What is API Discovery?
API Discovery helps identify, map, and manage APIs within an organization, ensuring security, performance, and seamless integration across systems.

Kruti
Dec 7, 2024
API discovery is the process of identifying and classifying APIs (Application Programming Interfaces) within an organization's digital environment. API Discovery enables the systematic discovery of APIs, giving organizations complete insight and control over the APIs available across their networks.
This blog will explore API Discovery, including its importance, types, functionality, tools, and key challenges in API Discovery.
What is API Discovery?
API Discovery is the creation of a centralized repository or API registry, which acts as a uniform database for documenting all APIs, whether internal (private APIs used within the organization) or external (public APIs used to communicate with external partners or customers).
This repository serves as the official source of information for the organization's entire API architecture, reducing the risk of unmanaged or unprotected APIs. This approach guarantees that security engineers, DevOps teams, and system administrators can efficiently manage the APIs, which includes creation, versioning, security, and discontinuation.
What does API Discovery Discover?
API discovery discovers and categorizes all APIs within an organization's environment:
1. Public APIs
Public APIs, or external or open APIs, allow external developers and users outside the organization to access them. They enable third-party integrations that allow applications or services from external organizations to interact with the organization's systems. For instance, a social media company might offer its public API so that developers outside the company can integrate their applications with the company's services.
2. Internal APIs
The organization designs internal APIs for internal use. They allow communication and data exchange between internal systems, services, or applications. With the help of internal APIs, organizations can modularize their architecture, which promotes reusability and efficient internal processes. For example, an internal API could allow the HR system to communicate with the payroll system to process employee salaries.
3. Shadow APIs
Shadow APIs are APIs that organizations fail to document or authorize, causing them to exist without the knowledge of IT or security teams. Developers often create these APIs for testing or specific projects and deploy them without following standard governance protocols.
These APIs pose significant security risks because they often lack proper security measures and oversight. For example, a developer might create a temporary API endpoint for a specific task and forget to remove it, leaving it vulnerable to exploitation.
4. Zombie APIs
Zombie APIs refer to outdated or deprecated APIs that teams or systems fail to shut down, leaving them operational but no longer actively maintained or used. Version updates often lead to these APIs when teams do not properly retire old API versions.
These APIs become security vulnerabilities because organizations or teams might fail to apply necessary updates or patches. For instance, an old version of a login API might still allow access even after developers deploy a new version, providing a potential attack vector.
5. Endpoints and Methods
Endpoints are specific URLs or URIs that clients use to access APIs. Methods, also known as HTTP methods (such as GET, POST, PUT, DELETE), define the type of operation that clients perform at the endpoint.
Each API specifies a set of endpoints and methods that outline the available functions and data interactions. For example, an API might include an endpoint /users with a GET method to retrieve user information and a POST method to create a new user.
How Does API Discovery Impact API Security?
API discovery is a basic security aspect of protecting APIs, and it provides critical security benefits by systematically identifying and documenting all APIs within an organization's ecosystem. Comprehensive discovery increases visibility by giving a comprehensive view of all APIs, including undocumented or unmanaged shadow APIs.
This process minimizes blind spots and makes sure that the security team accounts for and monitors all APIs effectively. API discovery also assists in risk identification since it detects outdated or vulnerable APIs, through which sensitive data may leak. Thus, organizations can find such vulnerabilities and act to strengthen the security posture early enough.
API discovery ensures proper compliance is maintained, such as GDPR, HIPAA, or PCI DSS, by keeping the correct API inventory secure. It also reduces threats from 'shadow' and 'zombie' APIs, which remain undocumented or deprecated but operational, thereby reducing attack vectors. Finally, API discovery strengthens access control measures, ensuring authentication and authorization suit the current API landscape and minimize unauthorized data access.
How does Akto help with API Discovery?
