Security Requirement: Types, Purpose, and Importance
Security requirements illustrate the specific procedures, controls, and safeguards that protect an organization's sensitive data from cyber threats and data breaches.

Muze
Aug 2, 2024
A security requirement specifically outlines the necessary security functionalities to ensure various security properties of software are met. Industry standards, legal obligations, and historical vulnerabilities derive these requirements. They define new features or enhancements to address specific security issues or mitigate potential risks.
In this blog, we will teach you about security requirements, their purpose, several types of security requirements, and the implementation process of security requirements. Additionally, we will introduce you to the key challenges in defining security requirements and present the top security requirements for robust protection.
Let’s get started!
What is a Security Requirement?
The term security requirement describes the particular procedures, controls, and safeguards that must be implemented to protect an organization's data, resources, and assets from potential dangers, security lapses, and unauthorized access.

Purpose of Security Requirements
Security requirements lay the groundwork for implementing security features within an application. By defining these requirements, organizations can clearly guide how to integrate security into their software development processes. These guidelines ensure consideration of all security aspects from the first design phase through deployment and maintenance.
Adhering to security requirements helps avoid the pitfalls of custom security solutions, which can often be prone to errors and may not cover all potential vulnerabilities effectively. Instead, security requirements enable security engineers and developers to use established best practices and controls that the industry has vetted over time.
Additionally, implementing security requirements helps prevent the recurrence of past security failures. By learning from historical vulnerabilities and incorporating those lessons into the security requirements, organizations can build more resilient systems. This proactive approach mitigates risks before they become exploitable vulnerabilities, thereby enhancing the application's overall security posture.
Types of Security Requirements
Security requirements can be categorized into several types:
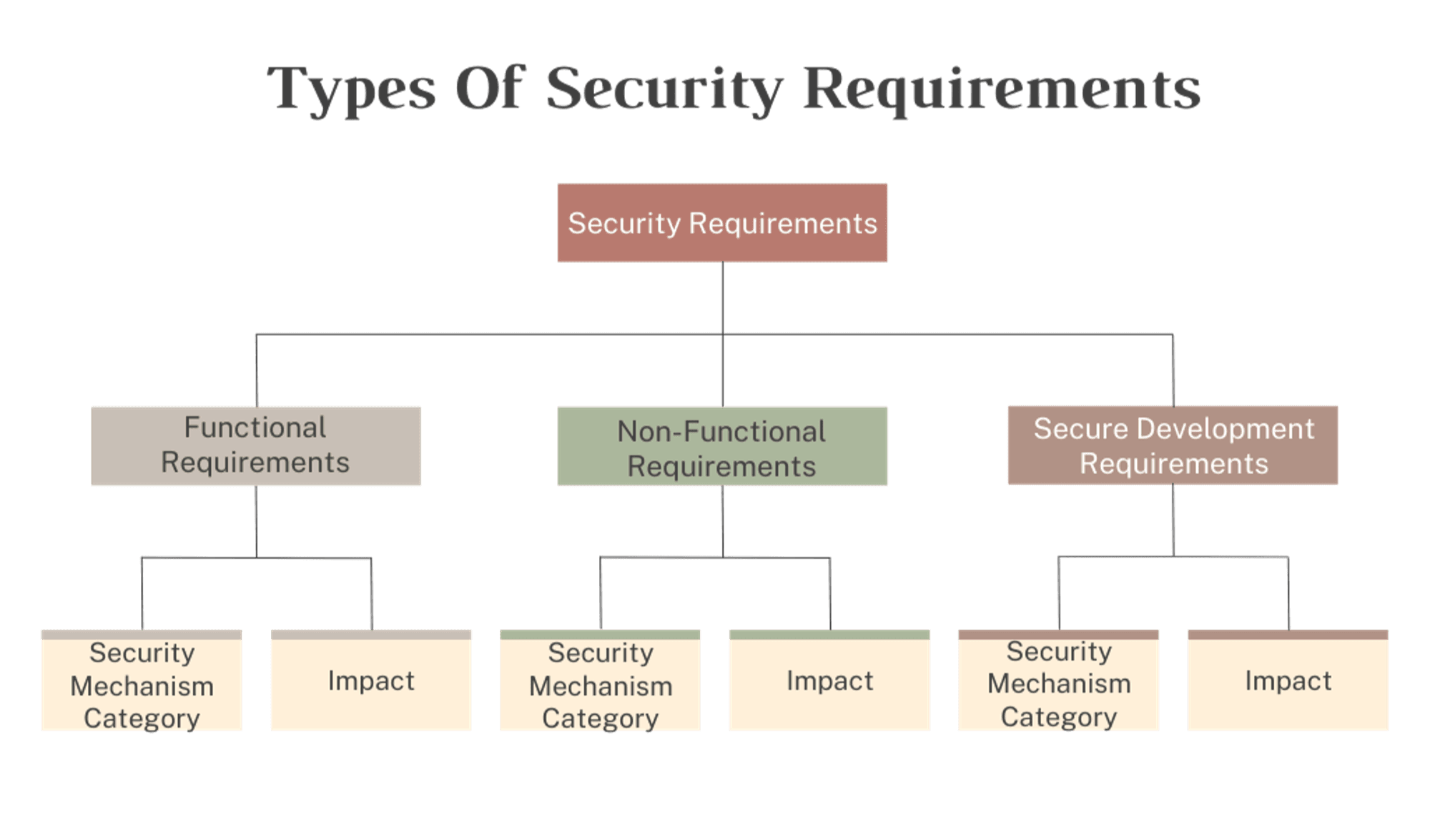
Secure Functional Requirements: These integrate security measures into the overall functional requirements in the organization’s system and specify actions that the organization must prevent to ensure security. For example, they prevent unauthorized access to sensitive data and ensure that only authorized personnel can perform certain actions within the system.
Functional Security Requirements: These specify the security services and features that the system must provide to protect data and resources. Examples include authentication methods to verify user identities, authorization mechanisms to control user access levels, and encryption services to safeguard data in transit and at rest.
Non-Functional Security Requirements: These focus on the architectural and performance aspects of security within the organization’s system. They include considerations like system robustness, which enables the system to withstand attacks and continue operating, and performance requirements that ensure security measures do not degrade system efficiency.
