LDAP Injection

Insha
Nov 7, 2024
LDAP injection occurs when attackers exploit vulnerabilities in an application's LDAP query structure. By injecting malicious code into LDAP queries, attackers can manipulate or bypass authentication mechanisms. This can lead to unauthorized access or retrieval of sensitive directory information. Proper input validation and using parameterized LDAP queries can help prevent such attacks.
This blog explains the working, examples, types, and prevention measures of LDAP Injection, a major security vulnerability.
What is LDAP Injection?
LDAP Injection is a security vulnerability that occurs when an attacker exploits weaknesses in an application's input validation mechanisms to manipulate LDAP (Lightweight Directory Access Protocol) queries. In simpler terms, it's like someone sneaking into a system by tricking it into running unauthorized commands.
For example, a web application that searches for user information using LDAP queries can be vulnerable if it doesn't properly validate input. An attacker could inject malicious code into the search field. When the application sends this input to the LDAP server, the injected code executes, granting the attacker access to or control over sensitive data.
LDAP Injection Example
Now, let's consider a vulnerable backend code where user input is not properly sanitized, leading to LDAP injection vulnerability:
In this vulnerable code, the search_username variable is directly concatenated into the LDAP filter without proper validation or sanitization. An attacker can exploit this flaw by providing a malicious input like "user123)", which alters the LDAP filter and potentially triggers unintended queries.
In the context of LDAP injection, "user123)" represents a malicious input that manipulates the LDAP query structure. While "user123" appears as a legitimate username, the closing parenthesis ")" changes the query's structure, leading to unintended behavior within the application.
Common Types of LDAP Injection Attacks
LDAP injection attacks come in various forms, each exploiting different vulnerabilities in LDAP-based systems. Let's explore the main types of LDAP injection:
Unsanitized Input
Unsanitized input occurs when the application fails to validate or sanitize user-supplied data before using it in LDAP queries. Attackers can exploit this by injecting malicious LDAP syntax into input fields, which can alter the structure of the query. This vulnerability allows attackers to manipulate query results or access unauthorized information.
LDAP Filter Injection
LDAP filter injection involves attackers inserting malicious LDAP filter expressions into user input fields intended for search queries. By manipulating the filter, attackers can change the logic of the query, bypassing authentication or gaining access to restricted information. This type of injection compromises the security of the LDAP query structure.
Base Injection
In base injection, attackers manipulate the base distinguished name (DN) used in LDAP queries. By injecting wildcard characters like "*", they can broaden the scope of the query, potentially retrieving more data than intended. This vulnerability can lead to unauthorized data access or even denial-of-service attacks on the LDAP server.
Attribute Injection
Attribute injection occurs when attackers inject LDAP attribute names into search queries. By altering which attributes are retrieved, they can access sensitive information or cause unintended behavior in the application. This type of attack compromises the integrity of the LDAP query results and can expose confidential data.
Time-Based Blind Injection
In time-based blind LDAP injection, attackers exploit response delays in LDAP queries to infer information about the database. They craft queries that intentionally cause the server to pause, using the response time to extract data. This method allows attackers to retrieve sensitive information without directly viewing query results.
Error-Based Blind Injection
Error-based blind LDAP injection involves attackers crafting queries designed to trigger errors in the LDAP server. By analyzing the error messages that the server returns, attackers can infer details about the underlying database structure or content. This method indirectly reveals sensitive information, making it a potent form of attack.
How Does LDAP Injection Occur?
Attackers manipulate user inputs to alter the structure of an LDAP query in LDAP Injection attacks. This typically occurs in applications that fail to properly validate or sanitize user input before incorporating it into LDAP query statements. Attackers can change the behavior of the query by injecting malicious input, leading to unauthorized access, data breaches, or other security vulnerabilities.
Manipulating LDAP Queries
Attackers structure LDAP queries similarly to SQL queries, using filters and attributes to search and manage directory data. When an application directly includes unvalidated user input in these filters, it creates a risk of injection attacks. For instance, in a search operation like (cn=user123), an attacker might inject additional characters or expressions to alter the intended query logic.
For example, an attacker could provide an input like user123) to close the existing LDAP expression prematurely and inject malicious content. This can lead to unintended access to directory data or bypass authentication controls.
Lack of Input Sanitization
The lack of input sanitization is one of the key reasons LDAP Injection occurs. Applications expose themselves to injection vulnerabilities when they fail to sanitize or validate user-supplied data. Attackers can exploit this by injecting LDAP metacharacters, such as * or ), to manipulate the structure of the query.
