Best Stackhawk Alternatives and Competitors
Discover the best StackHawk alternatives and competitors in 2025 to improve your application security testing.

Kruti
Jan 17, 2025
Securing APIs is essential for organizations to prioritize security to protect their sensitive data and ensure compliance. APIs are the backbone of modern applications, and attackers commonly target them. Organizations must use comprehensive API security solutions to protect sensitive data, prevent breaches, and ensure compliance.
StackHawk is a strong API security tool that helps organizations identify and reduce vulnerabilities throughout the development lifecycle. It connects easily with CI/CD pipelines and allows for automatic security testing with each code deployment. StackHawk provides deep insights and enables security professionals to quickly fix issues while maintaining development speed.
This blog talks about the top StackHawk alternatives for 2025, helping organizations to select the best API security solutions.
Top 10 StackHawk Security Competitors
Here are StackHawk's top ten competitors, each offering specific security solutions to help organizations protect their APIs and web apps.
1. Akto API
Akto is an API security platform that automates vulnerability scanning and provides continuous API protection. Akto has an emphasis on minimal setup and ease of integration into CI/CD pipelines, enabling security engineers to quickly find and remediate API issues.
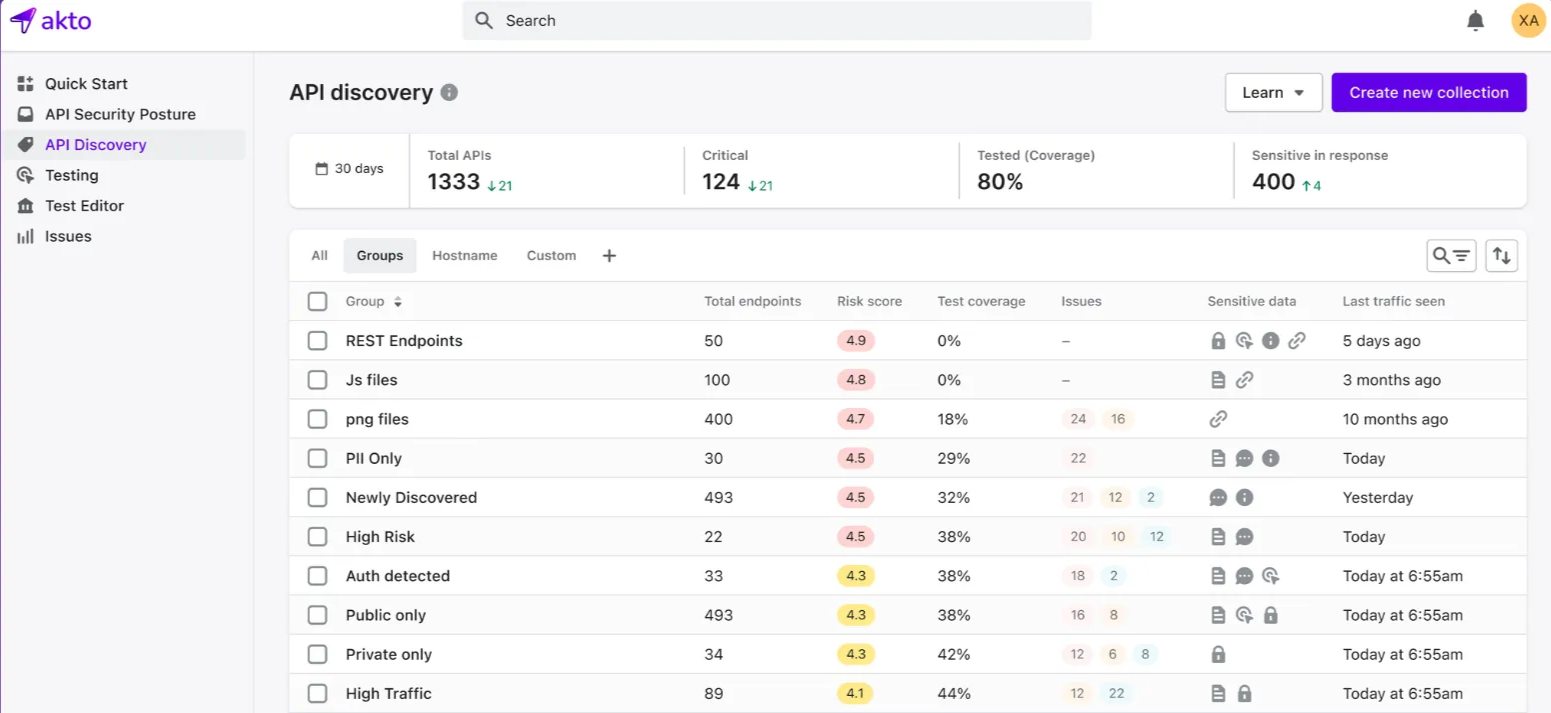
Features of Akto API
API Scanning: The system identifies vulnerabilities in real-time as APIs communicate with actual systems.
