance security and prevent unauthorized access or data breaches.
This blog will explore the importance and methodologies of cloud penetration testing. Learn how to identify vulnerabilities, enhance security, and protect your valuable data in the cloud.
What is Cloud Penetration Testing?
Cloud penetration testing actively assesses cloud-based system security by identifying vulnerabilities and weaknesses. It simulates real-world attacks to evaluate security measures' effectiveness and detect potential risks.
The process analyzes cloud infrastructure, applications, and configurations to uncover vulnerabilities that could compromise data integrity, confidentiality, and availability. By conducting comprehensive tests, organizations can strengthen their cloud security posture proactively, mitigate potential threats, and protect sensitive information.
Benefits of Cloud Penetration Testing
Cloud penetration testing offers numerous benefits that enhance an organization's security posture and protect valuable assets in the cloud environment.
Identifying Vulnerabilities
Cloud penetration testing helps organizations discover vulnerabilities before malicious actors exploit them. Testing can uncover issues like misconfigurations in cloud storage that may lead to data leaks. By identifying these flaws early, organizations can take proactive steps to secure their cloud environment and prevent unauthorized access.
Enhancing Security Posture
Regular penetration tests enable organizations to improve their overall security posture in the cloud. Identifying weaknesses like weak authentication mechanisms can prompt the adoption of security measures like multi-factor authentication (MFA). This continuous assessment helps reinforce and strengthen security defenses over time.
Mitigating Risks
Cloud penetration testing helps organizations reduce potential risks associated with cloud deployments. By discovering vulnerabilities in web applications or other cloud components, developers and security engineers can promptly patch them, reducing the chance of a successful cyberattack. This ensures a safer and more resilient cloud infrastructure.
Safeguarding Sensitive Data
Penetration testing ensures the protection of sensitive data stored in the cloud by identifying weaknesses. For example, testing might find flaws in encryption methods, prompting the use of stronger algorithms to protect data confidentiality. This helps maintain data integrity and prevents unauthorized access or data breaches.
Compliance Assurance
Regular penetration testing supports compliance with industry regulations and standards. By conducting these tests, organizations show their commitment to data security and demonstrate adherence to regulations like GDPR or HIPAA. This proactive approach helps meet legal requirements and build confidence in data protection practices.
Preventing Financial Loss
Proactively identifying and fixing vulnerabilities through cloud penetration testing helps prevent financial losses due to breaches or service interruptions. Discovering flaws in cloud-based infrastructure early can prevent costly security incidents or downtime, saving the organization from potential damages and loss of business.
Building Customer Trust
Regular penetration testing demonstrates a robust security posture that builds trust with customers and stakeholders. By conducting tests and sharing the results, organizations can show their commitment to securing cloud-based services, instilling confidence in clients regarding the security and reliability of their cloud solutions.
Common Threats in Cloud Computing
Cloud computing introduces several critical security threats that organizations must address to protect their data and infrastructure.
Misconfiguration
Misconfigurations of cloud security settings lead to many cloud data breaches. Many organizations find their strategies for managing cloud security posture inadequate for protecting their cloud-based infrastructure.
Cloud infrastructure is designed to be easily usable and to enable easy data sharing, making it difficult for organizations to ensure that data is only accessible to authorized parties.
Additionally, organizations using cloud-based infrastructure do not have complete visibility and control over their infrastructure, meaning they need to rely on security controls that their cloud service provider (CSP) provides to configure and secure their cloud deployments.
Since many organizations are unfamiliar with securing cloud infrastructure and often have multi-cloud deployments – each with a different array of vendor-provided security controls – A misconfiguration or security oversight can easily leave an organization's cloud-based resources exposed to attackers.
Unauthorized Access
Unlike an organization's on-premises infrastructure, their cloud-based deployments exist outside the network perimeter and are directly accessible from the public Internet.
While this is an asset for the accessibility of this infrastructure to employees and customers, it also makes it easier for an attacker to gain unauthorized access to an organization's cloud-based resources. Improperly-configured security or compromised credentials can enable an attacker to gain direct access, potentially without an organization's knowledge.