This manipulated query broadens the search, potentially allowing attackers to retrieve more data than intended. The lack of proper input validation allows malicious input to interpret as part of the LDAP query syntax, leading to serious security risks.
Query Structure Manipulation
Attackers can manipulate the structure of LDAP queries by inserting characters that alter the intended logic. For example, in a filter designed to retrieve user information (cn=user123), an attacker can add an extra closing parenthesis ) or a wildcard * to change the query into something like (cn=user123)), which could terminate the query early or modify its behavior to include unintended results.
This manipulation resembles SQL injection, where attackers exploit query syntax to achieve their malicious goals. In LDAP, this often results in bypassing authentication or gaining access to sensitive directory information.
Exploiting Application Logic
LDAP Injection often occurs because application logic assumes that user input is trustworthy. In cases where the application directly embeds the input into the LDAP query without filtering, attackers can introduce malicious payloads. This can lead to query tampering, where injected values affect the logic of the LDAP query, such as:
Bypassing Authentication: Instead of providing valid credentials, an attacker could inject an OR condition (
|) that always evaluates to true, granting unauthorized access.Retrieving Unauthorized Data: Through crafted injections, attackers may be able to retrieve sensitive information that would otherwise be protected.
For example, if attackers input *)(uid=*))(|(uid=*, they can potentially bypass normal authentication checks or widen the scope of an LDAP search query.
Impact of LDAP Injection Attacks
LDAP Injection attacks can have serious consequences for organizations, as they target the systems that manage sensitive directory data, including user authentication, access control, and configuration information. Below are the key impacts that organizations face from LDAP Injection attacks:
1. Unauthorized Access to Sensitive Data
One of the primary dangers of LDAP Injection is the ability for attackers to gain unauthorized access to sensitive information that organizations store in directory services. Organizations commonly use LDAP to manage user credentials, organizational roles, and resource access permissions. By exploiting injection vulnerabilities, attackers can alter LDAP queries to retrieve data they should not have access to, including usernames, passwords, and confidential organizational information.
For example, if an attacker can manipulate a query that a developer designs to return information for a specific user, they might be able to retrieve all users’ data or sensitive system configuration details. This type of data leakage can lead to privacy violations and legal repercussions, especially in industries with strict data protection regulations, such as healthcare or finance.
2. Bypassing Authentication Mechanisms
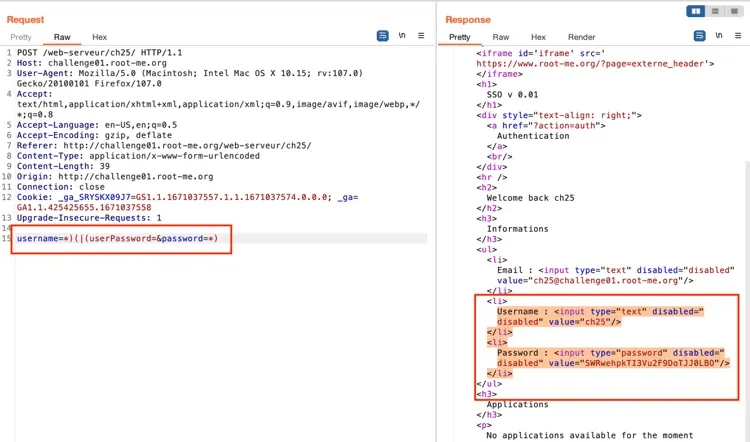
LDAP Injection allows attackers to bypass authentication mechanisms by altering queries that verify user credentials. This can lead to situations where attackers gain unauthorized access to systems without needing valid login credentials. By injecting specific expressions, such as (|(uid=*)(userPassword=*)), attackers can bypass normal authentication logic and gain access to privileged accounts.
Once authenticated, attackers can masquerade as legitimate users, potentially with administrative privileges which allows them to perform malicious activities undetected. This poses a significant security risk as attackers could manipulate or delete critical data, access restricted resources, and disrupt normal business operations.
3. Privilege Escalation
In addition to bypassing authentication, LDAP Injection can enable attackers to escalate their privileges within a system. By manipulating queries, attackers can grant themselves elevated permissions, allowing them to gain administrative access or control over resources they would not normally be authorized to access.
