What is a Shadow API?

Insha
Oct 8, 2024
Shadow APIs pose a significant risk to organizations by operating outside of the normal security and monitoring processes. These undocumented APIs often go unnoticed, creating potential entry points for attackers to exploit. Failing to account for shadow APIs can lead to data breaches, unauthorized access, and compliance issues. Organizations must actively discover and manage these hidden APIs to ensure they are secure, properly documented, and monitored, protecting the overall integrity of the API ecosystem.
This blog provides a comprehensive understanding of Shadow APIs, their risks, and their identification.
What is a Shadow API?
A Shadow API is an undocumented or unknown API endpoint that exists within an organization’s system. Developers often create these APIs during rapid development or testing but do not track or manage them properly. Because they operate outside of standard security and monitoring practices, shadow APIs can expose the organization to security vulnerabilities, data breaches, and compliance risks. Detecting and managing shadow APIs is essential to maintaining a secure API environment.
Risks of Shadow APIs
Shadow APIs pose significant risks to organizations, threatening data security, system integrity, and regulatory compliance. Let's explore the key risks associated with these hidden endpoints:
Unauthorized Access
Attackers can find and exploit undocumented endpoints like /beta/user-data to gain unauthorized access to sensitive information. Without authentication or authorization checks, these endpoints offer a direct entry point to the data, putting user privacy and security at risk.
Lack of Monitoring
When security teams do not document an API, they also fail to monitor it. This lack of visibility means that any malicious activity targeting the shadow API could go unnoticed for a long time, allowing attackers to remain undetected while they exfiltrate data or escalate privileges.
Security Vulnerabilities
Shadow APIs often lack the security measures found in documented APIs. Developers may omit essential protections, such as encryption, input validation, or rate limiting. As a result, these endpoints are more likely to have vulnerabilities like SQL injection, cross-site scripting (XSS), or insecure direct object references (IDOR).
Compliance Risks
Because shadow APIs are unknown, they may not comply with regulatory requirements like GDPR, CCPA, or HIPAA. Organizations risk facing legal penalties, fines, or reputational damage if a breach involving an undocumented API exposes sensitive data.
Data Exposure
Without proper logging and auditing, shadow APIs can inadvertently expose sensitive data, such as personal information, financial records, or confidential business details. This exposure increases the risk of data leaks, which can damage customer trust and the organization’s reputation.
Operational Impact
Shadow APIs can introduce unexpected behavior in applications, leading to potential outages or performance issues. When developers or system engineers are unaware of these APIs, they cannot optimize or maintain them effectively, which can cause reliability problems.
Shadow API vs Zombie API
Let's explore the key differences between Shadow APIs and Zombie APIs to understand their unique characteristics and potential risks.

How to Identify Shadow APIs
This is how your organization can identify shadow APIs using automated tools, monitoring, and regular audits:
Automated API Discovery Tools
API Security Platforms: Deploy tools like Akto to detect and monitor APIs in real-time. These platforms automatically scan the network to identify all active APIs, including undocumented ones, and they provide continuous oversight to prevent shadow APIs from slipping through the cracks.
API Discovery from Code: Akto has introduced Automated API Discovery from source code to help modern AppSec teams and developers automatically find and inventory APIs directly from their codebase. This feature aims to improve security in the DevSecOps pipeline by providing a more comprehensive way to discover APIs.
Network Scanners: Use network scanners to examine all communication between services. These tools can reveal hidden APIs by identifying traffic patterns that don’t match the documented API inventory.
Monitoring and Logging
Traffic Analysis: Regularly analyze network traffic logs to identify unexpected endpoints or patterns that could indicate the presence of hidden APIs. This helps organizations detect unauthorized activity and to secure their API environment.
Usage Analytics: Implement analytics tools to monitor API usage closely. Look for unusual activity, such as spikes in traffic or requests from unknown sources, which may point to shadow APIs that need attention.
Regular Audits
Security Audits: Conduct regular security audits to review all active APIs and cross-check them against the documented inventory. This helps an organization identify any APIs that might be missing from the records and require further investigation.
Code Reviews: Perform thorough code reviews to catch APIs that developers may have created without following proper documentation or security protocols. This proactive approach helps organizations uncover shadow APIs early in the development cycle.
