What is API Security Posture?

Insha
Oct 4, 2024
API Security Posture is crucial because it reflects an organization's overall ability to protect its APIs from threats and vulnerabilities. A strong security posture helps organizations identify potential risks and implement effective mitigation measures. It involves continuously assessing and improving API security practices, which allows organizations to respond swiftly to emerging threats and adapt to changing security landscapes.
Discover the importance of API security posture and learn effective strategies to protect the APIs from threats. Implement best practices and utilize essential tools to enhance API security.
What is API Security Posture?
API Security Posture refers to an organization’s overall security stance regarding its APIs, encompassing the measures, practices, and protocols in place to protect them from threats and vulnerabilities. It includes the strategies that organizations use to identify, assess, and mitigate risks associated with API usage, ensuring that sensitive data remains secure and the system prevents unauthorized access.
A strong API security posture involves regularly monitoring APIs for potential threats, implementing robust authentication and authorization mechanisms, and conducting frequent security assessments.
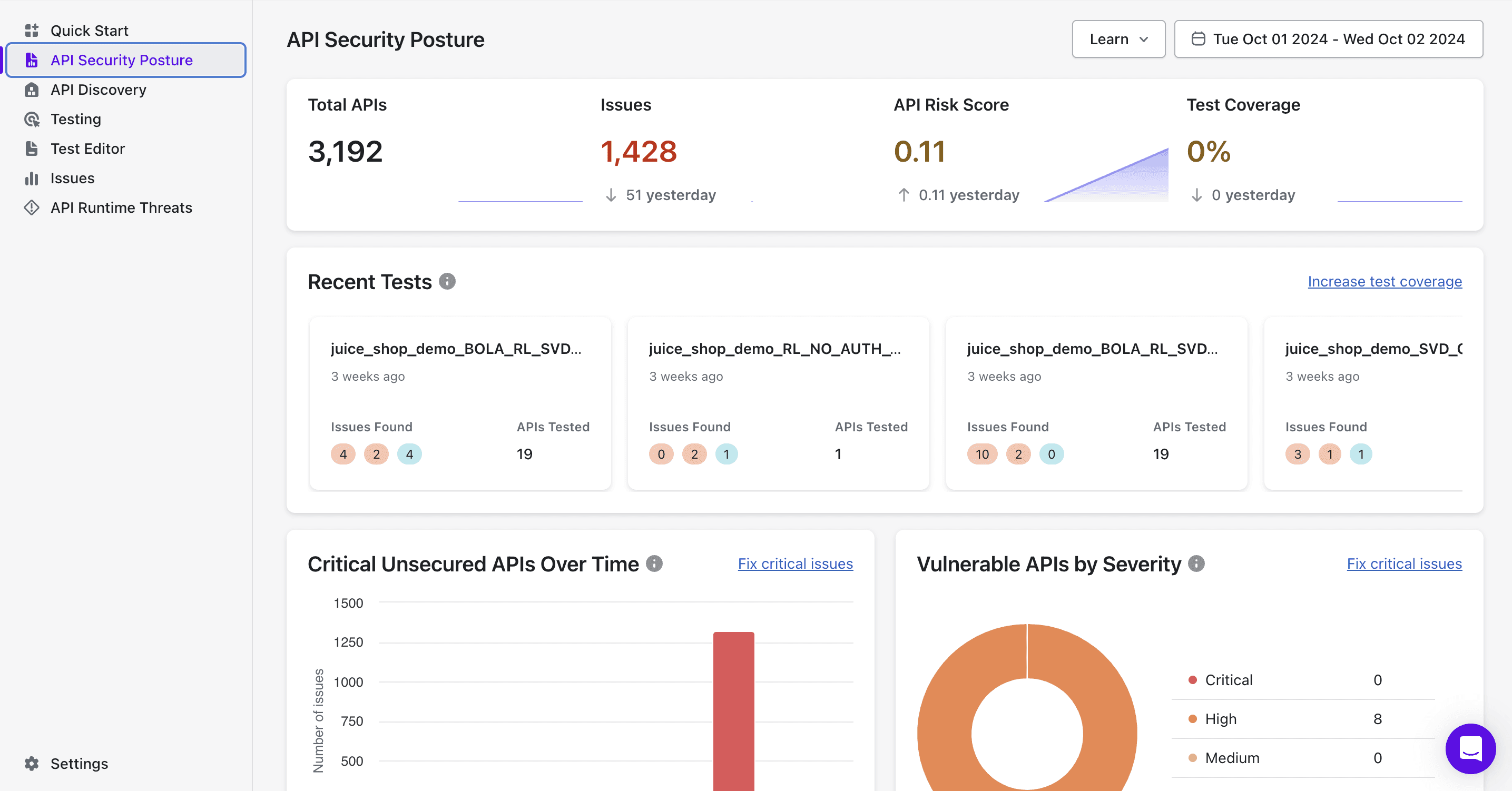
API Security Posture in Modern Applications
In today's world, many applications rely on APIs to communicate and share data, making a robust API security posture crucial. This security posture helps protect sensitive information, maintain user trust, and prevent data breaches. A well-secured API ensures that only authorized users can access data and services, significantly reducing the risk of attacks.
