External Pen Testing

Insha
Nov 8, 2024
External penetration testers probe an organization's systems from the outside to find vulnerabilities that hackers could exploit. Testers simulate real-world attacks by attempting to access networks, applications, and systems from outside the organization's environment. The goal is to identify weak points before attackers can exploit them.
This blog covers the importance, benefits, common vulnerabilities and process of external penetration testing, and best practices.
What is External Penetration Testing?
External penetration testing involves actively assessing an organization's external-facing systems and networks to uncover vulnerabilities that could be exploited by attackers. Security engineers, with the help of security teams, simulate real-world cyber attacks, probing web servers, applications, firewalls, and network devices to identify entry points and security flaws.
Techniques include reconnaissance, vulnerability scanning, and exploitation. The objective is to detect and remediate vulnerabilities before they are exploited, reducing the risk of unauthorized access, data breaches, and other security incidents.
Risks of Neglecting External Penetration Testing
Neglecting external penetration testing puts sensitive data at risk and weakens the organization's overall cybersecurity framework. It leaves systems vulnerable to malware, phishing, and DDoS attacks, which can cripple an organization’s operations.
Lack of testing can also lead to undetected backdoors that attackers can use for persistent access. Financial losses from a data breach, customer distrust, and damaged brand reputation can have long-term consequences. Furthermore, organizations risk falling behind on security best practices, making them easy targets for increasingly sophisticated cyberattacks.
Benefits of External Penetration Testing
External penetration testing offers several key benefits that strengthen an organization's cybersecurity posture. These benefits include:
Enhances Security From Threats
External penetration testing evaluates an organization's internet-facing systems, such as web servers, applications, and network devices. By simulating real-world cyberattacks from external sources, testers uncover vulnerabilities that could be exploited by outside attackers. This proactive approach helps secure external access points and prevents unauthorized entry into the network.
Identifies Security Vulnerabilities
External penetration testing actively identifies vulnerabilities in a system that may not be detected through internal reviews. Simulating real-world attacks uncovers weaknesses in the network, applications, and configurations. This proactive approach allows organizations to address security gaps before they can be exploited by malicious actors.
Enhances Incident Response Readiness
Conducting external penetration testing enhances an organization's ability to respond to security incidents. By exposing potential attack vectors, the test helps improve the incident response team's preparedness. This ensures quicker detection and mitigation of security breaches, reducing potential damage.
Meets Compliance Requirements
Many industries require regular external penetration testing to comply with regulatory standards. Organizations that conduct these tests demonstrate adherence to industry regulations, such as GDPR or PCI DSS. Organizations avoid penalties and ensure their security measures meet legal requirements by conducting these tests.
Protects Customer Data
External penetration testing helps protect sensitive customer data by identifying and fixing vulnerabilities that could lead to data breaches. By securing systems against unauthorized access, organizations build trust with customers and safeguard personal and financial information from cybercriminals.
Improves Security Posture
External penetration testing strengthens an organization's overall security posture. The test reveals areas that need improvement and provides actionable insights to bolster defenses. As a result, organizations can implement stronger security measures, making it more difficult for attackers to compromise their systems.
Common External Vulnerabilities
External penetration testing uncovers a range of common vulnerabilities that attackers frequently target. Let's explore some of the most prevalent external vulnerabilities:
Open Ports and Services
Attackers often exploit open ports and unsecured services to gain unauthorized access to a network. Attackers can exploit misconfigured or unmonitored ports to access sensitive systems. External penetration testing helps identify exposed ports and insecure services, enabling organizations to secure or restrict access to these potential vulnerabilities.
Insecure Web Applications
Web applications are frequent targets for attacks such as cross-site scripting (XSS), SQL injection, and cross-site request forgery (CSRF). Attackers can exploit vulnerabilities in these applications to cause data breaches, gain unauthorized access, or deface sites. External Pen-Testing helps find and address these issues to secure the application’s code and configurations.
Weak or Default Credentials
Using weak passwords or default login credentials makes systems highly susceptible to brute-force attacks. External testing attempts to exploit these weak authentication mechanisms to highlight the need for stronger password policies, multi-factor authentication, and regular credential updates.