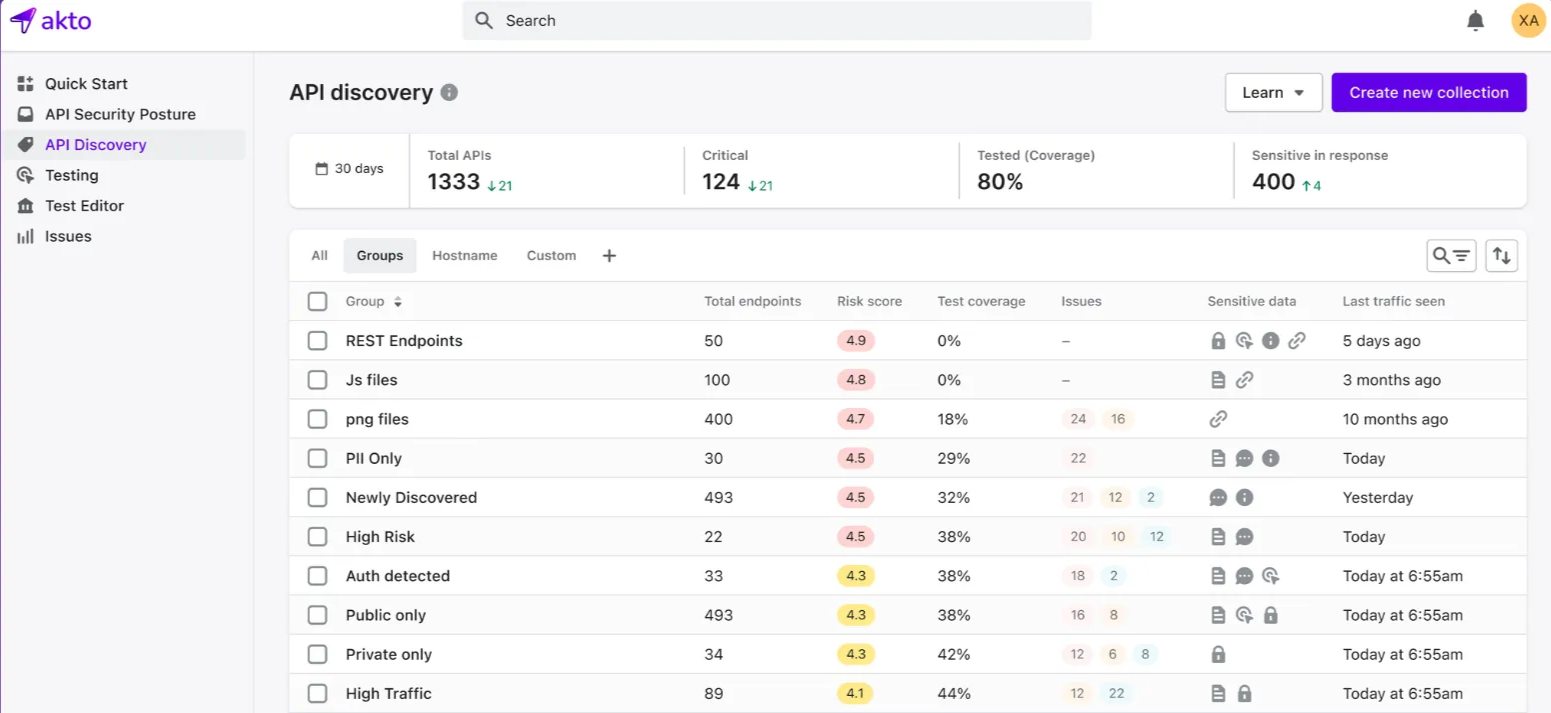
Akto enhances API discovery through a comprehensive approach that combines automated source code analysis with real-time traffic monitoring. This dual methodology ensures that organizations maintain an up-to-date and complete inventory of all APIs, including internal, external, third-party, shadow, and zombie APIs.
Automated API Discovery from Source Code
Akto scans the source code repositories of applications to automatically identify APIs, real-time recording of their development. Such undocumented or forgotten APIs are highly unlikely, and they notify security teams directly about new and modified endpoints. Having direct integration capabilities with source management systems like GitHub, Bitbucket, and GitLab, it ensures its documentation of API is current and complete.
Real-Time Traffic Monitoring
Beyond code analysis, Akto has over 40 traffic connectors to observe all API interactions, including cloud and on-premises. These real-time monitors pick out active APIs, highlight shadow and zombie APIs, and determine their vulnerability exposure to threats.
Correlating both code and runtime environment data, Akto offers a complete view of the API landscape. Security teams can perform dynamic risk assessments and promptly remediate vulnerabilities.
Importance of API Discovery
API Discovery is a crucial aspect of modern software infrastructure that brings several key benefits to organizations. Let's explore why API Discovery has become an indispensable tool for organizations.
Improved Security
APIs are gateways for data exchange, and any vulnerability in them can expose critical systems to attacks. With API Discovery, organizations can identify shadow APIs—undocumented, deprecated, or forgotten endpoints that hackers often exploit. These APIs may lack adequate security measures, making them susceptible to attacks such as injection vulnerabilities, authentication bypasses, and misconfigurations.
Operational Efficiency
In large organizations, different teams build and use APIs independently, duplicating functionality and inefficiencies. API Discovery helps teams reuse APIs by keeping an accurate inventory of current ones and reducing redundancy. Teams can focus on innovation rather than recreating APIs, saving time and money. It also optimizes API usage by notifying services of endpoints, reducing rework.