Employee Feedback
Developer Input: Encourage open communication with developers and team members to identify APIs that may have been created without following formal processes. Regular check-ins can help discover shadow APIs that might otherwise go unnoticed.
Surveys: Distribute surveys to your development teams to ask directly about any undocumented APIs they might know of. This method can provide valuable insights into hidden APIs and promote a culture of transparency.
Cross-Referencing
Inventory Comparison: Regularly compare the internal API inventory against external sources, such as
API gateways, proxies, and third-party services, to ensure all APIs are accounted for. Cross-referencing helps catch discrepancies and uncover hidden APIs that may have been missed during initial documentation.
Shadow API Example
Imagine a development team working on a new feature for a web application that requires access to user data. To test this feature quickly, a developer creates an API endpoint like /beta/user-data to fetch user information. The developer intends this endpoint only for internal testing purposes, so they don't add it to the official API documentation or implement full security measures, assuming they will remove or secure it before deployment.
However, in a rush to meet deadlines, the team mistakenly pushes the endpoint to the production environment along with other updates. Because the endpoint is undocumented and unknown to the rest of the team, it bypasses standard security checks, monitoring, and governance controls. The security team remains unaware of its existence and fails to perform regular security assessments, logging, or auditing on it.
Meanwhile, the /beta/user-data endpoint remains publicly accessible. Since the endpoint lacks proper security controls, such as authentication and authorization checks, attackers scanning for unprotected or hidden APIs find it an easy target. Malicious actors could exploit this endpoint to access or steal sensitive user data, which could lead to a significant data breach.
This scenario demonstrates how organizations create Shadow APIs: developers build them without proper oversight, fail to track them, and allow them to bypass standard security processes.
How to Prevent Shadow APIs
Preventing shadow APIs is vital for securing the API ecosystem and ensuring operational efficiency. Implementing these strategies protects the organization from risks associated with undocumented APIs and maintains robust security practices.
1. Maintain a Comprehensive API Inventory
Why: Keep track of all APIs to ensure nothing is left undocumented or unmanaged.
How: Regularly update the inventory with new APIs and remove
deprecated ones. Make it a routine to audit and verify the inventory against actual deployments to catch any discrepancies early.
2. Enforce Documentation Practices
Why: Guarantee that every API is properly documented and secured before it goes live.
How: Make documentation a mandatory step in the API development process. Establish guidelines requiring developers to document all endpoints, parameters, data types, and security measures before deployment. Incorporate these practices into the
CI/CD pipelineto enforce compliance.
3. Implement Role-Based Access Control (RBAC)
Why: Limit who can create, modify, or delete APIs, reducing the chance of unauthorized API creation.
How: Assign roles and permissions within the API management tools. Ensure that only authorized team members can create or modify APIs and require approvals for significant changes. Regularly review access controls to keep them up to date with current team roles and responsibilities.
4. Monitor API Traffic
Why: Detect hidden APIs and unusual activity patterns that could indicate security risks.
How: Deploy monitoring tools to track API usage,
analyze traffic patterns, and flag anomalies. Set up alerts for unusual behaviors, such as high traffic volumes on undocumented endpoints or requests from unknown sources, to quickly identify potential shadow APIs.
5. Foster a Culture of API Governance
Why: Encourage developers to follow best practices for API management and security.
How: Educate teams on the importance of API documentation and governance. Conduct regular training sessions, share guidelines, and promote a culture where developers feel responsible for maintaining secure and well-documented APIs.
6. Use API Gateways and Proxies
Why: Control and monitor API traffic centrally, reducing the risk of shadow APIs.
How: Implement API gateways or proxies that manage all incoming and outgoing API traffic. These tools can enforce policies, monitor usage, and block unauthorized endpoints, helping to identify and eliminate shadow APIs.
How does Akto Detect Shadow APIs?