Moreover, as the number of APIs in use grows, so does the complexity of managing their security. Modern applications often integrate multiple third-party APIs, increasing the attack surface. Therefore, organizations must continuously assess and improve their API security practices to address emerging threats. This involves not only implementing strong authentication and authorization mechanisms but also regularly conducting security assessments and vulnerability scans.
Additionally, organizations should prioritize logging and monitoring to detect unusual activities and potential security incidents in real time. By maintaining an active security posture, organizations can quickly respond to threats, minimizing potential damage.
Key Components of API Security Posture
Essential components form the foundation of a robust API security posture, safeguarding the APIs against potential threats and vulnerabilities. These include:
Authentication and Authorization
Authentication verifies the identity of users accessing an API, while authorization checks their permissions and what actions they can perform. Both are essential for protecting APIs from unauthorized access.
Authentication involves validating user credentials through methods like username/password combinations, multi-factor authentication (MFA), and token-based systems (e.g., JWT). Strong authentication reduces the risk of unauthorized access by ensuring that only verified users can make requests.
Authorization determines the permissions granted to authenticated users. It specifies which actions they can take and what resources they can access. Common strategies include Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC), which help enforce security policies aligned with organizational needs.
OAuth for APIs
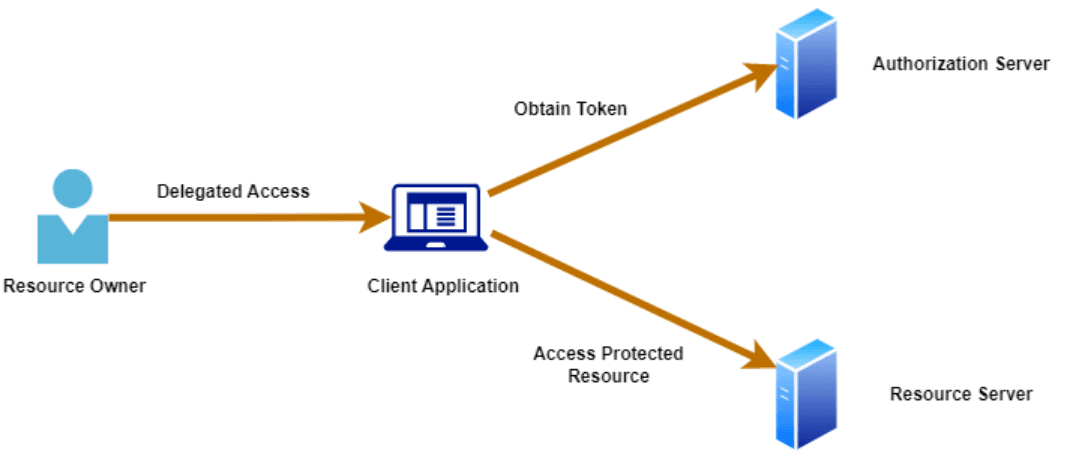
OAuth is a widely adopted protocol that enables third-party services to exchange information securely without sharing passwords. By allowing users to log into applications using their existing accounts from providers like Google, Facebook, or LinkedIn, OAuth simplifies the authentication process while ensuring security.
When a user logs into a website using a Google account, OAuth manages the authentication flow, granting limited access to specific data without exposing the credentials.
Organizations can implement OAuth to streamline user authentication and reduce the complexity of managing credentials. OAuth not only enhances user experience but also adds a layer of security by using tokens to grant access, minimizing the need for password storage.
Data Encryption
Encrypting data ensures the security of sensitive information during transmission over the internet and while storing it. By converting plain text into an unreadable format, encryption protects data from unauthorized access and interception. This process is essential for safeguarding personal information, financial data, and any sensitive content that organizations handle.
