Rapid7 DAST: Steps to Install and Configure Rapid7 DAST
Rapid7 DAST analyzes web applications to detect security vulnerabilities, helping you safeguard your apps from cyber threats and ensure robust protection.

Muze
Jul 12, 2024
In the modern era of digital technology, where everything is interconnected, securing and protecting web applications from cyber threats has become increasingly important. Rapid7 Dynamic Application Security Testing (DAST) detects security vulnerabilities comprehensively and automatically, protecting your web applications from online threats like SQL injection and XSS.
This tool helps identify and reduce security risks, ensuring your applications stay strong and secure.
In this blog, you will learn about Rapid7 DAST, how it works, its key features, steps to install and configure it, challenges and limitations, and alternatives to it.
Let’s get started.
What is Rapid7 DAST?
Rapid7 DAST, short for Dynamic Application Security Testing, is a comprehensive security testing system. It uses a black-box testing method to actively analyze web applications and expose possible security vulnerabilities.
Doing this increases the likelihood of uncovering concealed security risks that cyber attackers could exploit. This proactive and thorough approach to security testing is among the many reasons why organizations often employ Rapid7 DAST to protect web applications from online threats.
How Rapid7 DAST Works?
Rapid7 Dynamic Application Security Testing (DAST) tool operates by conducting a thorough and continuous search for vulnerabilities within live web applications. Upon identifying a security vulnerability, Rapid7 DAST immediately sends automated alerts to the relevant teams within the organization.
This efficient alert system equips these dedicated teams with the necessary tools to prioritize the identified vulnerability. These steps ensure that these teams have the vital information they need to take quick and decisive action to remediate the issue at hand.
Furthermore, the Rapid7 DAST also offers businesses a valuable opportunity to gain a deeper understanding of their web applications' behavior. This includes highlighting newly emerging weaknesses as the applications continue to evolve, grow, and adapt to new challenges.
Key Features of Rapid7 DAST
It offers a range of features designed to identify, manage, and remediate vulnerabilities in web applications. Here are the key features of Rapid7 DAST:
1. Early Detection
The Rapid7 DAST tool encourages early usage within the Software Development Life Cycle (SDLC) to identify potential weaknesses in web applications. This approach significantly reduces the cost and effort needed to rectify problems later in the development process.
2. Comprehensive Approach
The combination of Rapid7 DAST with Static Application Security Testing (SAST) and application penetration testing creates a multi-layered security approach, which significantly enhances the effectiveness of security measures and provides a robust defense against potential cyber threats.
3. Collaboration with DevOps
It facilitates effective cooperation with DevOps teams by integrating Rapid7DAST tools with bug-tracking systems. This integration provides developers with the precise information they need to remediate vulnerabilities in a timely manner.
4. Regulatory Compliance Assistance
This ensures that your web application adheres to the safety guidelines set by regulatory bodies. For example, it can evaluate how well your application aligns with the OWASP Top 10, a widely accepted benchmark for application security. This practice helps your business avoid penalties for non-compliance and protects your reputation by demonstrating your commitment to security.
5. Inspection of Input Sanitization and Error Handling
The Rapid7 DAST tool tests and verifies the strength of an application's input sanitization routines and error-handling mechanisms. These tests are crucial to ensure that applications handle erroneous or malicious inputs effectively.
Steps to Install and Configure Rapid7 DAST
To start utilizing Rapid7 DAST for your web application security, you must install and configure it. Here are the steps to install and configure Rapid7 DAST (Dynamic Application Security Testing):
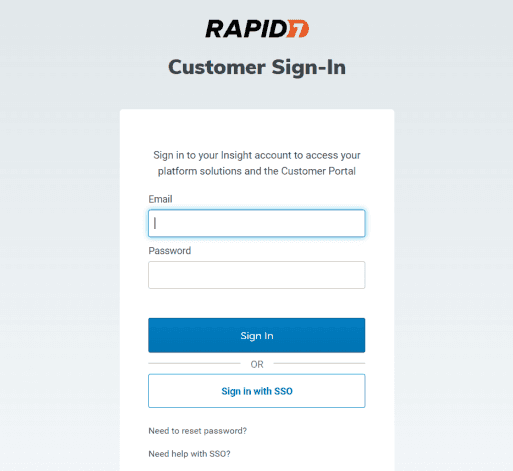
Step 1: Sign Up and Access Rapid7 Insight Platform
Sign Up:
Visit the Rapid7 Website: Rapid7 Sign Up.