Compliance and Governance
Many organizations have to comply with data management and security regulations like GDPR, HIPAA, and PCI DSS. These requirements frequently require full visibility into an organization's data flows, including APIs.
API Discovery helps organizations comply with these rules by monitoring and tracking all APIs, especially those handling sensitive or personal data. It also improves governance by allowing teams to apply similar policies across all APIs to fulfill internal and external legal standards.
API Lifecycle Management
Organizations discontinue earlier API versions as APIs change. Managing API versions and retiring outdated APIs is difficult without API Discovery. API Discovery tracks all API versions, helping teams replace insecure versions and upgrade systems that use them. This prevents service outages and keeps APIs current, safe, and optimized.
Faster Incident Response
API Discovery provides an inventory of all APIs, including configurations, security protocols, and usage, to speed up incident response in the case of a data breach or vulnerability attack. Security engineers can quickly discover and identify harmful APIs, implement updates, and revoke endpoint access using this inventory.
Types of API Discovery
Organizations use a number of different API discovery methods to identify, categorize, and understand the APIs that operate within their infrastructure. The following are the primary forms of API discovery:
1. Automated API Discovery
Advanced tools and technologies in Automated API Discovery scan and map APIs across an organization's ecosystem, scanning networks, application logs, and API gateways for detection of APIs, including undocumented or outdated ones.
This method is of more significance in dynamic and complex environments where in it would be impossible to track everything by hand. Automated techniques allow organizations to keep detailed, comprehensive lists of APIs; hence organizations limit the potential for vulnerability and inefficency.
2. Manual API Discovery
In manual API Discovery, teams such as security engineers, system administrators, and DevOps professionals actively search for and document APIs in use. This process often involves reviewing documentation, interacting with development teams, and examining configuration files and logs.
Although labor-intensive and time-consuming, the manual discovery provides detailed insights that automated methods might miss, especially in smaller environments or where specialized tools are unavailable.
3. Self-Descriptive APIs
These APIs make the discovery process easier because of metadata descriptions of their structure and function. These often contain specifications such as OpenAPI or Swagger, including information on endpoints, data formats, authentication mechanisms, and request and response patterns.
Discovery tools can use this metadata to automatically catalog APIs and understand their purpose. In the adoption of self-descriptive APIs, organizations can enhance both visibility and usability, thereby making the integration and monitoring processes smooth.
4. API Gateways and Management Platforms
API gateways and management platforms form a crucial part of API Discovery. They act as a central point for API traffic. They monitor all the interactions between APIs, which can provide real-time usage patterns and active endpoints.
As a consequence, they assist organizations to develop a complete API inventory. In large-scale infrastructures, API gateways simplify the discovery and management process by making sure that no API is missed, while facilitating enhanced traffic control and security enforcement.
5. Traffic-Based API Discovery
Traffic-based API Discovery discovers APIs by reading network activity. This works by monitoring HTTP or some other protocol traffic to sniff out API endpoints and use patterns. It especially reveals undiscovered or rogue APIs that other methods would not detect. By monitoring live traffic, companies can gain real-time awareness of their API ecosystem by addressing their potential blind spots and associated security risks.
How API Discovery Works?
API Discovery is the process of identification, documentation, and monitoring APIs across an organization's infrastructure. Let's discuss key steps and components that enable API Discovery to work effectively.
1. Environmental Scanning and Identification
The first step is scanning the environment to find all APIs. The tools and methods vary depending on the complexity of the organization's infrastructure. Network traffic monitoring plays a significant role, where tools observe API requests and responses to uncover active endpoints and associated metadata, such as request types and payloads.
In addition, source code scanning is employed to identify API calls embedded in repositories like Git or Bitbucket, which can reveal internal or third-party APIs. For organizations using API gateways, these gateways provide a centralized view by routing all API traffic, enabling the automatic discovery of APIs in real-time.
2. Classification and Documentation
After identification, security teams classify and fully document them. This procedure includes mapping the endpoints, supported methods, and base URLs, creating an entire structure of the APIs. It is tracked which APIs are either deprecated or no longer used in a version, therefore making the ones compatible and secured.
The security teams judge the security practices by documenting authentication methods like API keys or OAuth and authorization protocols. Tools also extract schemas that define the request and response format, creating detailed documentation, such as OpenAPI specifications. They categorize APIs in accordance with their roles—either as internal, external, or partner-facing—and tag them to improve management, keeping them aligned with the related team or use case.
