Top 10 API Security Tools in 2025
Top 10 API security tools help organizations protect their APIs from threats and vulnerabilities by offering real-time monitoring, authentication, encryption, and compliance to safeguard sensitive data and prevent unauthorized access.

Muze
Oct 9, 2024
API Security tools protect APIs by monitoring, detecting, and preventing threats in real-time, ensuring that they keep sensitive data secure and they prevent unauthorized access. This blog explores some of the top API security companies or API security vendors and their features to help application security engineers choose the best API protection tools for their unique organization needs.
What are API Security Tools?
API security tools are needed for protection of APIs from different kinds of threats and vulnerabilities. As APIs increasingly form part of the building blocks of software and data exchange, robust security cannot be emphasized more.
API Protection tools provide crucial features such as authentication, encryption, and access control to safeguard sensitive data and prevent unauthorized access. Moreover, they offer real-time monitoring and threat detection capabilities, enabling organizations to quickly identify and respond to potential security breaches.
Why are API Security Tools Important?
API security tools are important, especially when APIs are becoming the heart of most digital transformations. Here are the significant reasons why API Protection tools hold great importance:
Growing Attack Surface
Cybercriminals are targeting APIs more these days because they connect services and transfer sensitive data. A compromised API can cause serious data breaches, which can leak PII and other sensitive information.
Complexity of Security Needs
APIs do not follow traditional security measures, but instead, require a very specific security framework to tackle the vulnerabilities, including insecure authentication and inadequate access controls. API security tools aid in implementing these sophisticated security measures.
Real-Time Threat Detection
Many API security tools leverage AI and machine learning to analyze traffic patterns and detect anomalies in real-time. This capability allows organizations to respond swiftly to potential threats, minimizing the impact of any security breaches.
Compliance and Regulatory Requirements
Organizations must adhere to several regulations related to data protection. API security tools make compliance a bit easier since they enable APIs to adhere to the basic security standards to protect an organization and its customers simultaneously.
Secure Development Practices
API security tools integrate into the development lifecycle, allowing for early detection of vulnerabilities during the development phase. This proactive approach helps prevent developers from deploying security flaws into production environments.
Mitigation of Logic Flaws
Many breaches occur due to logic flaws within APIs rather than traditional vulnerabilities like SQL injection or XSS attacks. Specialized tools can identify these logic vulnerabilities before attackers can exploit them.
Key Criteria for Evaluating API Security Tool