Choose the appropriate product or trial version and complete the sign-up process by providing your details.
Login:
Access the Rapid7 Insight Platform: Insight Platform Login.
Use your credentials to log in to the dashboard.
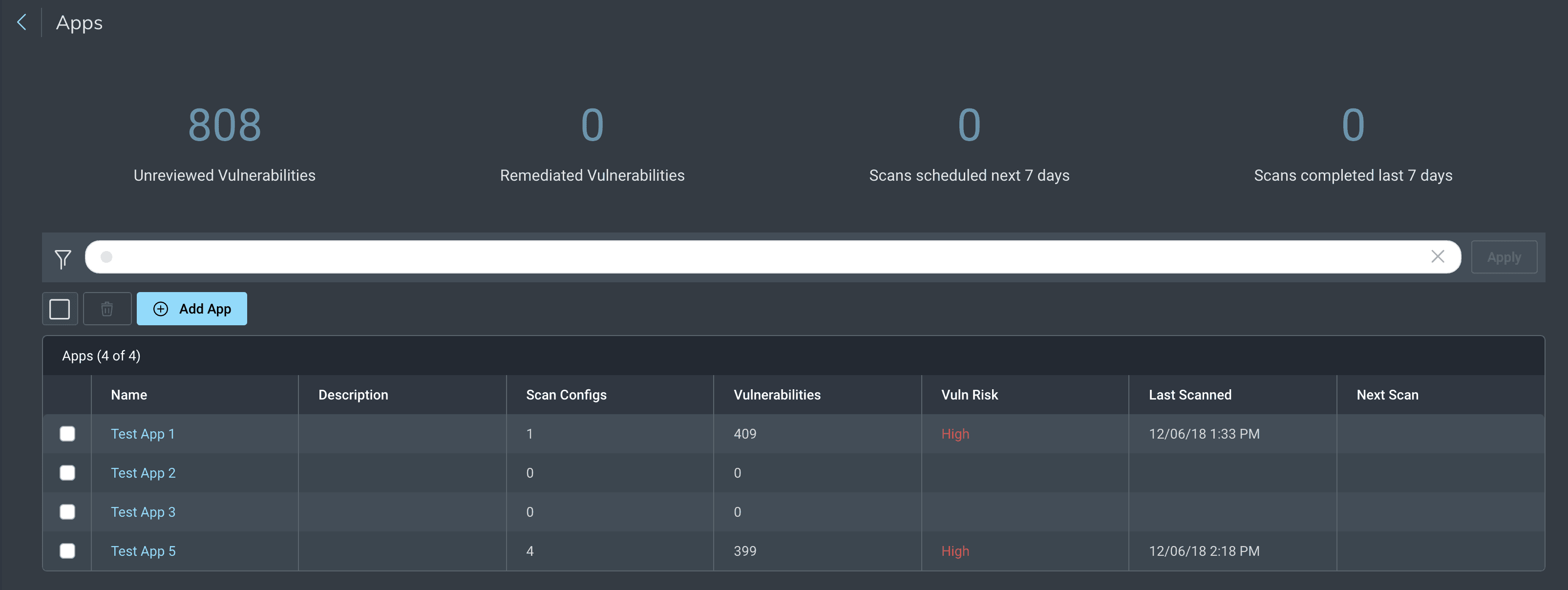
Step 2: Access InsightAppSec
Navigate to InsightAppSec:
From the Insight platform dashboard, locate and select the InsightAppSec application to access the DAST tool.
Step 3: Set Up Your Environment
Define Applications:
In InsightAppSec, click on the
Applicationstab.Click the
Add Applicationbutton.Enter the name and URL of the web application you want to scan.