Continuous Support: Works well with CI/CD workflows to automate security testing.
Real-Time Monitoring: Quickly detects new vulnerabilities and security threats.
Fast Installation: The setup process is quick, and achieves integration in less than 5 minutes.
Advantages of the Akto API
Real-time Threat Detection: Regular API monitoring to identify security vulnerabilities.
Seamless CI/CD Implementation: Automated security tests across existing workflows for speedy vulnerability response.
Deep Vulnerability Coverage: The platform detects flaws in all API endpoints and components.
Best For: Akto is for organizations that require quick, automated, and effective API security solution, and those that use modern DevOps and microservices architectures. Its smooth interaction with CI/CD pipelines means that security is built into the development process from the beginning.
2. OWASP ZAP
OWASP ZAP is an open-source application security platform that detects vulnerabilities in web applications and APIs. It is for security engineers looking for a free but powerful solution for pen testing and testing for vulnerabilities.
Source: OWASP ZAP
Features of the OWASP ZAP
Automatic Scanning: Automatically scans and detects vulnerabilities in web applications and APIs.
Rigid and Continuous Scanning: Detects vulnerabilities using both strict testing and regular monitoring.
Check API Security: Offers a specific feature for monitoring APIs and web services.
Versatile: Offers a variety of plugins for increasing its features.
Advantages of the OWASP ZAP
Open-Source and Free: There is no cost for using it, and it is available for everyone.
Various Features: Provides various plugins and allows users to add and change them accordingly.
Disadvantages of OWASP ZAP
Hard to Install: Installation is hard and can be tough for beginners.
Lack of Advanced Reporting: Reporting features less than other platforms.
Performance Challenges: Larger apps and scanning several APIs together can be slow.
Best For: OWASP ZAP is for security engineers who are looking for a free, open-source platform for pen testing and vulnerability scanning and technical teams who can install it easily.
3. Bugcrowd
Bugcrowd is a security platform that connects organizations to a global community of legal hackers. This platform performs actual penetration testing to identify vulnerabilities in APIs, online apps, and systems that automated tools might ignore. Bugcrowd regularly works with ethical hackers to make sure that ethical hackers identify and update vulnerabilities before attackers misuse them."
Source: Bugcrowd
Features of Bugcrowd
Penetration Testing: Performs deep security testing using a global network of ethical hackers.
Vulnerability Management: Tools for identifying, prioritizing, and responding to vulnerabilities.
CI/CD Integration: Works smoothly with CI/CD pipelines to carry out security testing across the development process.
Full Reporting: Teams get full vulnerability reports along with simple solutions.
Advantages of Bugcrowd
Performs Real-world Attacks: Real-world attacks are replicated to identify vulnerabilities that automatic approaches may miss.
Customizable Bug Programs: Organizations can adjust bug reward programs for particular types of vulnerabilities or complex environments.
Connection with DevOps Pipelines: Bugcrowd connects smoothly with CI/CD pipelines, allowing continuous security testing across the development process.
Disadvantages of Bugcrowd
Result Quality Variable: Ethical hackers' competency levels are different, which may lead to problems.
Coordination for Vulnerability Resolution: Organizations may need more coordination and resources to manage vulnerability fix operations.
Best For: Bugcrowd is for organizations that want to perform real-world penetration testing and use the skills of a global network of ethical hackers. It is for organizations looking for flexible security testing and continuous vulnerability management as part of their DevOps strategies.
4. Intruder
Intruder is a cloud-based vulnerability scanner that detects flaws in APIs, apps, and infrastructure. It delivers continuous vulnerability scanning to ensure that organizations maintain a solid security posture in the face of evolving threats. Intruder, with its emphasis on simplicity and automation, is designed for organizations of all sizes.
Source: Intruder
Features of Intruder
Regular Vulnerability Scanning: Performs regular scans to find security issues in APIs and apps.
Continuous Monitoring: Regularly monitors APIs and warns teams about emerging threats.
Complete Security Coverage: Scans for the OWASP Top 10 vulnerabilities and other common threats.
Simple Interface: A simple interface to manage scans and see results.
