ZAP DAST Overview: Installation Guide
ZAP DAST secures your web applications during runtime from security vulnerabilities by mimicking the actions of a malicious attacker.

Muze
Jul 12, 2024
Attackers always find new ways to attack, so staying ahead is critical. One great tool for this is ZAP DAST, a free tool designed to find security issues in web apps. ZAP DAST makes it easier to keep your website secure.
It's like having a smart detective working for you, scanning your site for potential security weaknesses. This helps prevent hackers from getting in and stealing your data. By using ZAP DAST, you're taking a big step towards protecting your online presence and giving yourself peace of mind about your digital safety.
In this blog, you will learn about ZAP, the key features of ZAP DAST, the installation guide, performing DAST Scans with ZAP, real-world use cases, best practices, and the alternatives of ZAP DAST.
Let's get started
What is ZAP DAST?
The Open Web Application Security Project (OWASP) developed ZAP as a comprehensive security assessment tool. ZAP automates the process of finding security vulnerabilities in web applications during runtime, mimicking the actions of a malicious attacker. With its extensive library of scanners and spiders, ZAP can identify a wide array of vulnerabilities, including but not limited to SQL injection, cross-site scripting (XSS), and insecure direct object references.

Key Features of ZAP DAST
ZAP tests the security of web applications. Here are its main features:
1. Automated Scanning
One of the key features of ZAP is the ability to scan a web application automatically. The tool systematically explores the application, finds all available links and forms, and checks for various security risks. These risks include, but are not limited to, well-known threats such as SQL injection and Cross-Site Scripting (XSS).
