Best Acunetix Alternatives and Competitors
Find the top Acunetix alternative in 2025 to improve your web application security and vulnerability scanning.

Kruti
Jan 23, 2025
Security teams must protect their sensitive data and APIs to prevent threats while following all the rules. As APIs grow, organizations need more effective solutions to find risks through features like anomaly detection, rate limiting, and automated vulnerability scanning.
Acunetix Security offers complete vulnerability scanning features. It helps organizations identify and reduce risks associated with APIs. It provides automated scanning, deep vulnerability reporting, and easy connection with CI/CD pipelines.
This blog explores the top Acunetix alternatives, analyzing their technical strengths, pricing models, and unique features, helping organizations find the right solution tailored to their security needs.
Top 10 Acunetix Competitors
Organizations should check these Acunetix alternatives and competitors, including their features and more, to find the right solution for their needs.
1. Akto
Akto is an API security platform focusing on automated discovery and complete testing and easily connects with modern CI/CD workflows. It performs regular API monitoring and vulnerability scanning and helps organizations secure their APIs, making it one of the best Acunetix alternatives.
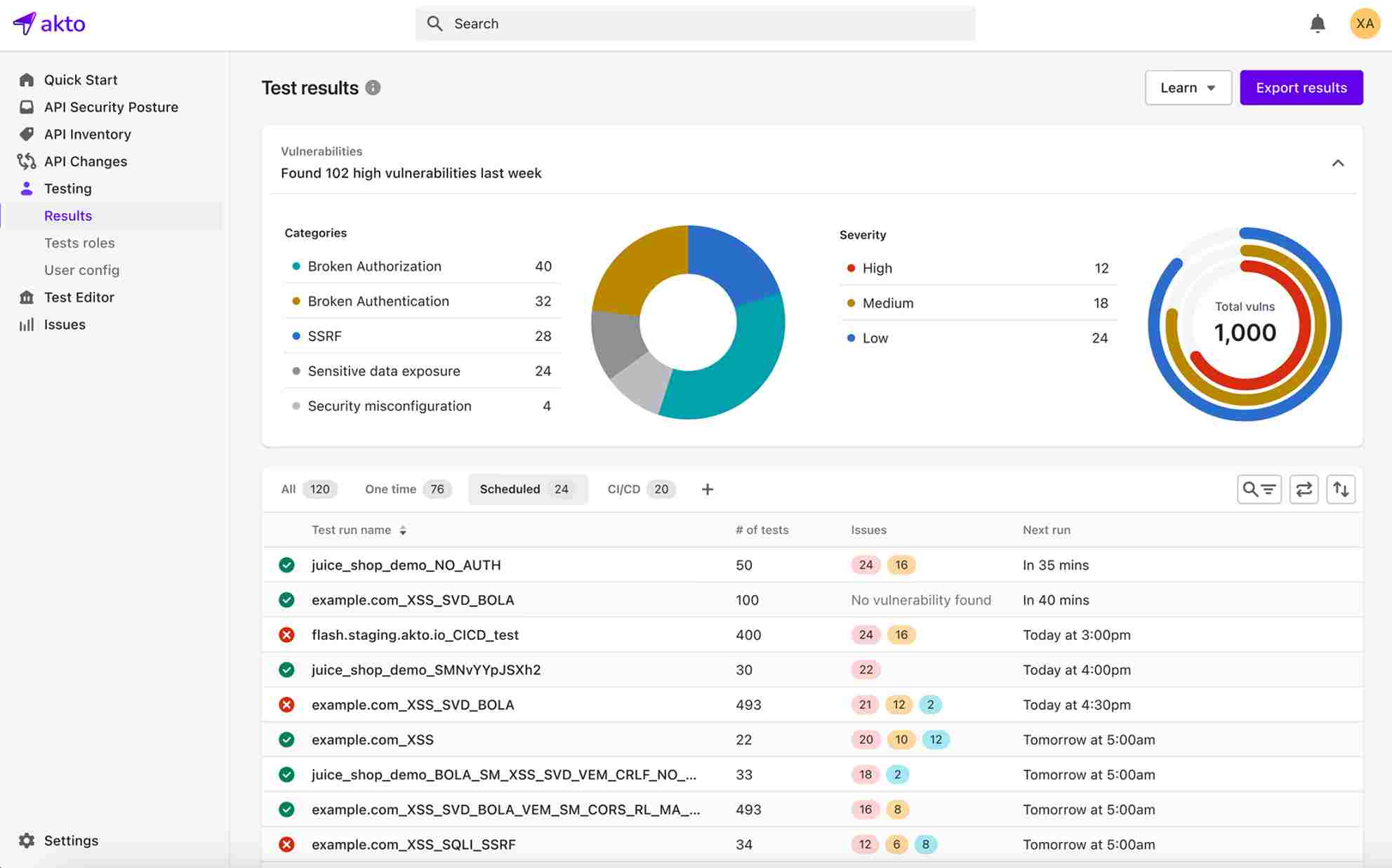
Features
Automatic API Discovery: Akto automatically finds and reduces APIs and covers all unsecured, internal, external, and third-party APIs.