When selecting API Security Tools, API security companies or API Security Vendors, application security engineers focus on several critical factors.
They look for API Security tools that offer robust security measures, including authentication, encryption, and compliance with standards like GDPR. The engineers ensure the solution gives them real-time threat detection and prevention as well as incident response capabilities. They review the reviews of the customers and check case studies to get effectiveness and review the organization's industry reputation and awards received.
Application Security engineers prefer API Security tools that integrate seamlessly with existing systems and support various environments, such as cloud, hybrid, and on-premises. They ensure the solution scales with increasing traffic and maintains performance under high loads.
Responsive and knowledgeable customer support is crucial, and security engineers look for cost-effective solutions with transparent pricing. Additionally, they favor API Protection tools that offer customization for specific needs, detailed reporting and analytics, and utilize AI/ML for enhanced threat detection.
10 Best API Security Tools in 2025
In the rapidly changing landscape of API security, there are top API security companies or API security vendors emerging with innovative solutions and complete protection. Let's take a look at the 10 best API security vendors:
1. Akto
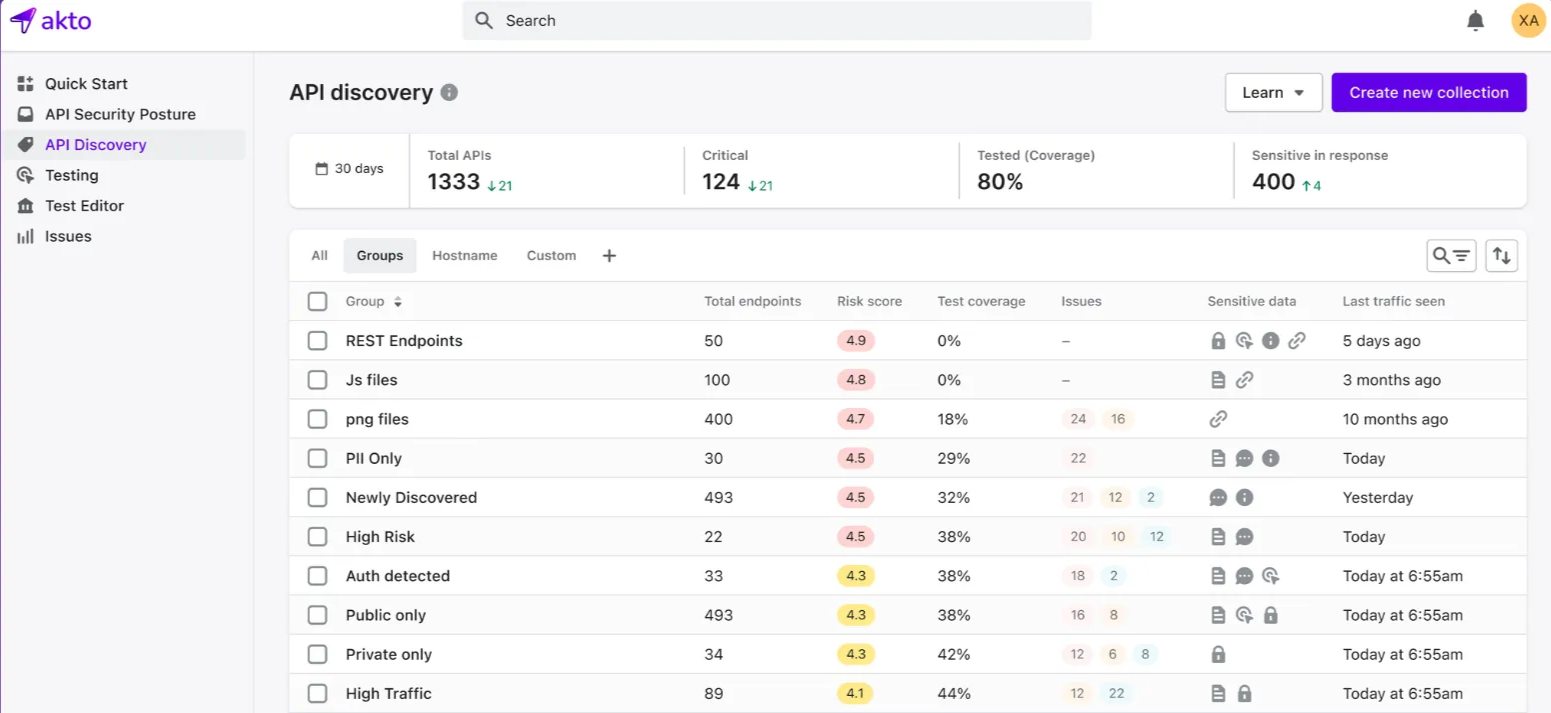
Akto is an API security-focused security platform that will continuously scan for vulnerabilities, misconfigurations, and actionable insights, improving the security posture of the organization's API ecosystem. It integrates easily into the CI/CD pipeline and thus enables real-time monitoring as well as quick remediation of potential threats.
Key Features
Discovers all APIs within the organization’s system without manual intervention.
Performs more than
400 pre-built security checksto uncover any vulnerabilities present.Provides ongoing monitoring and management of the API security status.
Guarantees strong security for authentication and authorization.
Easily integrates with
CI/CD pipelinesto support continuous testing.
Pricing
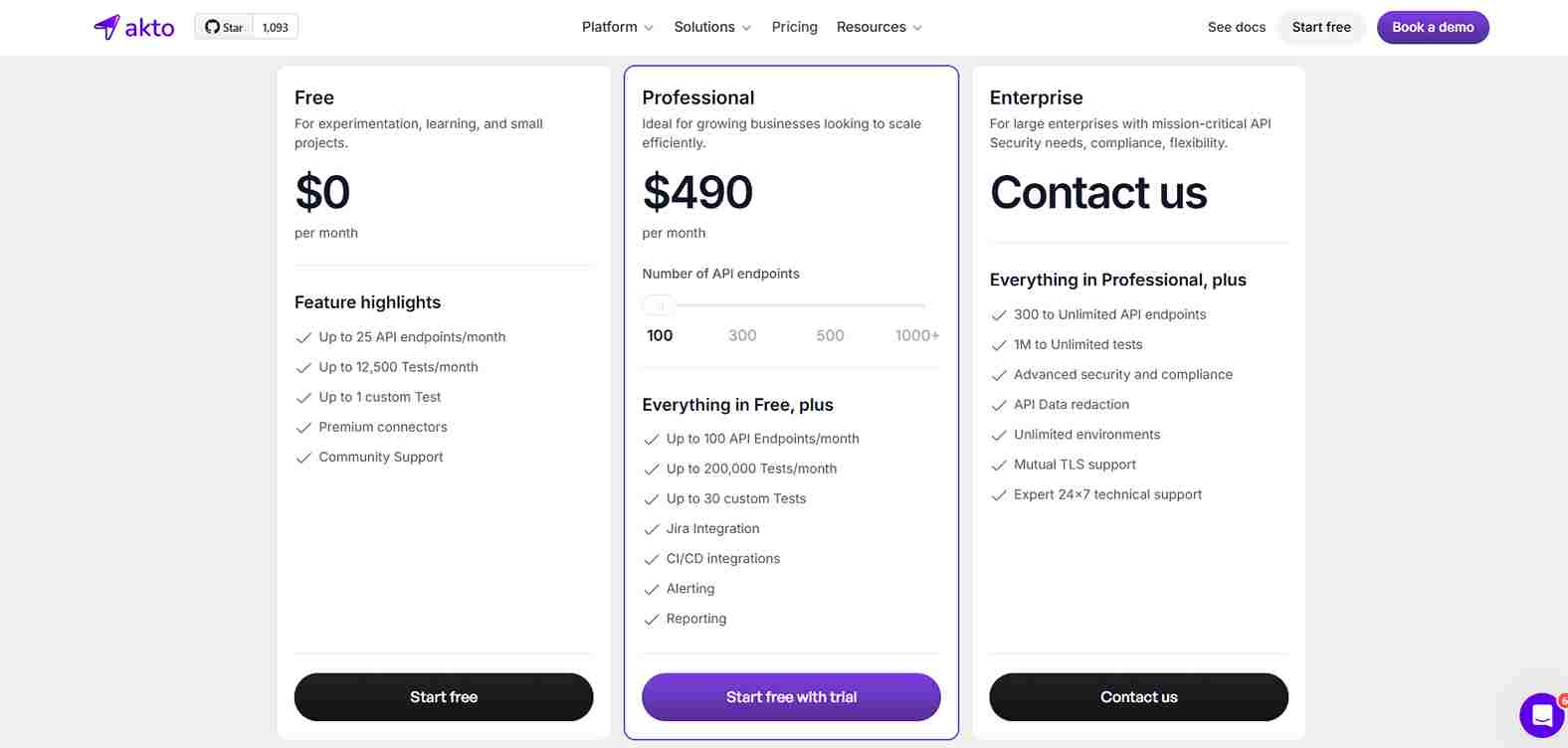
Image Source: Akto.io
Akto provides different pricing plans, accommodating various needs of an organization:
Free Plan: The free plan works best for individuals or small teams who want to test out the features of Akto or do a little light API security testing. With limited scalability, this plan suits
early-stage developers or organizationsexploring API security without significant costs.Professional Plan: Aimed at small e-commerce sites and organizations requiring advanced security and performance, the Business Plan offers additional features and support. The monthly cost is
$250, and the annual payment can be made at$2,400, which amounts to$200per month.Enterprise Plan: This is a type of custom plan solution targeted toward large organizations that have custom requirements. They provide pricing if it is requested and negotiate for an organization’s customized requirements.