Advantages of Intruder
Integration with Cloud Services: Grants easy integration with cloud platforms such as AWS and Azure.
Simple Setup and Use: It is simple to configure, which makes it suitable for teams with less security expertise.
Continuous Updates: Provide additional vulnerability tests and threat intelligence.
Disadvantages of Intruder
Limited Advanced Features: On comparing with specialized tools, it may lack advanced customization and deep-dive analysis.
Not Ideal for Large Organizations: Designed more for small-scale organizations.
Performance Impact: Scans on active systems can occasionally have an impact on performance.
Best For: Intruder is ideal for small to medium-sized organizations that require automated vulnerability scanning and ongoing monitoring. It's great for teams with limited resources who want full security coverage without a lot of effort.
5. Qualys Web Application Scanning(WAS)
Qualys is a cloud-based security platform that provides strong vulnerability management, including API security. It offers tools to find and reduce vulnerabilities in APIs, networks, and apps.
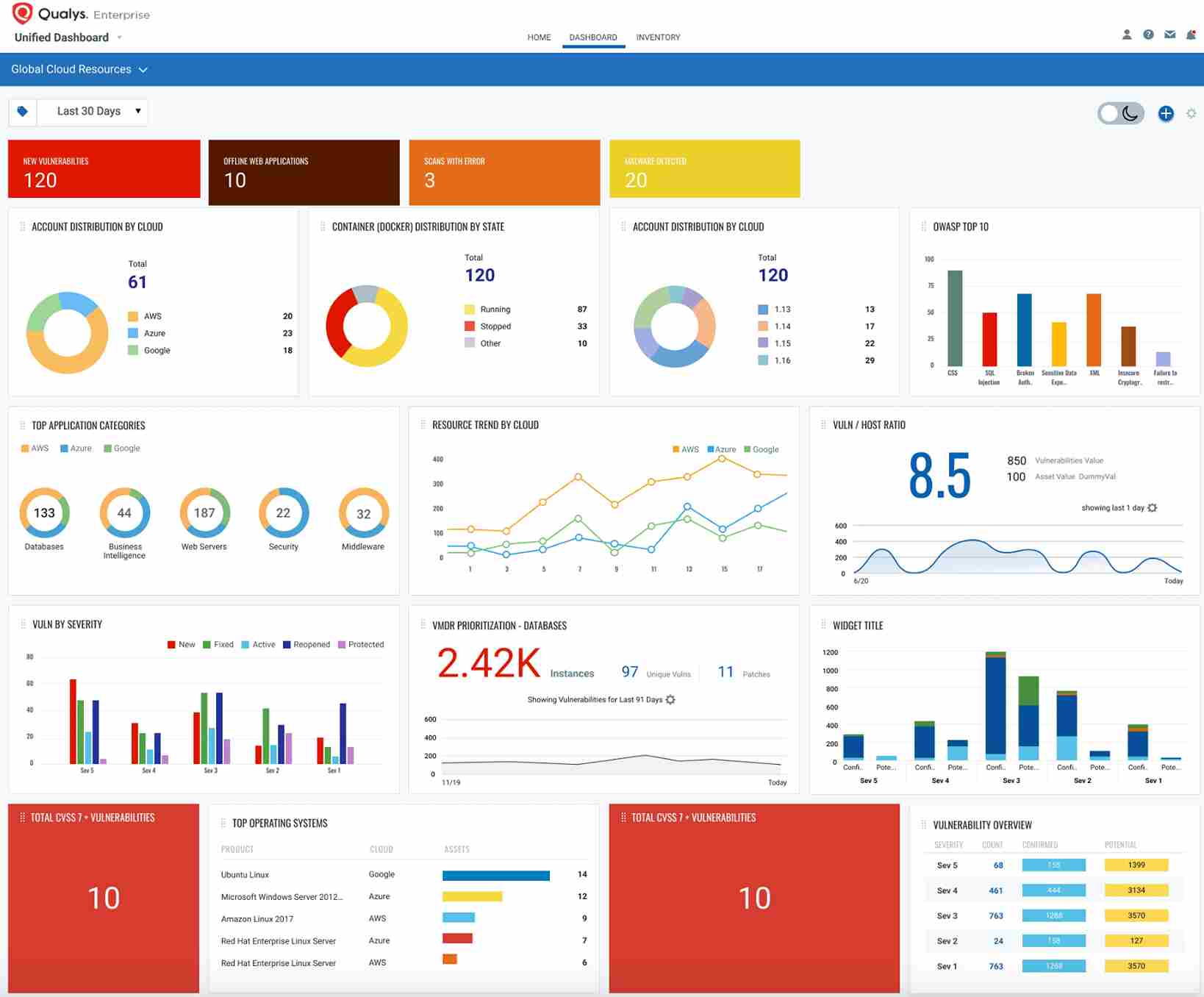
Source: Qualys
Features of Qualys
Regular Vulnerability Scan: Automatically finds weaknesses in APIs through scanning and testing.