2. Manual Explore
It allows users to manually test a web application, change requests, and personally check responses for security issues. This hands-on approach affords a deeper understanding of the application and its potential vulnerabilities.
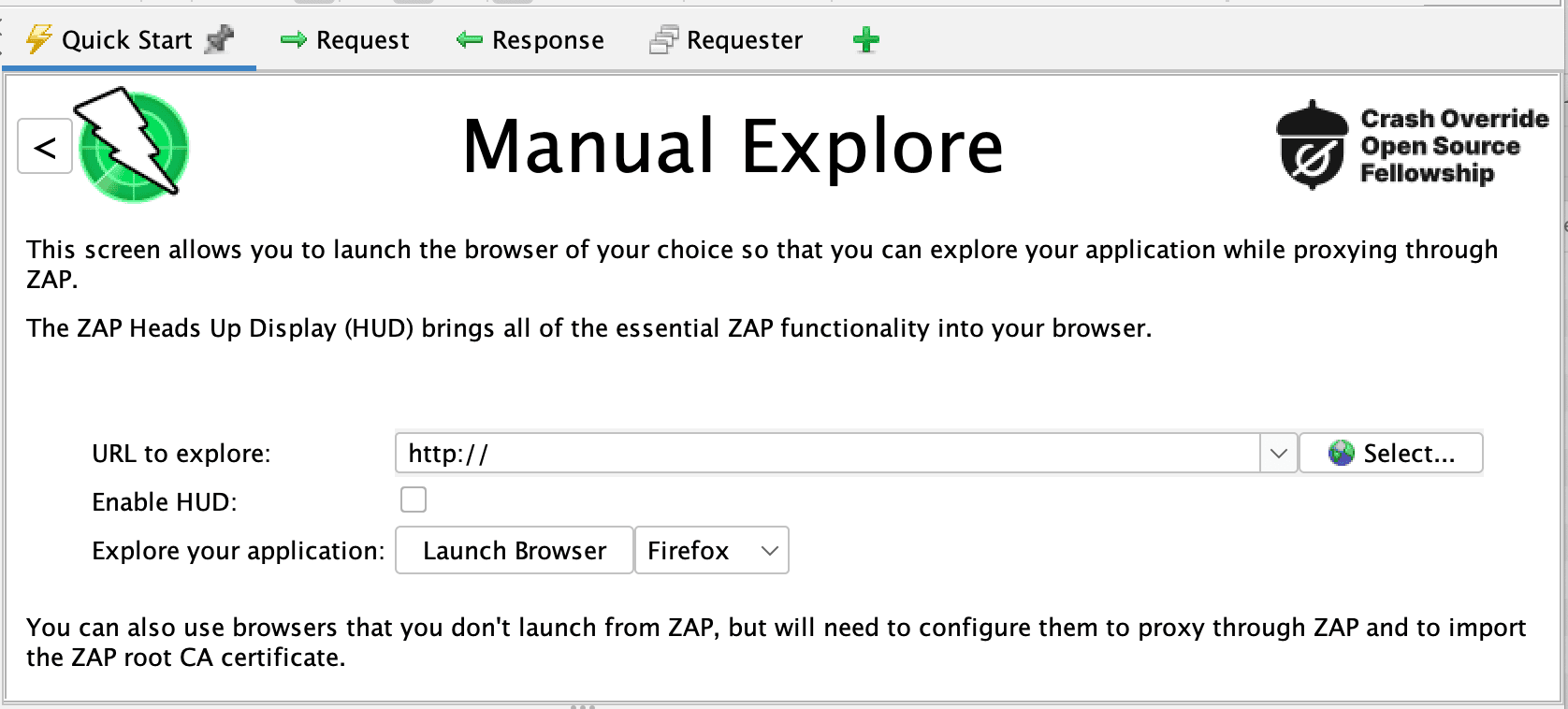
3. Active Scanning
It sends special requests to the application and analyzes how it responds. This method is comprehensive and covers many types of attacks and security risks, providing a robust evaluation of an application's security posture.
4. Passive Scanning
This feature watches and analyzes network traffic between the application and its users, looking for security issues and data leaks without interacting with the application directly.
5. Spider Tool
This tool automatically goes through a web application, following links, making a map of the application, and finding all pages, forms, and other content. Understanding how the application is structured and where to test further is useful.
6. AJAX Spider
This extends the Spider tool for web applications that heavily use AJAX to load dynamic content. It ensures that areas that update dynamically are included in the application map, which helps assess Single-Page Applications (SPAs).
Installing ZAP DAST: Step-by-Step Guide
Here are the steps to install the ZAP (Zed Attack Proxy) DAST (Dynamic Application Security Testing) tool:
Step 1: Prerequisites
Install the following prerequisites on your system:
Java: ZAP requires Java 8 or later. Verify Java installation by running the
java -versionon your terminal.
Step 2: Download ZAP
Go to the official OWASP ZAP download page.