2. F5
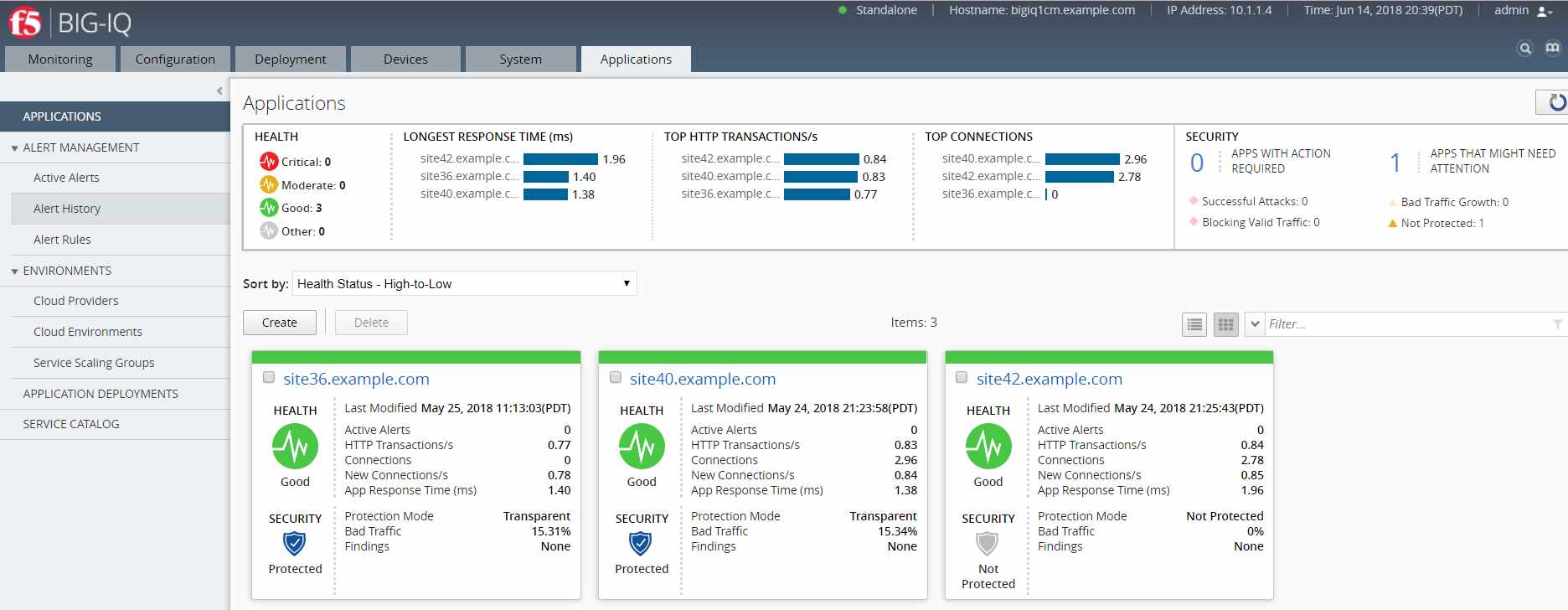
Image Source: F5
F5 is a leading multi-cloud application services and security company providing advanced solutions to protect APIs and web applications. It has a reputation for its set of security offerings, more so in protecting applications against Distributed Denial-of-Service (DDoS) attacks, bot traffic, and other types of web-based threats. F5 helps organizations ensure the performance, availability, and security of their applications in an increasingly distributed environment.
Key Features
F5 offers comprehensive DDoS protection that effectively mitigates large-scale attacks targeting APIs and web applications.
Enhances API performance and security with
traffic managementandload balancingcapabilities.F5 Advanced WAF provides API security, protection against injection attacks and other forms of unauthorized access to an API.
AI-powered threat intelligence identifies and mitigates new, emerging cyber unauthorized access to an API.
Pricing
F5 has different application delivery and security solutions in various price structures based on different deployment models and needs of organizations:
1. Licensing Options
Perpetual Licensing: F5 offers "Good, Better, Best" product bundles under perpetual licenses, allowing organizations to choose services that best meet their needs. Bundles can save as much as
65%over buying individual modules.Subscription Licensing: For added flexibility, F5 offers
subscription-basedlicensing for theirBIG-IP Virtual Editions(VE) in 1-, 2-, or 3-year terms. This model includes maintenance, support, and self-licensing options that enable organizations to scale services as needed.
2. Distributed Cloud Services
F5's Distributed Cloud Services are SaaS-based solutions that provide security, networking, and application management across various environments. The pricing of these services varies according to specific use cases and subscription plans. For instance, F5 charges a rate-limiting of $0.05 per 10,000 requests.