Click
Saveto add the application to your list.
Configure Authentication:
If your application requires authentication, navigate to the
Authenticationsection under your application settings.Choose the authentication type (e.g., form-based, HTTP, OAuth).
Provide the necessary credentials or tokens.
Test the authentication to ensure it’s working correctly.
Step 4: Install the Scan Engine
Download the Scan Engine:
Go to the ‘Engines’ section in InsightAppSec.
Click “Add Engine” and select the appropriate operating system (Windows, Linux, etc.).
Download the scan engine installer.
Install the Scan Engine:
Windows:
Run the downloaded installer (.exe file).
Follow the installation prompts to complete the installation.
Linux:
Open a terminal.
Run the installation script using the appropriate command. For example:
Configure the Scan Engine:
After installation, open the Scan Engine configuration interface.
Enter your InsightAppSec API key, which you can find in your account settings on the Insight platform.
Test the connection to ensure the scan engine properly links to your InsightAppSec account.
Step 5: Create a Scan Configuration
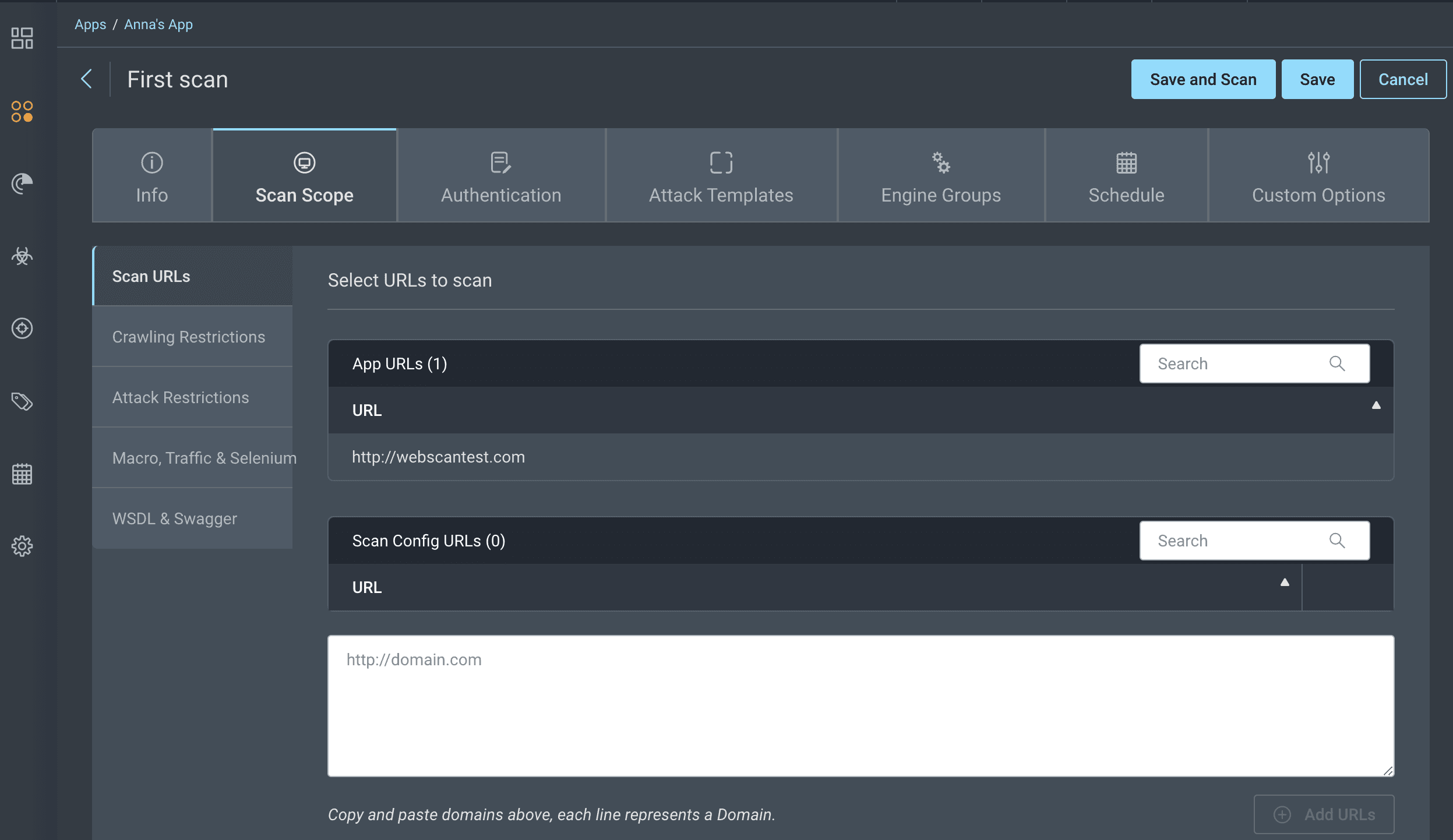
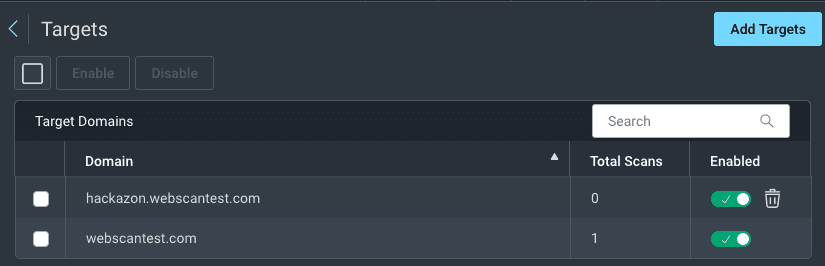
Define Scan Targets:
Go to the
Scanstab.Click
Create Scan Configuration.Select the application you added earlier.
Specify the scan targets (URLs or endpoints) you want to include in your scan.
Set Scan Policies:
