What is API Security?

Insha
Oct 4, 2024
APIs play a decisive role in today's software systems by enabling different uses to communicate and share information. Without proper security mechanisms malicious actors can exploit APIs as entry points leading to information breaches and unauthorized access.
This blog dives into the world of API security—exploring its importance common risks and practical strategies to protect APIs. This blog will also discover the best tools for security testing, the latest security standards and frameworks, and actionable best practices to fortify the API infrastructure against emerging threats.
What is API Security?

API security protects the communication between different software applications from threats and attacks. This keeps data safe from unauthorized access by making sure approved users and systems can use the API. Put security measures in place like authentication, encryption, and validation to stop misuse. Keep an eye on and test APIs often to spot any security problems. By securing APIs, application security engineers and security teams protect their organization and its data from potential breaches.
Why is API Security Important?
API security is crucial because APIs are the backbone of modern web applications and services. Here’s why it matters:
Protects Sensitive Data
APIs frequently handle extremely sensitive information, which may involve personal identifiers such as names, addresses, and social security numbers, along with financial information like bank account data and credit card numbers, as well as confidential business details such as trade secrets or proprietary algorithms. Using strong encryption, authentication, and authorization techniques to protect APIs helps safeguard data from unwanted access, hacks, and information leaks.
Prevents Unauthorized Access
Well-protected APIs implement strong access controls to make sure that only authenticated and approved users or applications can interact with them. This involves checking user identities, enforcing permissions, and using tools like OAuth, API keys, and tokens to manage access. By stopping unwanted access, application security engineers protect their organization from bad actors who might try to take advantage of weak spots, steal information, or do harmful things that could hurt operations.
Maintains Service Availability
APIs are the foundation of today's apps linking services and enabling smooth operation. Attackers use techniques like DoS or DDoS to overwhelm APIs with traffic cutting off access for real users. Mitigate these threats by adopting security strategies including rate limiting, throttling, and intrusion detection systems.
Ensures Data Integrity
This is very important in applications where the accuracy of information is paramount, such as financial transactions, healthcare records, and communications systems. Secure APIs maintain the integrity of data by ensuring that clients and servers transmit information accurately and ensure it remains unchanged during transfer. Checksums, cryptographic hashing, and digital signatures are some of the strategies that are used to inspect tampering attempts and to verify data integrity.
Builds Trust
Application Security Engineers must secure APIs to show commitment to security, privacy, and user protection, fostering trust and confidence in their organization. This will give the organization the stamp of security and reliability to more users and retain the older ones.
Compliance with Regulations
Numerous sectors are governed by rules that require the safeguarding of confidential information. For example, the General Data Protection Regulation (GDPR) in the European Union requires companies to safeguard personal information, whereas the Health Insurance Portability and Accountability Act (HIPAA) in the U.S. requires the safeguarding of medical information.
What are Common API Security Risks?
APIs connect systems but often face various attacks. Organizations can safeguard their information and ensure the integrity of their applications by recognizing these risks associated with API security.
1. Broken Object Level Authorization (BOLA)

BOLA is a critical API security risk that arises when an API does not properly enforce access control checks for object-level permissions. Attackers exploit this vulnerability by manipulating object identifiers, such as IDs or UUIDs, in API requests.
Attackers gain unauthorized access to sensitive data belonging to other users. For example, by guessing or enumerating object IDs, an attacker could retrieve another user's private information, such as medical records or account details.
2. Broken Authentication
Broken Authentication vulnerability occurs when APIs cannot determine the identity of the user. Defects in login mechanisms associate with this: weak policies for passwords, absence of multi-factor authentication, or mismanagement of tokens. From this, attackers can seize opportunities to impersonate real users or gain unauthorized access to the critical data. For example, not properply securing API keys or session tokens can results in account takeover attacks. To prvent this risk, APIs must implement secure authentication protocols, enforce MFA, and regularly audit authentication processes.
3. Broken Object Property Level Authorization (BOPLA)
BOPLA vulnerabilities occur when APIs fail to enforce access controls at the granular property level of objects. Even if APIs restrict object-level access, attackers may still exploit unsecured properties within those objects.
For example, if an API exposes a user’s financial details and does not restrict access to individual fields (like account balance or payment history), an attacker might retrieve or modify this data. APIs should implement field-level access control and validate permissions for every exposed property to mitigate this risk.
4. Unrestricted Resource Consumption
APIs that lack proper rate limiting and resource management are vulnerable to attacks that exhaust system resources. Malicious actors can overwhelm API with too many requests, resulting in denial-of-service (DoS) situations. This security weakness is particularly damaging to an organization's systems with high availability requirements. Successful mitigation involves enforcing rate limiting, quotas, and employing monitoring tools to detect and block abusive actions. APIs should also include back-off mechanisms to handle excessive load gracefully.
5. Broken Function Level Authorization
Inadequate authorization checks for API endpoints that execute specific functions can lead to attackers accessing privileged operations. For instance, an attacker could invoke admin-only functionalities, such as deleting user accounts, if proper access restrictions are not in place.
This issue often arises when role-based access control (RBAC) is poorly configured or entirely absent. APIs need to establish robust authorization checks and ensure that all permissions at the function level correspond with the roles and privileges of the user.