Cloud-based Integration: Lightweight agents allow continuous monitoring across on-premises, cloud, and hybrid systems.
Compliance Reporting: Assists organizations in complying with industry standards such as PCI DSS and HIPAA.
Threat Intelligence Integration: Uses global threat intelligence to prioritize and mitigate threats.
Advantages of Qualys
Large Network: It is for organizations that have large networks and API endpoints.
Connects Easily: Connects effortlessly with CI/CD pipelines and other DevOps tools.
Complete Reporting: Provide adherence and vulnerability reports.
Cloud-Based Architecture: Allows easy installation for organizations that work on the cloud.
Disadvantages of Qualys
Costly: Startups and smaller teams can find it expensive.
Complex Interface: Beginners may find the dashboard complex to understand.
Best For: Qualys is for large or medium-sized organizations that have complex environments and need ongoing vulnerability management and compliance monitoring. it is for an organization that works on the cloud and needs complete advanced reporting features.
6. Acunetix
Acunetix is a web application security scanner that runs automated vulnerability tests on APIs, websites, and web apps. Acunetix, which is known for its speed and accuracy, analyzes web applications for over 6,500 vulnerabilities, allowing security teams to discover flaws in real-time.
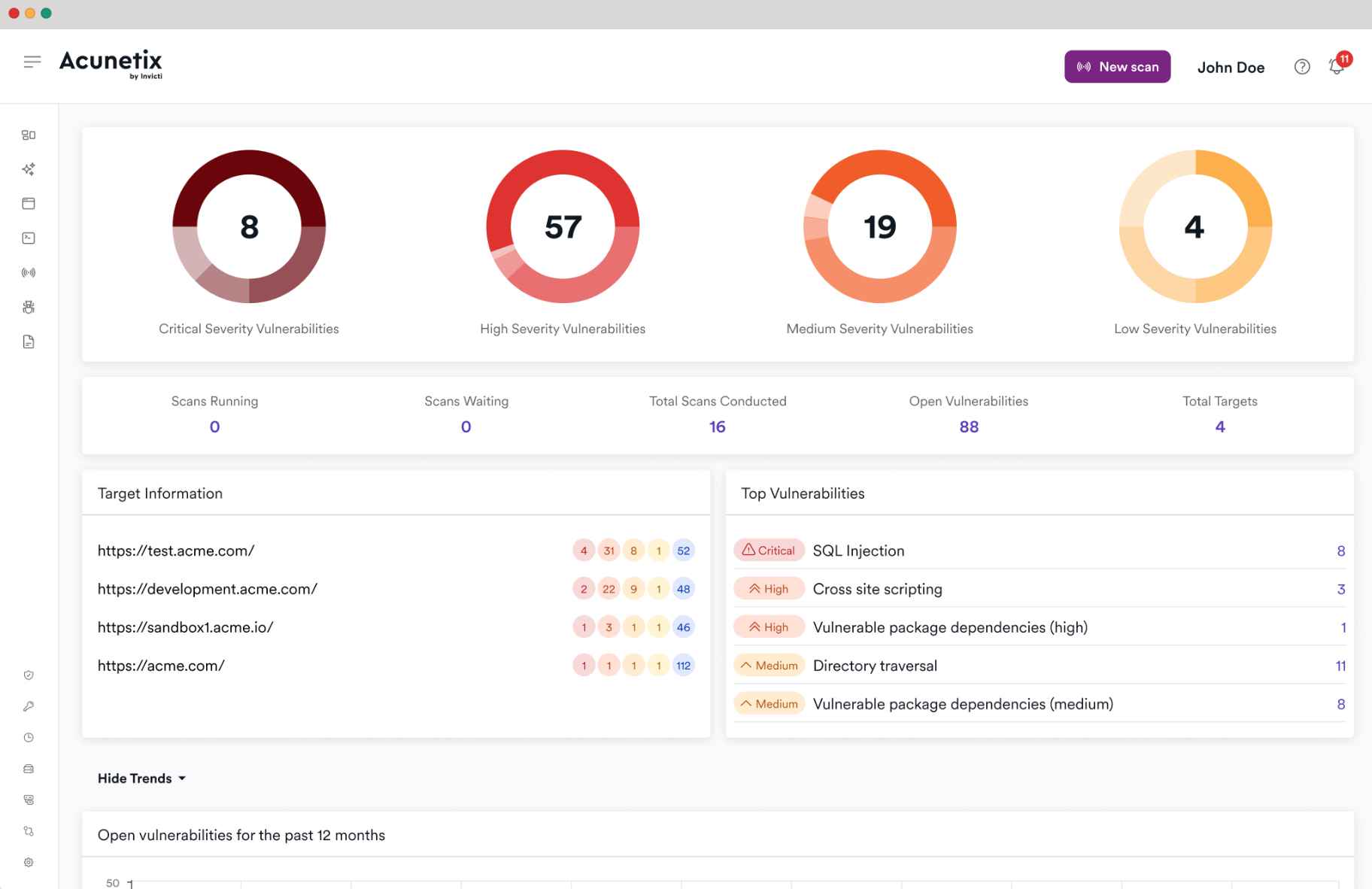
Source: Acunetix
Features of Acunetix
Vulnerability Scan: Checks APIs, websites, and web apps for vulnerabilities.
