Invicti DAST: Configuring a Scan and How Scanning Works in Invicti DAST
Invicti DAST is a tool designed to identify security vulnerabilities in websites and web applications by simulating real-world attacks.

Muze
Jul 11, 2024
Invicti DAST (Dynamic Application Security Testing) is a robust security tool that helps keep websites and web applications safe by identifying vulnerabilities attackers could exploit.
Invicti simulates real-world attack scenarios, mimicking the behavior of a hacker to uncover weaknesses in the application’s security posture. Known for its automation capabilities, Invicti DAST efficiently scans and tests applications, providing detailed insights and remediation steps.
In this blog, you will learn what Invicti DAST is, how to configure a scan, how to perform Invicti DAST scanning, how the discovery feature works, the limitations of Invicti DAST, and its alternatives.
Let’s get started
What is Invicti DAST?

Invicti DAST, short for Dynamic Application Security Testing, is a robust enterprise-level web application security scanner integrated into the Software Development Life Cycle (SDLC). It combines DAST, IAST (Interactive Application Security Testing), and SCA (Software Composition Analysis) to pinpoint security issues such as SQL Injections and Cross-site Scripting (XSS) across websites and APIs.
It helps streamline vulnerability management and resolution with its seamless integration and automation with Jira and Slack. It also provides different versions, such as Invicti Standard for simple scanning and Invicti Enterprise for scanning more than 50 targets, as it focuses on continuous improvement to guarantee precision, range, and speed.
With a focus on comprehensive automation and workflow integration, Invicti aims to enhance website and web application security effectively and efficiently.
Is Invicti DAST or SAST?
Invicti DAST is a DAST tool that tests live applications by mimicking real-world attacks to find security weaknesses. It does not analyze source code like SAST tools do. Invicti DAST focuses on dynamic application security testing (DAST). This approach helps to identify security issues in the application's behavior and interactions.
On the other hand, SAST (Static Application Security Testing) tools analyze the source code to find vulnerabilities before running the application. They help identify issues in the code itself.
How Does Invicti DAST Scanning Work?
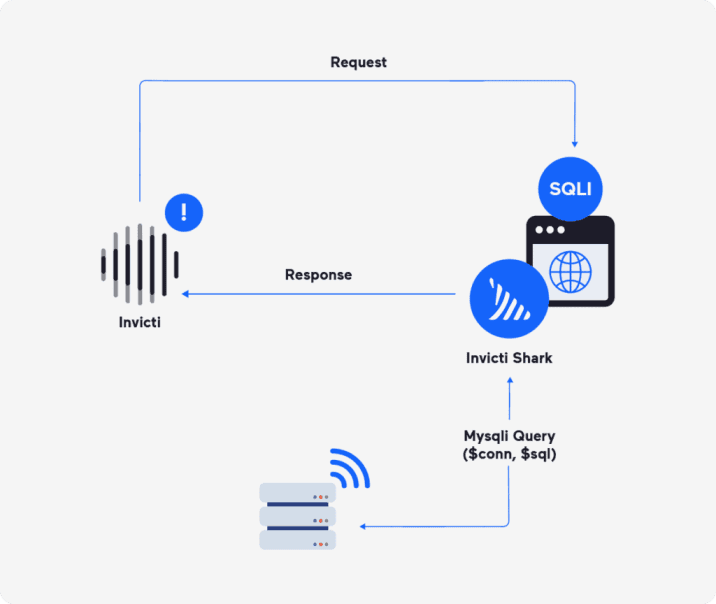
Invicti DAST scanning operates by simulating hacker actions to uncover vulnerabilities in web applications. Combining DAST, IAST, and SCA, it inspects websites and APIs for security issues like SQL Injections and XSS.
By using a real browser engine, Invicti ensures accurate testing of complex web applications with multiple layers of frameworks. The scanning involves configuring settings, selecting URLs, choosing profiles, and customizing policies for effective vulnerability identification.