6. Unrestricted Access to Sensitive Business Flows
Some APIs expose critical business logic, such as order processing or payment approval, without sufficient safeguards. Attackers can exploit these exposed flows to manipulate transactions, bypass payment steps, or abuse promotions.
For example, an attacker might place an order without proper validation of payment information. Mitigating this risk requires applying rigorous input validation, enforcing strict business logic controls, and thoroughly testing APIs for abuse scenarios.
7. Server-Side Request Forgery (SSRF)
SSRF vulnerabilities allow attackers to make unauthorized server-side requests through an API. This can expose sensitive internal resources, such as cloud metadata or private networks, to external attackers. For instance, by manipulating a URL parameter, an attacker could access confidential internal APIs or retrieve sensitive data that internal systems store.
8. Security Misconfiguration
Security Misconfigurations can leave organizations vulnerable to various attacks, such as unauthorized access and data breaches. Common issues involve usage of default login credentials, revealing debug endpoints, or incorrectly set CORS policies. For instance, leaving unnecessary HTTP methods (like PUT or DELETE) enabled can allow attackers to modify or delete data. APIs must adopt secure-by-default configurations, disable unnecessary features, and conduct regular configuration reviews to minimize this risk.
9. Improper Inventory Management
APIs often multiply and spread across different environments, such as development, staging, and production. Failing to maintain an accurate inventory of API endpoints, versions, and hosts can result in attackers exploiting deprecated or undocumented APIs.
For instance, an attacker might target an old API version with known vulnerabilities. Proper inventory management requires the use of automated tools to identify and document all APIs, monitor changes across different environments, and safely retire obsolete endpoints.
10. Unsafe Consumption of APIs
APIs frequently rely on third-party services to enhance functionality. However, blindly trusting data or responses from these third-party APIs can introduce vulnerabilities. Attackers may exploit these integrations by injecting malicious payloads, triggering unexpected behavior in the consuming API. For example, an attacker could manipulate a third-party API response to execute unauthorized actions on a dependent application.
REST API Security
REST API security involves several strategies that protect RESTful APIs from threats, vulnerabilities and unauthorized access. Without robust security measures, REST APIs can become entry points for attackers, resulting in data breaches, service disruptions and reputational damage. Effective REST API security not only protects the confidentiality and integrity of data but also helps maintain trust with users and compliance with regulatory requirements.
SOAP API Security
SoapUI is a popular open-source tool designed specifically for testing APIs, supporting both SOAP and REST protocols. With its powerful scripting capabilities and easy-to-use interface, SoapUI enables security teams to create, manage, and automate comprehensive API tests, ensuring that APIs function correctly and securely under different conditions.
GraphQL API Security
GraphQL serves as a query language for the API and provides a server-side environment to run queries based on a type system that teams create for their data. GraphQL API security involves adopting strategies and measures to safeguard GraphQL APIs from a wide range of threats and vulnerabilities. As GraphQL continues to gain traction due to its powerful and flexible nature. Therefore, securing these APIs has become increasingly critical for organizations leveraging this technology.
gRPC API security
gRPC API security refers to a set of strategies that aim to safeguard gRPC (Google Remote Procedure Call) services from potential threats and vulnerabilities. gRPC is a high-performance communication framework widely used for building distributed systems and microservices. It stands out for its unique features, such as its use of HTTP/2 for transport and Protocol Buffers (Protobuf) for data serialization, which enable efficient, low-latency communication across services.
What is an API Vulnerability?
API vulnerabilities refer to the potential weaknesses, flaws, or gaps in an API’s design, implementation, or configuration that malicious actors could exploit. These weaknesses can occur at any point during the API lifecycle, starting from the design and development stages to deployment, ongoing maintenance, and ultimately, decommissioning. If security teams leave these weaknesses unaddressed, they can lead to critical consequences including data breaches, unauthorized access, privilege escalation, service disruptions, and even complete system compromise. For instance, APIs may expose sensitive endpoints without proper authentication controls, leave critical functions accessible without authorization checks, or fail to validate user inputs effectively. These issues create opportunities for attackers to exploit APIs as a gateway into broader systems.
What are the Most Common API Misconfiguration Errors?
API misconfigurations can cause serious security vulnerabilities and system compromises. Understanding and addressing these common errors is important for maintaining robust API security. Here are the most frequent misconfiguration issues organizations encounter:
1. Insecure Default Configurations
APIs usually ship with default settings that favor convenience over security. These settings may include default credentials (e.g., "admin/admin") or permissive configurations that they document widely and, therefore, attackers can easily exploit.
For instance, third-party tools and frameworks might have open debug modes, default ports, or unrestricted access levels that attackers can exploit if left unchanged. An attacker can leverage these insecure defaults to bypass authentication, access sensitive functionalities, or even gain administrative control over the API. To mitigate this risk, always review and harden the default configurations by disabling unnecessary features, changing default credentials, and following secure setup guides.
2. Inadequate Access Controls

Access control mechanisms are crucial in guaranteeing that only permitted users are able to carry out particular tasks or obtain specific information. For example, an API endpoint might allow a regular user to perform administrative actions due to a lack of role-based or object-level access control checks.