Largest API Security Test Library: Akto offers one of the largest security test libraries for APIs, providing a myriad of pre-built tests that address critical vulnerabilities such as those in the OWASP API Security Top 10.
API Security Testing: Enables enterprises to run security tests based on threats in their API environment.
Connects easily CI/CD: Akto connects easily into DevOps pipelines and automates API security testing throughout the development cycle.
Protects Sensitive Data: Akto protects sensitive data by identifying it across APIs.
Advantages
Vast API test library with a wide range of pre-built tests.
Fast deployment and scalability across multi-cloud and hybrid environments.
Strong automation capabilities for continuous vulnerability scanning.
Customizable security tests and a deep focus on API security best practices.
Best For: Akto is ideal for organizations of all sizes with complex API infrastructures. It provides automatic testing features and connects easily with existing workflows. It is for organizations that use DevSecOps and have huge API environments.
2. Burp Suite
Burp Suite is a web application security testing platform known for its API security tests. It uses automation features with manual control and identifies weaknesses accurately.
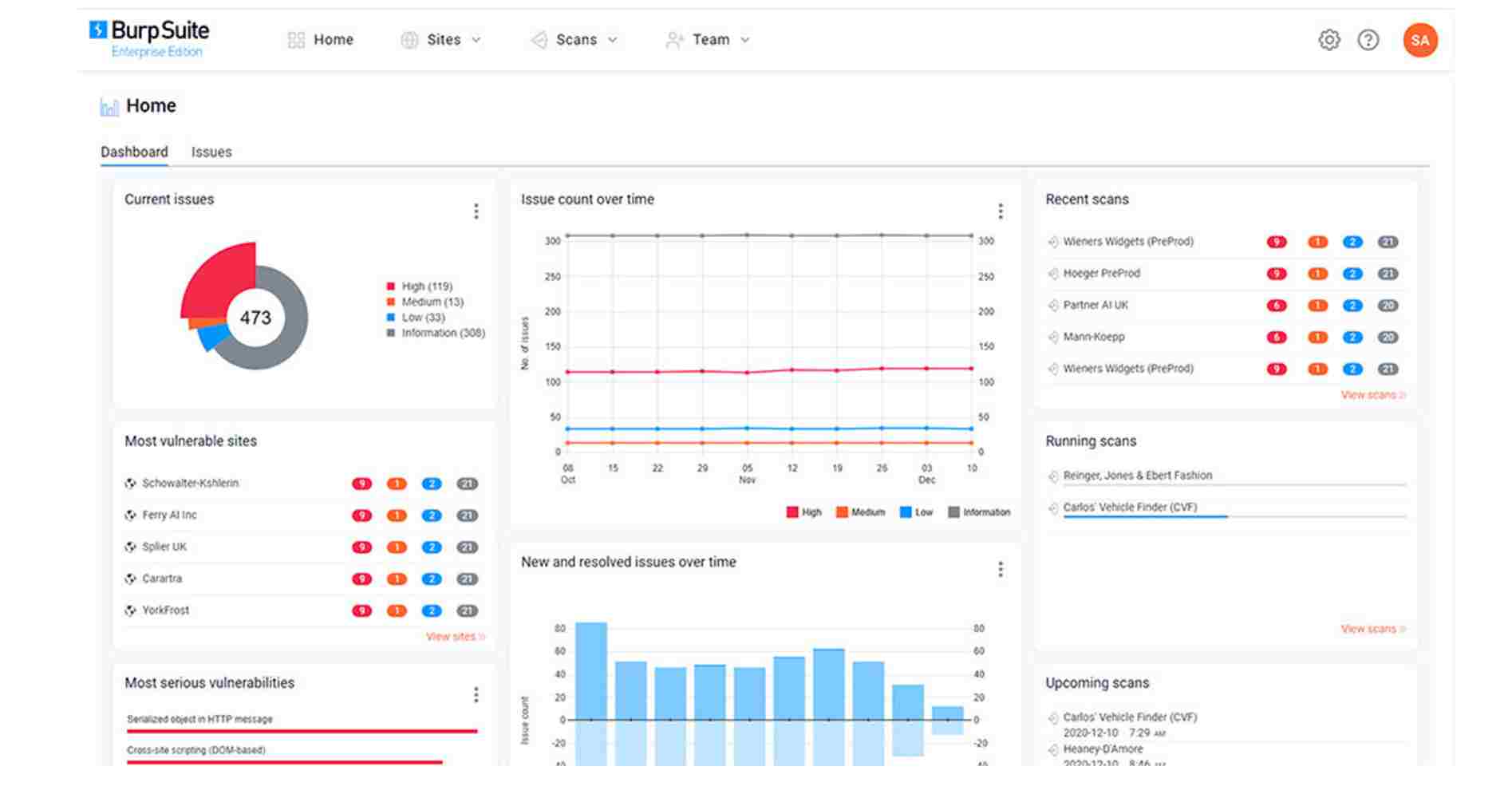
Source: Burp Suite
Features of Burp Suite
API-Related Testing: Perform deep analysis, authentication testing, and parameter-based vulnerability identification.
