Cobalt Pentest

Insha
Nov 11, 2024
Cobalt Pentest is a crowdsourced penetration testing platform that connects organizations with a network of vetted security professionals. These experts conduct on-demand pentests to identify vulnerabilities in applications, networks, or systems. The platform provides continuous testing and real-time collaboration with testers, allowing for quicker identification and remediation of security issues. Cobalt streamlines the pentesting process, offering flexibility and efficient security testing.
This blog explores Cobalt Pentest, its key features, processes, and challenges. Discover the transformative potential of Cobalt's PtaaS platform for enhancing cybersecurity frameworks.
What is Cobalt Pentest?

Cobalt Pentest is a Pentest-as-a-Service (PtaaS) platform that leverages a global network of security experts to perform penetration tests on an organization's digital assets. It combines real-time collaboration, automation, and reporting tools to provide quick identification of vulnerabilities and actionable remediation insights. The platform is designed for speed, scalability, and efficiency, offering flexible testing tailored to an organization's needs. By using Cobalt, organizations can continuously improve their security posture through streamlined testing processes and detailed analysis.
Key Features of Cobalt's PtaaS Platform
Cobalt's PtaaS platform offers several key features that revolutionize the penetration testing process and enhance organizational security:
Collaborative Environment
Cobalt's PtaaS platform fosters a collaborative environment, enabling pentesters, developers, security engineers, project managers, and business leaders to interact seamlessly throughout the testing process. This environment promotes effective communication, transparency, and teamwork, allowing for the quick resolution of security issues and enhancing the overall security posture of the organization.
Messaging Integration
The platform integrates with messaging tools like Slack, allowing stakeholders to communicate in real time. This integration ensures that updates are shared quickly, coordination is smooth, and all team members stay informed and engaged throughout the penetration testing process, facilitating faster decision-making and response to findings.
Scalability
The PtaaS platform offers scalability to meet diverse testing needs, allowing organizations to run penetration tests across a variety of applications, systems, and networks. It accommodates different sizes and complexities, from single application testing to multiple asset testing, making it adaptable to the security needs of both small teams and large enterprises.
Customization
The platform allows for customization, so organizations can tailor their testing processes to their specific security needs. Security teams can define the scope and objectives, set schedules, and configure parameters, ensuring the penetration testing is aligned with their unique operational requirements and security goals.
Reporting and Analysis
Robust reporting and analysis capabilities provide stakeholders with actionable insights from testing results. The platform generates detailed reports that highlight discovered vulnerabilities and weaknesses, as well as recommended remediation measures, enabling organizations to prioritize and effectively address their security risks.
Compliance Support
The PtaaS platform aids in meeting compliance with regulatory requirements and industry standards like GDPR, PCI DSS, and HIPAA. Organizations can utilize the platform's features to align their penetration testing activities with these regulations and adhere to security best practices, ensuring legal and regulatory compliance while strengthening their security framework.
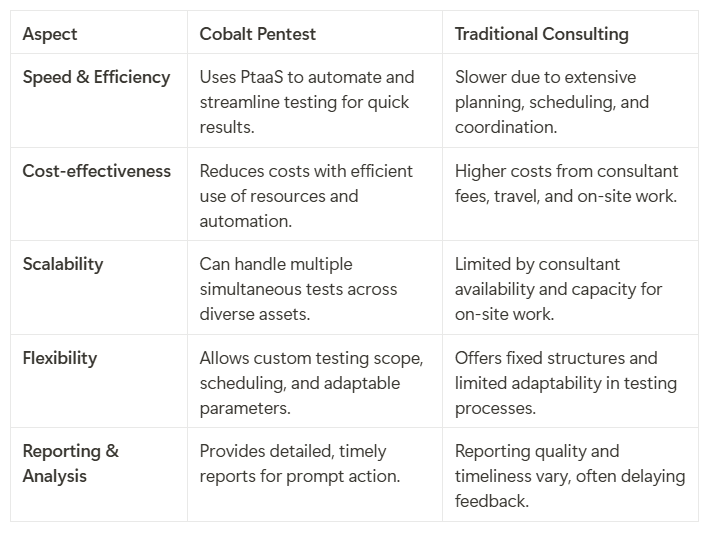
Comparing Cobalt Pentest with Traditional Consulting
Let's explore the key differences between Cobalt Pentest and traditional consulting engagements, highlighting how Cobalt's innovative approach revolutionizes the penetration testing landscape.
