Nessus Penetration Testing

Insha
Oct 15, 2024
Nessus is a vulnerability assessment tool designed to scan networks, systems, and applications for potential security risks. It identifies vulnerabilities like misconfigurations, default passwords, and software flaws. Nessus provides detailed reports to help security teams prioritize remediation and enhance their security posture. It's widely used for its efficiency and comprehensive scanning capabilities.
The blog explores Nessus Penetration Testing, covering its benefits, functionality, setup process, and best practices for effective use.
Let’s get started!
What is Nessus Penetration Testing?
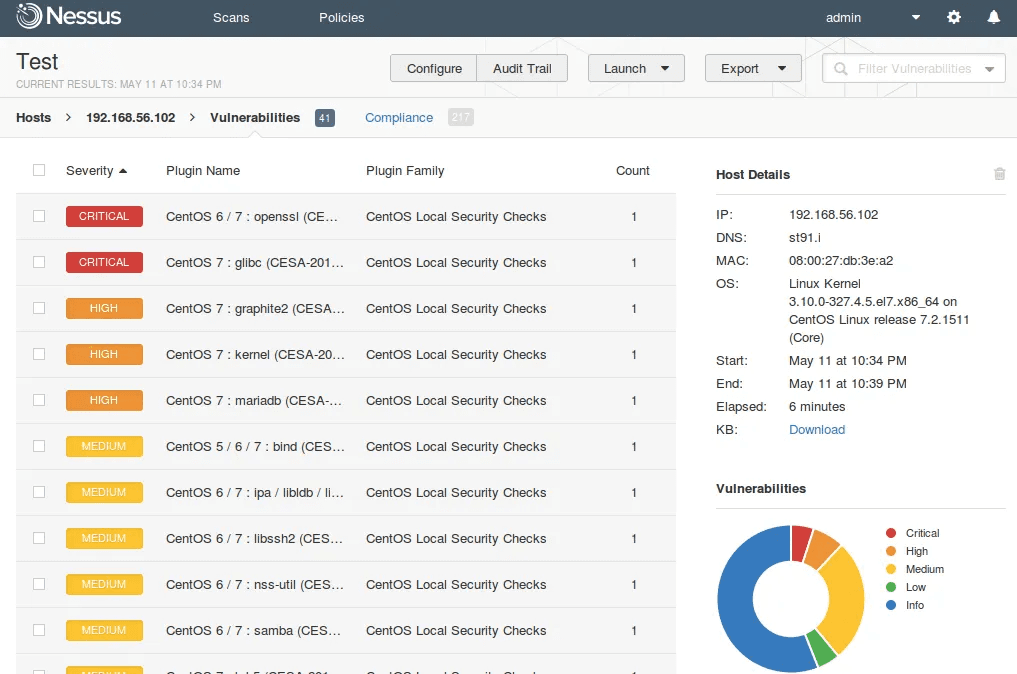
Nessus Penetration Testing is the process of using Nessus, a vulnerability scanning tool, to assess systems for potential security weaknesses. It automates the identification of vulnerabilities like misconfigurations, open ports, weak passwords, and unpatched software, providing comprehensive security insights.
Nessus offers detailed reports with information on risk levels and potential impact, enabling security teams to effectively prioritize and address these vulnerabilities. The tool is frequently updated with the latest vulnerability definitions, making it suitable for continuous and thorough security assessment across various environments.
Benefits of Nessus Penetration Testing
Nessus offers a powerful suite of benefits that enhance an organization's cybersecurity posture and streamline vulnerability management processes. The benefits include:
Proactive Security
Nessus enables security engineers to identify vulnerabilities before they can be exploited, providing a proactive approach to threat management. By uncovering weaknesses early, Nessus helps reduce the attack surface and improve overall security posture. This proactive approach ensures that risks are addressed promptly.
Efficiency
The scanning capabilities of Nessus are designed to be both fast and comprehensive, allowing security engineers to quickly assess their systems. With its ability to detect vulnerabilities in a short amount of time, Nessus helps save valuable resources while ensuring thorough security assessments. This efficiency supports timely remediation.
Comprehensive Coverage
Nessus is capable of detecting a wide array of vulnerabilities, from software flaws and configuration issues to malware and outdated patches. The tool’s extensive vulnerability database ensures that even the most obscure threats are identified, providing organizations with confidence that no security risk is overlooked.
Ease of Use
The user-friendly interface of Nessus makes it accessible to both security experts and beginners. Its straightforward setup and scanning processes allow users to efficiently configure scans, analyze results, and take action. This ease of use simplifies vulnerability management and supports quick learning.