3. Additional Considerations
F5's price structures are often complex and there may be additional costs for particular add-ons or advanced features. Therefore, organizations need to do a cost-benefit analysis of the chosen solution to ensure that it will meet the budget and operational requirements. Only for the most up-to-date and accurate prices and recommendations must security engineers communicate with F5 directly, or perhaps through authorized resellers from F5.
3. Cloudflare
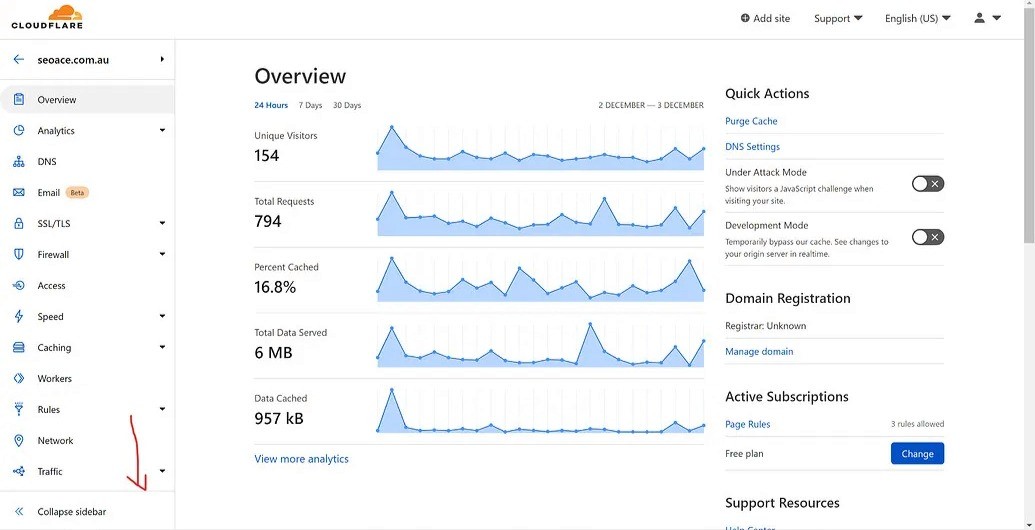
Image Source: Cloudflare
Cloudflare is known for the robust API security platform with which it offers assistance for organizations that intend to defend their APIs against all abusive and threat-ridden interactions. With an integrated WAF, DDoS protection, and bot management feature, this API Shield from Cloudflare detects malicious traffic and can stop real-time malicious API traffic by offering protection along with a wide range of features starting with OAuth authentication up to mTLS encryption for protection so only authorized users and devices get to your APIs.
Key Features
Rate limiting to prevent abuse by setting strict thresholds for API usage.
DDoS protection for APIs to safeguard against volumetric attacks.
Organizations achieve industry compliance standards, such as
PCI DSSand GDPR, for the enhanced protection of data and regulatory compliance.Machine learning-based detection against abuse of the API and injection or other types of data exposure attacks.
Pricing
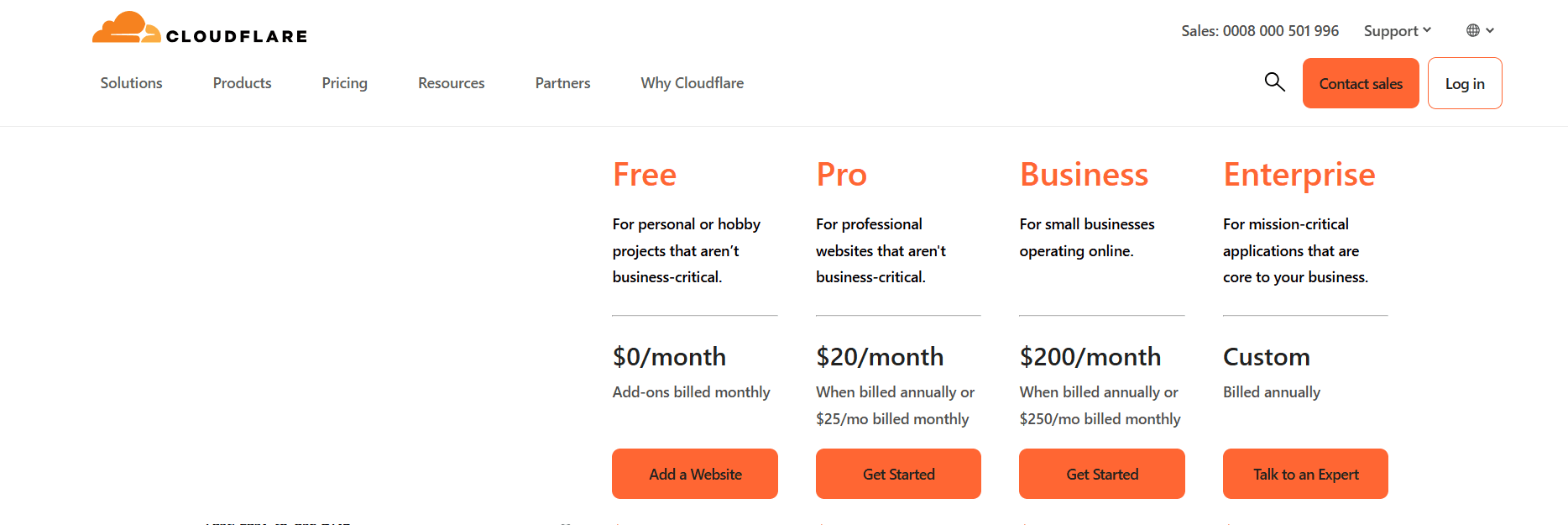
Cloudflare offers several plans designed for various needs, and each plan has its specific features and pricing structures:
Free Plan: This entry-level option provides essential services such as
SSL,CDN, andDDoS protection, making it suitable for personal websites or blogs.Pro Plan: Designed for professional websites and startups, the Pro Plan includes advanced security features and performance enhancements. As of
January 15, 2023, Cloudflare sets the price of the Pro Plan at$25 per month. Cloudflare also offers an annual option for$240 per year, effectively reducing the monthly cost to$20.Business Plan: The plan targets small e-commerce sites and organizations requiring advanced security and performance. This has extra features and support, with a monthly fee of
$250. The annual payment option is$2,400, or$200per month.Enterprise Plan: The Enterprise Plan provides custom solutions to big organizations that have unique needs. They make pricing available upon request and adjust it according to the needs of the organization.