Choose a scan template or policy that defines the types of tests to be performed (e.g., full scan, quick scan).
Customize the scan settings if needed, such as specifying particular areas of the application to focus on or excluding certain parts.
Schedule Scans:
Optionally, go to the
Schedulesection.Set up a scan schedule by choosing the frequency and timing of the scans (e.g., daily, weekly).
Step 6: Run a Scan
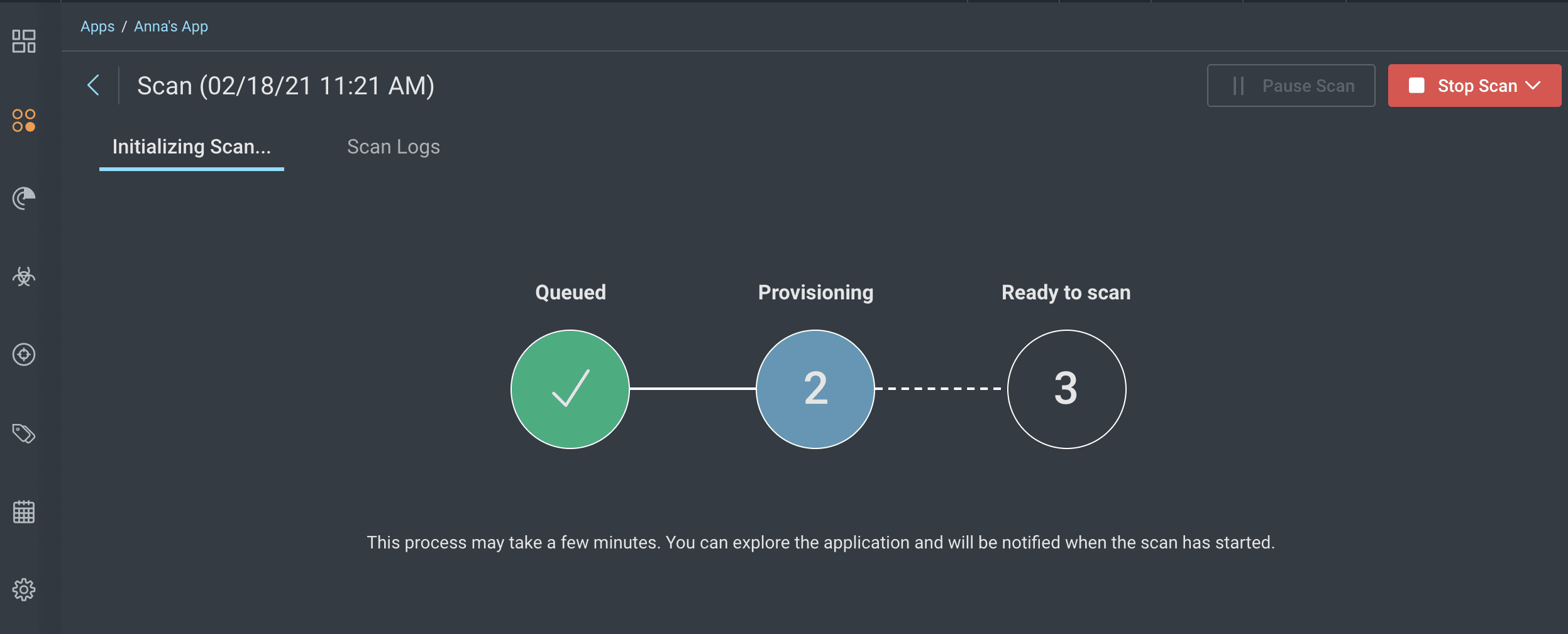
Initiate Scan:
From the InsightAppSec dashboard, select the scan configuration you created.
Click
Start Scanto begin the scanning process.
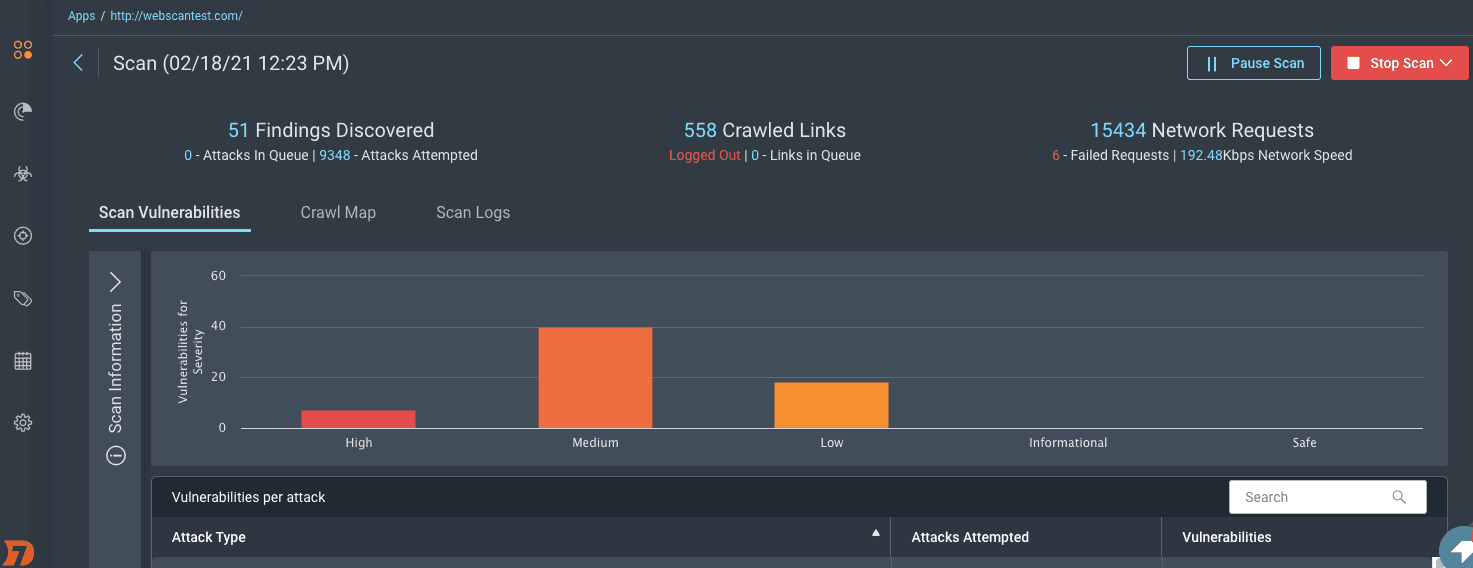
Monitor Progress:
Track the progress of the scan in real time through the InsightAppSec interface.