When transmitting data, such as during API calls, encryption protocols like TLS (Transport Layer Security) create a secure channel, preventing attackers from eavesdropping or tampering with the data in transit. For instance, when a user submits their credit card information online, encryption ensures that the data remains secure while traveling between the user's device and the server.
Input Validation and Sanitization
Validating and sanitizing inputs plays a critical role in protecting APIs from malicious data. When organizations implement proper input validation techniques, they ensure that only legitimate data is processed, safeguarding their systems from attacks. For example, by strictly defining the acceptable format for inputs like email addresses or user IDs, organizations prevent attackers from injecting harmful code.
Input sanitization further strengthens API security by removing or altering potentially harmful characters before processing the data. This practice shields systems from vulnerabilities such as SQL injection, where attackers attempt to manipulate databases, or cross-site scripting (XSS), where attackers inject malicious scripts into web pages. By combining both input validation and sanitization, organizations protect their APIs and maintain the integrity of their data while preventing unauthorized access or manipulation.
Rate Limiting and Throttling
Rate limiting controls the number of requests a user can make to an API, preventing abuse and ensuring fair usage among all users. By setting limits on the number of requests, organizations can protect their APIs from excessive traffic overwhelming them, which could lead to performance degradation or service outages.
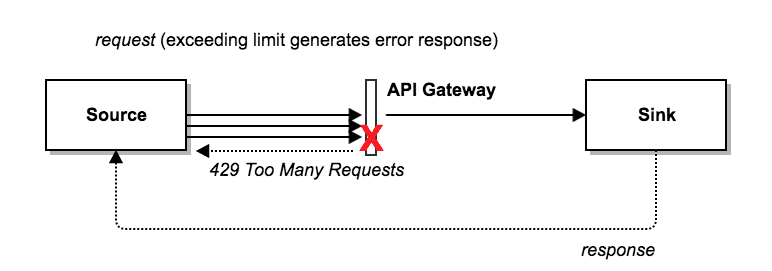
For example, allowing a maximum of 1000 requests per hour per user can significantly reduce the risk of denial-of-service (DoS) attacks, where attackers attempt to flood an API with requests to disrupt service. By enforcing such limits, organizations can maintain the integrity and availability of their APIs while ensuring that all users have fair access.
Tools like API Gateway facilitate the implementation of rate limits by providing built-in functionality to monitor and manage request rates. These tools enable organizations to define specific rules and thresholds, automatically tracking usage and blocking requests that exceed the set limits.
API Monitoring and Logging
Monitoring helps organizations track API performance, detect anomalies, and respond to potential security incidents effectively. By continuously observing API activity, security teams can identify unusual patterns, such as spikes in traffic or unexpected error rates, which may indicate security threats or performance issues.
Tools for Logging and Monitoring
Organizations can leverage various tools to enhance their API monitoring and logging efforts. For instance, Prometheus and New Relic are popular monitoring tools that provide valuable insights into API usage and performance. Prometheus collects metrics and offers powerful querying capabilities, enabling teams to visualize API performance over time. New Relic, on the other hand, provides comprehensive application performance monitoring (APM) features that help organizations understand the overall health of their APIs and identify bottlenecks.
API Security Posture Challenges
Organizations face several key challenges when striving to maintain a robust API security posture. These include:
Rapid Development Cycles
Organizations often prioritize speed during the development of new APIs, which can lead to teams overlooking security measures or allowing them to become outdated. As teams work to meet tight deadlines, they may not conduct security reviews and testing as thoroughly as needed, leaving APIs vulnerable to exploitation. To maintain security, organizations must integrate security checks into every stage of development without sacrificing speed.
Managing Third-Party APIs
Integrating third-party APIs adds value but increases the attack surface, as organizations lack control over the security practices that external providers use. If a third-party API has weak security protocols, it can expose the entire system to risk. Organizations must carefully vet third-party APIs, monitor their use, and establish strict security requirements for any external services integrated into their environment.
Complex Authentication and Authorization
Implementing consistent authentication and authorization across multiple APIs can become complicated, particularly in large systems with numerous endpoints. Each API may require different levels of access or permissions, creating opportunities for misconfigurations or vulnerabilities. Organizations must ensure that authentication and authorization mechanisms are uniform and robust across all APIs to prevent unauthorized access.