Akto’s Recommendation
Akto offers real-time monitoring and threat detection, allowing organizations to quickly identify and mitigate potential vulnerabilities. Similar to Cloudflare’s API Shield, Akto monitors traffic patterns for anomalies but focuses exclusively on API-specific threats, ensuring precise and actionable insights.
4. Zed Attack Proxy (ZAP)
Image Source: OWASP ZAP
The Open Web Application Security Project (OWASP) developed ZAP as an open-source web security testing tool. The community maintains it to ensure it stays up-to-date and effective against the latest threats. ZAP primarily offers penetration testing through automation.
Key Features
It is used to test web applications and APIs against several vulnerabilities defined by the OWASP Top 10 and is free and open-source.
It integrates easily with other platforms.
Supports Java and other languages like JRuby and Javascript.
Pricing
OWASP Zed Attack Proxy (ZAP) freely provides access for use without any associated licensing fees. Users can download and utilize ZAP's full features at no cost, making it an accessible option for both individuals and organizations aiming to enhance their web application security.
5. Wallarm
Image Source: Wallarm
Wallarm acts as a comprehensive API security platform that specifically suits modern API-first organizations. The product comes with real-time API discovery and exhaustive threat prevention that covers the whole portfolio regardless of whether one is dealing with multi-cloud or cloud-native environments.
Key Features
Provides the full set of API security tools and has seamless integration into other platforms.
Gives analysis and dashboards of the test report.
It integrates nicely with any CI/CD workflow, enabling the automatic execution of dynamic test cases.
Pricing
Wallarm offers a range of subscription plans tailored to different security needs:
WAAP and Advanced API Security This plan provides comprehensive protection for web applications and APIs against common threats such as
SQL injection,cross-site scripting(XSS), and brute force attacks. It supports all API protocols and addresses specific API threats, including those outlined in the OWASP API Top 10. Features include real-time protection,DDoS mitigation, IP reputation feeds, virtual patching, and automated protection againstBroken Object Level Authorization(BOLA).API Attack Surface Management (AASM) Designed to provide a comprehensive view of publicly exposed APIs, this agentless solution discovers external hosts and their APIs, identifies missing Web Application Firewalls (WAFs), and detects credential leaks. The number of external hosts determines the pricing, with the Core plan starting at
$325per month for25 hosts. An Enterprise plan is available for larger requirements, offering extended support and additional services.Security Edge This plan enables users to deploy the Wallarm node in a managed environment., eliminating the need for onsite installation and management. Wallarm handles node hosting and maintenance, providing robust traffic filtering, attack detection, and secure communication.
Free Tier Ideal for smaller organizations and educational purposes, the Free Tier account allows processing up to
500,000requests per month with no time limitation. It provides access to the Wallarm platform's Advanced API Security features, excluding certain functionalities like Security Edge Inline and Connectors, exposed assets scanner, vulnerability assessment, and API Abuse Prevention. Users can create a Free Tier account on either the US or EU Wallarm Cloud.
6. SALT Security
Image Source: SALT Security
SALT Security is a well-known API security company that uses AI to provide Continuous Delivery (CD) and real-time protection for the APIs against harmful cyber attackers. This approach offers better insights into the organization’s API security throughout its lifecycle.
Key Features
Uses artificial intelligence to detect and respond to suspicious behavior quickly.
Provides deeper insights into API usage and any gaps.
Employs sophisticated pattern recognition to prevent business logic abuse.
Delivers continuous discovery and assessment of API risks.
Pricing
Salt Security does not publicly provide specific pricing information regarding its API Protection Platform. Salt Security designs its pricing to address the specific needs of a particular organization most of the time. It might consider the scale of its deployment, the number of APIs, and more specific security requirements.
To get the right and tailored price quote, they suggest contacting Salt Security directly through their official channels. This way, security engineers will be able to interact with their sales team, which will provide them with a quote that meets the organization's specific API security requirements.