Here's a table comparing Cobalt Pentest and Traditional Consulting Engagements:
Cobalt Pentesting Process
Implementing Cobalt Pentest enhances an organization's cybersecurity framework through a structured, comprehensive approach that integrates advanced penetration testing into existing security protocols.
Scoping & Planning
Cobalt pentesting begins with defining the scope by identifying assets to be tested, setting security objectives, and aligning with business needs. This step includes determining test timelines, goals, and potential limitations to ensure all aspects of the organization's security requirements are addressed.
Assembling the Pentesting Team
Cobalt handpicks an experienced pentesting team based on the project's specific challenges and security requirements. The platform assigns each tester's skills and background are matched to the assets being tested, ensuring effective and specialized attention to different facets of the organization's infrastructure.
Kickoff & Asset Discovery
Once the team is onboarded, they engage in a kickoff session to align with stakeholders. The asset discovery phase involves mapping out all digital assets, gathering data, and understanding the architecture to identify potential attack surfaces, which lays the foundation for more targeted testing.
Vulnerability Identification
The testers utilize a blend of automated scans and manual testing to uncover vulnerabilities. During this phase, they examine areas like weak configurations, insecure code, and flaws in authentication to pinpoint security gaps. Each vulnerability is analyzed for severity, exploitability, and potential impact on the system.
Exploitation & Testing
In this phase, the team attempts to safely exploit identified vulnerabilities to confirm their presence and impact. The goal is to assess how an attacker might leverage these flaws without disrupting the system. Testing is thorough, covering multiple scenarios to understand how vulnerabilities could compromise security.
Reporting & Remediation Guidance
Detailed reports are generated to highlight vulnerabilities, their risks, and actionable remediation steps. The Cobalt platform supports interactive communication, allowing teams to discuss findings, ask questions, and seek guidance directly from testers. This collaborative approach helps the organization to efficiently address vulnerabilities and strengthen its security posture.
Challenges in the Cobalt Pentesting Process
Organizations face several challenges when implementing Cobalt's pentesting process, requiring careful planning and execution to maximize its effectiveness.
Clear Scope Definition
Setting a precise scope is vital to effective testing, but it's often difficult with complex systems that are constantly evolving. Testing teams must ensure all critical assets are covered without crossing boundaries, making ongoing adjustments as systems change.
Assembling Specialized Teams
Cobalt assembles teams with diverse skills tailored to each specific test environment. The company finds testers with expertise in certain technologies and ensures they stay up to date with the latest security practices and trends.
Managing Real-Time Collaboration
Coordinating between multiple testers and stakeholders in real time can be difficult. Rapid feedback loops are essential for effective testing, but time zone differences, varying communication styles, and project deadlines make collaboration a challenge, potentially delaying progress.
Complex Asset Discovery
Identifying hidden, forgotten, or undocumented assets is critical, as even a small oversight can leave vulnerabilities untested. Cobalt testers need to thoroughly map out every aspect of a system, but this can be hard when dealing with decentralized and complex cloud environments.
Balancing Automated and Manual Testing
Achieving the right balance between automated and manual testing is crucial for effective pentesting. Automation can quickly identify common vulnerabilities, but manual testing is needed to uncover more complex issues, making it challenging to cover all bases without redundancy.
Prioritizing Vulnerabilities
After discovering vulnerabilities, prioritizing them based on severity, potential impact, and exploitability is not straightforward. Testers must work closely with stakeholders to weigh each vulnerability against the organization's risk appetite and remediation capacity to address the most critical issues first.
Final Thoughts
Cobalt's Pentest as a Service (PtaaS) platform is a transformative tool for organizations looking to enhance their cybersecurity frameworks. Its user-friendly, collaborative environment, combined with its scalability, automation, and customization capabilities, make it a cost-effective and efficient solution for penetration testing. Its powerful reporting and analysis features provide actionable insights that empower organizations to strengthen their security postures effectively.
Explore more from Akto
Blog
Be updated about everything related to API Security, new API vulnerabilities, industry news and product updates.
Events
Browse and register for upcoming sessions or catch up on what you missed with exclusive recordings
CVE Database
Find out everything about latest API CVE in popular products
Test Library
Discover and find tests from Akto's 100+ API Security test library. Choose your template or add a new template to start your API Security testing.
Documentation
Check out Akto's product documentation for all information related to features and how to use them.

