OWASP Risk Rating Methodology
The OWASP Risk Rating Methodology assigns a rating to the identified risks by considering the likelihood of the risk and its potential impact on the organization.

Muze
Aug 1, 2024
The Open Web Application Security Project, or OWASP, developed the OWASP risk rating methodology. This methodology addresses critical vulnerabilities with high system impact, such as SQL injection and XSS (Cross-Site Scripting). OWASP offers open-source tools that help organizations implement this risk rating methodology, including testing, assessment, and scanning functionalities.
In this blog, we'll discuss the OWASP risk rating methodology, its importance, criteria, benefits, an example of calculating risk, and how to implement it. Let’s dive in!
What is OWASP Risk Rating Methodology?
The OWASP Risk Rating Methodology identifies and prioritizes security risks in software applications. First, it identifies potential risks within a software application. Hackers might exploit these risks to cause harm to the software.
Then, it assigns each risk a number or a rating. This rating considers factors such as the likelihood of the risk and its potential impact. Dealing with the highest-rated risks is the top priority. This way, the most serious potential problems are addressed before the lesser ones.
Organizations can customize the OWASP Risk Rating Methodology to fit their specific needs, making it a valuable tool in cybersecurity.

Importance of OWASP Risk Rating Methodology
For any software application to run smoothly, it is essential to identify vulnerabilities and risks. Different vulnerabilities pose different types of risks. Rating these risks can help identify their impact on the system. With a rating system, you can save time arguing about priorities.
Organizations should ignore minor risks and deal with more serious risks first. This framework's best feature is that it can be customized for each business, as a crucial risk may not be important for another.
What are OWASP Risk Rating Methodology Criteria?
OWASP designed the risk rating criteria for their methodology to assess and prioritize security risks in software applications systematically. These criteria include:
1. Threat Agent Factors
These are characteristics of the person or thing that might take advantage of a weakness. This includes their skill level, motivation, how many of them there are, and if they happen upon the weakness or are actively looking for it.
2. Vulnerability Factors
These consider how an attacker might exploit a weakness, including how easy it is to find, how simple it is to exploit if known, and whether the system can detect the attack.
3. Impact Factors
These determine what will happen if a threat agent takes advantage of a weakness. This includes technical impacts (loss of secrecy, accuracy, availability, and responsibility) and business impacts (money loss, reputation damage, rule violations, and privacy breaches).
4. Security Controls
This measures the quality of current security measures. It includes measures to prevent, detect, and respond to risks and how these measures manage the identified risks.
Implementation Process of OWASP Risk Rating Methodology
The OWASP risk rating methodology follows a systematic process. There are the following steps in the implementation process of the OWASP risk rating methodology:
1. Identify Assets
First, identify important assets in the system or application. These assets may include critical functions, sensitive data, intellectual property, etc. This approach helps concentrate efforts on protecting critical and valuable assets.
2. Identify Risks
The second step is to find potential risks or threats to the system. It includes identifying attack vectors, vulnerabilities, security weaknesses, etc. Penetration testing, threat modeling, code reviews, or vulnerability scanning can identify these.
3. Estimate Likelihood
Organizations must estimate the likelihood or probability of each risk by understanding the effectiveness of current security controls in the system. Risk likelihood also depends on risk complexity or whether exploiting the risk is easy or difficult. It also depends on the ease of risk discovery and the skill level of attackers.
4. Estimate Impact
Organizations must assess the impact of risk by considering the potential consequences after exploiting the risk. If we realize the risk, would it result in financial damage, loss of integrity, privacy violation, etc.? These questions can help organizations estimate the impact of the risk.