7. Imperva Security
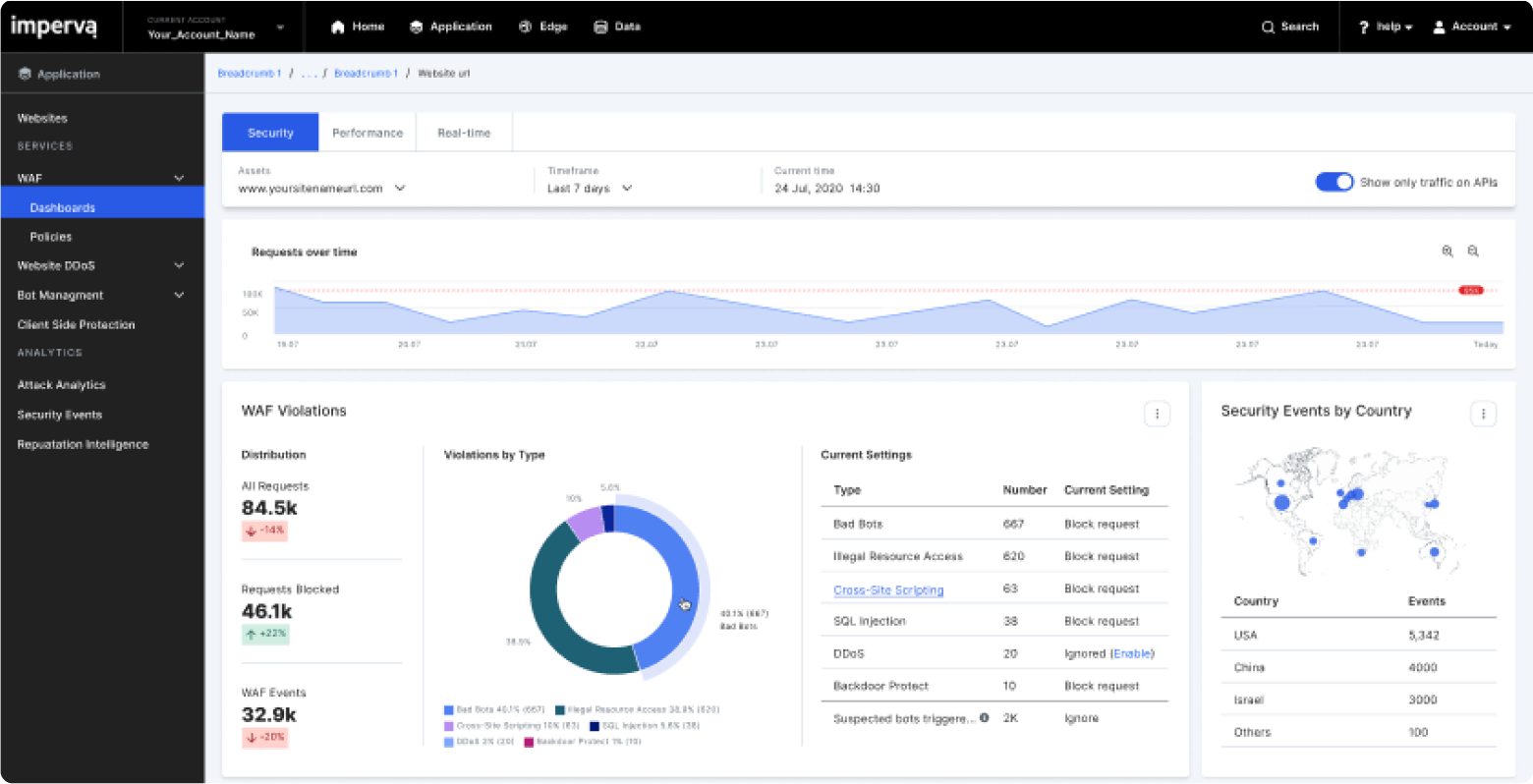
Image Source: Imperva
The market offers Imperva as one of the outstanding API security solutions. This platform offers several features and all-around protection for APIs such as DDoS protection, bot mitigation, and API web traffic analysis.
Key Features
Provides advanced bot security to prevent automated cyber-attacks.
Conducts API web traffic analysis to determine any security threats and stop them.
It ensures robust DDoS protection to keep the API available during heavy traffic.
Pricing
Imperva's site doesn't provide detailed price offerings for its solutions or products. The prices could range differently based on factors including, for example, the needed solution, scale of deployments and the needs of the organization. To obtain accurate and tailored pricing information, it's recommended to contact Imperva directly.
Akto’s Recommendation
Akto automatically recognizes and protects sensitive data types, including PII information such as Social Security Numbers, credit card information, and email addresses. This is one of the similar capabilities that Imperva offers, except Akto offers deeper insight tailored for API-driven environments, ensuring complete compliance with the standards of data protection.
8. IBM API Connect
Image Source: IBM Connect
IBM's API Connect is a complete API management and security platform. The tool offers a comprehensive API gateway, a robust developer portal, and analytics with a focus on security. Moreover, the long history of IBM in enterprise solutions makes this tool a favorite among organizations.
Key Features
Delivers a complete API management platform with built-in security features.
Provides analytics to monitor API traffic and identify potential threats.
Supports OAuth for secure authentication and authorization.