Akto provides a powerful and efficient method for detecting Shadow APIs in the organization’s system. Its automated process simplifies the identification of these hidden endpoints, enhancing API security. Let's walk through the steps to use Akto for Shadow API detection:
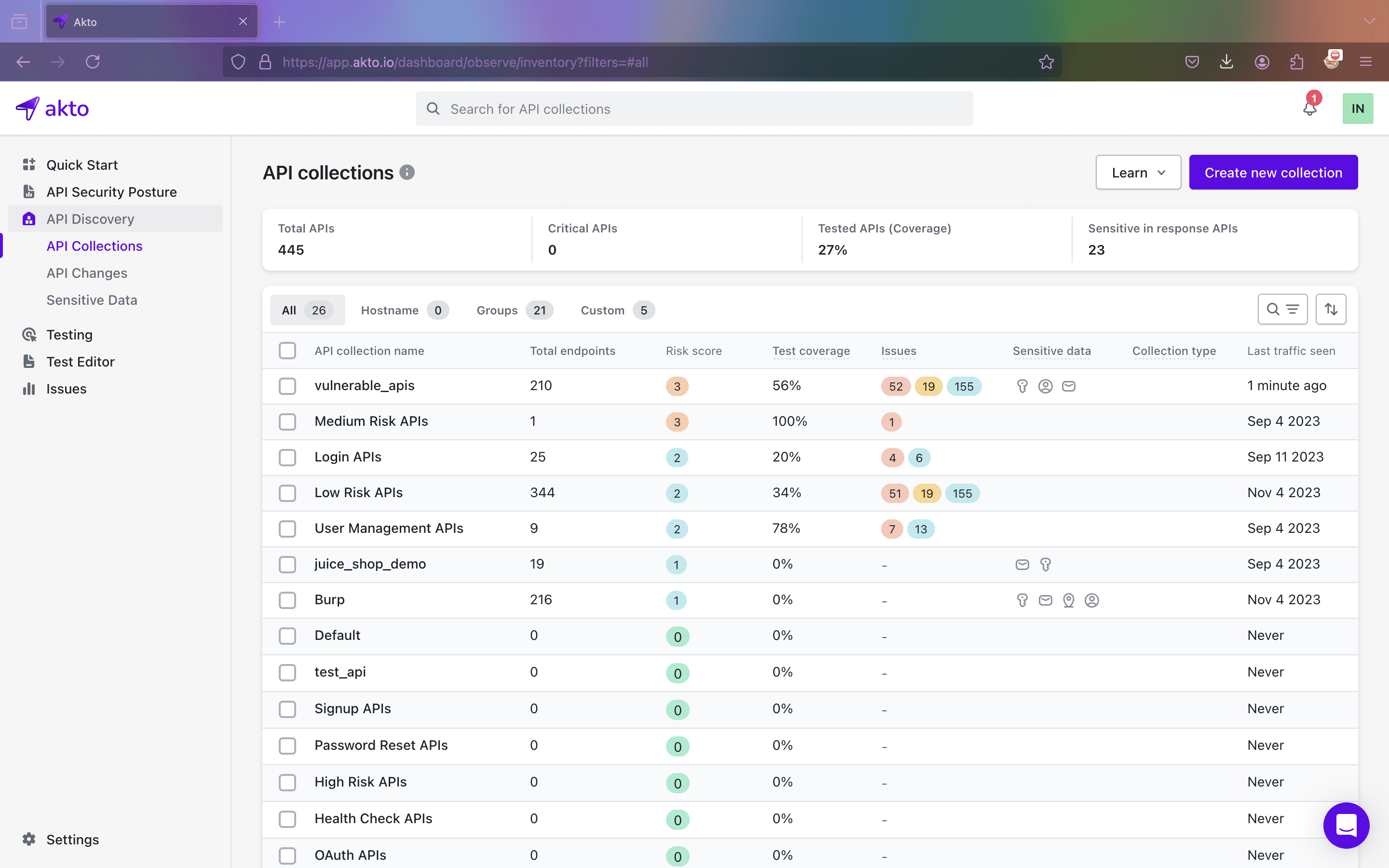
Step 1: Go to the API Collection and select the collection where you wish to find shadow APIs.