This can result in data leaks, privilege escalation or system compromise. Effective mitigation includes introducing strong authentication, role-based access control (RBAC), or attribute-based access control (ABAC), and permissions validation for any request.
3. Verbose Error Messages
APIs can inadvertently return detailed error messages that disclose sensitive information about the system's architecture and components. For example, error responses may reveal database connection strings, server stack details, or specific software versions. Based on this information, attackers empower themselves to map the infrastructure and know where potential vulnerabilities should be exploited. To eliminate or minimize such risks, APIs should employ generic error handling that offers enough details for legitimate users without leaving behind sensitive details. A full error logging for local debugging purposes is acceptable; however, this should also only be done securely on server-side logs.
4. Misconfigured HTTP Headers
HTTP headers are the most essential layer of API security, for they define how the server and client can securely communicate with each other. A misconfigured or missing header may leave APIs to be vulnerable to Cross-Site Scripting, insecure data transmission, and unauthorized access. For instance, a wrongly set up Content-Security-Policy header allows attackers to inject evil scripts into a user's browser. Similarly, not setting the Strict-Transport-Security (HSTS) header leaves open communication channels to be done insecurely in HTTP, making them prone to man-in-the-middle attacks. APIs must configure security headers appropriately, including enabling CSP, HSTS, and secure CORS policies.
5. Open Cloud Storage
Many APIs use cloud storage services to store and manage data, but improper configurations expose sensitive files to unauthorized users. For example, improper configurations of an Amazon S3 bucket or Azure Blob container can misconfigure it and allow public access to files containing user data, API keys, or backups. Attackers can use these kinds of exposures to steal data or inject malicious content into applications. To mitigate such risks, security teams must review and configure cloud storage settings carefully to restrict access to authorized users only.
Security teams should disable public access unless explicitly required, and teams should always encrypt sensitive data both in transit and at rest. Regular security audits and monitoring tools can help identify and address misconfigurations proactively.
What is Credential Stuffing for APIs?
It is a form of cyber attack where an attacker uses stolen credentials, such as usernames and passwords, that attackers obtain from a data breach of one service to attempt unauthorized access to another, unrelated service.
This method exploits the tendency of individuals to reuse the same credentials across multiple platforms. For example, imagine a scenario where an attacker acquires a list of usernames and passwords leaked from a data breach at a major department store. The attacker then takes this list and systematically attempts to log in to the online banking portal of a national bank, using the stolen credentials.
The attacker's strategy relies on the likelihood that some customers of the department store also have accounts at the bank and that they have reused the same login credentials for both services. If any of the stolen username-password combinations match the credentials for the bank accounts, the attacker gains unauthorized access, potentially leading to financial fraud, identity theft, or other malicious activities.
What are the Latest Trends in API Security?
As API security continues to evolve rapidly in response to emerging threats and technological advancements, several key trends are shaping how organizations protect their APIs.
Zero Trust Architecture for APIs
Organizations are increasingly applying Zero Trust principles to securing their APIs because zero trust requires continuous identity and device verification for each API access request. This ensures no one inherently trusts any request that helps in minimizing the risks of unauthorized access. With Zero Trust, which treats every request from inside or outside the organization's network-as potentially harmful, it enforces strict access controls and, therefore, significantly enhances API security posture.
Increased Focus on API Governance
The growing utilization of different APIs has increased the demand for a strong API governance. The governance frameworks define security best practices based on different types of APIs, technologies, and standards. These frameworks address challenges posed by protocols such as GraphQL, AsyncAPI, and REST by ensuring uniform security measures, version control, and compliance requirements and reducing vulnerabilities related to inconsistent practices or outdated policies.
Evolving API Gateway Solutions
API gateways, which once centralized control points to manage API traffic, are becoming more distributed models. In the new architectures, the lightweight gateways now sit closer to the APIs they serve. This will reduce latency and improve responsiveness. This migration makes it possible to scale to more granular security policy management while ensuring high performance. Organizations can ensure that better scalability and localized enforcement of security as well as a much improved developer experience come from distributing responsibility across multiple gateways and addressing increasing API ecosystem complexity.
Addressing API Sprawl and Visibility Challenges
The growth of APIs has led to significant problems for organizations in terms of API sprawl. Outdated documentation, unmanaged endpoints and misconfigured APIs result in blind spots that malicious attackers can exploit. Organizations must address these challenges with effective management techniques, like discovery tools, inventory tracking, and solutions for monitoring centrally. Improvement of visibility and control leads organizations to the prevention of risk and maintaining their API environment securely and orderly.
Types of API Attacks
There are different types of API attacks, each targeting different vulnerabilites in API Implementations. The following are the main types of API attacks that organizations need to defend:
1. Injection Attacks
Injection attacks happen when a malicious actor introduces harmful code or commands into an API request, exploiting inadequate input validation or security measures. When the API processes this malicious input as part of its execution, it can result in unauthorized actions such as data theft, unauthorized data manipulation, or even full system compromise.
2. Authentication Hijacking
Authentication hijacking occurs when an attacker gains unauthorized access to a system by stealing or exploiting authentication tokens. Once an attacker obtains a valid token—whether through interception, brute force, or phishing—they can impersonate legitimate users and perform unauthorized actions within the system.