Customizable Scanning: Security teams can perform scans according to their specific API endpoints and attack surfaces.
Provides Extensions: Provides various add-ons for various API testing environments.
Advantages of Burp Suite
Offers unparalleled manual testing tools for precise exploitation and debugging.
It provides a flexible combination of automated and manual testing suitable for complex API infrastructures.
It has wide community support and is continuously enhanced with new features.
Disadvantages of Burp Suite
It is hard for beginners to understand, especially those who lack knowledge of pen testing.
The free version has fewer features, and the premium version might be expensive for small teams.
Best For: Burp Suite is for organizations that want to easily integrate API vulnerability testing into their workflows. It performs tests for small—to medium-sized organizations using automation and manual testing.
3. Checkmarx
Checkmarx is a full security platform that incorporates API security into the whole lifecycle of the development process. It helps to identify vulnerabilities in custom and third-party APIs. Scalable, it serves large organizations with solutions: with a shift-left approach, it enables early detection of vulnerability during development, enhancing security before deployment.
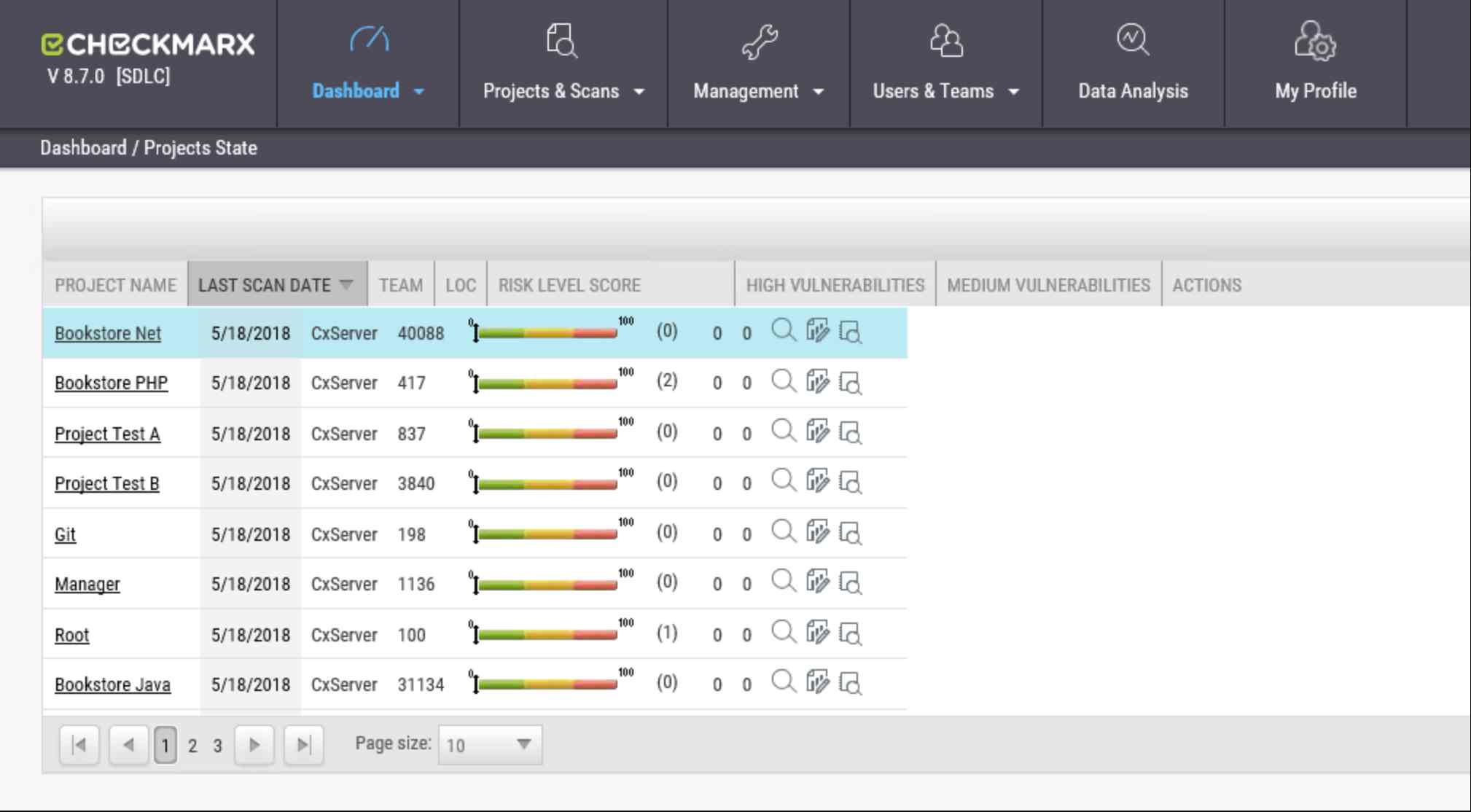
Source - Checkmarx
Features
SAST for APIs: In-depth static analysis of APIs to detect vulnerabilities early.