Improper SSL/TLS Configuration
Secure Sockets Layer (SSL) and Transport Layer Security (TLS) protect data transmitted over networks. Improper configuration leaves data vulnerable to interception when organizations use outdated protocols or weak ciphers. External Penetration testing checks for these issues, ensuring secure communication between systems.
Unpatched Software and Vulnerable Versions
Attackers can exploit known vulnerabilities when organizations run outdated or unpatched software. Regular external penetration testing identifies any outdated software, libraries, or frameworks, emphasizing the importance of timely updates and security patches to mitigate these risks.
Misconfigured Firewalls and Security Controls
Firewalls and security controls play a critical role in restricting access to sensitive systems. Overly permissive rules or unmonitored exceptions in firewall and security control configurations lead to unintended access. External Penetration Testing evaluates these configurations to reinforce security and prevent external threats from bypassing controls.
DNS and Domain-Based Attacks
Domain Name System (DNS) vulnerabilities can lead to DNS spoofing, hijacking, and cache poisoning attacks, which allow attackers to redirect traffic or steal data. External penetration testing examines domain configurations, such as DNS records and zones, to detect weaknesses and secure the organization's domain against potential exploitation.
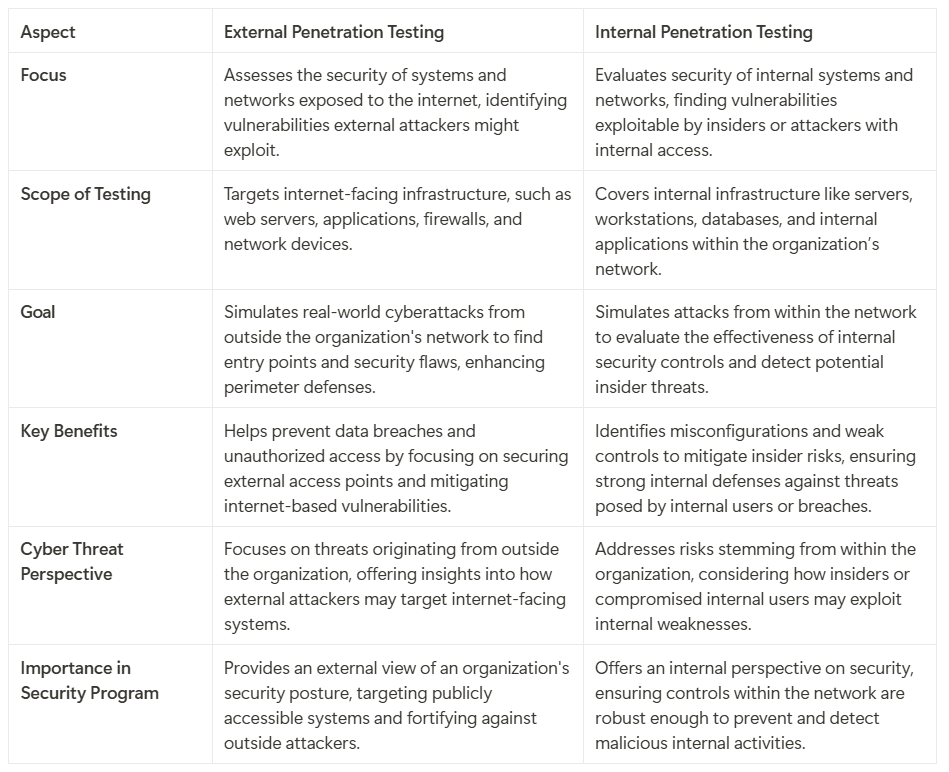
Internal Vs External Pentesting
External penetration testing and internal penetration testing, serve distinct purposes in evaluating an organization's security posture:
How to Perform External Penetration Testing?
Executing an external penetration test involves several crucial steps that security engineers must follow to comprehensively assess an organization's external defenses. These include:
1. Preparation
In the preparation phase, define the exact scope of the penetration test, outlining which systems, networks, and assets will be assessed. It's crucial to gather all necessary information about the organization’s external infrastructure, such as IP addresses, domain names, and publicly accessible services. Setting a clear scope helps testers focus their efforts and ensures the test covers all critical areas while avoiding unnecessary risks to the organizations.