Advanced DAST Features: Provides DAST features for dynamic application security testing to detect complex vulnerabilities.
Regular Monitoring: Allows for regular monitoring of applications for new vulnerabilities.
API Security Testing: Protects APIs by authentication bypass and input validation checks.
Advantages of Acunetix
Deep Vulnerability Detection: Scan for a variety of vulnerabilities, including the OWASP Top 10 for deep testing.
Fast and Accurate Scanning: Performs quick scans to find vulnerabilities accurately while maintaining performance.
Actionable Reports: Provides detailed, easy-to-understand reports with remediation procedures to help teams resolve issues.
Disadvantages of Acunetix
Limited Customization: Some users may find that the customization options are insufficient for their security requirements
Costly: Smaller organizations with restricted funds may find the pricing expensive.
Best For: Acunetix is best suited for organizations that want fast, comprehensive, and automated web application security testing. It is intended for organizations who want API and web application security testing in one platform.
7. Invicti
Invicti is an automated web application security testing platform that detects web apps and APIs vulnerabilities. It improves accuracy by reducing false positives and provides a complete analysis of security risks.
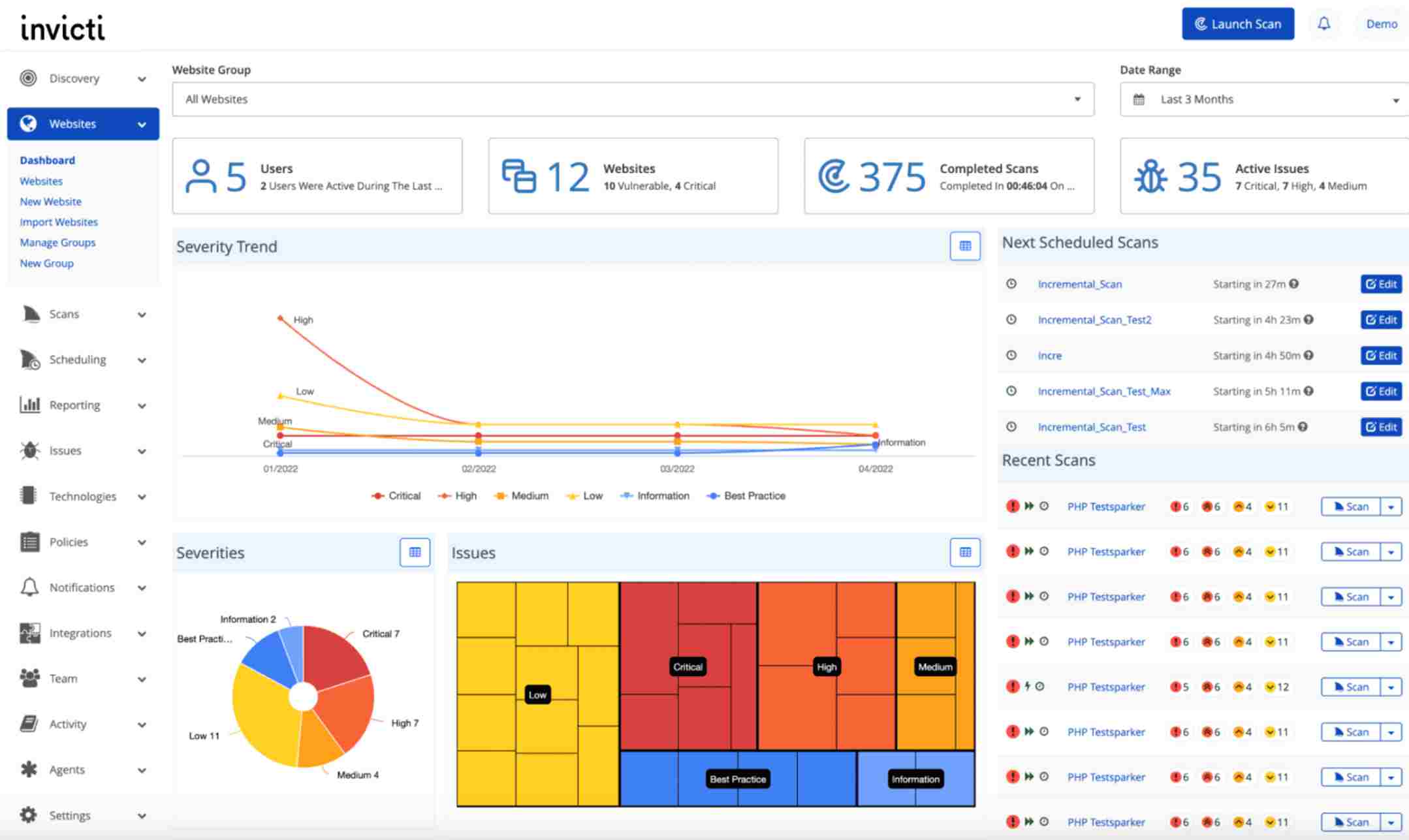
Source: Invicti
Features of Invicti
Deep API Testing: Deep security testing focused on APIs.
Intelligent Scanning: Utilizes innovative algorithms to remove false positives while increasing accuracy.
Compliance Checks: Determines whether an application complies with industry standards.
Detailed Reporting: Creates actionable reports with detailed vulnerability findings.
Advantages of Invicti