Real-time Monitoring: Continuous monitoring of API activity, alerting for threats and vulnerabilities.
Provide Adherence Support: Follow all adherence rules according to industry standards, like GDPR, HIPAA, and PCI-DSS.
Connects with DevSecOps: Easily connects into DevSecOps pipelines and performs automatic security testing.
Advantages of Checkmarx
Easily connects with DevSecOps and performs regular, automated API security scanning.
Flexible for organizations with large, complex environments.
Follows all rules like GDPR and HIPAA.
Disadvantages
It is more suitable for larger organizations with advanced API security needs.
Requires expertise to integrate and configure within an organization's existing workflows completely.
Best For: Checkmarx is for big organizations that need flexible API security solutions, regular monitoring, and strong regulatory adherence.
4. Detectify
Detectify is a security platform specializing in External Attack Surface Management (EASM) and Dynamic Application Security Testing (DAST). It has a global community of ethical hackers who find new vulnerabilities and updates its security test suite weekly.
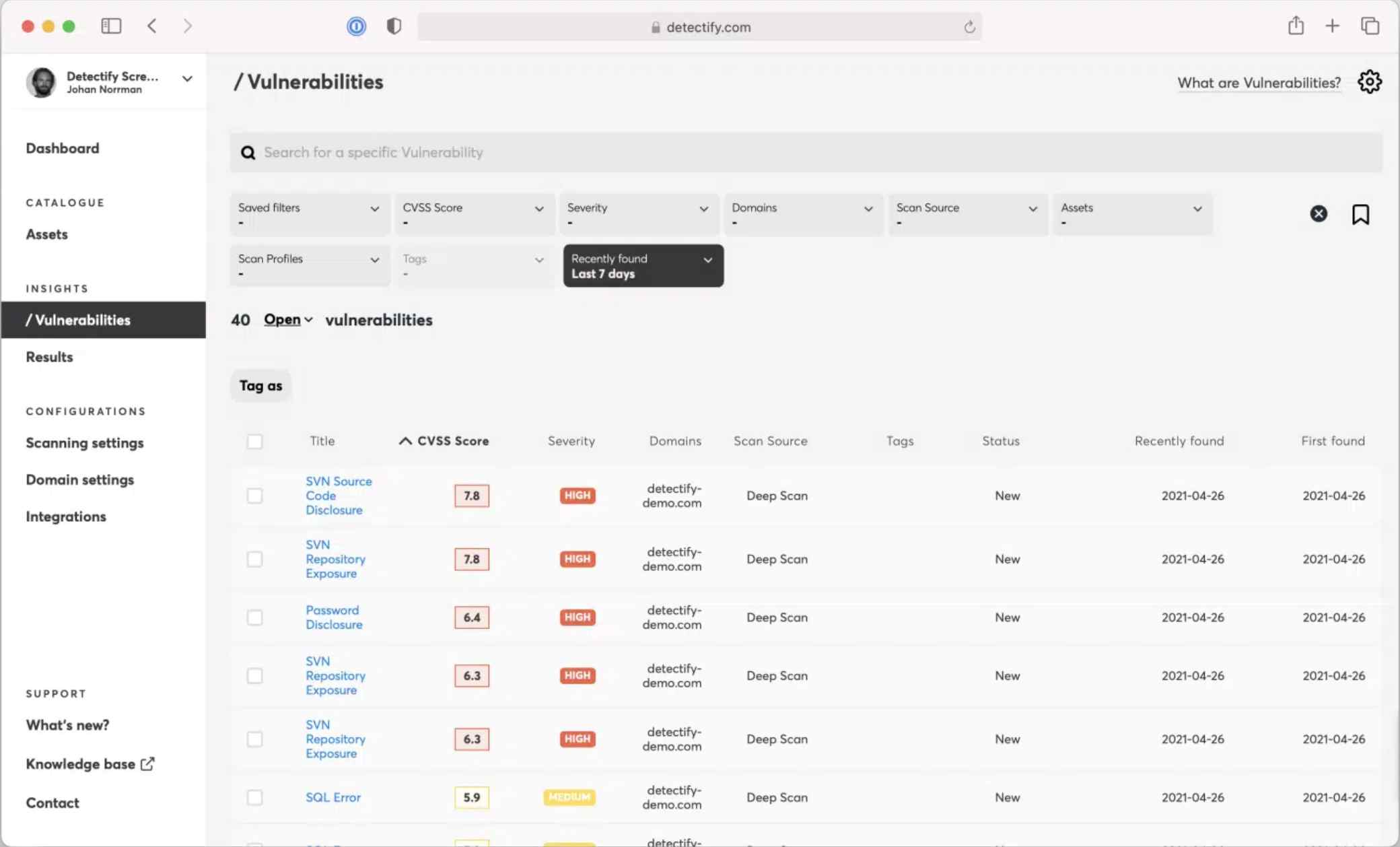
Source - Detectify
Features of Detectify
Complete Scanning: Provides a crawler that navigates web applications and finds vulnerabilities.