Select the appropriate version for your operating system (Windows, macOS, Linux).
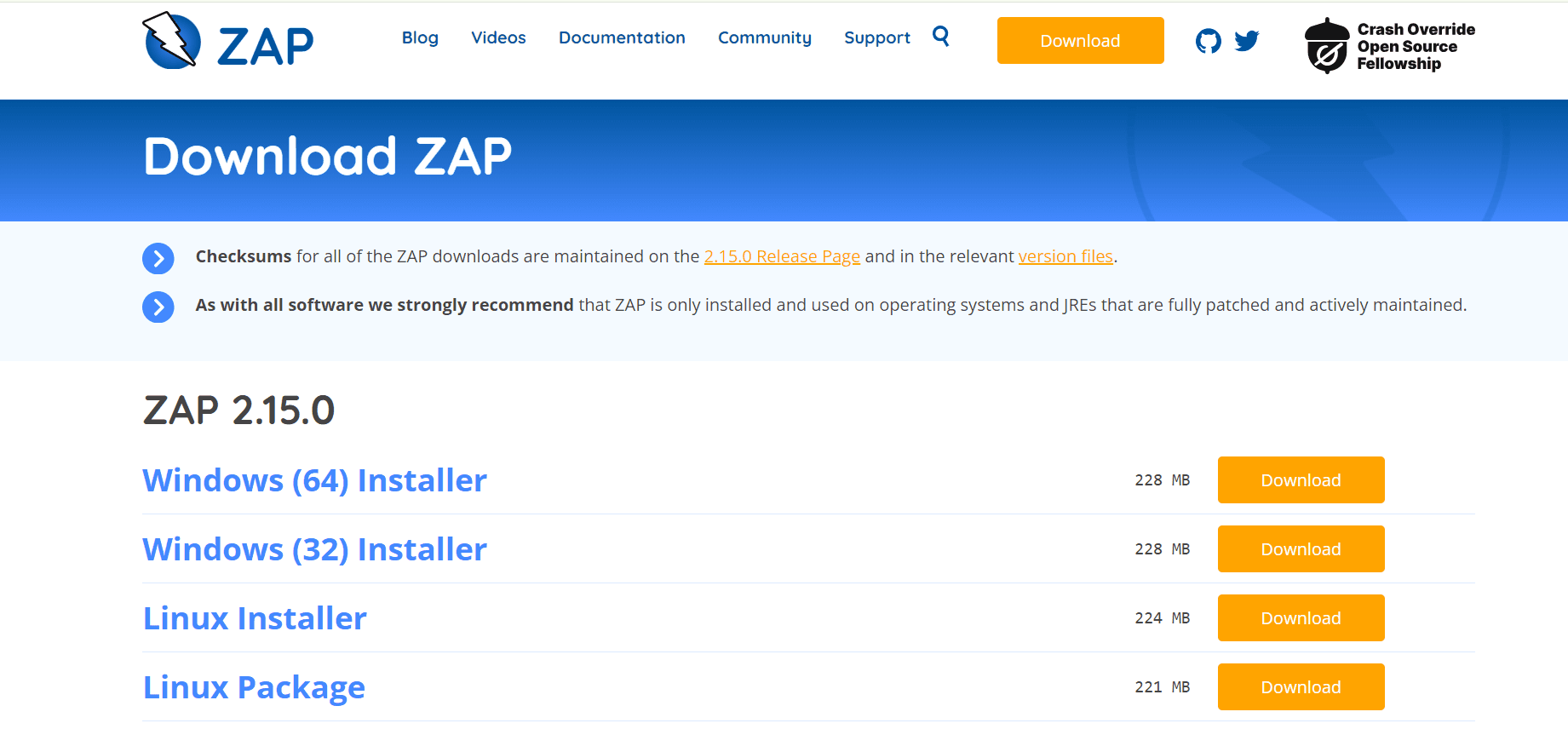
Step 3: Install ZAP
For Windows:
Download the
.exeinstaller.Run the installer and follow the on-screen instructions to complete the installation.
For macOS:
Download the
.dmgfile.Open the
.dmgfile and drag the ZAP application to yourApplicationsfolder.
For Linux:
Download the
.tar.gzfile.Extract the downloaded file:
Navigate to the extracted directory and run the ZAP executable:
Step 4: Start ZAP
After installation, start ZAP:
Windows: Find ZAP in your Start Menu or Desktop and launch it.
macOS: Open the Applications folder and double-click ZAP.
Linux: Use the terminal command
./zap.shfrom the installation directory.
Step 5: Initial Configuration
When ZAP starts for the first time, it might prompt you to choose your preference for setting up a persistent session.
The system might prompt you to configure a local proxy. By default, ZAP runs on
localhostand port8080.
Step 6: Update Add-ons
Go to
Tools>Options.Navigate to the
Check for Updatessection.Click
Check for Updatesto ensure you have the latest plugins and extensions.
Step 7: Verify Installation
Open a browser and set the proxy to
localhost:8080.Visit any website to ensure traffic is passing through ZAP. You should see ZAP logging the site requests.
Step-by-Step Guide to Performing DAST Scans with ZAP
Here's a step-by-step guide to conducting DAST scans using ZAP:
Step 1: Setup ZAP
Make sure ZAP is installed and properly configured. Follow the previous installation steps in the blog if needed.
Step 2: Configure Your Browser to Use ZAP as a Proxy
Open your browser.
Set the proxy settings to use
localhostand port8080(or the port you configured ZAP to use).
Step 3: Start ZAP
Launch ZAP.