Evolving Threat Landscape
The constant evolution of cyber threats challenges organizations to keep up with new vulnerabilities and attack vectors. Hackers continually develop new tactics to exploit APIs, and organizations must regularly update their security practices and tools to stay ahead. This requires ongoing monitoring and adaptability to address emerging risks and safeguard API security.
Insufficient Logging and Monitoring
Without adequate logging and monitoring practices, organizations may struggle to detect and respond to suspicious activities. APIs that lack detailed logs can make it difficult to trace security incidents or track unauthorized access attempts. Implementing comprehensive logging and real-time monitoring is crucial to identifying and addressing potential security breaches quickly.
Compliance and Regulatory Pressure
Meeting evolving compliance requirements can complicate an organization’s efforts to maintain a strong API security posture. Regulations like GDPR, HIPAA, and PCI DSS impose strict data protection standards that require careful management of APIs. Organizations must ensure that their APIs comply with these regulations, which can be resource-intensive and add complexity to their security strategies.
API Protection Tools
Organizations use various tools to safeguard their APIs from vulnerabilities and attacks. These tools enable developers and security teams to detect, test, and secure APIs throughout development and production.
Akto API Security Platform
Akto provides an advanced API security platform designed to help organizations identify, test, and secure their APIs in real time. It enables continuous monitoring and protection of APIs, ensuring they remain secure throughout the development lifecycle.
OWASP ZAP
OWASP ZAP is an open-source security tool that actively scans APIs for vulnerabilities. It helps developers and security engineers identify security issues in the organization’s applications during the development process.
Postman
Postman not only facilitates API testing but also includes security features that allow security teams to perform security testing and validate API responses against expected security standards.
API Fortress
API Fortress provides a comprehensive platform for API testing and monitoring. It enables security teams to automate security tests and integrate them into their CI/CD pipelines, ensuring that APIs remain secure throughout the development lifecycle.
Burp Suite
Burp Suite is a widely used security testing tool that actively tests APIs for vulnerabilities. It offers features like web vulnerability scanning and manual testing tools to help security professionals assess API security effectively.
Salt Security
Salt Security focuses on runtime API protection by using machine learning to detect and block attacks in real-time. It continuously monitors API traffic to identify suspicious behavior and helps organizations respond swiftly to potential threats.
API Security Posture Best Practices
Implement these essential best practices to fortify your API security posture and protect your digital assets from potential threats.
Strong Authentication Mechanisms
To protect the APIs, use strong methods to verify user identities. One effective method is Multi-Factor Authentication (MFA). With MFA, users must provide two or more verification factors to access their accounts. For example, they might need to enter a password and a code sent to their phone. This adds an extra layer of security to enter a password and then a code sent to their phone. This adds an extra layer of security.
Least Privilege Principle
The least privilege principle requires limiting user access to only what is necessary for their role or task. By carefully managing access control and permissions, organizations reduce the risk of unauthorized actions.
For instance, if a user only needs to read data, assign read-only access and avoid granting write or delete permissions. Implementing this principle minimizes the potential for accidental errors or malicious actions that could compromise system security or integrity. Regularly review and adjust permissions to ensure users maintain only the access they need, further strengthening the organization's security posture.
Secure API Endpoints
Protect the API endpoints by using API gateways. An API gateway serves as a gatekeeper, controlling traffic to and from the APIs. It effectively manages requests, allowing only authorized users to access the services. By enforcing security policies, the gateway helps prevent unauthorized access and mitigates potential threats.