Fuzzing Engine: Advanced fuzz testing simulates creative attack scenarios to identify unexpected security flaws.
Fingerprinting Technology: Scans vulnerabilities based on the detected technologies and frameworks.
OWASP Top 10 Focus: Identifies risks beyond the OWASP Top 10, targeting obscure vulnerabilities.
Advantages of Detectify
Ethical hackers regularly update it for advanced threat detection.
Effective for complex applications with dynamic and JavaScript-heavy content.
Authenticated testing for deep tests of sensitive locations.
Connects easily with existing workflows.
Disadvantages of Detectify
Requires technical expertise to leverage its advanced features fully.
Limited static analysis capabilities compared to competitors.
Customization options in smaller plans may not match enterprise packages.
Best for: Detectify is for medium and big organizations that need API testing and monitor attack surfaces, especially those with complex application ecosystems.
5. Incapsula
Imperva develops Incapsula, which offers a powerful suite of web application and API security tools designed to protect websites, applications, and APIs from advanced threats. Its cloud-based platform emphasizes proactive threat prevention and real-time monitoring.
Source - Incapsula
Features of Incapsula
DDoS Protection: It provides protection against DDoS attacks, ensuring that the websites remain accessible even during API attacks.
Bot Detection: Incapsula uses advanced bot detection capabilities, differentiating between genuine users and automated threats.
Customized Security Rules: Using an easy GUI or syntax-based rule editor, organizations may customize security policies to meet their specific needs.
Proactive Zero-Day Protection: Regularly monitors suspicious activity and vulnerabilities to provide protection against threats.
Advantages of Incapsula
Complete coverage of different OWASP vulnerabilities.
Filters bot traffic to increase app performance.
Provides regular analysis and complete threat reports for quick incident response.
Provides managed services to simplify operations and reduce expenses.
Disadvantages of Incapsula
Installing Incapsula requires technical expertise and knowledge.
Potentially higher costs for premium features compared to competitors.
Limited connecting options for organizations with large environments.
Best For: Incapsula is for medium and big organizations looking for a complete application and API security platform that provides customization features and regular threat monitoring. It includes security features for industries like e-commerce, finance, and SaaS platforms.
6. Nessus
Nessus is widely acclaimed as the biggest vulnerability assessment solutions company. Tenable has owned it since 2002, when it purchased it. It includes scanning, checking, or measuring all types of IT res. The recent extension ensures coverage within modern web application security/API, including both dynamic application and API scanning.
Source - Nessus
Features of Nessus
Dynamic API Security Testing: Identifies vulnerabilities in APIs and custom application code, including OWASP Top 10 issues and misconfigurations.
Predefined Scan Templates: Simplifies the detection of SSL/TLS certificate issues and HTTP header misconfigurations, enhancing cyber security.
Accurate Coverage: Reduces false positives/negatives with in-depth scans across web application servers, frameworks, and JavaScript libraries.
Seamless Integration: Seamlessly integrates both on-premise and cloud environments. This means that, for instance, organizations can now scan environments without disrupting operations.
Advantages of Nessus
Provides one of the most accurate vulnerability assessments in the industry, minimizing false alerts.
Versatile support for traditional IT assets, external attack surfaces, and cloud infrastructures.
Provides templates for vulnerability scanning.
Disadvantages of Nessus
It lacks regular threat detection in contrast to other platforms
Proper expertise is needed to understand the results.
It may be costly for small organizations or startups.
Best For: Nessus is for organizations that need accurate, complete vulnerability tests for both traditional IT infrastructure and modern web applications. It is for medium and big organizations that have complex API environments.
7. OWASP ZAP (Zed Attack Proxy)
The OWASP Foundation developed OWASP ZAP as an open-source tool, and developers widely recognize it for security testing in web applications. It provides features to find APIs and their vulnerabilities during development for testing.
Source - OWASP ZAP
Features of OWASP ZAP
GraphQL and SOAP API Scanning: ZAP scans GraphQL APIs by parsing schema and Simple Object Access Protocol (SOAP) APIs by connecting WSDL files.
Dynamic and Passive Scanning: Provides active vulnerability scanning and passive detection methods to find security risks.
Deep Customization via Scripting: Supports Python and other scripting languages and customizes scans and tests.