Secure Development Requirements: These outline the practices and methodologies to follow during the system's development to minimize vulnerabilities. This includes adhering to coding standards that prevent common security flaws, conducting regular security testing to identify and fix issues early, and implementing secure development practices throughout the software development lifecycle.
Security Requirements Implementation
Four comprehensive steps typically guide the successful implementation of security requirements:
1. Discovery and Selection
In this initial phase, security engineers identify relevant security requirements from various standard sources, such as industry standards, legal regulations, and historical vulnerability data. Select the requirements most applicable to the current application release, ensuring they align with the organization's security objectives and risk management strategies. Consult with stakeholders to understand their specific security needs and expectations.
2. Investigation and Documentation
After selecting the relevant security requirements, security engineer assess the existing application against these requirements. Thoroughly evaluate the application's current security posture to identify any gaps or areas needing improvement. Document the compliance status of the application, any necessary changes to meet the security requirements, and the reason behind these changes. This documentation will serve as a reference for future audits and continuous improvement.
3. Implementation
Integrate the identified security requirements into the application. Modify the application's code, architecture, and configuration to meet the specified security standards. Deploy new security technologies or tools to address the identified vulnerabilities. Collaborate between security engineers, developers, and IT staff to ensure seamless implementation without disrupting the application's functionality.
4. Testing
Create and execute test cases to verify that the new security functionalities have been correctly implemented and that all identified vulnerabilities have been addressed. Use various testing methods such as security testing, penetration testing, and vulnerability assessments. Security engineers must ensure that the application meets the defined security requirements and that the implemented security measures effectively mitigate potential risks. Continuously test and monitor to maintain the security posture over time as new threats and vulnerabilities emerge.
Key Challenges in Defining Security Requirements
Defining security requirements presents several key challenges that complicate the process of ensuring robust application security.
1. Complexity of Security Needs
Security requirements must address a wide range of potential threats and vulnerabilities, which vary significantly across different applications and environments. This complexity makes it difficult to create a comprehensive set of requirements that are both effective and manageable.
2. Evolving Threat Landscape
The rapid evolution of cyber threats necessitates continuously updating security requirements. Organizations must stay informed about new vulnerabilities and attack vectors, which create challenges in maintaining relevant and up-to-date security requirements.
3. Integration with Existing Requirements
The functional and non-functional requirements of the software must integrate security requirements. This integration requires balancing security needs and the overall functionality and usability of the application.
4. Stakeholder Alignment
Different stakeholders have varying priorities and understandings of security needs. Achieving consensus on what security requirements to prioritize can be a significant challenge, especially in larger organizations.