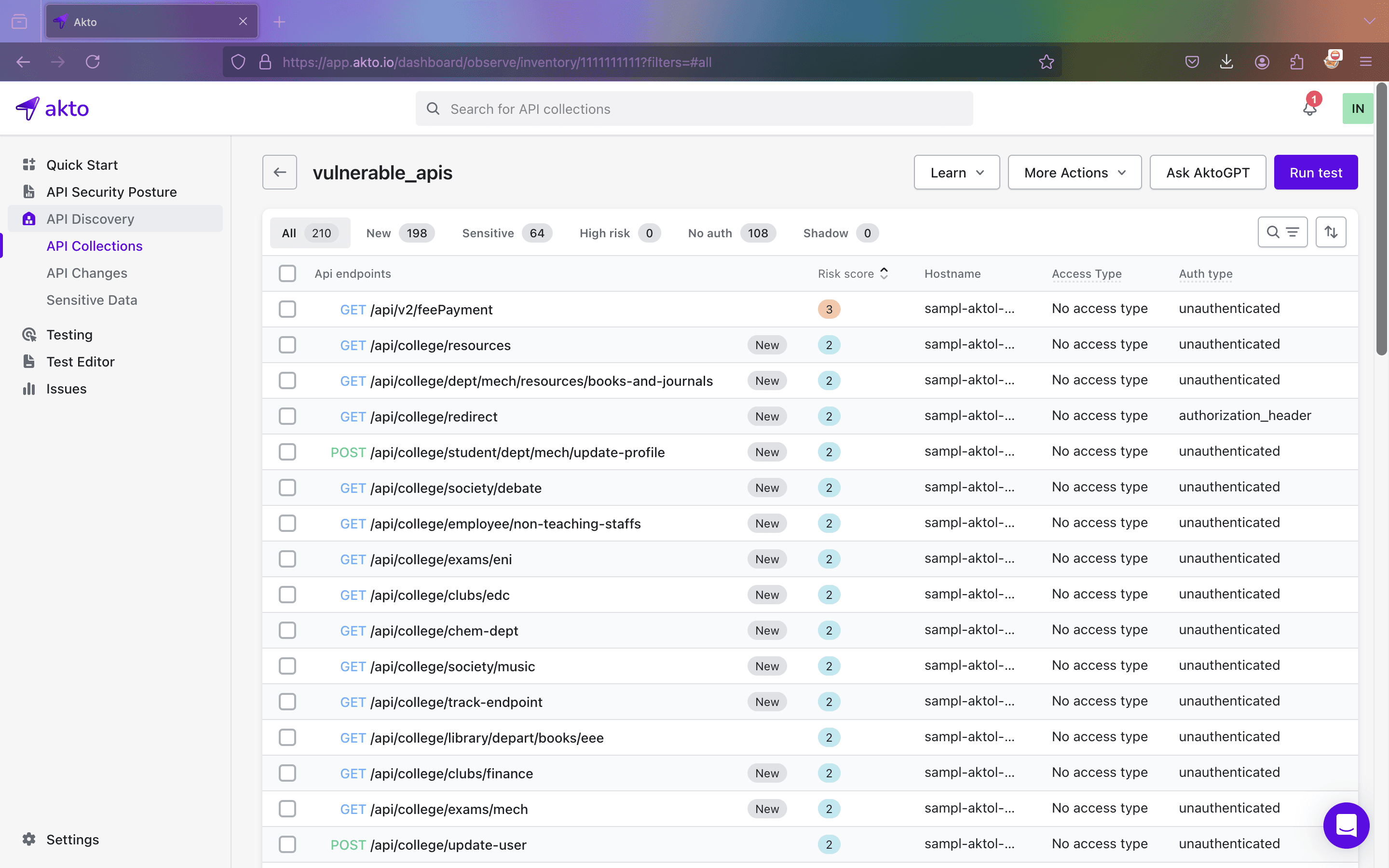
Step 2: Manually select the API endpoints you want to test or leave them as they are, and then click on “Run Test”.
Step 3: By default, all the tests will be selected; click on “Remove All”.