ZAP Marketplace Extensions: The ZAP marketplace offers a variety of plugins and extensions to use with API testing products.
Advantages of OWASP ZAP
Free and open with no licensing costs.
The OWASP community regularly updates to find new threats.
Complete documentation and strong community support for troubleshooting.
Easily connects with CI/CD pipelines for automated API security checks.
Disadvantages of OWASP ZAP
Initial setup and configuration can be a little challenging for beginners.
It lacks some reporting tools, unlike other platforms
Regular scans can take longer for larger applications.
Best for: OWASP ZAP is for developers and small and mid-sized organizations looking for a free and robust API security testing solution.
8. Pentest-Tools
Source - Pentest tools
Pentest-Tools is a web-based cloud platform that performs pen testing and scans for vulnerabilities more efficiently. It is famously user-friendly and offers automated, customizable tools for both technical and non-technical users.
Features of Pentest-Tools
Modular Scanning Toolkit: This toolkit includes API scanners, XSS scanners, SQL injection exploiters, and network vulnerability tools for pinpointing complex issues.
Attack Surface Dashboard: Automatically identifies and organizes risks and provides actionable reports.
Pentest Robots: Customizable, drag-and-drop automation sequences to create workflows for repetitive tests.
Handles False Positive: Have a dedicated response team to verify and reduce false positives, improving scanner accuracy.
Advantages of Pentest-Tools
Easy platform with templates for rapid setup and scanning.
Performs automated scans with deep manual testing workflows.
Provides deep reports for professional use.
Regular updates with new vulnerability definitions and guides for remediation.
Disadvantages of Pentest-Tools
Limited to cloud-based operations, which may concern high-security environments.
Advanced features may be hard to understand.
It slows down and affects performance in large environments.
Best For: Pentest Tools is for small and medium-sized organizations that want flexible tools with comprehensive reporting features.
9. Veracode
Veracode is a security tool that helps security teams identify vulnerabilities in APIs and applications throughout the software development lifecycle. Organizations use it because of its integration features and focus on automatic security processes.
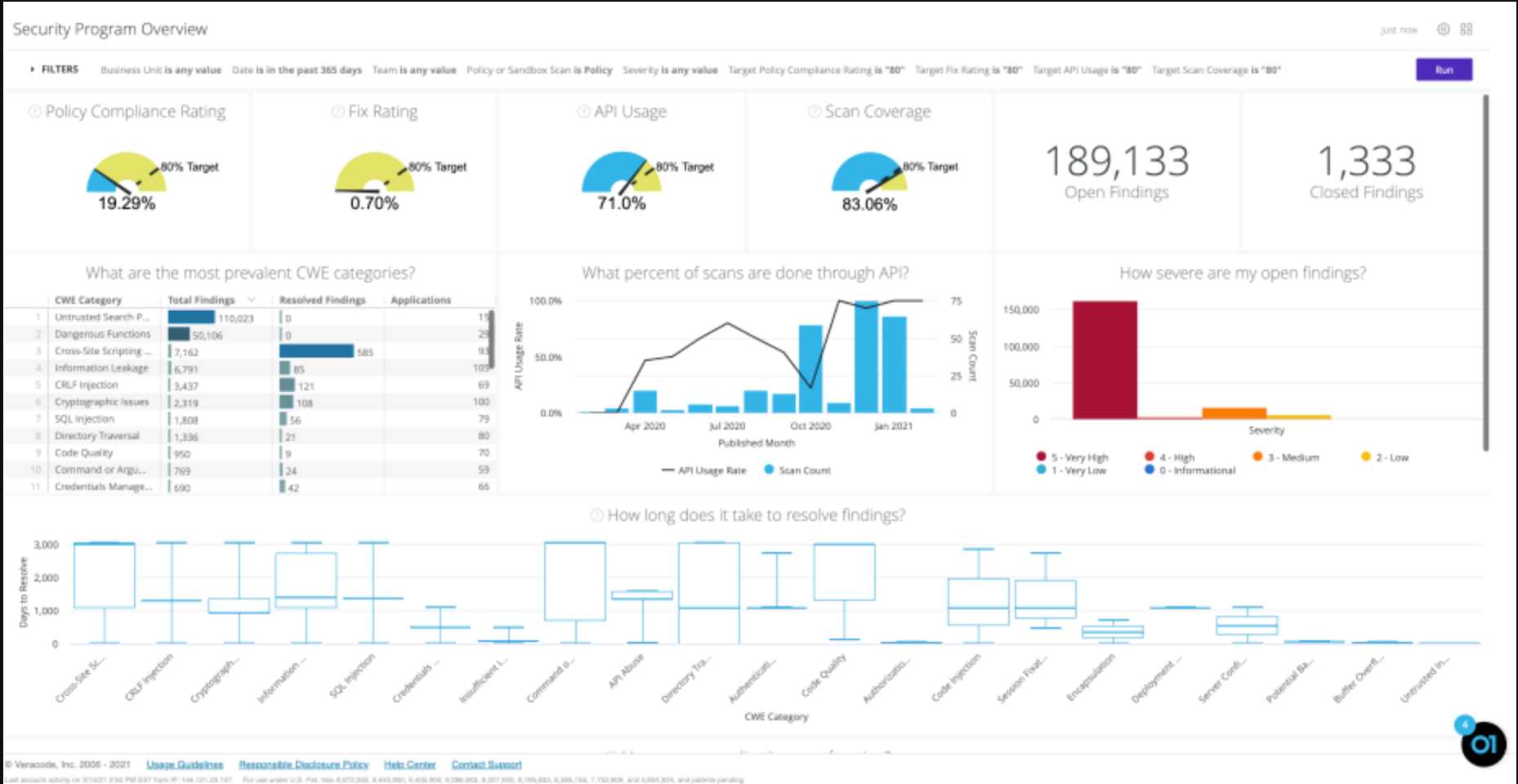
Source - Veracode
Features of Veracode
Runtime API Scanning: Veracode has advanced runtime API scanning that scans for vulnerabilities in production-like environments, allowing for proactive remediation.