Ensure it is running and you have configured your browser to route traffic through ZAP.
Step 4: Explore Your Application Manually
In your configured browser, navigate through your application.
ZAP will capture and log all the requests and responses as you browse.
Step 5: Automated Scan
5.1: Quick Start
In the ZAP main window, go to the
Quick Starttab.Enter the URL of the application you want to scan.
Click the
Attackbutton.
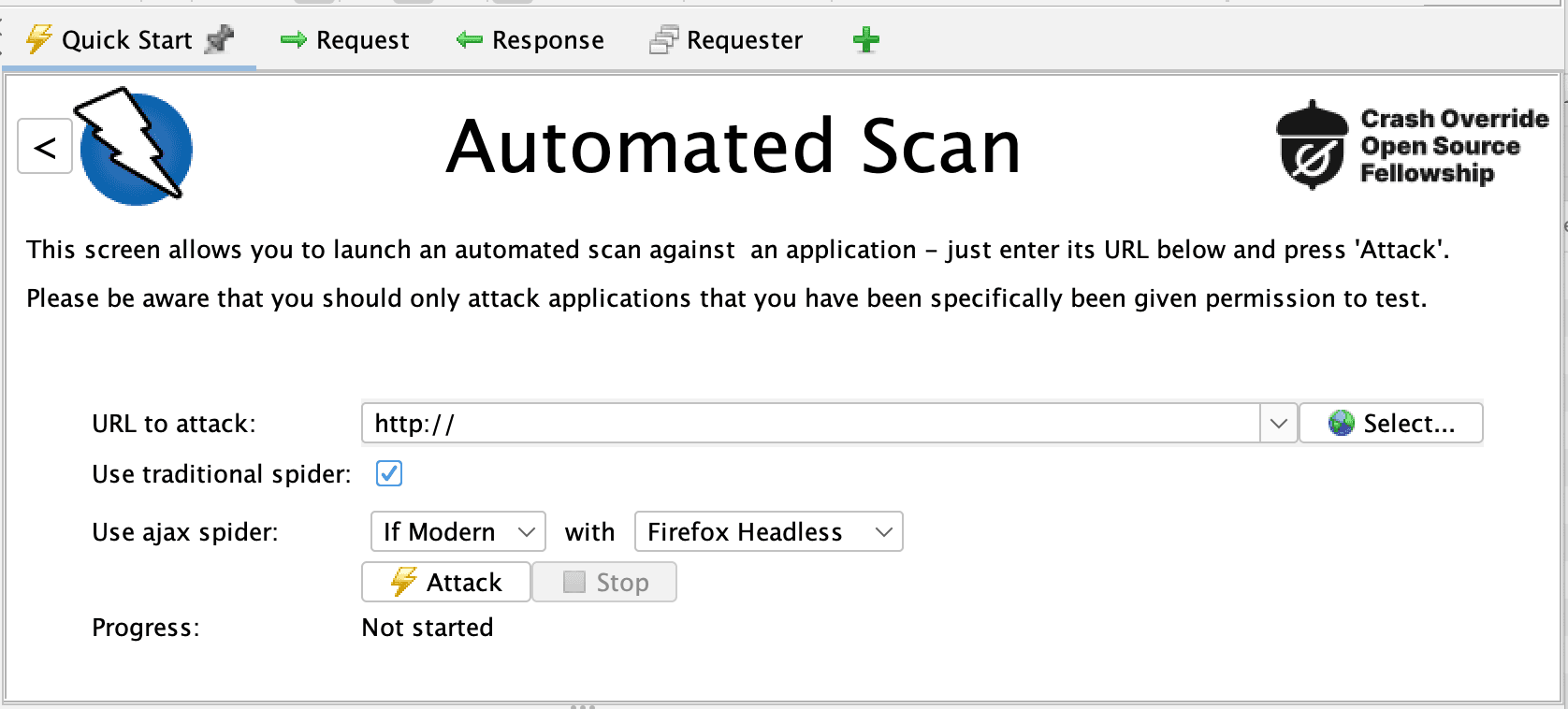
5.2: Spider Scan
In the main window, select the
Sitestab.Right-click on the site you want to scan.