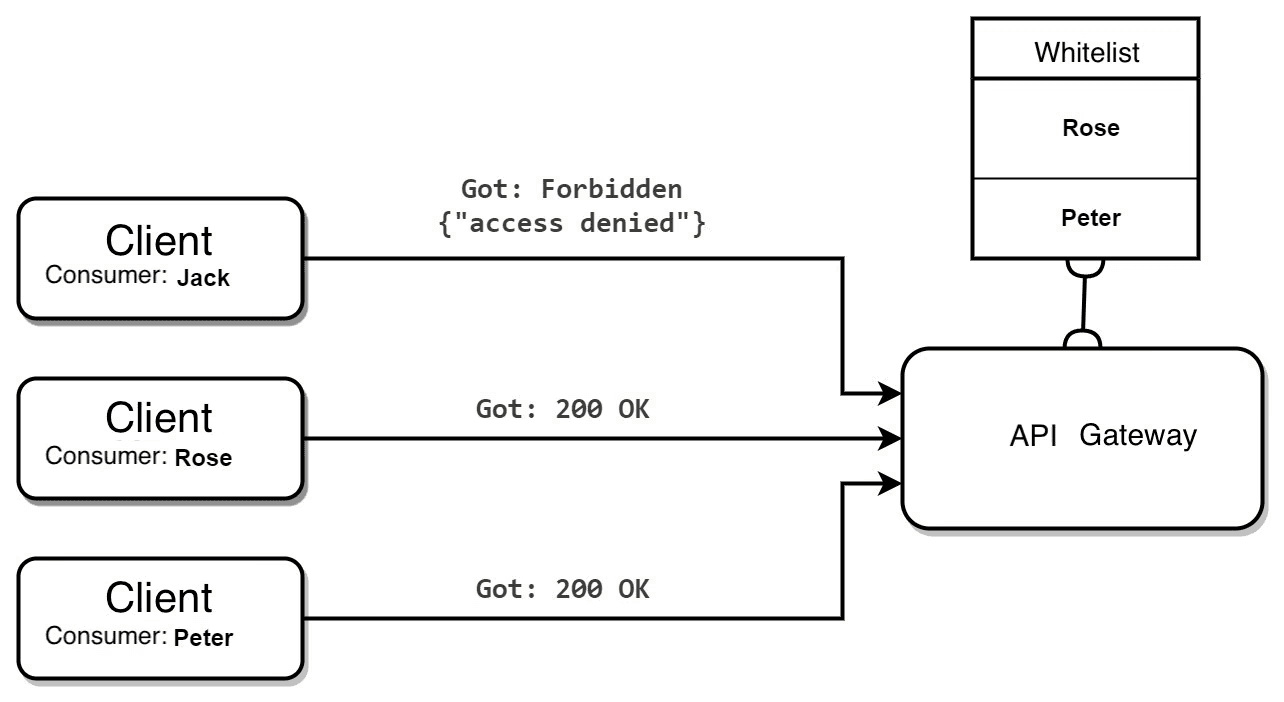
API gateways can also authenticate requests, ensuring that only legitimate users can interact with the APIs. This authentication process often includes verifying API keys, tokens, or credentials, adding an essential layer of security. Additionally, the gateway can handle rate limiting, preventing abuse by controlling the number of requests from individual users and maintaining overall API performance.
Security Audits and Testing
Conduct regular security audits and penetration tests to identify and fix vulnerabilities in the APIs. Security audits involve a comprehensive review of the organization’s security practices, policies, and controls to ensure they meet industry standards. During these audits, security teams evaluate authentication mechanisms, data encryption methods, and access controls to ensure they effectively protect sensitive information.
Penetration testing complements security audits by simulating real-world attacks on the APIs. Security engineers attempt to exploit vulnerabilities, revealing weaknesses that could be targeted by malicious actors. This proactive approach allows organizations to address security gaps before they can be exploited, ultimately strengthening the overall security posture.
Automate Security with DevSecOps
Integrate security into the organization development process with DevSecOps by embedding security practices directly into the Continuous Integration/Continuous Deployment (CI/CD) pipelines. By automating security checks such as code analysis and vulnerability scanning during development, security teams can catch issues early, reducing the likelihood of security vulnerabilities making it to production.
In a DevSecOps approach, security teams implement security tools that automatically analyze code for potential vulnerabilities as developers write it. This proactive measure helps identify insecure coding practices or dependencies that may pose risks. Additionally, incorporating automated vulnerability scanning allows teams to assess the security of third-party libraries and components, ensuring they meet security standards before deployment.
Final Thoughts
By adopting the strategies and tools outlined in this blog, organizations can greatly improve their API security posture. These measures will protect valuable digital assets, ensure compliance, and maintain customer trust. Staying proactive helps mitigate risks in today’s evolving digital landscape.
Akto provides a comprehensive API security platform with real-time monitoring and automated testing to safeguard the APIs. Enhance the organization’s security efforts with Akto’s seamless integration into the workflows. Akto Book demo today to take the first step toward robust API protection.
Explore more from Akto
Blog
Be updated about everything related to API Security, new API vulnerabilities, industry news and product updates.
Events
Browse and register for upcoming sessions or catch up on what you missed with exclusive recordings
CVE Database
Find out everything about latest API CVE in popular products
Test Library
Discover and find tests from Akto's 100+ API Security test library. Choose your template or add a new template to start your API Security testing.
Documentation
Check out Akto's product documentation for all information related to features and how to use them.