What are Business Logic Vulnerabilities?

Insha
Oct 8, 2024
Business logic vulnerabilities occur when attackers exploit the intended functionality of an application to achieve malicious outcomes. Flaws in the design or implementation of an application's business rules and workflows, rather than coding errors or technical security weaknesses, cause these vulnerabilities to arise.
This blog explores business logic vulnerabilities—weaknesses that attackers exploit by manipulating an application's intended functions. Learn how to identify these threats and implement strong safeguards to protect the application's core business processes.
What are Business Logic Vulnerabilities?
Business logic vulnerabilities emerge when an application fails to enforce the intended rules and processes, creating gaps that attackers can exploit. These gaps might allow unauthorized actions, such as bypassing payment steps, modifying order quantities without limits, or applying discounts incorrectly. For instance, if a user can add an item to their cart and manipulate the checkout flow to get it for free or at a drastically reduced price, the application has a business logic flaw.
These vulnerabilities often result from poor design decisions, inadequate testing, or misunderstandings about how the application should handle specific scenarios. Unlike technical vulnerabilities like SQL injection or XSS, which exploit coding errors, business logic vulnerabilities target the fundamental way an application operates.
Impact of Business Logic Vulnerabilities
Business logic vulnerabilities can have serious consequences for organizations. When attackers exploit these weaknesses, they can gain unauthorized access to sensitive data or perform actions that disrupt normal operations. For example, they might manipulate processes to bypass payment systems, allowing them to obtain products or services without paying.
These vulnerabilities can also lead to financial losses. If attackers exploit a flaw to steal money or resources, the organization may face significant costs to recover. Additionally, a breach of sensitive information can damage an organization’s reputation, causing customers to lose trust and potentially leading to a decline in business.
Moreover, business logic vulnerabilities can create compliance issues. Organizations must adhere to various regulations regarding data protection and security. Failing to address these vulnerabilities could result in legal penalties and fines, further harming the organization’s financial standing.
Types of Business Logic Vulnerabilities
Business logic vulnerabilities come in various forms, each exploiting different aspects of an application's intended functionality. Let's explore the main types of these vulnerabilities:
1. Insufficient Validation
When developers and security engineers do not adequately check that the user input is valid or not, the application becomes vulnerable to processing invalid or malicious data. This lack of proper validation can cause unexpected behavior, such as allowing a user to place an order with negative quantities, apply incorrect discounts, or input data that breaks the normal operation flow. For example, a form may accept a quantity of "-10" for an item, resulting in a refund or payout instead of a purchase.
Insufficient validation also opens the door for more severe attacks, such as injecting code or manipulating data to access unauthorized areas or perform unintended actions.
Example of Vulnerability
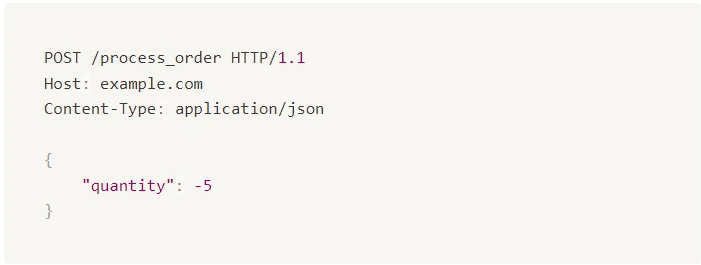
In this example (JSON), the HTTP request sends a POST request to the /process_order endpoint on the server example.com. The request includes a Content-Type header specifying that the data is in JSON format. The body of the request contains a JSON object with a key-value pair where the key is "quantity" and the value is -5.
The vulnerability here is that the system does not properly validate the quantity field. The request allows a negative number (-5) for quantity, which should not be possible when processing an order. To prevent this vulnerability, the system must validate the quantity to ensure it is a positive number before processing the order.
2. Process Manipulation
Attackers can manipulate the sequence of steps in a business process to bypass critical parts of the workflow. For example, a user might alter the checkout flow on an e-commerce site to skip the payment step, allowing them to complete a purchase without actually paying.
This type of vulnerability occurs when the application does not enforce the correct order of operations or fails to validate that users have completed each step properly before moving on to the next.
By exploiting these weaknesses, attackers can gain unauthorized access, complete actions that should be restricted, or disrupt normal business operations.