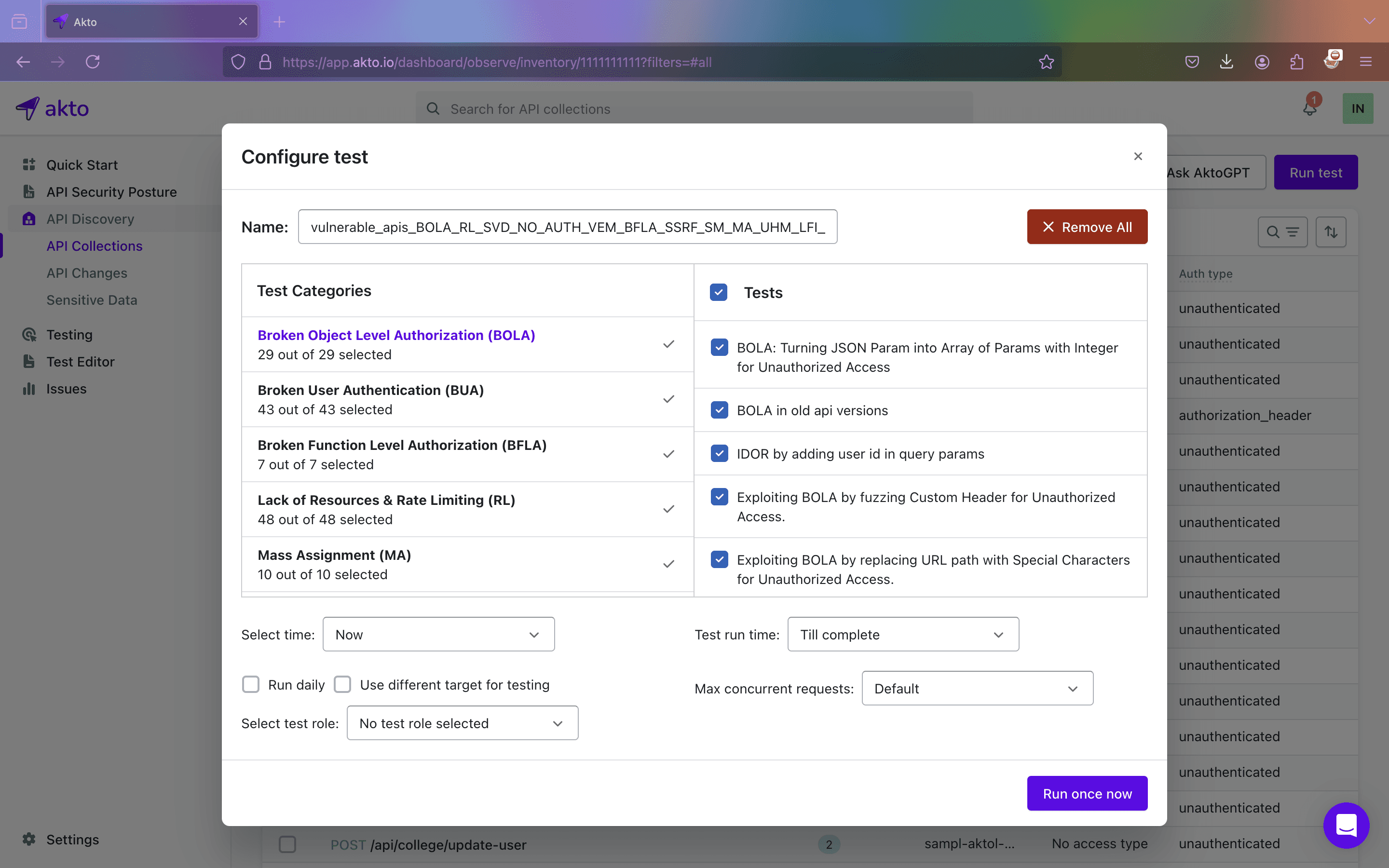
Step 4: Only select the “BOLA in old API versions.”