Vulnerability Detection: High accuracy with low false positives.
Automated Testing: Automatically scans APIs and web applications without the need for the operator’s involvement.
Scalable: Ideal for big organizations with complex infrastructures.
Disadvantages of Invicti
Expensive: The cost can be high for small to medium-sized organizations.
Configuration: Some people need to set up and customize to fit personal preferences.
Fewer Manual Testing Features: A lesser focus on manual penetration testing.
Best For: Invicti is ideal for organizations requiring high-accuracy vulnerability detection, especially in big environments.
8. Rapid7
Rapid7 is a security platform that focuses on vulnerability management and application security, which now includes API security. It leverages its platform, the InsightVM, for vulnerability scans and enables clients to monitor their security posture regularly. While InsightVM takes care of vulnerability management across networks and assets, the InsightAppSec platform performs API security testing.
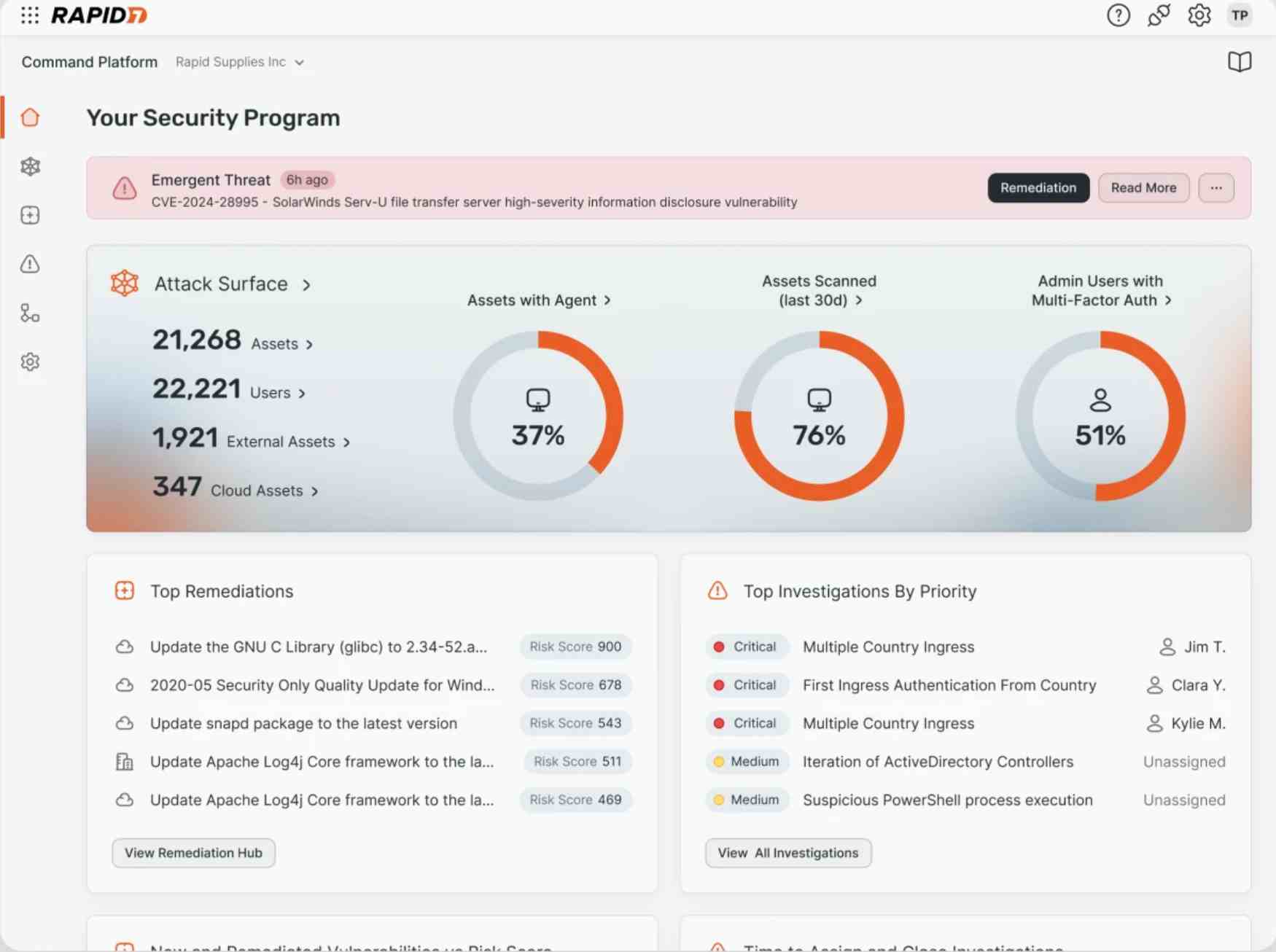
Source: Rapid7
Features of Rapid7
Regular Vulnerability Scanning: Continuous scanning and monitoring to find and prioritize vulnerabilities.
Deep Coverage: Offers extensive coverage of all assets, including APIs, networks, and web applications (via InsightVM and InsightAppSec).
Prioritized Risk Assessments: Provides automated risk prioritizing based on the potential and severity of vulnerabilities.
Detailed Reporting: It provides useful reports that efficiently manage the issues.
Advantages of Rapid7
Complete Solutions: Rapid7 offers full security, IT, and compliance solutions that simplify vulnerability management and threat detection.
User-Friendly Interface: Its straightforward design makes it easy to use, even for beginners in cybersecurity.