Insecure Interfaces/APIs
CSPs often provide several application programming interfaces (APIs) and interfaces for their customers. In general, CSPs well-document these interfaces in an attempt to make them easily usable for CSP's customers.
However, this creates potential issues if a customer has not properly secured the interfaces for their cloud-based infrastructure. A cybercriminal can also use the documentation designed for the customer to identify and exploit potential methods for accessing and exfiltrating sensitive data from an organization's cloud environment.
Hijacking of Accounts
Many organizations have extremely weak password security, including password reuse and the use of weak passwords. This problem exacerbates the impact of phishing attacks and data breaches since it enables a single stolen password to be used on multiple different accounts.
Account hijacking is one of the more serious cloud security issues as organizations are increasingly reliant on cloud-based infrastructure and applications for core business functions. An attacker with an employee's credentials can access sensitive data or functionality, and compromised customer credentials give full control over their online account. Additionally, in the cloud, organizations cannot often identify and respond to these threats as effectively as for on-premises infrastructure.
Lack of Visibility
An organization locates its cloud-based resources outside of the corporate network and runs them on infrastructure that it does not own. As a result, many traditional tools do not effectively achieve network visibility for cloud environments, and some organizations do not have cloud-focused security tools. This can limit an organization's ability to monitor their cloud-based resources and protect them against attack.
External Sharing of Data
The cloud is designed to make data sharing easy. Many clouds provide the option to explicitly invite a collaborator via email or to share a link that enables anyone with the URL to access the shared resource.
While this easy data sharing is an asset, it can also be a major cloud security issue. The use of link-based sharing – a popular option since it is easier than explicitly inviting each intended collaborator – makes it difficult to control access to the shared resource. The shared link can be forwarded to someone else, stolen as part of a cyberattack, or guessed by a cybercriminal, providing unauthorized access to the shared resource.
Denial of Service Attacks
The cloud is essential to many organizations' ability to do business. They use the cloud to store business-critical data and to run important internal and customer-facing applications.
This means that a successful Denial of Service (DoS) attack against cloud infrastructure will likely significantly impact several different organizations. As a result, DoS attacks where the attacker demands a ransom to stop the attack pose a significant threat to an organization's cloud-based resources.
Cloud Pentesting Methods
There are three types of cloud penetration testing, each tailored to specific needs and requirements of the system(s) under test. In all three forms, security teams actively probe the system as attackers would, aiming to identify real and exploitable weaknesses.
Transparent Box Testing
In transparent box testing, the organization provides testers with admin-level access to the cloud environment, giving them full visibility and control over all resources. This approach allows for the most in-depth analysis of security settings, configurations, and potential vulnerabilities.
For example, when an organization hires a testing team to assess the security of its AWS infrastructure, the testers receive full access to the AWS console. This lets them evaluate cloud configurations, such as IAM policies, network security groups, and data storage permissions, enabling a thorough check for misconfigurations, unpatched systems, and potential exploitation paths.
Semitransparent Box Testing
Semitransparent box testing provides testers with partial knowledge or access to the cloud environment. This approach balances the depth of analysis with the realism of an external attack, offering limited insight into the system while still challenging testers to uncover vulnerabilities.
For instance, an organization may give a penetration team read-only access to specific cloud components, such as databases, virtual machines, or API endpoints, without administrative privileges.
This allows them to assess how an attacker with limited access might exploit misconfigurations or weak access controls to gain deeper access to the environment.
Opaque Box Testing
In opaque box testing, testers start with no prior knowledge or access to the cloud systems. This approach simulates an external attacker who has no insider information and must rely on external reconnaissance and public-facing data to identify vulnerabilities.
For example, an organization might engage a testing firm without offering any details or credentials related to its cloud setup. Testers then conduct activities like domain enumeration, network mapping, and service probing to gather information before attempting to find and exploit security weaknesses. This method closely replicates real-world attacks by unknown external threats, testing the cloud environment's resilience to unanticipated breaches.