This type of attack is a serious threat because the attacker can bypass authentication processes and, thus, make his actions seem valid. The effects of authentication hijacking can be data breaches, unapproved access to confidential information, and identity theft. Such attacks can undermine the trustworthiness of the API and the systems related to it.
3. Data Exposure
Data exposure happens when an API accidently reveals confidential data during data transmission. One of the reasons of this is returning more data than needed, lacking wrong access controls, or not using the secure communication channels.
The attackers take advantage of these vulnerabilities to gain access to confidential data that includes personal user information, financial records, or proprietary business data. Data exposure has broad-ranging implications, from violations of privacy and regulatory penalties to loss of customer trust and reputational damage.
4. Parameter Tampering
Parameter tampering refers to changing the parameters in an API to modify its intended behavior. An attacker may alter query parameters, path variables, or payload data in order to access unauthorized information, bypass security measures, or take advantage of vulnerabilities in the logic of the API.
For example, an attacker might change the limit parameter in an API request to retrieve more data than permitted, or they might alter an account ID to access another user's information. Parameter tampering can lead to unauthorized data access, theft of sensitive information, and data manipulation.
5. Man-in-the-Middle (MitM) Attacks
In this attack, the attacker intercepts API calls to get sensitive information like authentication credentials, session tokens, or even private data. Moreover, the attacker may alter the intercepted data to inject malware payloads or alter the communication while taking advantage of the vulnerabilities in the target system.
The impacts of MitM attacks include data breaches, Unauthorized access to systems, and Information manipulation. These hacks expose confidential information to the assailants. This means that these can pose serious security and privacy problems.
API Security Best Practices
With the increasing reliance on data-driven projects, protection of sensitive data is the key. The following are some of the API security best practices that are required to secure APIs effectively.
Identifying Vulnerabilities
Begin by assessing the risks present in the organization to pinpoint vulnerabilities in the API lifecycle. For instance:
SQL Injections: If the API allows SQL queries from users, an attacker could inject malicious SQL code to access or modify the database in the organization. For example, a user might enter a string like
'; DROP TABLE users; --in a login form to delete the users table. Check out the SQL Injection prevention cheat sheet.JSON Path and Schema Validation: Enforce strict rules by using
JSON pathandschema validationto prevent attackers from injecting malicious data. Validate fields expecting a username to accept only simple strings and reject any scripts or complex objects, thereby ensuring the API processes only the intended data types.Rate Limits: The implementation of rate limiting can prevent an attacker from overwhelming the API with requests. An example of this is setting a limit of 100 requests per minute on every user.
Using Security Tokens
Security tokens ensure secure communication by requiring token authentication on both ends before proceeding. For example:
Access Control: A user logging into an online banking service receives a token. Each subsequent request, such as transferring money or checking balances, requires this token. The system denies access to anyone trying to use these services without the token.
Session Management: In an e-commerce website, after a user logs in, they receive a token. This token serves to verify identity and grant permission for tasks such as adding products to the shopping cart, completing a checkout, or accessing order history.
Implementing Encryption
Encryption safeguards information by transforming it into a coded format that only permitted individuals can interpret using the appropriate decryption key. This process is crucial for safeguarding sensitive information both during transmission and when it is stored.
Data in Transit: Whenever data moves between the client and the server, it is considered "in transit." Encryption protocols like
HTTPSencrypt data transmitted over the internet., preventing attackers from intercepting or altering it. For example, when a person accesses a banking application, HTTPS encrypts their username, password, and transaction details, making them unreadable to anyone trying to eavesdrop.Data at Rest: This refers to data stored on a disk or in a database. Encryption for data at rest protects sensitive information from unauthorized access. For example, an API that stores a user's credentials or other sensitive data, such as social security numbers or health records, can encrypt the information and, thereby, in its storage, which means a hacker cannot access the same even if the hacker infiltrates the server.
End-to-End Encryption (E2EE): This encrypts data from the sender to the receiver, so that only these two parties can access the information. It even prevents the service provider from reading the data in transit. For example, messaging applications employ end-to-end encryption to guarantee that messages can only be seen by the sender and the designated receiver, keeping them safe from third-party surveillance or hacking attempts.
Utilizing OAuth and OpenID Connect
OAuth defines how client-side applications obtain access tokens, while OpenID Connect adds an authentication layer on top of OAuth. For example:
OAuth: A third-party app that wants to access Google contacts. Instead of sharing the Google login credentials, you grant the app access through OAuth. The app receives an access token, allowing it to access your contacts without the password.
OpenID Connect: When you sign in to a new service using your Google account, OpenID Connect verifies your identity with Google, ensuring that the service knows who you are without storing your Google password.
Applying Throttling and Quotas
Throttling and quotas manage bandwidth and prevent system overloads. For example:
Throttling: Throttling controls the rate at which users or applications can make API requests, helping prevent overuse or abuse of the service. It sets a maximum limit on the number of allowed actions, like API calls or data transfers, within a specified timeframe. Once a user reaches this limit, the API slows down.
A streaming service like Netflix limits video streams per user each hour to prevent congestion and ensure fair use. When users exceed this limit, the service denies new streams and displays a message to try again later.