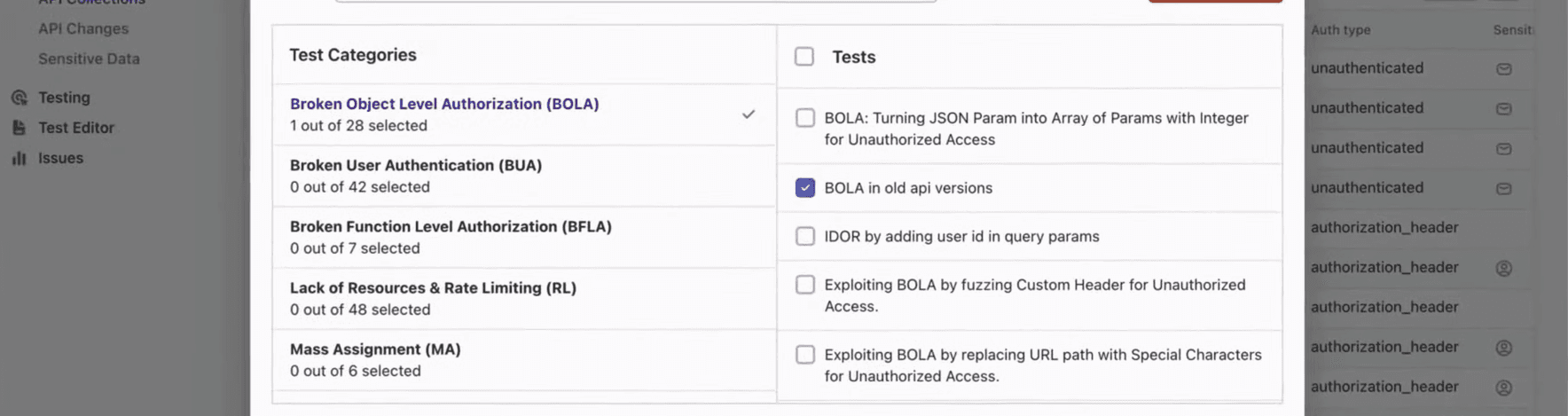
Step 5: After that, click on "Run Once Now".
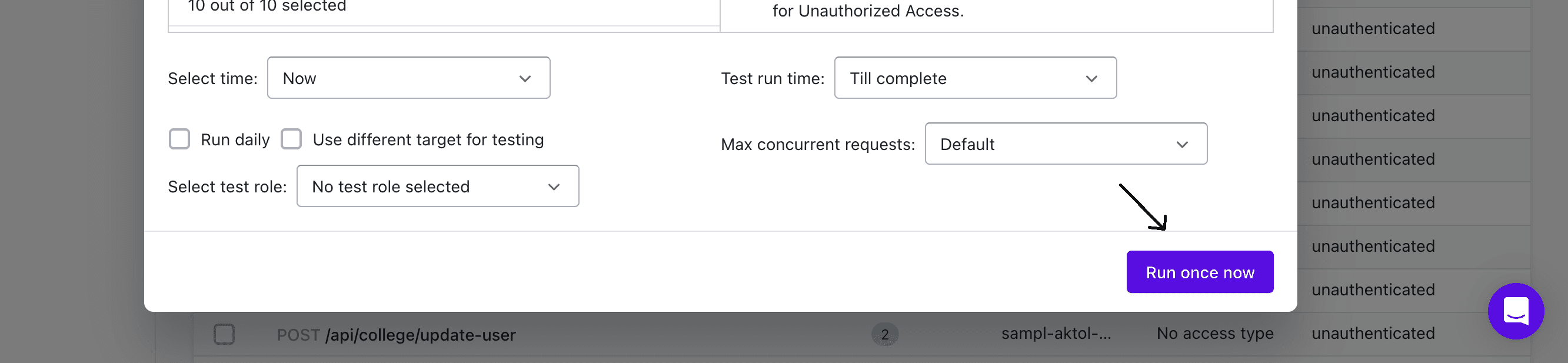
Step 6: Proceed to "Testing" to view the results. Once all the tests are complete, return to the API collection.