Step 7: Review Scan Results
Access Scan Reports:
After completing the scan, navigate to the
Reportstab.Select the completed scan to view the detailed report.
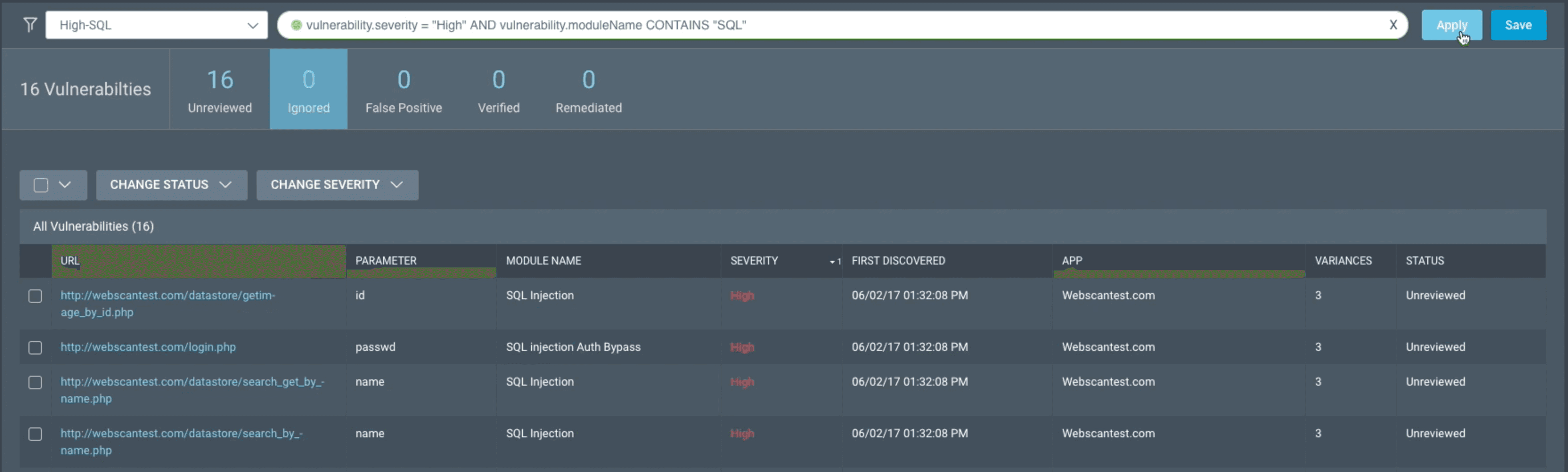
Analyze Findings:
Review the identified vulnerabilities, categorized by severity (e.g., critical, high, medium, low).
Each finding will include a description, affected URLs, and remediation guidance.
Challenges and Limitations
Common Challenges Using Rapid7 DAST
While Rapid7 DAST is a powerful tool for dynamic application security testing, users can face several challenges:
1. Complex Setup
The initial setup of Rapid7 DAST can be quite complex and time-consuming. This is because it requires a good level of technical knowledge to properly configure and optimize the tool.
2. False Positives/Negatives
Like any automated security tool, Rapid7 DAST sometimes generates false positives and negatives. False positives occur when the tool incorrectly flags safe items as threats, causing unnecessary alarms and wasting time for security teams.
3. User Interface
The user interface of Rapid7 DAST is another area where some users experience challenges. Some find the interface not as intuitive as they would like, making the tool difficult to navigate and understand, especially for beginners or those unfamiliar with such security tools.