Quotas: Quotas enforce a cap on the total amount of resources a user or application can consume within a specified period, such as a day, month, or year. Unlike throttling, which controls the rate of requests, quotas set a hard limit on the overall usage.
A cloud storage service like Google Drive allows
1 GBof uploads per day to manage capacity and ensure fair use. If users exceed this limit, the service blocks further uploads until the next day.Deploying an API Gateway
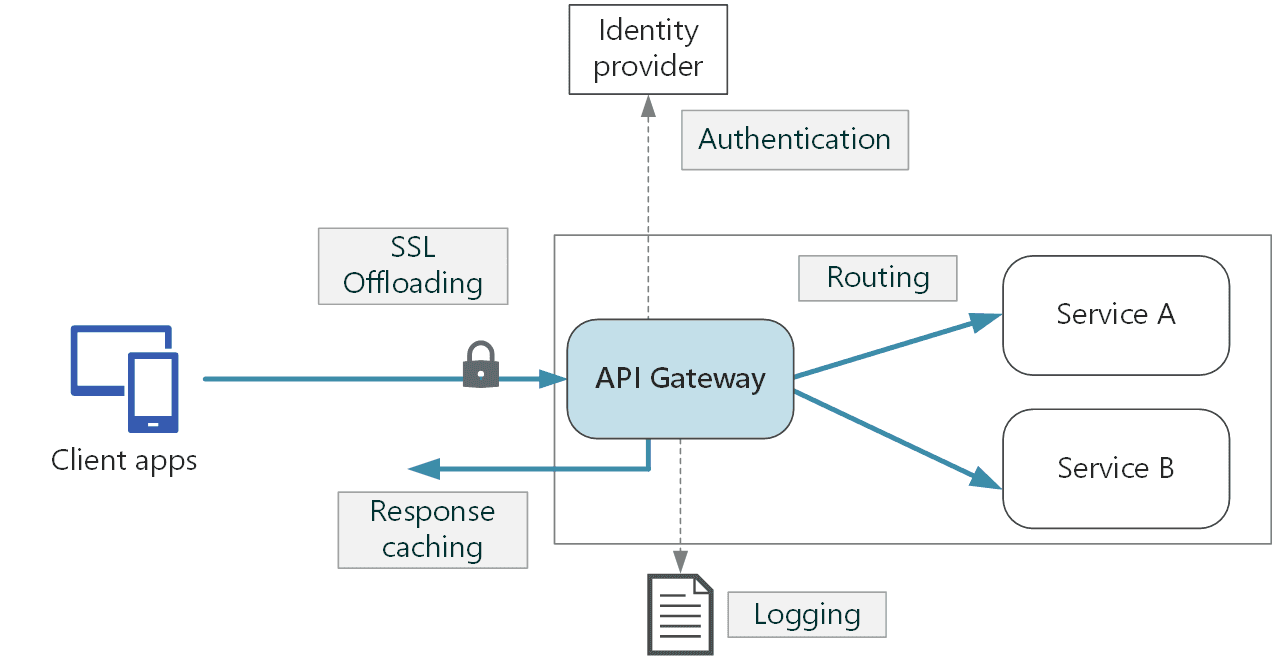
An API gateway acts like a reverse proxy that takes client requests and routes them to backend services while offering centralized controls for security, rate limiting, and performance optimization. It simplifies client interaction by providing a single entry point to all API calls.
Authentication and Routing: On an online marketplace, an API gateway handles authentication and routes requests for complex systems. On log-in, the gateway authenticates the users' credentials. Valid authentication will then route the request to the right backend service. For example, the user management service receives requests meant for profiles, while those for product browsing go to the inventory service, and the order requests go to the order management service. In this manner, all the different functions on the marketplace are handled in efficient ways.
Load Balancing: API gateways distribute incoming requests evenly across multiple servers through load balancing, making sure that no single server is burdened. For example, when a news website has very high volumes of requests for articles, videos, or other types of content, it would use an API gateway to help manage those requests. It checks the load on every server and directs the request to the least busy server to ensure even distribution of traffic and a smooth, fast user experience.
Adopting a Zero-Trust Approach
A zero-trust security model assumes that all traffic, whether internal or external, is untrusted. For example:
Network Access Control: In a corporate environment, employees must authenticate their devices and user credentials before accessing any resources, even if they are on the internal network. This stops an attcker who obtains access to the network from navigating through it without restriction.
Continuous Monitoring: A financial institution continuously monitors user activities and device health. If an employee's device shows signs of compromise, the system restricts its access until the issue is resolved.
What is an API Security Platform?