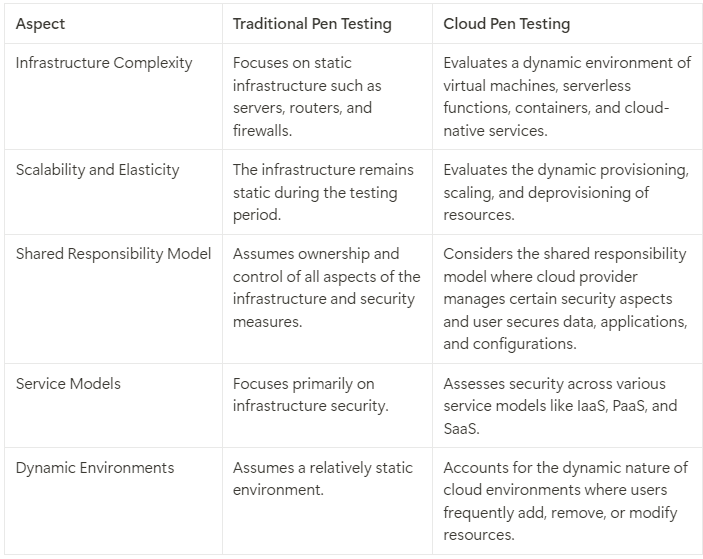
Difference Between Cloud and Traditional Penetration Testing
Cloud penetration testing differs significantly from traditional penetration testing in several key aspects, reflecting the unique challenges and complexities of cloud environments.
Methodology for Cloud Pentesting
Cloud penetration testing employs a structured methodology to systematically assess and strengthen the security of cloud environments. These include:
Understanding the Cloud Environment
Security teams must get familiar with the cloud platform they are testing, whether it's AWS, Azure, or Google Cloud. For instance, know how AWS manages services like EC2 instances or S3 buckets and how they’re interconnected. Understanding the environment helps identify which services might be misconfigured or have weak security settings, setting the foundation for effective testing.
Identifying and Mapping Assets
List and map all cloud resources, such as servers, databases, and storage containers. For example, use tools like AWS CLI or Azure Resource Graph to discover all active resources in an account. Knowing the scope of assets, like a publicly accessible S3 bucket, allows security teams to pinpoint attack surfaces and see how data flows between resources.
Testing for Misconfigurations
Check cloud configurations for issues like public data exposure or weak access controls. For example, security teams might find a storage bucket in AWS S3 that is publicly readable, which could expose sensitive data. Tools like ScoutSuite or CloudSploit can automate this process, helping teams find misconfigured resources that attackers could exploit.
Testing Access Controls and Permissions
Examine how organizations manage permissions across cloud resources. For instance, look for IAM policies in AWS that grant overly broad permissions, likes3:*:Allow, which could let any user perform all actions on S3 buckets.
Network Security Testing
Test for open ports, weak security groups, or misconfigured firewalls in the cloud setup. For example, check if any AWS Security Groups allow unrestricted inbound access on port 22 (SSH) or port 3389 (RDP). By using tools like Nmapfor port scanning, security teams can identify exposed services that could be vulnerable to attack.
Data Security and Encryption Testing
Ensure teams properly encrypt data both at rest and in transit. For example, verify that all S3 buckets are encrypted with Server-Side Encryption (SSE) and that data is transmitted over HTTPS instead of HTTP. Testing encryption policies helps prevent data breaches and ensures that sensitive data remains secure.
Application Security Testing
Conduct security tests on cloud-hosted applications and APIs. For example, test a web application running on an Azure App Service for vulnerabilities like SQL Injection or Cross-Site Scripting (XSS) using tools like OWASP ZAP or Burp Suite. Finding and fixing these issues helps to protect the cloud applications from attackers.
Testing Identity and Access Management (IAM)
Evaluate how organizations manage user identities, roles, and access policies. For example, test for exposed API keys or IAM roles in AWS that grant unnecessary privileges. By using tools like Pacu(AWS exploitation framework), teams can simulate attacks to see if privilege escalation or lateral movement is possible within your cloud environment.