Select
Attack>Spider.Configure the Spider scan options (e.g., include/exclude URLs).
Click
Start Scan.
Step 6: Active Scan
After the Spider scan is complete, right-click on the target site in the
Sitestab.Select
Attack>Active Scan.Configure the Active scan options.
Click
Start Scan.
Step 7: View Scan Results
Monitor the progress of the scan in the
Active Scantab.View the findings in the
Alertstab. ZAP categorizes the alerts by severity:High
Medium
Low
Informational
Step 8: Analyze and Interpret Results
Click on each alert to see detailed information, including:
Description of the issue
Affected URLs
Evidence of the issue
Possible mitigation steps
Step 9: Generate a Report
After the scan is complete, you can generate a report by going to
Report>Generate HTML ReportorGenerate XML Report.Choose a location to save the report and click
Save.
Step 10: Implement Fixes and Re-test
Based on the findings, work with your development team to implement necessary security fixes.
Please re-run the scan to mitigate the vulnerabilities.
Real-World Use Cases
Here are some real-world use cases where organizations implement ZAP DAST:
1. Continuous Integration/Continuous Deployment (CI/CD) Pipelines
Use Case: Integrating security testing into CI/CD pipelines.
Scenario: A software development company uses Jenkins for CI/CD and integrates ZAP DAST into their pipeline to automatically scan their web applications during the build and deployment process.
Outcome: This process ensures that the company identifies and addresses any security vulnerabilities early in the development cycle, reducing the risk of deploying vulnerable code to production.
2. E-commerce Platforms
Use Case: Securing online transactions.
Scenario: An e-commerce company regularly scans its web application using ZAP DAST to identify vulnerabilities that attackers could exploit to steal customer data or perform unauthorized transactions.
Outcome: The company maintains the security and trust of its customers and ensures secure transactions by regularly scanning and addressing vulnerabilities.

3. Financial Services
Use Case: Protecting sensitive financial data.
Scenario: A bank uses ZAP DAST to scan its online banking platform for vulnerabilities, focusing on identifying issues such as SQL injection, cross-site scripting (XSS), and insecure authentication mechanisms.
Outcome: Regular DAST scans help the bank secure its platform against potential breaches, protect sensitive financial data, and maintain regulatory compliance.
4. Healthcare Applications
Use Case: Ensuring the security of patient information.
Scenario: A healthcare provider uses ZAP DAST to scan their patient portal and other web applications to ensure they comply with HIPAA regulations.
Outcome: The provider can identify and remediate vulnerabilities that could expose patient information, ensuring they maintain the confidentiality, integrity, and availability of sensitive health data.
5. Government Websites
Use Case: Securing public-facing government services.
Scenario: A government agency uses ZAP DAST to scan their public-facing websites and portals to ensure they secure them against common web application attacks.
Outcome: The agency can prevent unauthorized access to sensitive information and maintain the trust of the public by identifying and fixing vulnerabilities.
Best Practices for Using ZAP DAST
Using ZAP DAST effectively requires adherence to best practices to ensure thorough and accurate security assessments. Here are some best practices for using ZAP DAST:
1. Regular Scanning
Frequency: Conduct scans regularly as part of your development lifecycle. Integrate ZAP into your CI/CD pipeline to ensure continuous security testing.
Consistency: Perform scans after significant changes, such as code updates, new feature implementations, or infrastructure changes.
2. Authentication and Session Management
Authentication: Configure ZAP to handle authentication mechanisms used by your application (e.g.,
OAuth, JWT, basic auth).Session Handling: Use the session management features in ZAP to ensure that scans can navigate through authenticated parts of your application.
Context Configuration: Define contexts to manage different parts of your application and their authentication settings.
3. Scope Definition
Target Definition: Clearly define the scope of your scans by including or excluding specific URLs, directories, or parameters.