It refers to a comprehensive framework for protecting APIs in terms of security threats and vulnerabilities through all their stages. An API security platform provides protection at various stages, from the design, development, and deployment through runtime, thus making sure it gives robust defenses against unauthorized access, data breaches, and other harmful infiltration. Secure coding, rigorous testing, and threat detection in real-time can help protect these APIs while keeping information as well as services intact
Top API Security Solutions
Quite a few powerful API security companies perform API security testing, each offering distinct features:
OWASP ZAP (Zed Attack Proxy)
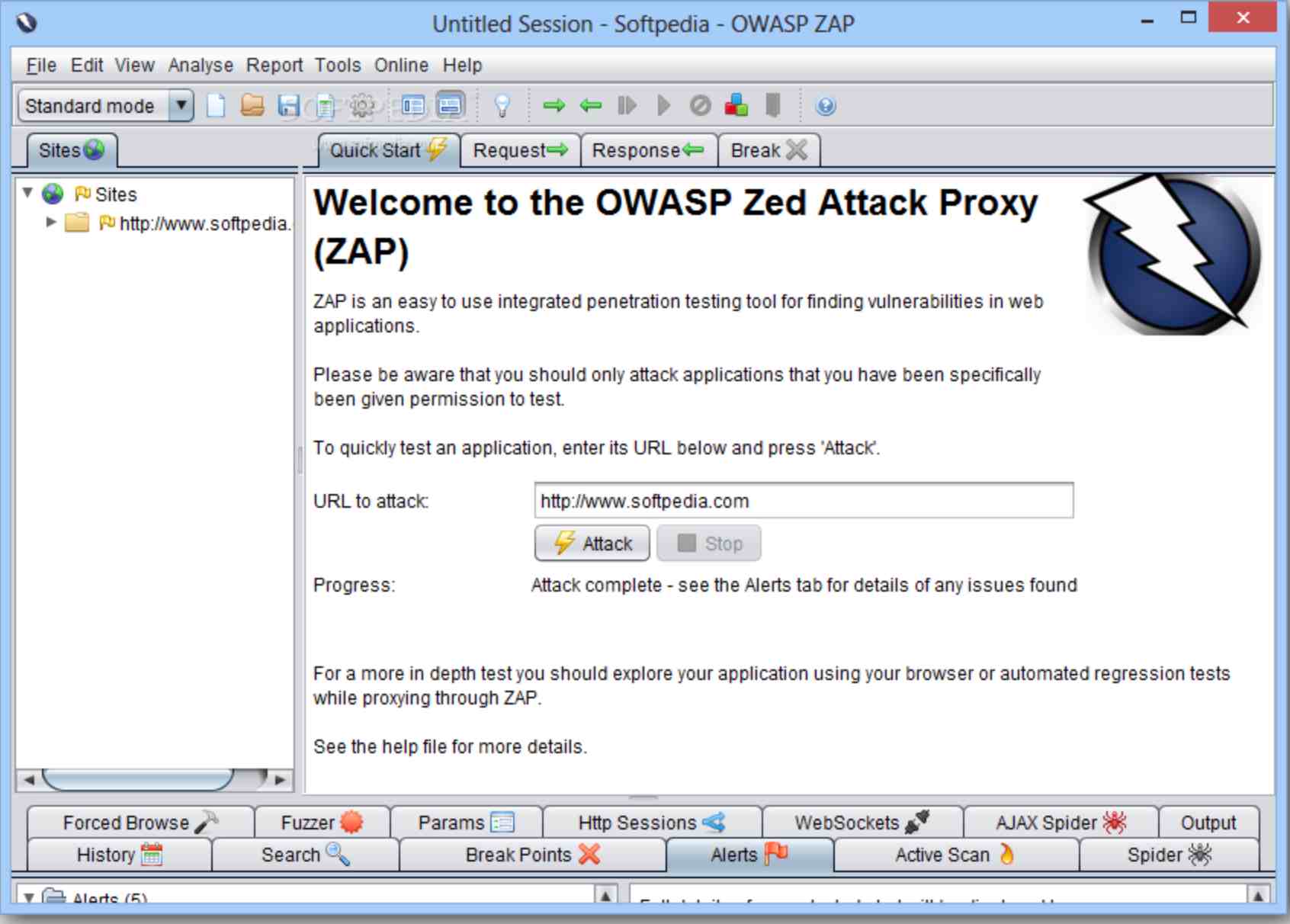
Use OWASP ZAP (Zed Attack Proxy), a free and open-source tool, to find security vulnerabilities in web applications and APIs during runtime. Leverage its capabilities for Dynamic Application Security Testing (DAST) to identify potential threats effectively. Run automated scans to detect common security issues like SQL injection and cross-site scripting (XSS). Analyze results to uncover hidden flaws and weaknesses in applications.