Dynamic Analysis: Specializes in detecting access control flaws and runtime vulnerabilities, particularly focusing on OWASP API Security risks like broken object-level and function-level authorization.
Customizable Reporting: Provides detailed security insights tailored to specific development teams, fostering collaboration between security and development units.
Wide Language and Framework Support: It can scan more than 50 languages and frameworks, making it versatile for API and app security needs.
Advantages of Veracode
Deep runtime vulnerability detection to improve pre-deployment security.
Easily connects with CI/CD pipelines for DevSecOps workflows.
Deep and customizable security reporting promotes effective collaboration.
Complete OWASP API risk coverage ensures high-level threat mitigation.
Disadvantages of Veracode
Setup and initial configurations can take time.
It needs expertise to perform advanced dynamic analysis.
Expensive pricing which might not be for smaller organizations.
Best For: Veracode is best for medium-sized and big organizations that follow strict compliance requirements. It is for organizations that want integrated, automated security testing across extensive development pipelines.
10. Qualys
Qualys is a comprehensive cloud-based security platform that supports vulnerability management and API security. It provides wide-reaching tools to a security engineer so that it can scan, detect, and correct vulnerabilities for the APIs, web applications, as well as in enterprise systems without violating a different industry's requirement.
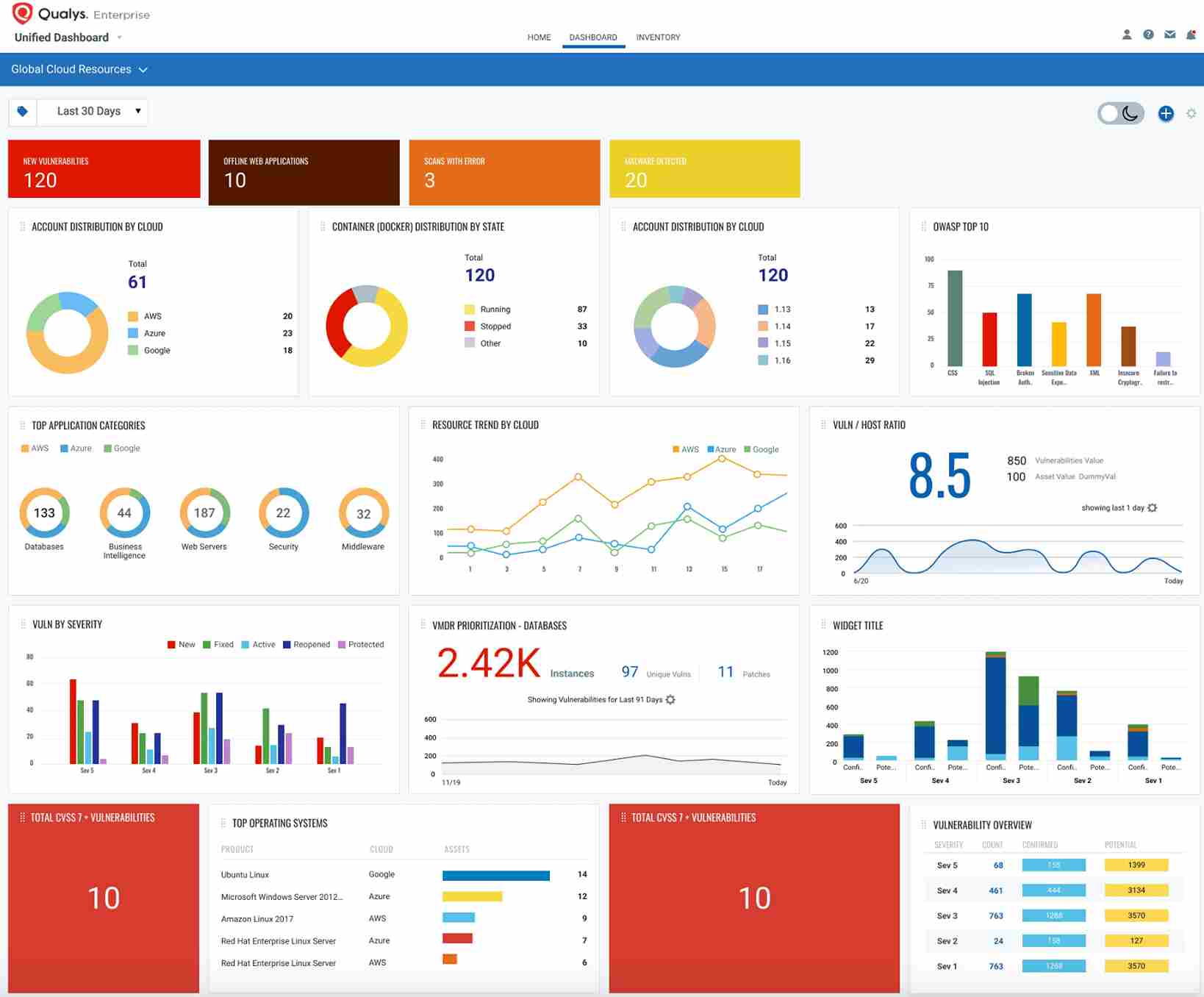
Source - Qualys
Features of Qualys
API Security and Adherence Monitoring: Qualys performs API scans to detect vulnerabilities with compliance checks.
Asset Management: Automatically identifies and tracks API assets, providing a clear view of external and internal attack surfaces.
Vulnerability Management and Detection (VMDR): Enables continuous vulnerability assessment, prioritization, and remediation for APIs, applications, and infrastructure in real time.
Risk-based Prioritization: Provides automatic prioritization of vulnerabilities based on risk level.
Advantages of Qualys
Complete coverage of API security with automated scanning and regular risk tests.
The platform connects with vulnerability management and compliance tools like VMDR.
Advanced AI-driven scanning capabilities improve detection accuracy and reduce manual workload.
Scalable for large organizations with complex multi-cloud environments and external attack surface management.
Disadvantages of Qualys
The platform may require initial configuration and integration for optimal use, especially for API scanning.
Advanced features such as TruRisk Management have higher licensing costs
Some tools needed by small businesses are missing.
Best For: This is best for large organizations that require a security platform with complete vulnerability management, API security, and adherence to rule requirements.
How to Choose the Best API Security Solution