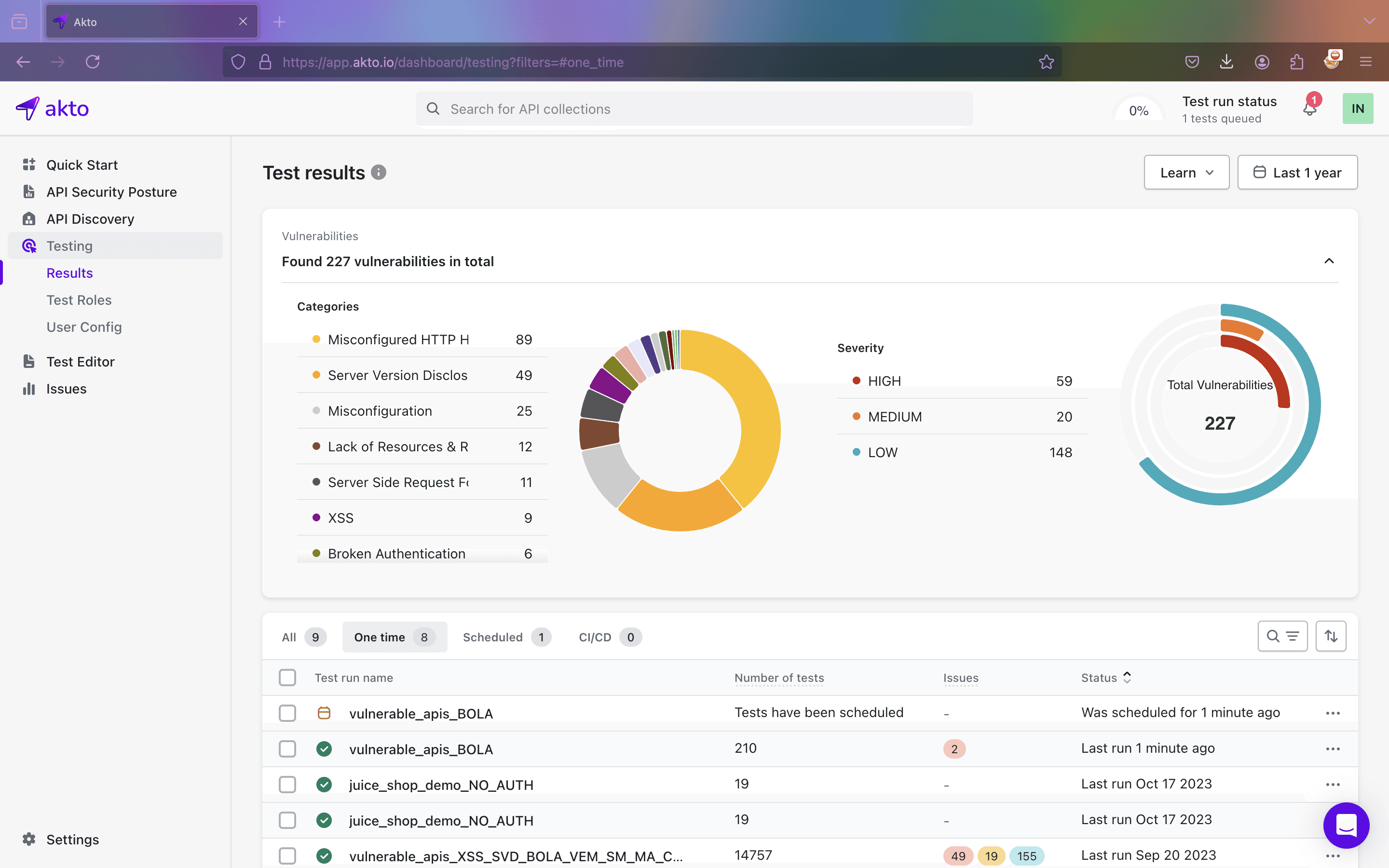
At this point, you should see a new API collection named "shadow_apis".