Postman
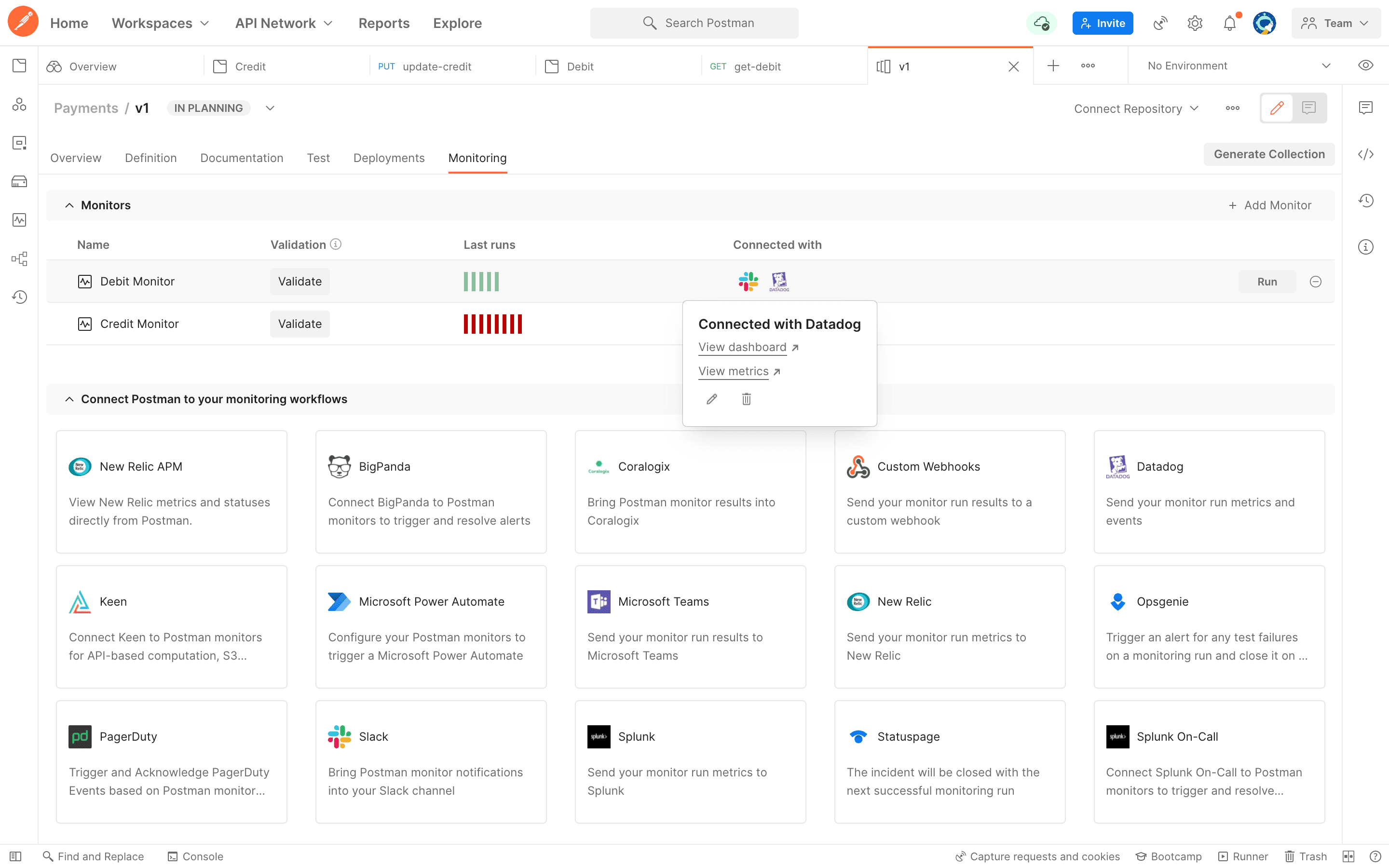
Although Postman is primarily known as a tool for developing APIs, it also has very solid testing capabilities. Security engineers can use it to set up and run automated tests to verify both the functional and security correctness of APIs.
Burp Suite
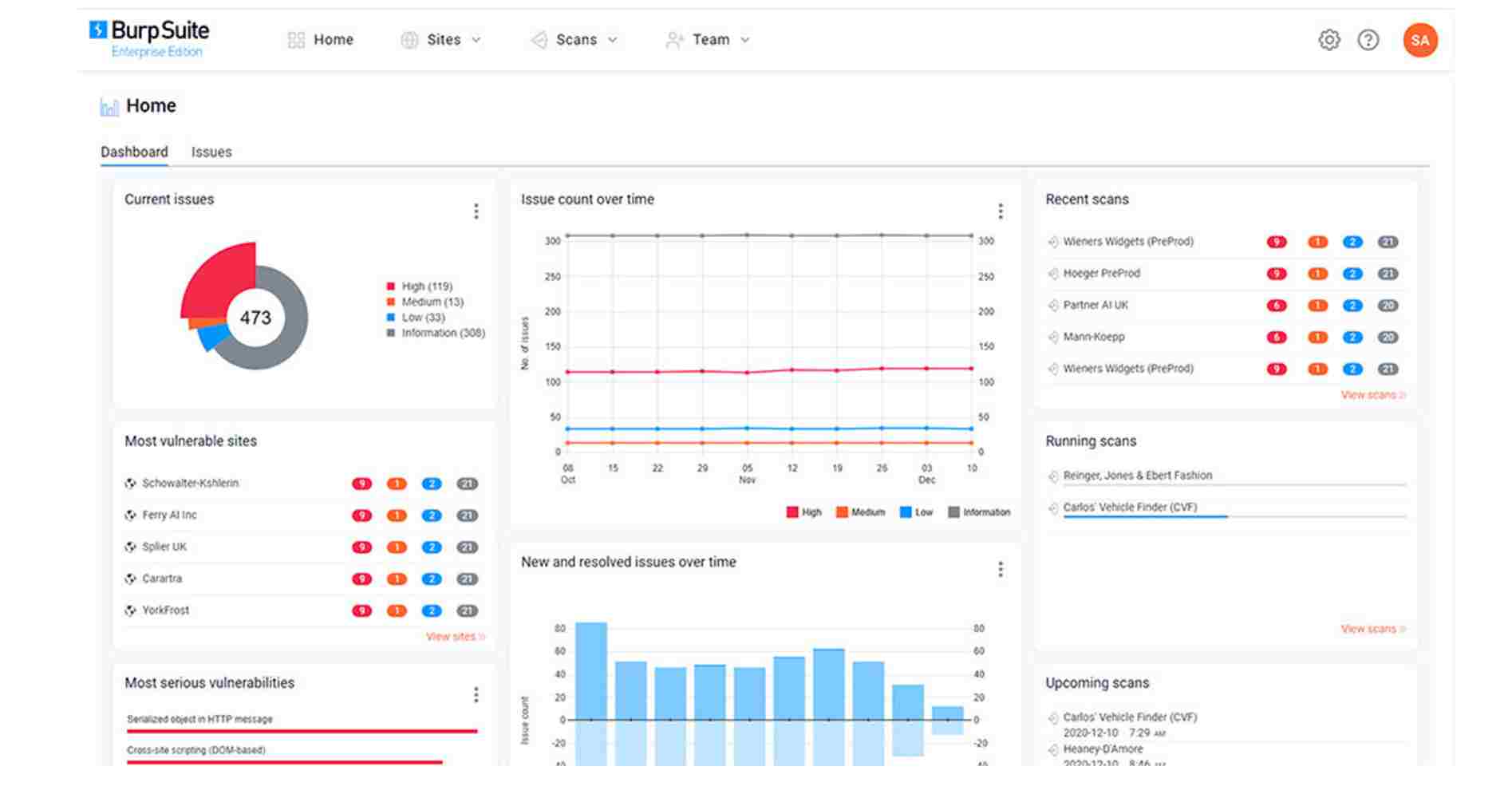
Security Engineers use a comprehensive web application security testing platform like Burp Suite for the purposes of vulnerability identification, analysis, and exploitation. It comprises an array of tools such as the Burp Scanner tool, which scans for vulnerabilities automatically with common security flaws, and the Burp Intruder tool, which tests the injection attacks and other types of complex vulnerabilities.
SoapUI
SoapUI is a popular open-source tool designed specifically for testing APIs, supporting both SOAP and REST protocols. It offers attributes for functional assessment, performance evaluation, and security evaluation, which makes it a flexible option for developers and security engineers.
With its powerful scripting capabilities and easy-to-use interface, SoapUI enables security teams to create, manage, and automate comprehensive API tests, ensuring that APIs function correctly and securely under different conditions.
Acunetix
It is a web application security scanner that offers robust capabilities for both web and API security testing. It automates the detection of vulnerabilities such as SQL injection, cross-site scripting (XSS), and other security flaws, providing detailed reports and guidance on remediation.
Akto API Security Solution
Akto offers a holistic platform designed to protect APIs throughout their lifecycle. It integrates advanced security protocols into the APIs so that they remain resilient to evolving threats.
Key Features
Automated API Discovery: Akto continuously identifies all APIs within the ecosystem, including undocumented or shadow APIs, providing a holistic view of the API landscape.
Sensitive Data Exposure Detection: This platform identifies the exposure of confidential information, including
Social Security Numbers,credit card information, and authentication tokens, thus remediates it in time.Comprehensive Security Testing: The huge test library in Akto covers vulnerabilities like the