Example of Process Manipulation
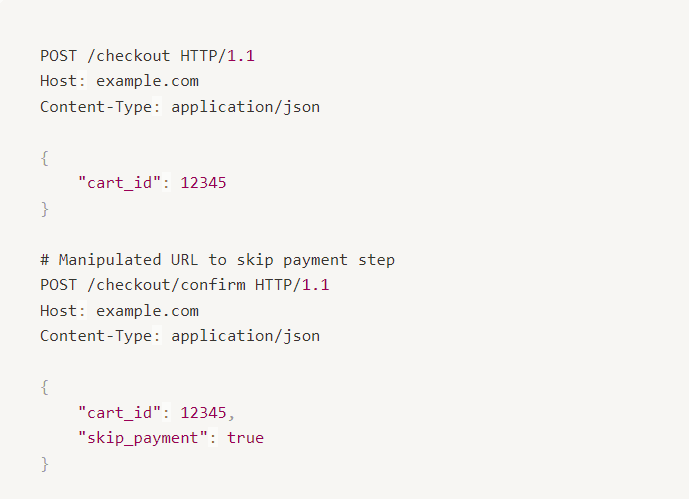
In the process manipulation example(JSON), the attacker first sends a POST request to the /checkout endpoint with a cart_id, initiating the checkout process. This request triggers the standard steps that complete a checkout, such as processing payment and handling shipping details.
However, in a manipulated request, the user directly sends a second POST request to the /checkout/confirm endpoint, attempting to bypass the necessary payment step. This manipulation disrupts the intended workflow, allowing the user to potentially complete the transaction without paying.
3. Authorization Flaws
Authorization flaws happen when the system does not properly check user permissions, allowing users to access functions or data they shouldn't. For example, a user might gain access to admin features without proper authorization, leading to potential security breaches.
These flaws occur when the application fails to verify whether a user has the right level of access before allowing them to perform certain actions or view restricted information. Attackers can exploit these weaknesses to perform actions that should be limited to privileged users, such as modifying data, changing settings, or accessing sensitive information.
Example of Authorization Flaws
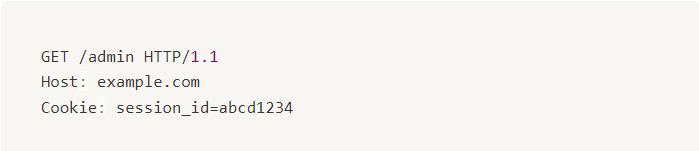
A regular user sends a GET request to the /admin endpoint in an attempt to access the admin panel. The request includes a session cookie (session_id=abcd1234), which likely belongs to a standard user account.
4. Business Rule Bypass
Users can exploit weaknesses in the application to bypass critical business rules that should be enforced. For instance, they may find a way to access premium content without having a valid subscription. This could happen if the application does not properly check user permissions or fails to validate subscription status before granting access.
Example of Business Rule Bypass
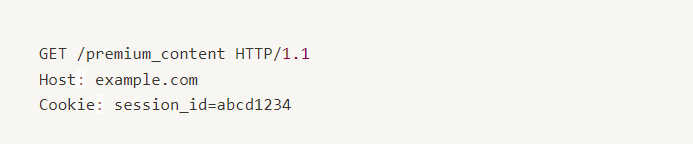
A non-subscribed user sends a GET request to the /premium_content endpoint, trying to access content meant for subscribers only. The request includes a session cookie (session_id=abcd1234), which likely belongs to a user without the necessary subscription or authorization to view the premium content.
Identifying Business Logic Vulnerabilities
Identifying business logic vulnerabilities involves systematically checking if an application correctly enforces its intended business processes and rules.
1. Understand the Business Process
Security engineers should thoroughly understand the business process that the application supports. This involves examining the workflow, rules, and constraints associated with the process. Begin by reviewing all available documentation, such as business requirements, user manuals, and design documents.
2. Identify Critical Business Logic
Identify where the team implements business logic, as these areas are most likely to contain business logic vulnerabilities. Begin by listing key functionalities, such as user registration, payment processing, and order management. Next, identify the specific rules and constraints for each functionality, including price calculations, input validations, and workflow sequences.
3. Create Test Cases
Develop test cases that cover all aspects of business logic, including edge cases and potential misuse scenarios. Start by writing test cases for normal, expected use. Next, create test cases for edge scenarios, such as extreme values or unusual sequences. Finally, design test cases for potential abuse, including attempts to bypass steps or input invalid data.
4. Perform Manual Testing
Manually test the application by following the organization’s test cases, paying close attention to how the application handles different scenarios. Execute each test case manually and document the results. Observe the application for any unexpected behavior, such as errors, crashes, or skipped steps. Record any deviations from the expected behavior.