Automatic Process: Automates repetitive processes to save time and increase the efficiency of operations.
Deep Analysis: Offers useful insights with detailed data collection and threat intelligence.
Disadvantages of Rapid7
Hard to Install: The start of installation might be complex and require extensive configuration and resources.
High Cost for Small Teams: Pricing may be too expensive for smaller organizations.
Can Show False Positives: Vulnerability scans could find false positives, increasing the effort on security teams.
Best For: Rapid7 is best suited for organizations wanting a real-time vulnerability management solution that prioritizes network and API security.
9. Telerik Fiddler
Telerik Fiddler is a strong web debugging tool that provides API testing and troubleshooting features. It allows security engineers to check, monitor, and secure HTTP/S traffic to detect API vulnerabilities. It has an easy interface and advanced debugging capabilities.
Source: Telerik Fiddler
Features of Telerik Fiddler
Monitors Traffic: Collects and checks HTTP/S traffic between clients and servers.
API Debugging: Provides deep information about API queries and responses for debugging.
Performance Testing: This will help to identify the issues and delays in API performance.
Works on Windows, macOS, and Linux: It works seamlessly on all three operating systems.
Advantages of Telerik Fiddler
Monitoring Traffic: It monitors the traffic at regular intervals and quickly gives an analysis to understand API activity.
Robust Analysis: It provides robust capabilities in terms of analyzing and debugging API calls.
User-Friendly Interface: It gives a simple user interface where everyone can view the analysis of traffic.
Less Expensive: Besides being inexpensive, a free version is available for beginners.