Detailed Reporting
Nessus generates comprehensive and detailed reports that offer clear insights into identified vulnerabilities and recommended remediation steps. These reports help prioritize vulnerabilities based on their severity, enabling security teams to make informed decisions and take effective actions to secure their systems.
How Nessus Works?
Nessus employs a systematic approach to identify and assess vulnerabilities in your network infrastructure, following a step-by-step process that ensures comprehensive coverage and accurate results.
1. Initial Target Discovery
Nessus starts by performing an initial discovery scan to identify all systems, networks, and devices within the specified scope. It uses techniques like ICMP pings, port scanning, and service detection to map out the network.
This step collects detailed information, such as open ports, operating systems, and running services or applications. By uncovering all active hosts and their configurations, Nessus creates an asset inventory to ensure comprehensive coverage. This discovery process is critical for identifying all potential entry points that need to be tested for vulnerabilities.
2. Vulnerability Matching
Nessus then analyzes the data collected during the discovery phase by comparing it against its extensive and frequently updated vulnerability database. This database contains thousands of known vulnerabilities, including software bugs, misconfigurations, and insecure protocols.
Nessus cross-references these vulnerabilities with details from the target systems, identifying specific security issues like outdated software, unpatched systems, open ports, and weak configurations. The tool automatically categorizes these issues based on severity, allowing security teams to quickly pinpoint critical vulnerabilities that need immediate attention.
3. Performing Vulnerability Tests
Nessus conducts thorough vulnerability testing by running a series of checks on the identified assets. It can perform credentialed scans, which involve authenticated access to systems for deeper inspection, or non-credentialed scans, which provide an outsider’s perspective.
During these tests, Nessus analyzes the environment for privilege escalation possibilities, patch management issues, weak configurations, and other security gaps. It simulates real-world attack scenarios to determine the risk exposure of each asset, providing detailed findings on any vulnerabilities that could potentially be exploited.
4. Active and Passive Scanning in Nessus
In Nessus, active scanning involves directly probing systems and networks to identify vulnerabilities. This type of scanning sends requests to target systems to detect open ports, services, and potential security issues. Active scanning can be resource-intensive but provides detailed results.
Passive scanning, on the other hand, listens to network traffic without interacting directly with the target systems. This technique identifies vulnerabilities based on observed traffic patterns, which reduces the risk of disruption but may miss some deeper security issues.
5. Generating Reports
Once Nessus completes the scanning process, it generates detailed reports containing all discovered vulnerabilities and their associated severity levels. Each vulnerability is documented with comprehensive information, including affected systems, potential impacts, and the urgency of remediation.
Nessus also provides actionable recommendations to resolve each issue, such as patching software, changing configurations, or strengthening access controls. Reports are customizable, allowing security teams to filter data based on criticality or asset type, and can be exported for sharing with stakeholders, ensuring efficient communication and prioritization of security efforts.
6. Prioritization and Remediation
Security teams review the detailed reports generated by Nessus to identify and prioritize high-risk vulnerabilities. Using the provided severity levels and risk assessments, they focus on addressing critical issues first to reduce the greatest security exposure.
Teams apply the recommended remediation steps, such as installing patches, updating software, and altering system configurations, to effectively secure assets. After remediation, they often conduct follow-up scans to verify that vulnerabilities have been successfully addressed and no new risks have been introduced. This cycle ensures continuous improvement in the security posture.
Setting up Nessus for Penetration Testing
Discover the essential steps to set up Nessus for effective penetration testing and enhance the organization's cybersecurity defenses.
Download and Install Nessus
To begin the setup, access the official Nessus website and choose the installer matching the operating system (Windows, Linux, or macOS). Download the file, then execute the installer, carefully following the installation steps provided. These steps include accepting the licensing agreements, setting the desired installation directory, and configuring basic settings like ports and paths. Ensure the system meets the necessary requirements for a smooth installation process.
Activate and Access the Web Interface
Once the installation is complete, access the Nessus interface through a web browser at https://localhost:8834. Upon first use, select the specific Nessus version (such as Essentials for basic use or Professional for advanced penetration testing), and enter the provided activation code to unlock features. The activation links your instance to your subscription, allowing full access to scanning capabilities and updates.
Configure Plugin Updates
After activation, immediately check for plugin updates by navigating to the settings in the Nessus web interface. Plugins are the scripts used to identify vulnerabilities during scans, and keeping them updated is essential for accurate detection. Choose to enable automatic updates to always have the latest security definitions or manually trigger updates before scans to ensure thorough assessments.