Contextual Scans: Use contexts to limit scans to relevant parts of your application, avoiding unnecessary scans on third-party services or irrelevant sections.
4. Advanced Scanning Techniques
Spidering: Use the spidering functionality to discover all parts of your application. Adjust spidering settings to handle dynamic content and JavaScript-heavy applications.
Active Scanning: After an initial passive scan, conduct active scans to probe for vulnerabilities. Configure scan policies to focus on high-priority areas.
5. Scan Customization
Custom Scripts: Utilize ZAP's scripting capabilities to create custom scan rules or modify existing ones to suit your application's specific needs.
Scan Policies: Adjust scan policies to prioritize different types of vulnerabilities (e.g., SQL injection, XSS, CSRF) based on your risk assessment.
Alternatives of ZAP DAST
Alternatives to ZAP for Dynamic Application Security Testing (DAST) include a variety of options, each offering unique features and capabilities. Here's a brief overview of some notable alternatives:
1. Akto
Akto is a proactive API security platform providing comprehensive API security testing. While OWASP ZAP DAST focuses on general web application security, Akto specializes in API security testing, boasting a robust testing library and supporting Dynamic Application Security Testing (DAST) specifically for APIs. This specialization makes Akto a strong alternative to ZAP DAST, especially for organizations that prioritize API security.
2. Burp Suite
Burp Suite, provided by PortSwigger, is a leading tool for web application security testing, offering both automated and manual scanning capabilities. It excels over ZAP due to its advanced manual testing features, a powerful intercepting proxy for traffic inspection and modification, and extensibility via numerous plugins and extensions, making it the go-to choice for security professionals engaged in penetration testing, bug bounty hunting, and comprehensive security assessments.
3. Acunetix
Acunetix, from Invicti Security, is a robust web vulnerability scanner that automates the detection and remediation of security issues in web applications and APIs. It stands out from ZAP with its user-friendly interface, advanced crawling and deep scanning capabilities, and seamless integration with CI/CD pipelines, making it particularly suitable for enterprises and security teams seeking efficient and continuous automated security testing.
4. Netsparker
Netsparker, also by Invicti Security, is known for its highly accurate automated web application security scanning, leveraging proof-based scanning to eliminate false positives. This precision and reliability make it a superior choice compared to ZAP, especially for organizations that need dependable vulnerability assessments integrated with their CI/CD tools and issue trackers, ensuring minimal disruption and actionable remediation steps.
5. Qualys Web Application Scanning (WAS)
Qualys WAS is an automated, scalable scanning solution for web applications and APIs designed to detect vulnerabilities and misconfigurations. Its ability to continuously monitor and scan a large number of applications, along with seamless integration with the Qualys Cloud Platform, provides a scalable and comprehensive security solution, surpassing ZAP in environments that require continuous and extensive security assessments.
Final Thoughts
In conclusion, ZAP DAST offers robust, automated scanning and in-depth vulnerability analysis, serving as a comprehensive tool for modern web application security. ZAP DAST dynamically simulates attacks to uncover issues like SQL injection and cross-site scripting (XSS) during runtime, providing critical insights into security weaknesses.
However, for those with a specific focus on API security, Akto emerges as a specialized alternative. Akto's proactive API security testing capabilities suit environments where API integrity is paramount particularly well. Akto offers thorough testing to detect and address vulnerabilities that traditional DAST tools might miss, making it an essential addition for organizations aiming to enhance their security strategy with a targeted approach to API protection.
Important Links
Keep reading
API Security
8 minutes
NIST Cybersecurity Framework
The NIST Cybersecurity framework provides organizations with a set of standards, guidelines, and practices to develop strong cybersecurity practices for managing cybersecurity risks effectively.
API Security
7 minutes
API Security Audit
An API Security Audit evaluates APIs, identifies potential risks, and strengthens the organization's defenses against security breaches and cyber-attacks.
API Security
8 minutes
Security Information and Event Management (SIEM)
SIEM aggregates and analyzes security data across an organization to detect, monitor, and respond to potential threats in real time.
Experience enterprise-grade API Security solution