Disadvantages of Telerik Fiddler
Fewer Features: There are fewer automated features for large-scale API security testing.
Poor Testing: It is for troubleshooting rather than conducting a deep security examination.
Sluggish: It may slow down the systems while monitoring more traffic.
Best For: Telerik Fiddler is ideal for small to medium-sized teams working on API debugging, performance testing, and troubleshooting. It is for organizations that need a less expensive solution to improve API dependability and security during the development and testing processes.
10. Probely
Probely is a platform where you can perform security testing for your APIs and web apps. Inadequacies are discovered at an early stage of the development lifecycle, thereby providing the security team an opportunity to appropriately verify and deal with the issues involved. User-friendly, especially with features for automation thereby aiding the development and DevOps teams.
Source: Probely
Features of Probely
Automated Vulnerability Scan: Automatically checks for vulnerabilities in APIs and web applications frequently.
Integration with DevOps Tools: It integrates with CI/CD pipelines and other common DevOps tools.
Deep Advice: Provides clear, concrete recommendations for correcting identified weaknesses.
Scan Customizability: The scope can be chosen by the user for targeted security checking.
Compliance: It includes compliance features such as OWASP, GDPR, and PCI DSS.
Advantages of Probely
Easy for Developers: Designed for developers and provides maintenance support.
Simple Integration: Integrates seamlessly with existing DevOps workflows and CI/CD pipelines.
Customizable Reports: Provides personalized reports to fulfill organizational and compliance requirements.
Ease of Use: Its user-friendly interface streamlines vulnerability management.
Regular Updates: Consistently updates to handle the most recent threats and vulnerabilities.
Disadvantages of Probely
Limited Advanced Features: Large-scale organizations may lack the advanced capabilities they want.
Dependent on Automation: It is highly dependent on automation and focuses less on manual testing possibilities.
Pricing For Small Teams: Smaller teams or organizations with limited resources may find it expensive.
Best For: Probely is for DevOps teams and medium-sized organizations that need an automated, user-friendly security solution for connecting to their CI/CD pipelines. It is intended for organizations that focus on early-stage vulnerability detection and compliance.
How to Choose the Best API Security Solution
Protecting an organization's data and applications from modern security threats is complex. Organizations must choose a strong API security solution. The correct tool helps to prevent breaches, assure compliance, and preserve operational efficiency. The following are five key criteria to consider while comparing API security solutions.
Integration with Existing Systems
A powerful API security solution integrates very smoothly with the current infrastructure, reducing interruption. It can implement with CI/CD pipelines, complex environments, or hybrid cloud systems and support the right technology. Solutions with pre-built connectors for a common DevOps platforms make deployment easier and include security in the development process.
Cost and Budget Considerations
It is important to maintain a balance between functionalities and cost considerations when choosing an API scanning tool. On examining scalability, cost of ownership, subscription plans and other services, the security teams can choose their preferable API security tool that aligns with their budget plans.
Scalability and Future Growth
When the organization grows, the chosen solution should be able to work according to more API endpoints, traffic, and integrations. Scalable platforms maintain performance while also adapting to new security problems. This scalability is important for providing effective protection in increasing or complicated contexts.
Feature Set and Customization
The scope and depth of a tool's features affect its effectiveness. Solutions that include vulnerability assessment, threat detection, and real-time monitoring provide comprehensive security. Customizable settings, alarms and reports improve adaptability by allowing security teams to optimize tool performance based on individual operating requirements.
Ease of Use and Deployment
Ease of deployment promotes quick integration into organizational workflow. Platforms with user-friendly interfaces, clear reporting, and simple configuration decrease onboarding time and increase productivity. A simple solution allows security engineers to focus on defensive measures rather than operational challenges.
Final Thoughts
Stackhawk offers a sophisticated API security solution with features like automatic vulnerability detection and CI/CD integration, but it may not be the best choice for every organization. Organizations seeking significant customization or a more comprehensive security suite may find Stackhawk lacking in certain features, such as deep code analysis or detailed compliance reporting. Akto is a strong competitor for organizations looking for a user-friendly, quick-to-deploy solution with a focus on real-time threat detection.
Akto will meet all the requirements of security engineers and organizations seeking an intuitive, agile, and efficient API security tool. Akto's ability to continually monitor and protect APIs in production, combined with its extensive vulnerability assessment, distinguishes it as a modern, powerful solution targeted to organizations' increasing needs. It is a good solution for organizations of all sizes seeking rapid implementation at low cost. Schedule A Demo Now!