5. Measurement and Testing
Defining measurable and testable security requirements is crucial for effective implementation. However, developing clear metrics for security can be difficult, as security often requires qualitative assessments rather than quantitative measures.
Top Security Requirements for Robust Protection
To ensure the safety and integrity of the organization's data and systems, adhere to key security requirements designed to protect against a wide range of threats.
1. Access Control and Authentication
Authentication confirms a user's identity before granting them access to a system or application. This process ensures that only users with permission can access particular files or resources.
The system protects sensitive data and uses robust authentication methods like role-based access control and multi-factor authentication to aid authorized access.
2. Data Encryption
This technique transforms private data into a code only authorized individuals can decode.
Encrypting the data ensures its confidentiality and integrity by preventing interception and unauthorized access in transit and at rest.
3. Use of Secure Communication Protocols
Encryption of data transmission over networks helps eliminate surveillance and man-in-the-middle attacks.
Secure communication protocols include HTTPS for web traffic and VPNs for remote access. These protocols protect communication confidentiality and security and create a safe channel for data transfer.
4. Patch Management
Update and patch the systems regularly to fix security holes and vulnerabilities that hackers could exploit.
Patch management lowers the likelihood of damaging cyberattacks and data breaches by ensuring administrators update systems with the newest security fixes.
5. Network Security
Security engineers can protect their organization’s network infrastructure against malware infections, unauthorized access, and network-based attacks by utilizing firewalls, intrusion detection systems, and network segmentation.
Implementing these network security measures helps safeguard the organization’s data and systems from external threats, creating a secure online environment.
6. Security Monitoring and Incident Response
Organizations that maintain ongoing security monitoring can identify and address security incidents instantly.
Implementing incident response plans, security information and event management (SIEM) systems, and security monitoring tools allows organizations to quickly identify and mitigate security threats, reducing the impact of security breaches.
7. User Training and Awareness
Keeping a secure environment requires teaching staff members and users about security best practices, phishing awareness, and safe computing habits.
Additionally, security engineers should cover common software development vulnerabilities and include details on the methods used by cybercriminals and hackers in security awareness training for developers and security teams.
8. Code Reviews to Spot Possible Security Risks
Code reviews assist developers in finding and addressing security flaws so they can avoid typical risks. Check any code changes to see if they create new security risks. Security engineers must also review security requirements to ensure teams follow secure coding practices during development.
9. Secure Software Development
Consider security from the project's early planning phases. Secure coding practices and integrating security testing throughout the software development lifecycle allow for identifying and mitigating vulnerabilities early in the development process.
10. Regulatory Compliance
Organizations must adhere to industry rules and data protection statutes, such as GDPR, HIPAA, and PCI DSS, to safeguard consumer data and uphold regulatory compliance.
By ensuring that security requirements meet regulatory requirements, organizations can prevent fines, legal repercussions, and adverse publicity from non-compliance.
Final Thoughts
Security requirements require constant attention and are not a one-time task. Application security engineers must monitor security measures and enhance and update them frequently to keep up with the changing risk settings.
In-house, robust security requirements benefit security teams by giving them a clear path forward. They also support external regulatory requirements. Implementing security requirements and establishing strategies to prevent data breaches can ensure your software is secure.
Are you looking for API security for your organization? From financial institutions to healthcare sectors, Akto offers a proactive API security platform designed to prevent API data breaches quickly and efficiently. Akto's extensive Test Library allows you to run comprehensive API security testing that covers the OWASP API Security Top 10 vulnerabilities. With features such as continuous monitoring, integration with CI/CD pipelines, and a growing library of customizable tests, Akto ensures robust protection for your APIs
Fix API vulnerability issues with Akto. Book a demo now!
Important Links
Keep reading
API Security
8 minutes
NIST Cybersecurity Framework
The NIST Cybersecurity framework provides organizations with a set of standards, guidelines, and practices to develop strong cybersecurity practices for managing cybersecurity risks effectively.
API Security
7 minutes
API Security Audit
An API Security Audit evaluates APIs, identifies potential risks, and strengthens the organization's defenses against security breaches and cyber-attacks.
API Security
8 minutes
Security Information and Event Management (SIEM)
SIEM aggregates and analyzes security data across an organization to detect, monitor, and respond to potential threats in real time.
Experience enterprise-grade API Security solution