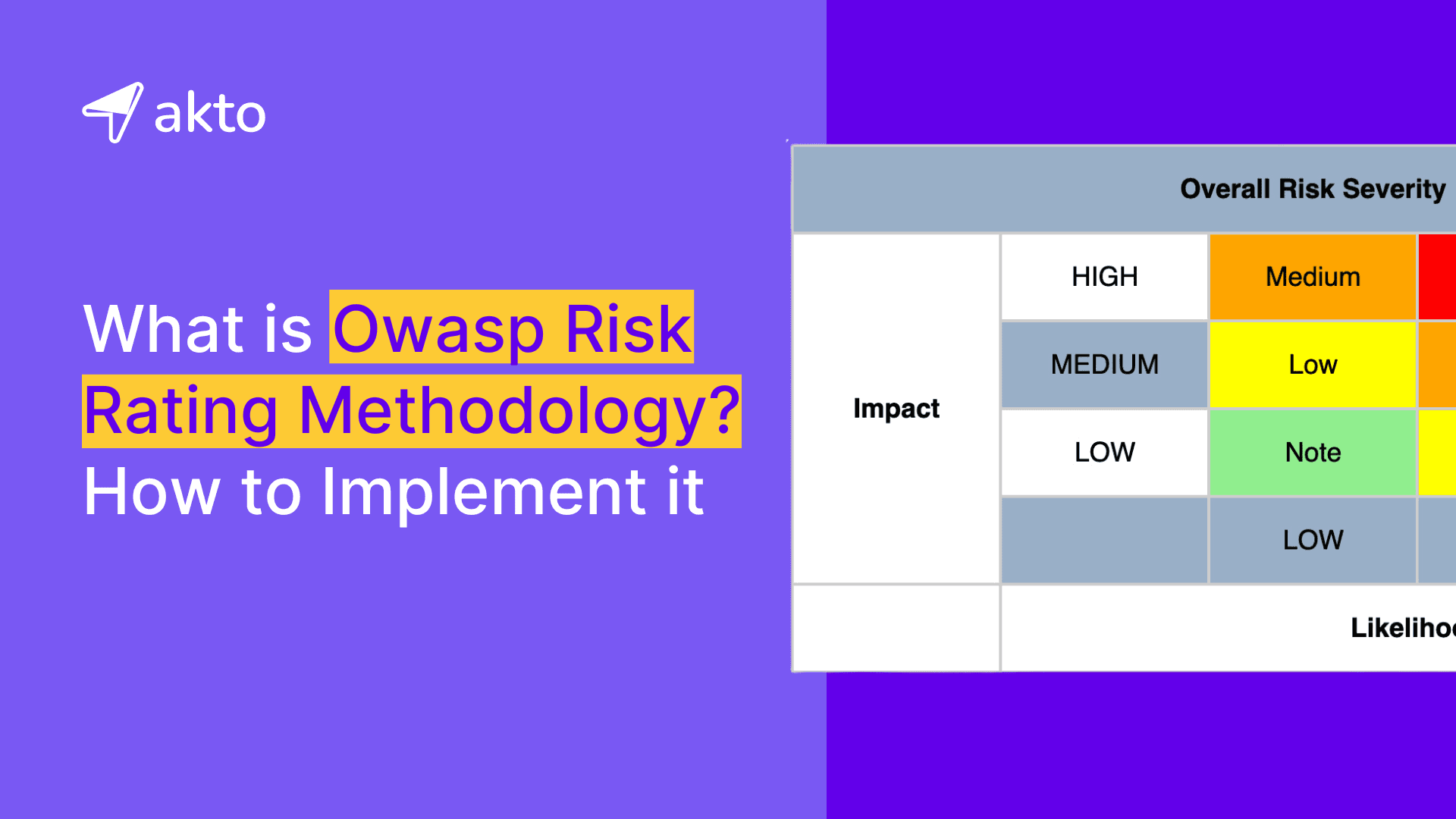
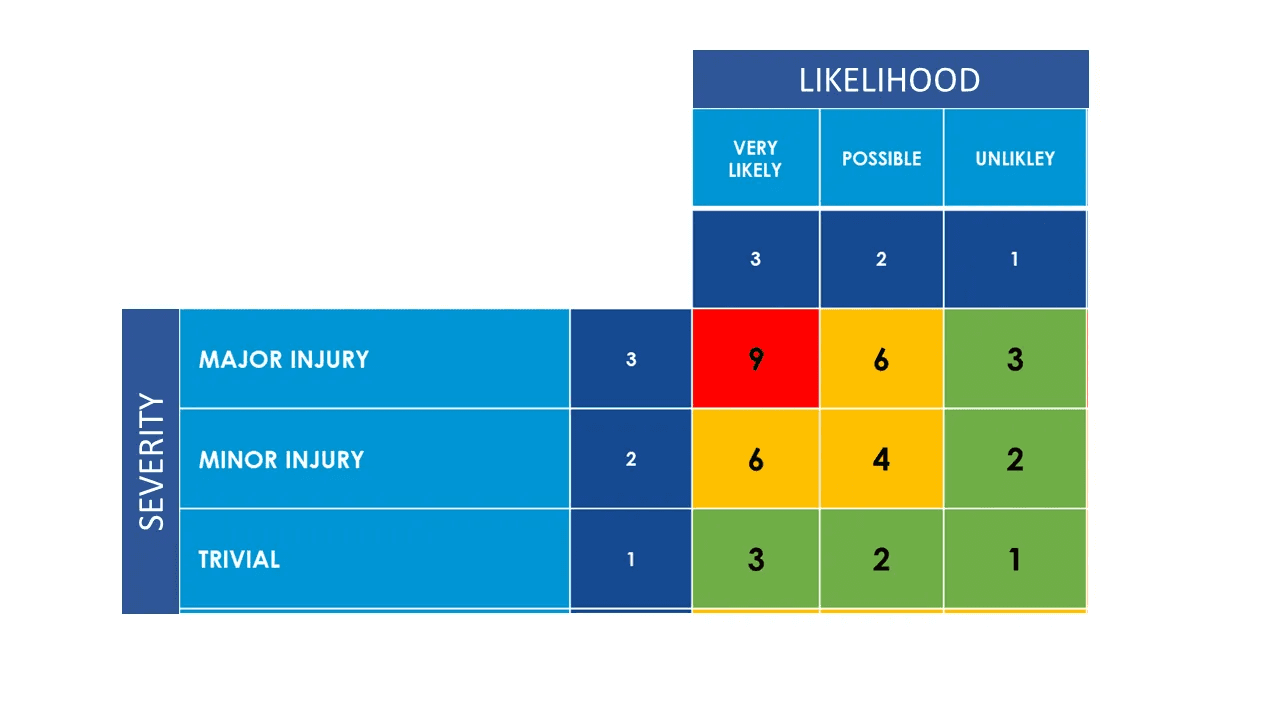
5. Assess Risk Severity
Various methods determine a risk's severity. These methods usually combine impact and likelihood ratings. You can use a standardized matrix or rating scale to assign a numerical rating to each risk.