The choice of API security solution is essential to protect sensitive data while following compliance rules.
Assessing API Security Needs
Evaluating API security requires organizations to know their business size, API complexity, and regulatory compliance. API complexity impacts security needs, and internal APIs may need basic tools to stop unauthorized access. Public APIs need solutions like regular monitoring, rate limiting, and abnormality detection to address cyber threats.
Small organizations can benefit from affordable, pre-configured tools. Mid-sized organizations may need flexible platforms for enhanced threat detection and customizable configurations. Large organizations will need AI-driven solutions, regular threat intelligence, and easy connections with advanced tools.
Other types of compliance are strictly enforced in various sectors, especially for finance, healthcare, and e-commerce companies, which have to maintain standards on compliance with standards like GDPR, HIPAA, and PCI DSS, will require platforms offering data encryption, audit logs, and compliance reporting features.
Check Features
Choose an API security platform based on the features that suit your needs. Automated security testing ensures no applications are left vulnerable. Strong API solutions should be able to grow with the organization while keeping the needed flexibility and security.
It should be easy and developer-friendly and follow compliance support. Securing shadow APIs is vital for organizations with dynamic architectures. Akto’s ability to detect and test shadow APIs makes it a strong choice for managing complex ecosystems.
Pricing Concerns
The cost of API security solutions changes based on factors such as the size of the organization, volume of traffic, and feature requirements. Smaller organizations should look for affordable solutions that provide essential protections without excessive complexity. Mid-sized organizations may need scalable, flexible options that grow with their API infrastructure.
Organizations should also assess their budget against the value offered by a platform’s features, such as automated workflows, compliance tools, and developer-friendly interfaces. Many platforms offer free trials for organizations to test their solutions.
Final Thoughts
API security is essential to provide protection for sensitive data, follow adherence rules, and ensure operation stability. Acunetix is a strong vulnerability scanning and API security testing tool but it may not match the needs of some organizations.
Checking other alternatives will help organizations find a specific solution to a specific need. Organizations looking for simplicity, automation, and real-time visibility of their APIs will find Akto to be an excellent choice.
Developer-friendly tools, very powerful API discovery features, smooth CI/CD integration, and real-time monitoring make Akto an ideal fit for any modern, fast-paced organization. Book your demo today and learn how Akto can meet an organization's API security needs.