4. Limited Customization
While Rapid7 DAST offers a good range of built-in features, it lacks flexibility in terms of customization. Some users may have specific needs or preferences that are not catered to by the default settings and features of Rapid7 DAST.
Limitations Using Rapid7 DAST
While Rapid7 DAST is a powerful tool for finding vulnerabilities in web applications, it does have some limitations:
1. Not Suitable for All Applications
One significant limitation of Rapid7 DAST is that it might not function optimally with all types of web applications. This is particularly the case for applications heavily reliant upon client-side scripting or complex technologies.
2. Misses Certain Issues
While Rapid7 DAST has the capability to identify a wide range of vulnerabilities, there might be certain issues that escape its grasp. These undetected issues are usually the ones that are more effectively identified through manual testing or other types of security testing.
3. Requires Technical Knowledge
The effective use of Rapid7 DAST calls for a certain degree of technical understanding from its users. The tool offers complex features and generates detailed reports, which may overwhelm beginners or those without a technical background.
4. Limited Coverage
It might not achieve as much effectiveness in handling other system security facets. For example, testing network systems or apps that don't need the internet might not give as good results as testing online web apps.
Alternatives to Rapid7 DAST
There are many options besides Rapid7 DAST for finding weaknesses in web apps and APIs. Each one has special features. When you look at these options, think about what kinds of weaknesses you want to find. Here are some notable alternatives:
1. Akto
Akto is a proactive API security platform that offers comprehensive API security testing, distinguishing it from Rapid7 DAST, which focuses on web applications. Akto’s robust testing library and support for Dynamic Application Security Testing (DAST) make it an excellent alternative for organizations prioritizing API security, ensuring thorough protection for their API endpoints alongside traditional dynamic testing.
2. OWASP ZAP
OWASP ZAP is a free, open-source tool known for its flexibility and strong community support, making it an economical alternative to Rapid7 DAST. Its high level of customization allows users to adapt the tool to specific testing needs, offering a versatile and budget-friendly option for dynamic application security testing.
3. PortSwigger
Known for its Burp Suite, it offers a comprehensive toolset for both manual and automated web security testing, providing deeper insights and control over the testing process than Rapid7 DAST. Its advanced features and user-friendly interface make it suitable for users seeking detailed, customizable security assessments.
4. Acunetix
Acunetix detects a wide range of web vulnerabilities and integrates well with other security tools, offering more extensive vulnerability scanning capabilities than Rapid7 DAST. Its robust feature set makes it ideal for enterprises looking for thorough application security assessments with strong integration support.
5. Nessus
Nessus provides comprehensive vulnerability management beyond just web applications, making it a versatile alternative to Rapid7 DAST. It offers detailed vulnerability assessments and integrates seamlessly with Tenable.io products, making it ideal for organizations needing a unified, broad-spectrum security solution.
Final Thoughts
Rapid7 Dynamic Application Security Testing (DAST) is crucial for fortifying web applications against modern cyber threats. Its automated vulnerability detection system empowers organizations to proactively identify and mitigate security risks, ensuring robust protection throughout the application lifecycle.
However, users may encounter challenges such as complex setups and occasional false positives, necessitating careful consideration of alternative solutions. Exploring alternatives like Akto, which specializes in API security testing, offers organizations a tailored approach to addressing specific security needs. Akto’s focus on API protection and support for Dynamic Application Security Testing (DAST) make it an appealing choice for businesses seeking enhanced security measures.
Important Links
Keep reading
API Security
8 minutes
NIST Cybersecurity Framework
The NIST Cybersecurity framework provides organizations with a set of standards, guidelines, and practices to develop strong cybersecurity practices for managing cybersecurity risks effectively.
API Security
7 minutes
API Security Audit
An API Security Audit evaluates APIs, identifies potential risks, and strengthens the organization's defenses against security breaches and cyber-attacks.
API Security
8 minutes
Security Information and Event Management (SIEM)
SIEM aggregates and analyzes security data across an organization to detect, monitor, and respond to potential threats in real time.
Experience enterprise-grade API Security solution