Pricing
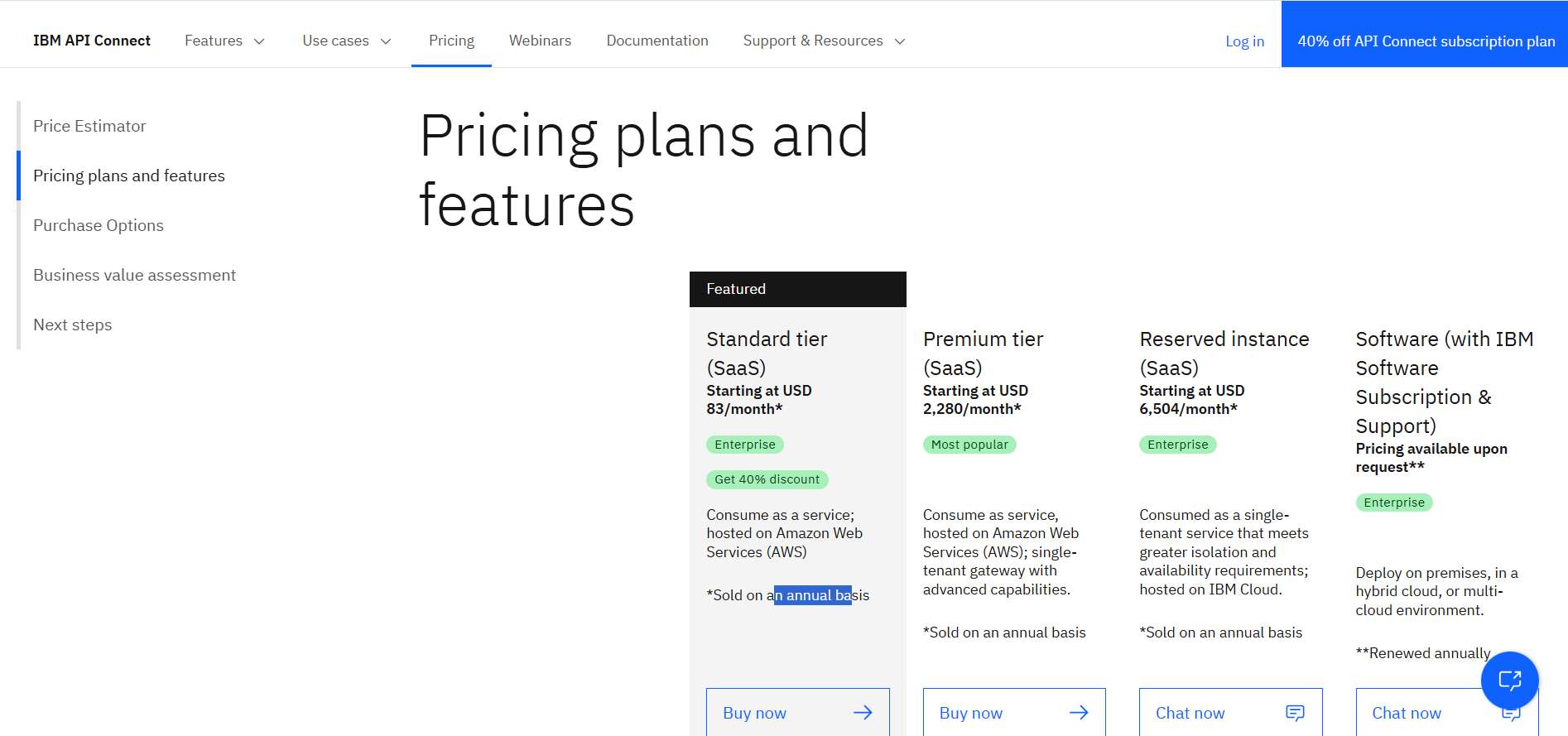
Image Source: IBM API Connect
IBM API Connect offers flexible pricing plans to accommodate various organizational needs, available as both on-premises software and Software as a Service (SaaS) hosts on Amazon Web Services (AWS). The primary SaaS plans include Standard, Premium, and Reserved Instance, each designed to cater to different requirements.
IBM API Connect provides flexible pricing plans to suit different organizational needs, and it is available as both on-premises software and Software as a Service (SaaS) hosted on Amazon Web Services (AWS). The main SaaS plans are Standard, Premium, and Reserved Instance, all of which are designed to meet different needs.
Standard Plan: This multi-tenant offering hosts on AWS and is ideal for organizations seeking a cost-effective solution. Pricing starts at approximately
USD 83 per month, billed annually, and includes up to100,000 API callsper year. This plan provides essential API management features suitable for small to medium-sized enterprises.Premium Plan: Also hosts on AWS, the Premium Plan offers a single-tenant gateway with advanced capabilities, making it suitable for larger organizations with higher security and performance demands. Pricing begins at around
USD 2,280 per month, billed annually, and supports a higher volume of API calls.Reserved Instance Plan: For enterprises requiring greater isolation and availability, the Reserved Instance Plan provides a single-tenant service hosted on IBM Cloud. Pricing starts at approximately
USD 6,504 per month, billed annually. IBM tailors this plan for organizations with stringent compliance and performance requirements.Limited-Time Promotion: Purchase the SaaS Standard Plan subscription now until the
31st of December in 2024for just40% discountedcost. This offer includes any new subscription, thereby disregarding renewals.
For organizations that prefer on-premises deployment, IBM offers a software option for which pricing is available upon request. This option will allow deployment across on-premises, hybrid cloud, or multi-cloud environments, providing flexibility to accommodate diverse infrastructure needs.
To estimate costs based on specific requirements, IBM offers a Price Estimator Tool on their official pricing page. This tool helps organizations calculate expenses by selecting the desired offering, private data connectivity options, and estimated annual API call volume.
9. StackHawk
Image Source: Stackhawk
StackHawk is a trusted API security tool that lets security teams find, fix, and prevent various security vulnerabilities in the APIs with ease. The tool's key highlight is its easy integration into the development pipeline, making it an excellent option for DevOps teams.
Key Features
Empower developers to find and solve pressing security concerns throughout the development lifecycle.
Supports a lot of programming languages and frameworks.
It integrates fairly easily into CI/CD workflows, and it works to identify and resolve defects.