It adapts tosingle-page application, handles authentication forms, and can crawl up to 15,000 pages. It focuses on automation, accuracy, and continuous innovation to ensure comprehensive coverage and efficient DevSecOps processes.
Invicti DAST utilizes advanced vulnerability scanning techniques and integration capabilities to deliver comprehensive security testing for web applications. It integrates security testing into the development lifecycle and adopts a shift-left approach, conducting testing as early as possible to eliminate vulnerabilities in the initial stages.
How to Configure a Scan in Invicti DAST?
Configuring a scan in Invicti DAST is a straightforward process. Follow these steps:
Log in: Start by logging into your Invicti DAST account.
Navigate to Scans: Go to the 'Scans' section in the dashboard.
Initiate a New Scan: Click 'New Scan' to begin the configuration process.
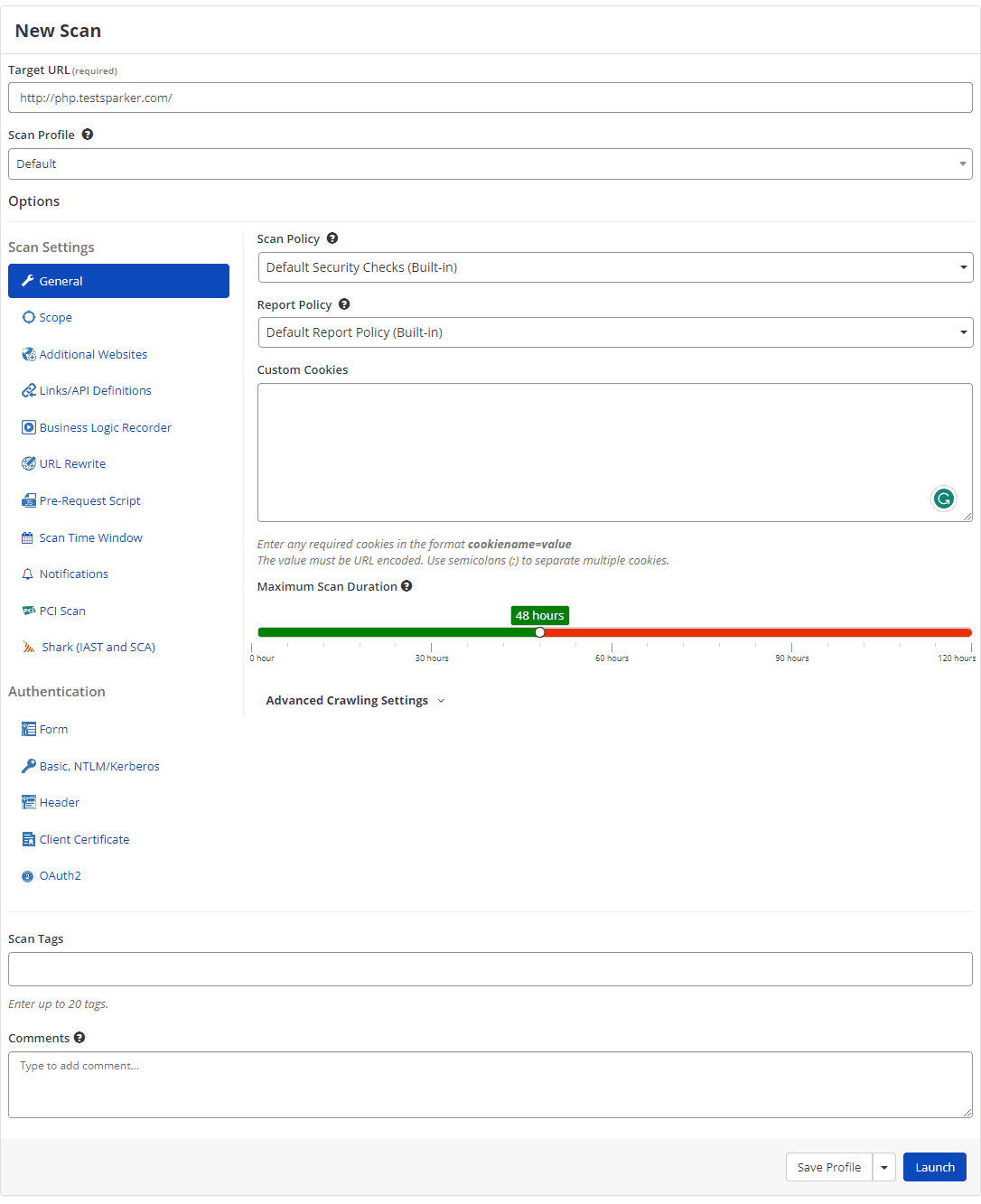
Enter URL: Provide the URL of the website or web application you want to scan.