3. Real-Time Monitoring and Continuous Discovery
Tools facilitate continuous monitoring post-discovery, allowing continuous monitoring to detect changes or new APIs in real-time. This is critical in dynamic environments, such as microservices architectures, where APIs can be rapidly deployed or modified. Continuous monitoring tracks the traffic of APIs, meaning newly created or updated APIs document and integrate promptly into the central catalog.
In addition to discovery, tools often track API health and performance metrics like latency and error rates to identify potential bottlenecks early. Security teams integrate monitoring to detect misconfigurations, insecure endpoints, and suspicious activities like abnormal traffic patterns or failed authentication attempts, proactively mitigating risk.
4. API Lifecycle Management
API Discovery helps with the full life cycle of an API-from its creation and updates to its eventual deprecation and removal. Tools track API version releases, ensuring that teams stay compatible across systems while keeping the older versions flagged for replacement. At the time of API deprecation, the team determines the dependencies, making it seamless and without breaking any service.
Organizations maintain governance and compliance by enforcing the security policies and regulatory requirements of data encryption and HIPAA standards, GDPR. The purpose of all this is that the APIs stay secure, functional, and compliant with organizational goals.
5. Integration with DevOps and CI/CD Pipelines
API Discovery integrates with DevOps workflows and CI/CD pipelines. It discovers and documents APIs automatically across the entire lifecycle of development. As developers develop new APIs, their discovery tools will scan the environment, which will update the catalog to avoid tedious manual tracking efforts.
This integration will foster a feedback loop between developers and security teams to enable early detection and resolution of documentation errors, security gaps, or performance issues. By embedding API Discovery into the development process, organizations maintain an up-to-date and secure API ecosystem while streamlining development and deployment cycles.
Challenges in API Discovery
API Discovery is essential for an organization, but several challenges should be addressed. Here are some of the challenges in API discovery:
1. Shadow APIs
One of the most difficult challenges with API Discovery is detecting shadow APIs, which exist but are undocumented, unmonitored, or forgotten. Development teams often create these APIs during rapid development cycles or for short-term use. Shadow APIs have a substantial security risk since they lack the same monitoring and security measures as documented APIs, making them open to attacks like data leaks or unauthorized access.
2. API Sprawl
Organizations are struggling with API sprawl, which occurs when teams create and use hundreds or thousands of APIs across several environments and platforms. This can make it challenging for security engineers and DevOps teams to keep track of all APIs and ensure they document, secure, and manage them properly.
3. Lack of Centralized API Management
Diverse teams develop and deploy APIs, but they don't have a consistent API management strategy or centralized API gateway. This leads to fragmented API management, where various teams use different techniques for API documentation, versioning, and security. Without centralized governance, it is difficult for teams to locate, document, and secure APIs consistently throughout the organization.
4. Real-time API Changes
APIs are often updated or modified in real-time, particularly in systems that use continuous integration and delivery (CI/CD) pipelines. Teams can release new versions, developers add or remove endpoints, and API traffic patterns can change quickly. Keeping track of these dynamic changes is difficult for API discovery tools because the API inventory can quickly become outdated if teams do not monitor it continuously.
5. Security and Compliance Issues
Maintaining compliance with industry regulations such as GDPR, HIPAA, and PCI-DSS is becoming increasingly difficult as the use of third-party APIs and complicated API interfaces grows. APIs that handle sensitive data must comply with these requirements, and failing to detect or monitor such APIs can result in severe legal and financial consequences.
Final Thoughts
API Discovery is essential for every organization that uses APIs to provide digital services. API Discovery optimizes performance, improves security, and increases operational efficiency by providing visibility into all APIs, both internal and external. API Discovery is an ongoing process and allows security engineers to effectively monitor the API lifecycle.
Akto offers a complete API discovery and API security solution that gives organizations real-time visibility of their API landscape. Its broad capabilities assist security engineers in discovering, monitoring, and securing APIs while keeping them compliant and optimized for performance. Schedule a demo and take control of the API administration today.
Important Links
Keep reading
API Security
8 minutes
NIST Cybersecurity Framework
The NIST Cybersecurity framework provides organizations with a set of standards, guidelines, and practices to develop strong cybersecurity practices for managing cybersecurity risks effectively.
API Security
7 minutes
API Security Audit
An API Security Audit evaluates APIs, identifies potential risks, and strengthens the organization's defenses against security breaches and cyber-attacks.
API Security
8 minutes
Security Information and Event Management (SIEM)
SIEM aggregates and analyzes security data across an organization to detect, monitor, and respond to potential threats in real time.
Experience enterprise-grade API Security solution