2. Reconnaissance
Reconnaissance involves collecting as much information as possible about the target without actively engaging with it. Start with footprinting, using passive methods like DNS enumeration, WHOIS lookups, and search engine queries to gather external details about the organization.
Move on to active scanning with tools like Nmap, Masscan, or Shodan to identify live hosts, open ports, and active services. This phase actively prepares the groundwork for a deeper understanding of the target's environment.
3. Vulnerability Assessment
Once reconnaissance is complete, assess the target for vulnerabilities. Use automated tools like Nessus, OpenVAS, or Qualys to scan the systems and detect known vulnerabilities. Follow up with manual verification to validate the findings from these scans, ensuring they are accurate and relevant to the environment. This step is essential for identifying security weaknesses and reducing false positives.
4. Exploitation
In the exploitation phase, attempt to exploit identified vulnerabilities to gain unauthorized access or extract sensitive data. Testers use different exploit techniques to see if they can breach the target's defenses. If initial access is gained, the next step is privilege escalation—attempting to obtain higher access rights to critical systems, services, or data to deepen the level of compromise.
5. Post-Exploitation
After successful exploitation, focus on maintaining access and gathering further intelligence. Use lateral movement to explore the network, looking for additional targets and assets. Establish persistence by installing backdoors or creating rogue accounts to ensure that access can be maintained even after the system is rebooted or security measures are implemented.
6. Reporting
Document all findings from the penetration test in a detailed report. Include in the report each identified vulnerability, describe the methods and tools you used to exploit them, and provide recommendations for remediation. Additionally, prioritize vulnerabilities based on their severity and potential impact, helping the organization address the most critical issues first.
7. Remediation
Offer actionable recommendations to fix the identified vulnerabilities, which may include patching software, altering configurations, or implementing additional security controls. Collaborate with the organization’s IT to verify that remediation actions are applied effectively. Conduct follow-up assessments to confirm that vulnerabilities have been addressed and that no new issues have arisen.
Best Practices for External Penetration Testing
Implementing these best practices ensures robust and effective external penetration testing, enhancing an organization's security posture against potential threats.
Define a Clear Scope and Objectives
Before conducting external penetration testing, define the scope and set clear objectives. Identify which systems, networks, and applications are internet-facing and prioritize critical assets. Establish testing goals, such as finding vulnerabilities in web applications or network security, to ensure that testing efforts are focused and relevant to the organization’s needs.
Use a Mix of Automated and Manual Testing
Leverage both automated tools and manual techniques to uncover a wide range of vulnerabilities. Automated scanners can quickly identify common security issues, such as open ports or outdated software. However, manual testing is crucial for detecting complex flaws like logic errors, authentication issues, and other subtle weaknesses that automated tools may miss.
Simulate Realistic Attack Scenarios
Approach external penetration testing with the mindset of a malicious attacker. Simulate realistic attack scenarios, such as SQL injections, phishing attempts, or brute-force password attacks, to evaluate how the external defenses hold up. Test the effectiveness of security controls like firewalls, intrusion detection systems, and access controls to understand the organization’s readiness against actual threats.
Prioritize and Document Findings
After identifying vulnerabilities, prioritize them based on their potential impact and exploitability. Document the findings clearly, providing details on the risks, affected systems, and suggested remediation steps. A well-documented report enables the organization to efficiently address high-priority vulnerabilities and improve its overall security posture.
Final Thoughts
External penetration testing offers invaluable insights into an organization’s security posture against real-world threats. By simulating attacks on internet-facing systems and networks, security professionals can identify and exploit vulnerabilities before malicious actors do.
This proactive approach helps uncover critical weaknesses that might otherwise go unnoticed, ensuring timely remediation. Regular external testing enhances the organization’s defenses, fortifies perimeter security, and reduces the risk of unauthorized access or breaches.
Explore more from Akto
Blog
Be updated about everything related to API Security, new API vulnerabilities, industry news and product updates.
Events
Browse and register for upcoming sessions or catch up on what you missed with exclusive recordings
CVE Database
Find out everything about latest API CVE in popular products
Test Library
Discover and find tests from Akto's 100+ API Security test library. Choose your template or add a new template to start your API Security testing.
Documentation
Check out Akto's product documentation for all information related to features and how to use them.