Create a New Scan Policy
Navigate to the “Policies” section in the Nessus dashboard to create a new scan policy. Define all relevant parameters, such as target IP ranges, network segments, or domains, and set the type of vulnerabilities you wish to detect. Customize scan settings like depth (full vs. quick scans), performance considerations, and authentication credentials. Use templates provided by Nessus or fully customize a policy based on specific needs.
Add Targets for Scanning
Add specific targets that need scanning by entering their IP addresses, hostname, network ranges, or domains into the target list. Create groups of assets based on criteria like system type, business criticality, or location. Prioritize high-risk assets to ensure the most critical systems are scanned first. Organizing targets efficiently helps streamline the scanning process and improves focus on essential security areas.
Schedule and Launch the Scan
Set the schedule for the scan based on organizational needs and network traffic considerations. Define the frequency for recurring scans, such as daily, weekly, or monthly, to maintain continuous security monitoring. Once the schedule is in place, launch the scan from the Nessus dashboard and monitor progress in real-time. Review any errors or issues that arise, and adjust the scan settings if necessary. Pause, resume, or stop the scan based on operational requirements.
Analyze and Act on Scan Results
Once the scan concludes, review the detailed report generated within the Nessus interface. The report contains a full list of detected vulnerabilities, categorized by severity level, and provides remediation recommendations. Use this data to prioritize which vulnerabilities to address first, focusing on high-risk issues. Follow the suggested remediation steps, such as applying patches, modifying configurations, or updating software to strengthen your security posture effectively.
Nessus Penetration Testing Best Practices
Implement these best practices to enhance your Nessus penetration testing and maximize its effectiveness in identifying and mitigating security vulnerabilities.
Keep Nessus Updated
Regularly update Nessus software and its vulnerability database to ensure accurate detection of the latest security threats. Staying current with updates improves scan effectiveness, as Nessus continuously adds new vulnerability checks and detection methods. This practice helps identify emerging risks early.
Use Credentialed Scans
Enable credentialed scanning by providing system access credentials to Nessus. This allows deeper insights into configurations, patches, and privilege issues that non-credentialed scans may miss. Credentialed scans can detect vulnerabilities hidden beneath application layers and offer more comprehensive testing.
Tailor Scanning Profiles
Customize scanning templates to match the organization's specific needs. Define the scope, depth, and focus of scans based on asset types and criticality. By tailoring these profiles, security engineers can ensure thorough coverage and more precise vulnerability detection across different environments.
Schedule Scans Regularly
Set up automated scans to run on a consistent schedule, such as weekly or monthly. Regular scanning helps catch vulnerabilities as they emerge and maintains continuous security monitoring. Scheduled scans can be timed to avoid network disruption, ensuring they run effectively without affecting operations.
Prioritize Vulnerabilities Wisely
Review the severity levels and potential impacts listed in Nessus reports to focus on high-risk vulnerabilities first. Addressing critical issues before less severe ones optimizes resource allocation and reduces the biggest threats quickly, enhancing overall security.
Integrate with Workflow Tools
Integrate Nessus with ticketing systems or other workflow tools for automated vulnerability management. This allows for easier tracking of remediation tasks, real-time updates on vulnerability status, and streamlined collaboration across security and IT teams to enhance efficiency.
Final Thoughts
Nessus offers a proactive, efficient, and comprehensive approach to penetration testing. Its detailed reporting and ease of use make it an essential tool for any organization looking to enhance its cybersecurity. As cyber threats continue to evolve, Nessus is poised to lead in innovative cybersecurity solutions, ensuring organizations stay ahead of potential risks and maintain robust security defenses.
While Nessus focuses on general vulnerability assessments across networks and systems, Akto is specifically built for API security, offering a more tailored approach for protecting APIs throughout their lifecycle. Akto’s continuous, real-time monitoring and automated testing help teams detect API-specific vulnerabilities, such as authentication flaws or data exposure risks, which Nessus might overlook.
Additionally, Akto offers features like API discovery, sensitive data detection, and alignment with OWASP Top 10 API vulnerabilities, enabling organizations to enhance both API security and development practices more effectively. Book your demo today to explore Akto’s benefits.
Explore more from Akto
Blog
Be updated about everything related to API Security, new API vulnerabilities, industry news and product updates.
Events
Browse and register for upcoming sessions or catch up on what you missed with exclusive recordings
CVE Database
Find out everything about latest API CVE in popular products
Test Library
Discover and find tests from Akto's 100+ API Security test library. Choose your template or add a new template to start your API Security testing.
Documentation
Check out Akto's product documentation for all information related to features and how to use them.