6. Prioritize Remediation
Based on the rating, prioritize high-risk vulnerabilities first because they pose the maximum threat to the system. Address high-risk events first by implementing countermeasures and allocating resources.
7. Customize the Model
As the final step, customize the risk rating model to suit the system's needs. Adjust the risk rating criteria to incorporate more relevant factors.
Example of Calculating Risk with OWASP Risk Rating
Here's an example of how to calculate risk using the OWASP Risk Rating Methodology:
Scenario
You have a web application with a SQL injection vulnerability.
Step-by-Step Process
Identify Vulnerabilities:
Vulnerability: SQL Injection in the login form.
Threat Agents and Attacks:
Threat Agent: Malicious hacker.
Attack: Exploiting SQL injection to gain unauthorized access to the database.
Security Controls:
Existing Controls: Attackers find basic input validation insufficient to prevent the attack.
Likelihood of Threat Agent:
Skill Level: High, as SQL injection is a common vulnerability.
Motivation: High because the database contains sensitive user information.
Resources: Moderate, with tools to exploit SQL injection readily available.
Likelihood Assessment:
Likelihood of Discovery: High (3/4). Since SQL injection is well-known, they can easily detect it.
Likelihood of Exploit: High (3/4). Skilled hackers find it straightforward to exploit SQL injection.
Overall Likelihood = (Likelihood of Discovery + Likelihood of Exploit) / 2 = (3 + 3) / 2 = 3 (High)
Impact Analysis:
Technical Impact: High (3/4) because gaining access to the database can cause data leakage, modification, or deletion.
Business Impact: Severe (4/4) data leakage can cause to financial loss, legal issues, and reputational damage.
Overall Impact = (Technical Impact + Business Impact) / 2 = (3 + 4) / 2 = 3.5 (Severe)
Risk Calculation = Likelihood * Impact
= 3 (High) * 3.5 (Severe)
= 10.5
Based on a predefined risk rating scale (e.g., 0-3 is low, 4-6 is medium, 7-9 is high, and 10-12 is critical), a risk score of 10.5 categorizes this vulnerability as Critical.
Remediation
Implement strong input validation, parameterized queries, and prepared statements to mitigate the risk and address this critical vulnerability immediately.
Benefits of OWASP Risk Rating Methodology
There are several benefits for organizations in securing their software systems, as follows:
1. Standardized
The OWASP risk rating method is standardized and follows a consistent yet effective framework. Different teams objectively assess the risks.
2. Prioritization
This risk rating approach assigns a numerical value to different risks. This can help prioritize the mitigation process for risks. The factors considered while prioritization is exploitability, likelihood, impact, etc. Prioritization ensures that teams first manage high-severity risks and allocate resources effectively.
3. Optimization
This method optimizes resource allocation by focusing on high-risk events first. If organizations have limited resources, they can direct those resources toward critical risks and vulnerabilities. This is also important because not all risks threaten the software.
Final Thoughts
The OWASP risk rating methodology is a valuable framework in cybersecurity. It helps organizations manage available resources wisely, systematically evaluate risks, and effectively mitigate their impact. It enhances resilience in software applications. This methodology helps businesses improve their security posture against vulnerabilities and threats.
Cybersecurity is essential for business; Application security engineers must take action before a security breach occurs. Leverage a powerful platform like Akto to find and fix vulnerabilities in APIs. Our team of knowledgeable security experts assists organizations in creating a strong security posture for their web applications and applying the OWASP Risk Rating Methodology.
Contact us for a demo today!
Important Links
Keep reading
API Security
8 minutes
NIST Cybersecurity Framework
The NIST Cybersecurity framework provides organizations with a set of standards, guidelines, and practices to develop strong cybersecurity practices for managing cybersecurity risks effectively.
API Security
7 minutes
API Security Audit
An API Security Audit evaluates APIs, identifies potential risks, and strengthens the organization's defenses against security breaches and cyber-attacks.
API Security
8 minutes
Security Information and Event Management (SIEM)
SIEM aggregates and analyzes security data across an organization to detect, monitor, and respond to potential threats in real time.
Experience enterprise-grade API Security solution