For example, by injecting commands that modify user roles or permissions, an attacker could escalate from a regular user account to an administrator account, giving them full control over the directory service and its resources. This level of access can be catastrophic, leading to widespread damage and potential system takeover.
4. Denial of Service (DoS) Attacks
Another potential impact of LDAP Injection is the ability to cause Denial of Service (DoS) conditions on the LDAP server. Attackers can inject queries that are highly resource-intensive, such as those using wildcards or complex expressions, which can overwhelm the LDAP server. When resource exhaustion prevents the server from processing legitimate requests, it can cause system downtime and interrupt business services.
This type of attack can disrupt critical operations, especially in organizations that rely heavily on LDAP for authentication and directory services. Prolonged downtime can result in significant financial losses and reputational damage.
5. Data Integrity Compromise
LDAP Injection can also affect the integrity of directory data by allowing attackers to inject commands that modify or delete entries in the LDAP database. This can lead to data corruption, unauthorized changes to user accounts, or the removal of important configuration data. Altered data can make it difficult for organizations to trust the accuracy of their directory services, and recovering from such attacks can be time-consuming and costly.
For example, attackers might alter group membership data, allowing unauthorized users to gain access to restricted areas, or modify security policies that control access to sensitive resources. Such changes could allow attackers to go unnoticed for extended periods, making the organization vulnerable to further attacks.
How to Prevent LDAP Injection?
Implementing robust prevention measures safeguards the organization’s systems against LDAP injection attacks and ensures the integrity of the data. These strategies include:
Enforce Input Validation
Ensure rigorous input validation before incorporating any untrusted data into LDAP queries. Validate all inputs against a predefined list of acceptable strings or characters, even when client-side validation is in place. Server-side validation is crucial for structured inputs like email addresses or social security numbers, and security teams should ensure that they adhere to strict regular expression patterns. For usernames, ensure only approved characters are allowed, excluding LDAP filter control characters.
Escape Input with Encoding
Encode user-controlled input strings to prevent LDAP control characters from altering the intended search filters. For example, Java applications use backslashes as escape characters to prevent metacharacters from being interpreted as part of the LDAP query. Encoding treats untrusted input as a literal string rather than a part of the LDAP query logic.
Use Parameterized Queries
Whenever possible, utilize parameterized queries to avoid concatenating user input directly into LDAP query strings. Parameterized queries separate data from the query structure, ensuring that security teams treat any input provided by users as data rather than part of the LDAP command. This approach effectively mitigates injection attacks by preventing user input from altering the query’s intended behavior.
Implement Logging and Monitoring
Implement robust logging and monitoring mechanisms to detect and respond to LDAP injection attempts. By monitoring LDAP queries for unusual patterns or unexpected results, security teams can quickly identify potential attacks. Logging failed queries or invalid input attempts can help trace malicious activity and strengthen future defenses.
Harden Directory Authorization
Reduce the impact of LDAP injection by applying the principle of least privilege to directory authorization. Limit the access permissions of the LDAP account that the application uses to bind to the directory. This approach restricts the execution of LDAP queries to authorized users only, thereby enhancing the security of the directory server.
Final Thoughts
LDAP injection remains a serious security threat, especially in applications that rely on directory services for authentication and user management. By exploiting poorly validated input, attackers can manipulate LDAP queries to access unauthorized data or compromise system functionality.
To prevent LDAP injection, organizations must prioritize input validation, use parameterized queries, and enforce strict access controls. Regular security audits and monitoring can also help detect vulnerabilities early, reducing the risk of exploitation.
Akto, an API Security Platform, can help in preventing LDAP Injection as part of its comprehensive API security suite. Akto includes tests that assess how well APIs handle various types of input, including LDAP queries.
By leveraging Akto's capabilities, application security engineers can run targeted injection tests, including LDAP, to identify vulnerabilities where unsanitized input could lead to security breaches. This testing is part of Akto's broader focus on input validation, ensuring that they protect APIs against various injection-based attacks such as SQL, NoSQL, and LDAP injections..
Book the Akto Demo today!
Explore more from Akto
Blog
Be updated about everything related to API Security, new API vulnerabilities, industry news and product updates.
Events
Browse and register for upcoming sessions or catch up on what you missed with exclusive recordings
CVE Database
Find out everything about latest API CVE in popular products
Test Library
Discover and find tests from Akto's 100+ API Security test library. Choose your template or add a new template to start your API Security testing.
Documentation
Check out Akto's product documentation for all information related to features and how to use them.