Documenting and Reporting Findings
After completing the pentest, document all vulnerabilities, misconfigurations, and security gaps found, along with the risk level and potential impact. For instance, if security teams discovered an S3 bucket with public access containing sensitive data, provide clear details on how it was found, its severity, and remediation steps.
Use tools like Dradisor ReportGenerator to create comprehensive and easy-to-understand reports. These reports should include recommendations for fixing the issues and prioritizing them based on risk, helping stakeholders understand and act upon the findings to secure the cloud environment effectively.
Cloud Pentesting Tools
Cloud penetration testing tools empower security professionals to identify vulnerabilities and strengthen defenses in cloud environments. Let's explore some essential tools used in cloud security assessments:
WeirdAAL: An AWS Attack Library
WeirdAAL provides a collection of defensive and offensive security functions specifically for AWS environments. It allows testers to use the tool in black-box testing scenarios, where they simulate attacks without much insider knowledge. Its comprehensive set of features makes it useful for testing the security posture of AWS cloud setups, uncovering potential vulnerabilities efficiently.
ScoutSuite: A Multi-Cloud Security-Auditing Tool
ScoutSuite supports major cloud providers like AWS, Azure, Google Cloud, Alibaba Cloud, and Oracle Cloud. It automates the assessment of cloud environments, giving testers a clear view of the attack surface. The tool helps identify misconfigurations and potential weaknesses across multiple cloud platforms, making cloud security audits simpler and more effective.
Pacu: An AWS Exploitation Framework
Pacu is a versatile exploitation tool designed for AWS environments. Developed by Rhino Security Labs, it includes multiple modules for enumeration of permissions, listing internal AWS resources, and carrying out privilege escalation attacks. Serving as a Metasploit-like tool for the cloud, Pacu allows testers to uncover security gaps in AWS setups efficiently.
S3Scanner: Scan for Open AWS S3 Buckets
S3Scanner automates the discovery of open AWS S3 buckets, making it easier for testers to find public resources exposed to the internet. This tool scans across cloud services for improperly secured storage, enabling the identification of potentially sensitive data. It’s essential to ensure that S3 buckets have correct access controls.
SkyArk: Discover Privileged Cloud Users
SkyArk is designed to identify privileged users within cloud environments, such as "shadow admins." By expanding the scope of the attack surface it helps security teams pinpoint users with elevated permissions. This tool enhances the security of cloud access controls by ensuring that only authorized users have sensitive privileges.
ROADTools: Framework for Azure Active Directory
ROADTools enables interaction with Azure Active Directory (AD) through a library and exploitation framework. It assists in tasks like authentication testing, querying AD data, and exploring the structure of Azure AD. This tool is valuable for testers focusing on the security of identity and access management in Azure.
PowerZure: PowerShell Framework for Azure Security
PowerZure is a PowerShell-based toolkit for reconnaissance and post-exploitation in Azure environments. It provides a range of functionalities, from discovering assets within Azure to testing for potential privilege escalation paths. The tool helps testers simulate attacks and assess the security of Azure cloud infrastructures effectively.
Final Thoughts
Cloud penetration testing provides a crucial layer of defense for organizations in the digital age. By actively identifying and addressing potential vulnerabilities within cloud-based systems, organizations can significantly enhance their security posture, protect valuable data, and bolster customer trust.
Akto is an API security platform that also covers cloud environments by securing APIs across different cloud platforms. It integrates seamlessly with AWS, Google Cloud, and other providers to discover, test, and monitor APIs within cloud infrastructures. Take the first step towards secure and effective API management by booking your demo today.
Explore more from Akto
Blog
Be updated about everything related to API Security, new API vulnerabilities, industry news and product updates.
Events
Browse and register for upcoming sessions or catch up on what you missed with exclusive recordings
CVE Database
Find out everything about latest API CVE in popular products
Test Library
Discover and find tests from Akto's 100+ API Security test library. Choose your template or add a new template to start your API Security testing.
Documentation
Check out Akto's product documentation for all information related to features and how to use them.