5. Use Automated Tools
Use automated tools to assist in testing for business logic vulnerabilities. While these tools cannot fully replace manual testing, they help identify common issues. Choose tools that are well-known for testing business logic, such as Selenium for web applications. Automate tests by writing scripts to perform repetitive tasks, especially for edge cases and misuse scenarios. Review the results from these automated tests to identify potential vulnerabilities.
6. Review and Remediate
Security engineers must review the testing results and address any vulnerabilities to ensure the application correctly enforces all business logic. Analyze the findings to identify patterns or recurring issues. Collaborate with developers to fix the vulnerabilities, ensuring the solutions align with business rules. After making the changes, retest the application to confirm that you have resolved the vulnerabilities and introduced no new issues.
Preventing Business Logic Vulnerabilities
Preventing business logic vulnerabilities involves several best practices to ensure the application correctly enforces its business rules and processes. Here are ways to help prevent these vulnerabilities:
1. Understand Business Requirements
To ensure the application aligns with its intended purpose, start by thoroughly understanding the business requirements and logic it must follow. Gather and document all business requirements by working closely with business analysts and stakeholders. Create detailed specifications that outline the application's expected behavior.
2. Implement Proper Input Validation
Organizations should utilize validation libraries that check for numbers, email addresses, and special characters to ensure all user inputs meet the required format and values. These libraries help enforce data integrity by validating inputs at the point of entry, reducing the risk of errors and vulnerabilities.
Example
The function validate_input(quantity) checks if the input quantity is an integer and greater than zero. If not, it raises a ValueError to prevent invalid input from proceeding. This practice stops negative or non-integer quantities from causing issues in the system.
Implementing server-side validation is equally crucial. While client-side checks provide a user-friendly experience, they can be easily bypassed by attackers. By validating inputs on the server side, organizations scrutinize all data before processing, adding an extra layer of security. This approach prevents malicious users from submitting harmful data, such as SQL injection attempts or cross-site scripting (XSS) payloads.
3. Enforce Workflow Integrity
To ensure users follow the correct sequence of steps in the application, use state management to track their actions and verify they proceed in the correct order. Implement checks at each step to confirm that the the system completed the previous steps accurately.
Example
The function process_order(order) ensures the order is processed only after verifying payment completion. If the payment is not complete, it raises an exception, maintaining the integrity of the workflow by preventing unauthorized actions.
4. Implement Robust Authorization Controls
Ensure that users can access only the data and functions they are authorized to use by implementing role-based access control (RBAC) to manage permissions. Regularly review and update user permissions to keep them appropriate and aligned with current access needs.
Example
The function access_admin_panel(user) checks if the user has administrative privileges before granting access. If the user is not an admin, it raises a PermissionError, enforcing authorization controls and preventing unauthorized access.
5. Handle Concurrency Properly
Manage simultaneous actions to prevent issues like double-spending or data corruption by implementing database transactions, which ensure that operations are completed fully or not at all. Use locking mechanisms to prevent multiple users from modifying the same resource at the same time.
Example
The function book_ticket(user, event) handles ticket booking in a transactional manner to avoid race conditions. It checks ticket availability and, if available, decrements the ticket count; otherwise, it raises an exception, ensuring consistent data in concurrent scenarios.
6. Regularly Test Business Logic
Continuously test the application’s business logic to identify and fix vulnerabilities by creating comprehensive test cases that cover all aspects, including edge cases. Perform both manual and automated testing to uncover potential issues and ensure robust business logic.
Final Thoughts
Business logic vulnerabilities are a critical concern for application security. Organizations must actively implement robust testing strategies to uncover these elusive threats. The Akto platform provides powerful tools to detect and mitigate these vulnerabilities effectively.
By using advanced technology with a security-focused approach, organizations can protect their critical processes and maintain the integrity of their applications in an ever-evolving threat landscape. Discover how Akto can help you achieve comprehensive security. Book your demo today and start protecting your APIs!
Explore more from Akto
Blog
Be updated about everything related to API Security, new API vulnerabilities, industry news and product updates.
Events
Browse and register for upcoming sessions or catch up on what you missed with exclusive recordings
CVE Database
Find out everything about latest API CVE in popular products
Test Library
Discover and find tests from Akto's 100+ API Security test library. Choose your template or add a new template to start your API Security testing.
Documentation
Check out Akto's product documentation for all information related to features and how to use them.