Pricing
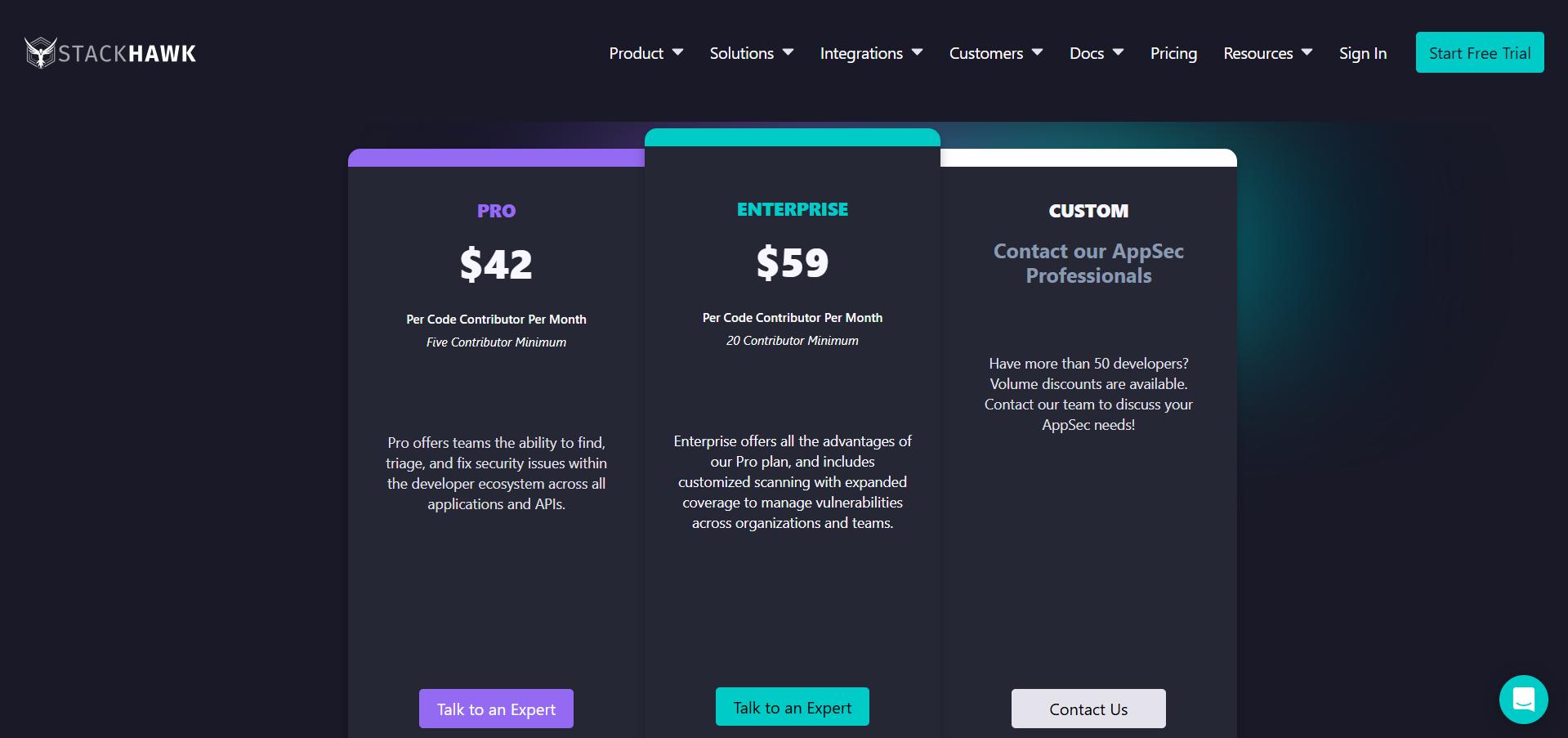
Image Source: StackHawk
StackHawk offers a variety of pricing plans to suit different team sizes and needs:
Pro Plan: Priced at
$42 per code contributorper month, with a minimum of five contributors, this plan provides enhanced features suitable for teams aiming to integrate security testing seamlessly into their development processes.Enterprise Plan: This plan costs
$59 per codecontributor per month and requires at least20 contributors. Larger organizations with more complex security needs design its advanced capabilities.
For organizations with more than 50 developers, StackHawk offers custom plans with volume discounts. All plans include unlimited scans, comprehensive API support, and integration with existing development tools to ensure thorough security coverage.
Akto’s Recommendation
Akto integrates nicely into CI/CD workflows and enables automated API security testing during development. This allows teams to find vulnerabilities at the early stages of the software lifecycle, much like StackHawk's CI/CD-centric approach. However, Akto specifically tailors the tests to API-specific vulnerabilities, making it a very effective tool for API-first organizations.
10. Cequence
Image Source: Cequence
Cequence Security offers a unified API security platform that provides protection across the entire API lifecycle. It specializes in detecting and mitigating API threats such as data leaks, API abuse, and automated attacks. Cequence focuses on both API visibility and protection, ensuring organizations have a clear view of their API ecosystem and the API Security tools necessary to defend against complex threats.
Key Features
Provides full visibility into known and unknown (shadow) APIs to detect and mitigate risks.
Offers API threat protection by blocking suspicious actions and analyzing real-time traffic.
Pricing
The cost of the Unified API Protection platform is not publicly disclosed. Pricing varies depending on factors such as the size of the organization, the number of APIs that need protection, and specific security needs that the business may have. Security engineers can obtain detailed pricing tailored to their organization's requirements by contacting Cequence Security through their official website.
Final Thoughts
API usage being on the rise requires maximum security for digital assets and applications. API security is essential in safeguarding the rapidly increasing threats. Using innovative protection tools from leading companies in API security allows companies to detect and mitigate their risks, thereby providing an assurance of secure data handling and smooth operation of service.
Among the top API security solutions, Akto stands out with its extensive capabilities. Akto offers over 100 built-in tests and seamless integration with platforms like AWS . It excels in API discovery, automated testing, and identifying critical vulnerabilities. Akto's user-friendly interface and strong security measures make it an excellent choice for organizations looking to enhance their API security and stay ahead of potential threats.
To explore Akto further, book a demo today.
Related Links
Experience enterprise-grade Agentic Security solution