Select Scan Profile: Choose a scan profile that suits your needs. Scan profiles define the type of tests and depth of analysis for the scan.
Customize Scan Policy: If needed, customize the scan policy to adjust settings for specific checks and technologies or to include/exclude certain tests.
Set Authentication (Optional): If your website requires authentication, configure the authentication settings to ensure the scanner can access all parts of your site.
Schedule (Optional): You should also schedule the scan at a specific time or set it to run periodically.
Start Scan: Once you have set everything up, click 'Start Scan' to begin scanning.
These steps will help you efficiently configure and start a scan in Invicti DAST. For more detailed instructions, including advanced configurations and troubleshooting, refer to the Invicti DAST documentation or support resources.
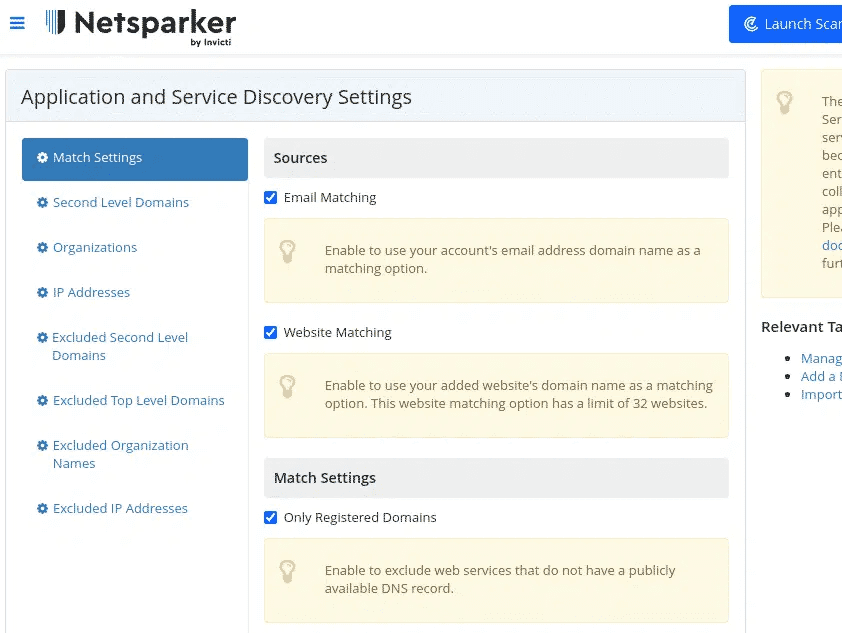
How Does the Discovery Feature Work?
The Discovery feature in Invicti DAST plays a crucial role in identifying potential security vulnerabilities in web applications. It does this by first mapping out the structure of the web application. This includes all the pages, inputs, and other elements that a user or a hacker might interact with.
Once it has a comprehensive picture of the application's structure, it then uses this map to guide its testing. It tries different inputs and behaviors to determine if they can trigger security weaknesses.
The Discovery feature is highly automated, enabling it to work quickly and efficiently. It's also smart enough to handle complex web applications, including modern technologies such as single-page applications.