OWASP API Top 10, authentication and authorization flaws, and business logic weaknesses, ensuring a detailed security assessment.CI/CD Integration: Akto can easily integrate into the CI/CD pipelines so that the security test happens during development. This enables early discovery and resolution of vulnerabilities.
Real-Time Monitoring and Risk Scoring: Akto monitors APIs in real time and assigns risk scores according to factors like traffic patterns and exploitability, so it allows proactive risk management.
Customizable Testing Framework: Tailor security tests to address unique vulnerabilities specific to APIs, ensuring that security measures align with the organization's requirements.
Why Choose Akto?
Trusted by modern application security teams globally, including Fortune 500 companies, Akto's platform is recognized for its precision, depth, and automation in API security.
Experience firsthand how Akto can fortify the API security posture. Request a demo today to explore the platform's capabilities and understand how it can be tailored to meet the organization's specific needs.
Final Thoughts
APIs are indispensable in today’s interconnected digital ecosystem, but their ubiquity also makes them a significant attack surface. Protecting APIs is not just about securing data but also ensuring operational continuity and maintaining user trust. By understanding API security risks and implementing best practices, organizations can proactively mitigate threats and stay ahead in an evolving security landscape.
Leveraging advanced solutions like Akto empowers organizations to secure their APIs with automated testing, real-time monitoring, and actionable insights. Organizations can safeguard their digital assets, enhance compliance, and build a robust security framework that supports innovation and growth.
Explore more from Akto
Blog
Be updated about everything related to API Security, new API vulnerabilities, industry news and product updates.
Events
Browse and register for upcoming sessions or catch up on what you missed with exclusive recordings
CVE Database
Find out everything about latest API CVE in popular products
Test Library
Discover and find tests from Akto's 100+ API Security test library. Choose your template or add a new template to start your API Security testing.
Documentation
Check out Akto's product documentation for all information related to features and how to use them.