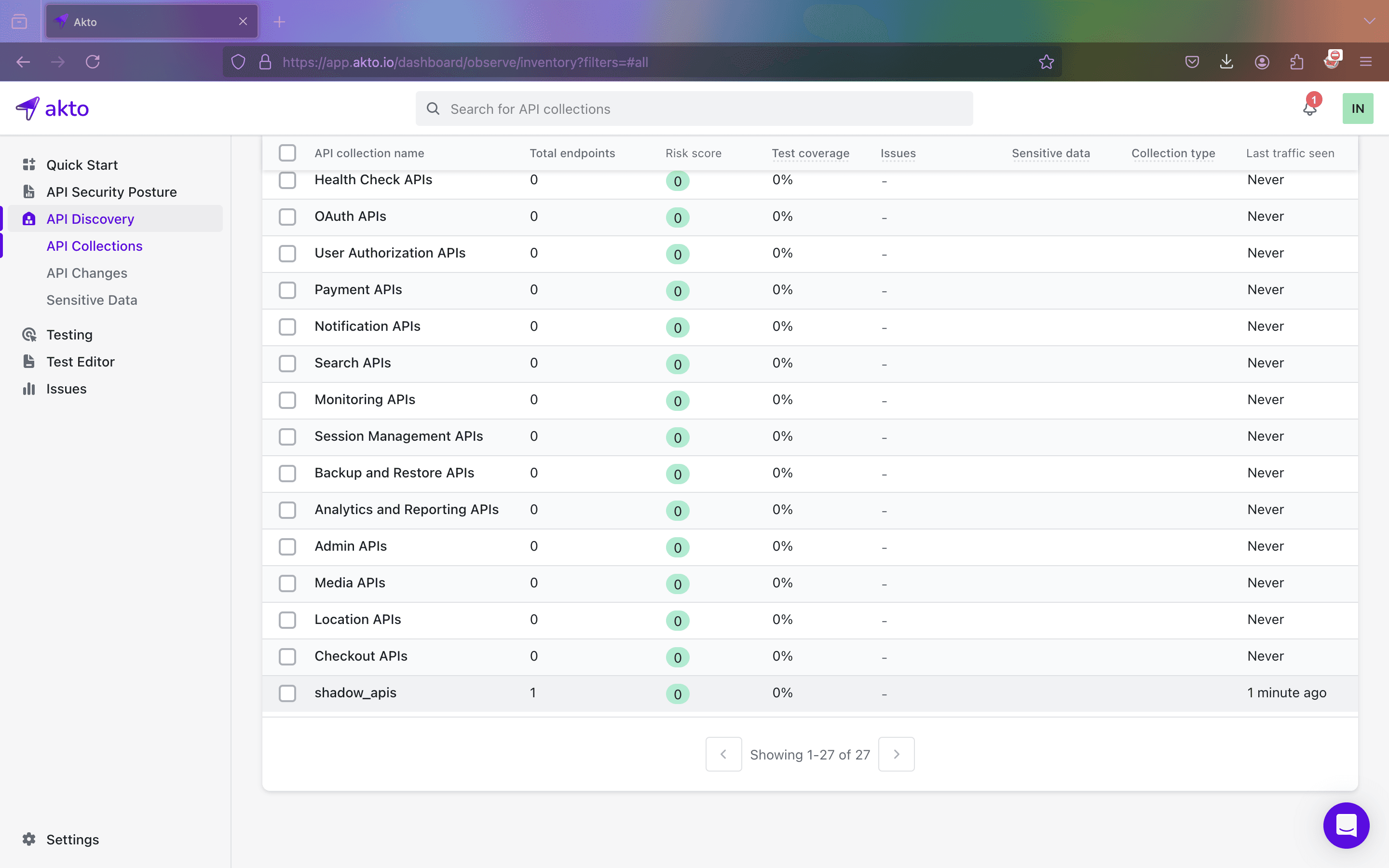
Here, you'll find a shadow API. To test it for vulnerabilities, click on "Run Test" to identify potential weaknesses in the discovered Shadow APIs.
Final Thoughts
Shadow APIs pose serious risks by operating outside standard security measures, leaving organizations vulnerable to unauthorized access, data breaches, and compliance violations. Organizations must maintain a complete API inventory, enforce strict documentation, and monitor API traffic regularly to mitigate these risks.
They should use automated discovery tools, implement role-based access control, and deploy API gateways to further secure the API environment. Cultivating a culture of API governance and conducting routine audits helps identify and manage hidden APIs, protecting both operational integrity and data security.
Explore more from Akto
Blog
Be updated about everything related to API Security, new API vulnerabilities, industry news and product updates.
Events
Browse and register for upcoming sessions or catch up on what you missed with exclusive recordings
CVE Database
Find out everything about latest API CVE in popular products
Test Library
Discover and find tests from Akto's 100+ API Security test library. Choose your template or add a new template to start your API Security testing.
Documentation
Check out Akto's product documentation for all information related to features and how to use them.