It is important to note that the Discovery feature isn't just about finding vulnerabilities. It also aims to understand the structure of the application so that it can fix these vulnerabilities as effectively as possible.
Limitations of Invicti DAST
While Invicti DAST is a robust and comprehensive tool, it has a few limitations that users should be aware of:
Application-Specific: Invicti DAST primarily focuses on web application vulnerabilities. Another security testing tool might be more suitable for other types of applications, such as desktop or mobile apps.
Limited Integration: Invicti DAST integrates with some development tools, but it might not be compatible with every tool your team uses. Ensure compatibility with your current development environment before opting for Invicti DAST.
Struggles with Complex Applications: Invicti DAST can encounter difficulties with complex, single-page applications and newer technologies, which can cause it to miss vulnerabilities. Experts recommend using additional testing methods for these types of applications.
Cost Prohibitive: Smaller organizations may find the cost of Invicti DAST to be a barrier. Consider your budget and the tool's cost-effectiveness in relation to your specific needs.
Complexity: Beginners in security testing might find Invicti DAST too complex. They need adequate training or guidance to fully utilize its features.
Requires Manual Intervention: Invicti DAST requires users to confirm some vulnerabilities manually despite its automation capabilities. This can be time-consuming and may slow down the testing process.
What are the Alternatives to Invicti DAST?
Invicti DAST alternatives include various tools that offer dynamic application security testing (DAST) capabilities. Here are the alternatives:
1. Akto
Akto is a proactive API security platform providing comprehensive API security testing. While Invicti DAST focuses on web applications, Akto specializes in API security testing with a robust testing library and supports Dynamic Application Security Testing (DAST). This specialization makes it a strong alternative to Invicti DAST, especially for organizations prioritizing API security and seamless integration into development workflows.

2. Acunetix by Invicti
Acunetix specializes in automated web application security testing with advanced vulnerability detection, dynamic scanning, and seamless integration with CI/CD pipelines. Its ability to handle modern single-page applications (SPAs) and its Proof-Based Scanning™ technology distinguishes it from Invicti DAST.
This makes Acunetix particularly suitable for organizations seeking comprehensive, automated security testing solutions that integrate deeply into their development workflows and efficiently validate vulnerabilities.

3. OWASP Zed Attack Proxy (ZAP)
The open-source DAST tool, widely recognized for its manual penetration testing capabilities and customizable security assessments, distinguishes itself from Invicti DAST through ZAP’s flexibility and extensive community-supported plugins. This positions ZAP as the ideal choice for organizations and security professionals needing a versatile, cost-effective tool capable of tailoring testing procedures to specific security needs and innovating through community-driven enhancements.

Final Thoughts
Invicti DAST is a formidable tool in web application security, leveraging a blend of DAST, IAST, and SCA technologies to detect and mitigate vulnerabilities like SQL Injections and XSS efficiently. Its robust automation capabilities and seamless integration with popular SDLC tools enhance operational efficiency, streamlining the identification and resolution of security issues.
In contrast, Akto emerges as a compelling alternative with its specialized focus on dynamic and proactive API security testing capabilities. This ensures thorough vulnerability assessments throughout the development lifecycle, empowering organizations to proactively strengthen their defenses against evolving cyber threats. By choosing Akto, businesses can take a proactive security stance, effectively mitigating risks and confidently safeguarding their applications in today's dynamic digital world.
Important Links
Keep reading
API Security
8 minutes
NIST Cybersecurity Framework
The NIST Cybersecurity framework provides organizations with a set of standards, guidelines, and practices to develop strong cybersecurity practices for managing cybersecurity risks effectively.
API Security
7 minutes
API Security Audit
An API Security Audit evaluates APIs, identifies potential risks, and strengthens the organization's defenses against security breaches and cyber-attacks.
API Security
8 minutes
Security Information and Event Management (SIEM)
SIEM aggregates and analyzes security data across an organization to detect, monitor, and respond to potential threats in real time.
Experience enterprise-grade API Security solution



